This is the first instalment of a 3-part series on making cyber threat intelligence actionable. The series will cover what threat intelligence is, where to find it, and how to turn it into threat hunting material using the MITRE ATT&CK framework and Sigma rules. Today we will be delving into the MITRE ATT&CK framework.
This framework is the holy bible of cyber threat intelligence. It provides a common language for describing and categorizing adversarial tactics, techniques, and procedures (TTPs) based on real-world observations. It was created by MITRE Corporation, a not-for-profit organization that operates federally funded research and development centres.
Let’s jump in!
Overview of the MITRE ATT&CK Framework
The ATT&CK framework is used to analyse and understand the tactics and techniques that threat actors use to compromise, infiltrate, and exfiltrate information from a system or network.

It consists of a a matrix that lists various tactics and techniques used by attackers, such as initial access, persistence, privilege escalation, and exfiltration.
In recent years, the initial matrix has been separated into three matrices that cover Enterprises, Mobile, and ICS (Industrial Control Systems).
These matrices list the specific TTPs threat actors will use in each respective domain. We will focus on the Enterprise version of the framework because it is the most widely used by security professionals. That said, I encourage you to check out the Mobile and ICS versions if you have an interest in these fields.
The MITRE ATT&CK framework is widely used by cybersecurity professionals to assess and evaluate their organization’s defences and identify areas that need improvement. By understanding the specific tactics and techniques used by attackers, defenders can take proactive measures to improve their security posture and mitigate potential threats. As a threat intelligence analyst the MITRE ATT&CK framework is an indispensable tool as it allows collaboration within the industry when reacting to common threats.
For example, if ABC Security provides managed security services to several organisation and they see a threat actor targeting several of these organisations using similar TTPs, they will often share the TTPs used by said threat actor to the wider community. The security team at XYZ Corp. can then use this information to perform threat hunting, confirm if they have detection capabilities related to these TTPs, and, ultimately, be better protected. The common language used to share the TTPs will be the MITRE ATT&CK framework.
The Technical Details
Now you have an understanding of what the MITRE ATT&CK framework is, and how it is used, let’s jump into the technical details so you can begin using the framework yourself!
The MITRE ATT&CK framework is comprehensive and provides detailed knowledge of adversarial tactics and techniques. These tactics and techniques are divided into an organisational structure as follows; Tactics are at the top with Techniques (and sub-techniques) being grouped under a Tactic. Under Tactics are Procedures which are the specific actions required to perform a Technique.
A Tactic is high-level goal or objective that an attacker aims to achieve during a cyber attack. It encompasses a broad range of techniques and procedures that attackers may use to accomplish their objectives.
A Technique is a specific method or approach that an attacker may use to accomplish a specific objective or goal, as defined by a Tactic.
The Tactics in the framework stay consistent, however as new hacking methods emerge the Techniques are regularly updated between versions of the framework.

These 14 Tactics include:
- Reconnaissance: Techniques that involve adversaries actively or passively gathering information that can be used to support targeting victims, such as scanning for vulnerabilities or phishing for information about technologies or people.
- Resource Development: Techniques that involve adversaries creating, purchasing, or compromising/stealing resources that can be used to support targeting victims. These resources include; infrastructure, accounts, or capabilities (e.g. malware, ransomware, phishing emails, etc.).
- Initial Access: Techniques used to gain an initial foothold in a system or network, such as exploiting vulnerabilities or using social engineering methods.
- Execution: Techniques used to execute malicious code on a system, such as running scripts or installing malware.
- Persistence: Techniques used to maintain access to a system or network over a longer period of time, such as creating backdoors or installing rootkits.
- Privilege Escalation: Techniques used to gain higher levels of access on a system or network, such as exploiting vulnerabilities in the operating system or applications.
- Defence Evasion: Techniques used to evade detection by security controls, such as antivirus software or intrusion detection systems (AV, IDS, EDR).
- Credential Access: Techniques used to steal or crack user credentials, such as stealing passwords or exploiting vulnerabilities in authentication mechanisms.
