Hello there 👋
Welcome back to the Kraven Security weekly newsletter, triaging the week. We round up the week’s top news stories, highlight our featured article, give you some learning resources, and finish with a few personal notes about what’s happening at the company.
This week we saw several novel malware variants popup. One used Discord bots to exfiltrate stolen data, another targeted threat researchers with malicious intelligence reports, and a leak revealed the “Uber of cybercrime.” We also saw governments flexing their muscles, with the Australian government posing sanctions on a Russian national behind REvil ransomware and the UK NCSC publishing a report on the dangers of AI.
Alongside the doom and gloom of the news, we saw some great learning resources released on cloud security, LOLBins, and Sysmon. Let’s dive into it!
Top 5 News Stories

Story #1: Malware Uses Discord Bots to Exfiltrate Your Data
NS-STEALER is a new Java-based information stealer that leverages Discord bots for data exfiltration from popular browsers. It is being distributed as a ZIP archive masquerading as cracked software. It steals cookies, credentials, and data from various popular web browsers.
This malware is interesting because it uses a Discord Bot channel to exfiltrate the stolen data. This is a high level of sophistication, using X509 certificates to authenticate to Discord, but it provides the adversary a cost-effective solution to blend into their target’s environment.
Story #2: Australia Imposes Cyber Sanctions on Russia Hacker
Australia has taken its cyber security efforts to a new level with the imposition of sanctions on a Russian national implicated in a significant cyber attack on health insurer Medibank Private. The health insurer was attacked by ransomware in 2022, and data on around 10 million customers leaked, later sold on the dark web.
The REvil ransomware gang likely carried out the attack, and Australian authorities accused Russia of harboring the group. These new sanctions mark the first application of the “significant cyber incidents” sanctions the Australian government introduced in 2021.
Australian Government – Defence
Story #3: North Korean Hackers Weaponize Fake Research to Deliver RAT
Media organizations and high-profile experts in North Korean affairs have been targeted by a threat actor known as ScarCruft since December 2023. ScarCruft has been experimenting with new infection chains, including using a technical threat research report as a decoy to deliver the infamous RokRAK backdoor.
This new campaign likely targets consumers of threat intelligence (cybersecurity professionals) to gain strategic intelligence and insight into non-public cyber threat intelligence and defense strategies.
Story #4: Vextrio: The Uber of Cybercrime
VexTrio has emerged as a key player in brokering malware. A recent leak revealed that the criminal affiliate program brokers malware for 60+ threat actors, including ClearFake, SocGholish, and TikTok Refresh. The gang has been dubbed the “Uber of cybercrime” and the “single largest malicious traffic broker described in security literature.”
I highly recommend reading the full report by Infoblox for great insights into the operations of cybercrime and the malware-as-a-service (MaaS) economy.
Story #5: NCSC Says AI Will Empower Ransomware Over the Next 2 Years
The United Kingdom’s National Cyber Security Centre (NCSC) has warned about the growing threat of ransomware, citing the potential adverse impact of artificial intelligence (AI) tools on cyber security. They say cybercriminals are already using AI for nefarious purposes, and this will worsen over the next two years, helping increase the volume and severity of cyber attacks.
AI lowers the barrier of entry for cybercriminals, making it significantly easier for low-skilled hackers to perform sophisticated cyber attacks at scale. To defend against this, security tools and defenders must up their game and embrace AI.
Top Tips of the Week

