There are a lot of challenges with indicators. The sheer quantity can be overwhelming, collecting good ones can be difficult, and knowing how to use them effectively is confusing.
This article explores the challenges you will face when using indicators during your cyber security operations and how you can overcome them through planning, foresight, and cyber threat intelligence best practices. Challenges will be highlighted, solutions will be explained, and you will discover how to use indicators productively to improve your organization’s cyber security posture.
Let’s start with a quick refresher on indicators and their importance in cyber security.
Indicators Recap
Before diving into the challenges you will face when using indicators, let’s recap what indicators are and why they are important to cyber security operations.
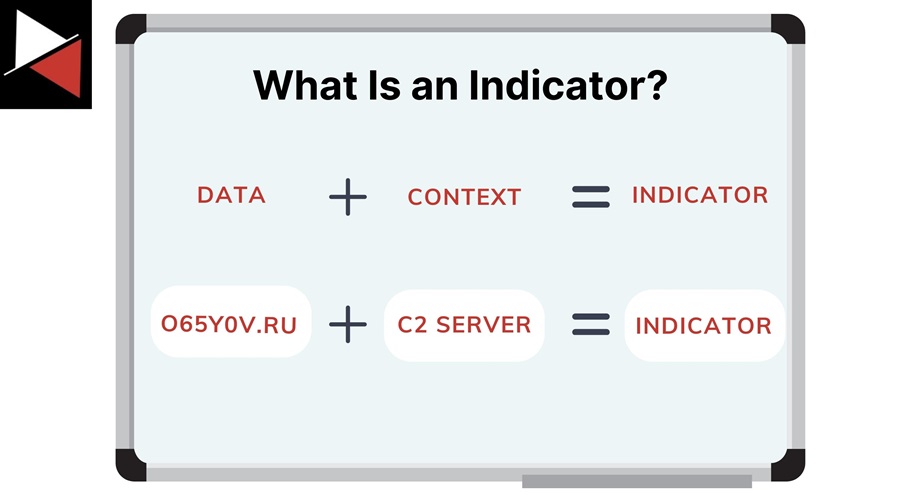
Indicators are data and context. Combined, these two pieces of information are evidence that suggests a potential security threat, malicious activity has occurred, or a data point needs to be investigated. For example, you may find a domain name in a log file and correlate it with a well-known Command and Control (C2) server using threat intelligence. This domain name would then become an indicator that warrants further analysis or response.
An indicator does not necessarily mean malicious activity has occurred. You may find a file hash relating to a popular remote access tool like AnyDesk. This could suggest several potential scenarios:
- An attacker is using AnyDesk to maintain persistence in your environment and exfiltrate data.
- An employee has installed AnyDesk for a business use case.
- AnyDesk is a company-wide technology that allows employees to work from home.
- An employee installed AnyDesk for a one-off task and forgot to install it.
Not all of these are malicious. Some increase your attack surface and are bad security practices, while others are business requirements. As a threat hunter or security analyst, you must investigate each scenario and perform root cause analysis.
Not all indicators are created equal. Indicators that remain consistent across intrusions, uniquely distinguish an attack campaign, and align to a phase of the Cyber Kill Chain are known as “Key Indicators.” These indicators are the most valuable and will allow you to write detection rules, trigger intelligence-driven threat hunts, and track adversary campaigns.
There are several different types of indicators. Knowing these types will allow you to align your intelligence requirements with the indicators you consume.
Atomic Indicators
A singular, discrete piece of information that serves as evidence or a clue of potentially malicious activity. They are the most granular indicator type and require the most context to determine if they are malicious. Examples include IP addresses, domain names, URLs, and email addresses.
Computed Indicators
These are calculated pieces of information based on the raw data of atomic indicators, the contents of a file, or correlation with other data points. Examples of these indicators include file hashes, behavioral anomalies, and alert thresholds.
Tactics, Techniques, and Procedures (TTPs)
These are behavior-based indicators that represent an adversary’s action. For instance, if someone runs several commands to check their hostname, user privileges, and file access, this is an indicator of host reconnaissance. You can learn more about TTPs in MITRE ATT&CK Framework: The Holy Bible of Threat Intelligence.
Indicators of Compromise (IOCs) and Indicators of Attack (IOAs)
These are the indicators you hear the most about. They are shared in threat intelligence reports, included in security adversaries, and are the starting point for most investigations. These indicators suggest a system has been compromised or an attack has occurred. They can be atomic, computed, or TTP indicators.
Now that you understand indicators (and why they are important), let’s examine the main challenges they present and strategies for overcoming them.
Challenges With Indicators
Despite the benefits indicators can provide, many cyber security professionals fail to utilize them effectively. This ineffective usage arises from a lack of understanding of how an adversary operates, improper use of the indicator lifecycle, or a lack of critical thinking, leading to the following challenges:
- Indicator overload
- Collecting key indicators
- Falling into rabbit holes
- Using indicators efficiently
- Sharing indicators with others
Indicator Overload
There are many indicators out there. Nearly every threat intelligence report will include a long list of IOCs related to a campaign, threat actor, or malware. This sheer volume of data can become overwhelming and bog a security team down in a never-ending battle to identify genuine threats from background noise.
If you try to collect them all or lack efficient data analysis processes, you will struggle to effectively use any indicators you collect. They will become more of a hindrance than an advantage.
Solution
You must focus on intelligence relevant to your organization and its threats to avoid becoming bogged down in indicators. This means you first need to define your intelligence requirements (the gaps in knowledge you must fill to protect your organization) and create a threat model that accurately represents your organization’s security risks.