- Discovery: Techniques used to gather information about a system or network, such as enumerating user accounts or scanning for open ports.
- Lateral Movement: Techniques used to move laterally through a network, such as using stolen credentials to access other systems or using remote desktop protocols.
- Collection: Techniques used to collect data or information from a system or network, such as exfiltrating sensitive data or capturing keystrokes.
- Command and Control: Techniques that adversaries may use to communicate with systems under their control within a victim network. Adversaries will try to mimic normal traffic to blend in to their target’s environment and avoid detection.
- Exfiltration: Techniques used to transfer data or information out of a system or network, such as using command-and-control channels or using cloud storage services.
- Impact: Techniques that adversaries use to disrupt availability or compromise integrity by manipulating business and operational processes. This is usually involves destroying or tampering with data.
The technical details for each tactic and technique include information about the attack vector, the type of software or tool used, and the potential impact to the system or network. This information is designed to help defenders understand the threat landscape and develop effective mitigation strategies.
For instance, under the Initial Access Tactic there are currently 9 Techniques that threat actors have used. One of these is Phishing (T1566), which has 3 sub-techniques:
- Spearphishing Attachment (T1566.001)
- Spearphishing Link (T1566.002)
- Spearphishing via Service (T1566.003)
Organisations and security platforms will publish threat intelligence reports that detail security incidents. In these reports there will be a list of TTPs the security team observed when investigating the incident and the team will detail this using the MITRE ATT&CK framework. If one of the initial access TTPs was a spearphishing attachment, the team would say that T1566.001 was used to gain initial access.
You, as a defender who is reading the report, can then research this Technique using the MITRE ATT&CK framework and find specific Mitigations (e.g. User Training M1017) or ways of detecting it through Detections (Network Traffic Content DS0029) these help protect your organisation from this technique. If you have these Mitigations/Detections in-place and you can sleep easy at night knowing you are protected against this threat.
That’s it! The flow of threat intelligence to operational security: read threat intelligence reports, use the MITRE ATT&CK framework to check you have appropriate Mitigations/Detections in-place, and rest easy.
The hard part is having the Mitigations/Detections in-place and keeping up-to-date with the latest threats, but this general flow is how security teams improve their defences on a continual basis.
Related Projects
The MITRE ATT&CK framework does not exist alone. There are a variety of useful related projects that help defenders use the framework.
Groups
MITRE tracks “activity clusters” (threat actors) and provides a description of the group, their associated names, techniques they commonly use, and software they often deploy in their campaigns. This is a treasure trove for threat intelligence analysts as they can figure out which groups are likely to target them (based on the description of the group), make a list of their TTPs/software, and then formulate an intelligence-driven approach to protecting their organisation from this threat.
Software
MITRE tracks the software that is being used to perform cyber attacks. As previously mentioned, MITRE maps this software to threat actors it tracks and an analyst can use this to provide intelligence lead defence to their security operations.
Campaigns
Recently, MITRE has begun to track campaigns which are being seen in the wild. Campaigns are intrusion activity that share common characteristics (e.g. phishing emails coming from the same domain name) and MITRE uses these characteristics to map campaigns to the groups and software it tracks. This is useful for a threat intelligence analyst as the look to identify, or gather further information, about a campaign that may be targeting them and they need to be aware of.
The ATT&CK Navigator
The Navigator is a web-based tool that enables users to visualize and explore the MITRE ATT&CK framework. It provides a graphical representation of the framework, which makes it easier for users to understand and analyse the tactics and techniques that threat actors use to compromise systems. Users can create and save their own views of the framework, highlight specific techniques or tactics, and add notes and comments to share with other team members.