Threat Intelligence
- Collaborate with industry ISACs for sector-specific CTI. Contribute and benefit from collective defense efforts.
- Use CTI to assess and mitigate risks associated with emerging technologies. Stay ahead of potential threats in evolving tech landscapes.
- Monitor emerging threats through CTI. Stay ahead by adapting defenses to new tactics and techniques.
Threat Hunting
- Integrate threat intelligence into threat modeling in cyber threat hunting. Enhance your security posture by identifying potential threats early in the development process.
- Simulate real-world attacks through red teaming exercises. Identify vulnerabilities and enhance cyber threat hunting capabilities.
- Implement threat intelligence in incident response. Proactive measures are as crucial as swift and effective responses.
Custom Tooling
- Balance flexibility and simplicity in custom tool design. Create tools that address specific needs without unnecessary complexity.
- Collaborate with compliance teams for custom tool development. Ensure that tools align with regulatory requirements and industry standards.
Feature Article
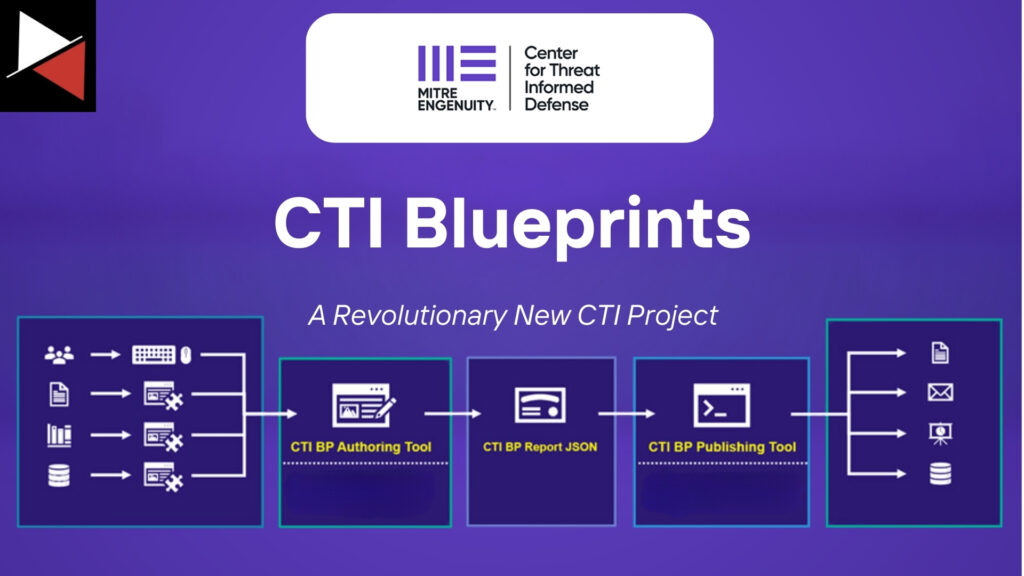
Cyber threat intelligence reporting is hard. You need to pinpoint who your intelligence is for, structure it in an easy-to-consume way for that audience, and make it actionable. However, the days of struggling with disseminating threat intelligence are over. Let me introduce you to CTI Blueprints.
This revolutionary new CTI project from the geniuses behind the MITRE ATT&CK framework aims to help CTI analysts tackle the challenges of creating consistent, actionable, and high-quality CTI reports. It provides a toolset to increase the operational relevance of reports and help analysts fulfill the intelligence requirements of their organization.
Let’s jump in and learn how a standardized set of templates and a couple of simple tools can change the CTI reporting game!
Learning Resources

Master Kubernetes Security
Check out this awesome blog post by the team at Red Canary. It outlines a security model you can use to enhance the security of your Kubernetes environment. With the widespread adoption of containers and cloud technology, learning to secure orchestration tools like Kubernetes is a must!
Detecting LOLBin Abuse
The team at Red Canary recently released a follow-up article to this great presentation on living off-the-land binaries (LOLBins). It details how popular malware and ransomware variants use LOLBins and how to detect them in your environment. It’s worth a watch for threat hunters and detection engineers!
Master the Linux xargs Command
Another great video by Tom Hudson (aka TomNomNom) in his ongoing series on Linux core utilities. This time he covers the xargs command, a tool that allows you to build and execute commands on standard input, making it one of the most powerful Linux tools to learn. Learning the core Linux utils will make you a better hacker, defender, and programmer. Get started learning them now!
Understanding Sysmon & Threat Hunting
Dive into the world of threat hunting using data collected via Sysmon. This excellent interview from Lawrence Systems discusses threat hunting, detection engineering, incident response, and how Sysmon can make a huge difference! It also demonstrates practical examples of using Sysmon to catch intrusion attempts.
10 Examples of AI in Cyber Security (Latest Research)
Let’s look at ten examples of AI in cyber security and discover why AI is a game-changing technology for the security industry. You will see how AI can be used across multiple cyber security domains, what makes it a good solution to existing problems, and the current tools using this technology.
This comprehensive roundup of AI use cases will help you understand the power of AI and why you need to adopt it into your workflow, tools, and daily life. This revolutionary technology will empower you to become a more efficient and effective cyber security professional.
Personal Notes

🤔 If you’re reading this newsletter or visited kravensecurity.co.uk recently, you would have seen our new email marketing efforts. We invested heavily last week into getting our email marketing right to deliver you high-quality content tailored to your needs. This was a big effort, but we are pleased with the initial results. The team is still testing and smoothing out any bumps, so if you spot any hiccups, please let us know.
Aside from getting our email upgraded, we have been busy testing new threat intelligence and threat hunting tools we believe will provide you with value. This includes this week’s feature article on MITRE’s CTI Blueprints as well as upcoming articles on malware configuration parsers, Netlas.io, and more. We hope you enjoy playing with these tools as much as we did and can integrate them into your workflow.
Have a great weekend!