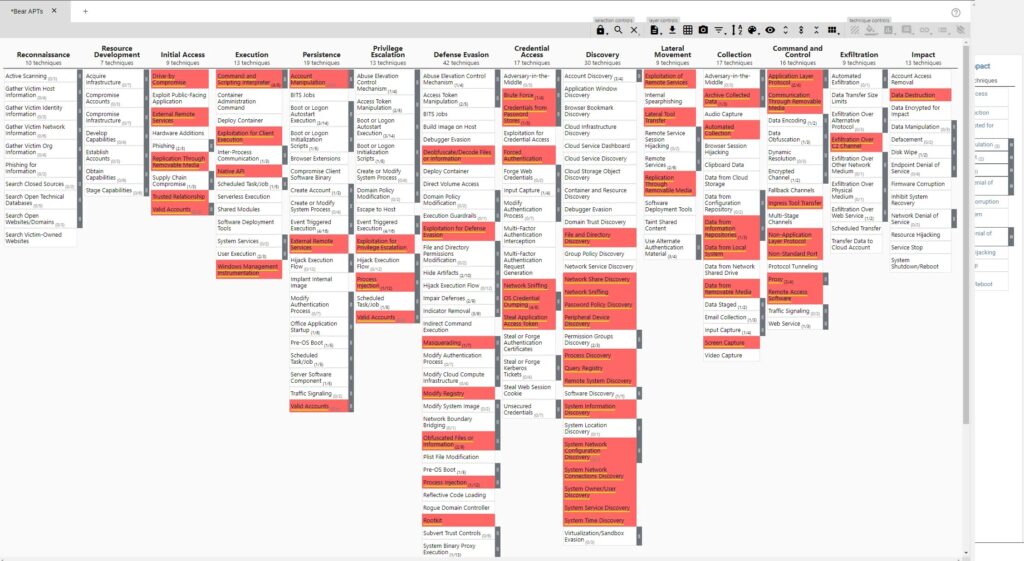
CALDERA
This is an open-source framework developed by MITRE for the creation of automated adversary emulation plans. It is designed to help security teams assess their organization’s defences by simulating real-world attacks using a techniques and tactics mapped to the MITRE ATT&CK framework. This automated solution includes a graphical user interface (GUI) that allows users to easily create and manage custom attack plans, as well as a range of plugins and modules for different attack techniques. It shows an attack in real-time and allows security teams to identify their weaknesses in a controlled environment.
CASCADE
This is a command-and-control (C2) framework developed by MITRE for use in red team operations and adversary emulation. The framework is designed to enable red teams to quickly and easily create and manage C2 infrastructure, allowing them to more effectively simulate the actions of a real-world adversary. Like CALDERA, Cascade is based on the MITRE ATT&CK framework, and it is designed to support a wide range of different attack techniques and tactics by being highly modular. It can be integrated with other tools and platforms to provide a comprehensive adversary emulation solution for red teams and security practitioners.
CAR
CAR stands for “Cyber Analytics Repository” an it is a knowledge base of analytic models, methods, and tools designed to help security teams detect and respond to cybersecurity threats. It contains a wide range of analytical models, which are essentially pre-built algorithms and analytical methodologies for detecting and responding to cyber threats. These models cover a wide range of techniques, including machine learning, behavioural analytics, and more traditional rules-based methods. It is intended to be an open resource, and users are encouraged to contribute their own models and methods to the repository.
ATT&CK Expressed in STIX
This project provides a machine-readable version of the MITRE ATT&CK framework using the Structured Threat Information eXpression (STIX) language. STIX is a standardized language for expressing structured cyber threat intelligence, and it allows security professionals to share and analyse threat intelligence in a more efficient and effective way. The project includes a range of tools and resources for working with the framework, including a STIX/TAXII server for accessing and sharing ATT&CK data, and a set of libraries and APIs for integrating the framework into existing security tools and platforms.
These related projects all make use of the MITRE ATT&CK framework to deliver a consistent language in understanding the TTPs employed by threat actors. It is highly recommended to investigate these projects further and see where they can help improve the security of your organisation.
The next instalment in this series will look at using the MITRE ATT&CK framework and a threat intelligence report to find TTPs and IOCs to hunt for malicious activity in our environment.
Till then friends, stay frosty!
Discover more in the Load & Load: Actionable Threat Intelligence 101 series!