Intelligence requirements and threat modeling are cornerstones of any successful cyber threat intelligence program. They will help guide you in collecting intelligence and searching for indicators in your environment. However, you also need an efficient process for ingesting this intelligence. This is where automation comes in.

If you work for an organization of any substantial size, you need automation to claw back valuable man-hours that can be dedicated to more important activities, like analysis or development. For indicators, this means automating collection and processing.
You can use tools like MISP to automatically ingest threat intelligence feeds and add indicators to your CTI database or create a custom CI/CD pipeline to verify indicators are legitimate and push them to your security tools for detection. How you automate the collection, processing, and deployment of indicators will depend on your intelligence requirements, team skillset, and available security tools.
Collecting Key Indicators
You want to prioritize collecting key indicators. They allow you to track adversaries and campaigns, write effective detection rules, and uniquely distinguish malicious behavior. Unfortunately, collecting key indicators can be difficult. Many analysts struggle to differentiate a regular indicator from a key indicator or don’t know where to find key indicators.
This is a problem for CTI teams because, without key indicators, it is very difficult to characterize attack campaigns, separate intrusions, or identify a specific threat actor’s activity.
Solution
Identifying key indicators requires analysts to know where to look for them and what they look like. Firstly, creating a Collection Management Framework (CMF) that analysts can use to identify available data sources and what information they can get from them goes a long way.
A central CMF will allow your team to know what questions they can ask during an investigation based on the available data, where it is, and how accurate it is. Key indicators will usually come from malware and intrusion analysis. These data sources are specific to you and are a good place to highlight your CMF.
Once you have created a CMF, you can tackle the challenge of training your team to identify key indicators. Here are some tips for things to look for:
- Uniqueness: Key indicators should be unique in that they can be distinguished from generic malicious activity, malware functionality, or attacker behavior. For instance, they could be specific mutex, custom malware, or command-line arguments used by a single attacker.
- Consistency: These indicators must be consistent across intrusions to group them into a campaign or attribute to a threat actor.
- Non-default: Look for cases where non-default values were used during an intrusion, whether in malware configuration data or when using living-off-the-land tools. This indicates a choice made by an attacker and can be tracked as a key indicator.
- Aligns to other indicators on the cyber kill chain: Key indicators usually align with other indicators seen during an intrusion. When analyzing an intrusion, you will use the cyber kill chain or MITRE ATT&CK matrix to map indicators to different stages of an attack. If you come across one indicator that consistently predicts you will encounter another at a different stage of the same attack, this is likely a key indicator.
Tracking indicators in a threat intelligence platform (e.g., MISP, OpenCTI, etc.), looking for correlations, and performing basic data analysis will help you identify key indicators over a longer time horizon.
Rabbit Holes
A big mistake analysts make when using indicators is falling into a rabbit hole. The indicator lifecycle dictates that you (a) find an indicator, (b) operationalize it, and (c) this process reveals more indicators. Unfortunately, indicators beget indicators. If you start with a good indicator, you will find more good ones to pivot to. But if you start with a bad one, you will fall down a slippery slope of chasing bad indicators that hinder your investigation.
If you fail to critically assess the indicators you are gathering, you will waste valuable investigation time chasing rabbit holes in the data.
Solution
There are three steps you can take to ensure you don’t fall down the rabbit hole of collecting bad indicators or just constantly collecting indicators without actioning them:
- Use good data sources: The best sources are your own (e.g., your logs). Look for indicators through these sources first, then move on to external threat intelligence that you have thoroughly reviewed and are relevant to your industry, geography, and niche. Again, using a CMF can help here.
- Follow the Indicator Lifecycle: The lifecycle is a structured approach to deriving the most value from the indicators you collect, ensures you action the intelligence you gather, and will help you make progress during an investigation.
- Ensure indicators align with your intelligence requirements: Indicators are useless if they are not relevant, timely, and actionable. If they do not help you fulfill one of your intelligence requirements, move on.
Using Indicators Effectively
Security analysts fail to use indicators effectively for a variety of reasons:
- They fail to understand how an attacker operates and the control the attacker has over an indicator.
- They don’t recognize what an indicator actually represents.
- They focus on quantity rather than quality.
- They over-rely on low-level indicators.
These failures often result in analysts stockpiling low-value indicators and hunting for thousands of indicators daily, or worse, creating detection rules out of them.
Solution
Let’s look at how to overcome each of these failures in turn:
- Defenders need to realize that an attacker will dictate an indicator’s value and lifetime. Attackers frequently change TTPs, infrastructure, and malware to avoid getting caught. This means you need to focus on indicators that are more difficult for an attacker to change by targeting ones higher up the Pyramid of Pain.
- You need to understand what an indicator represents and how easy or hard it is for an attacker to change it. Atomic indicators like hash values, IP addresses, and domain names are relatively easy to change, so stockpiling your IOC list with these is not optimal. However, TTPs are much more difficult to change, so focus on behavior indicators.
- Having a massive list of atomic IOCs that an attacker can easily change is far less valuable than having several key indicators that an attacker consistently uses.
- Again, don’t rely on low-level atomic indicators that can be easily changed; retire indicators when they are no longer valuable. Searching for a large list of low-level IOCs and finding nothing can give you a false sense of security.
These observations often lead to the conclusion that you should use atomic and computed IOCs as fishing bait and focus your threat hunts and detection rules on key indicators.
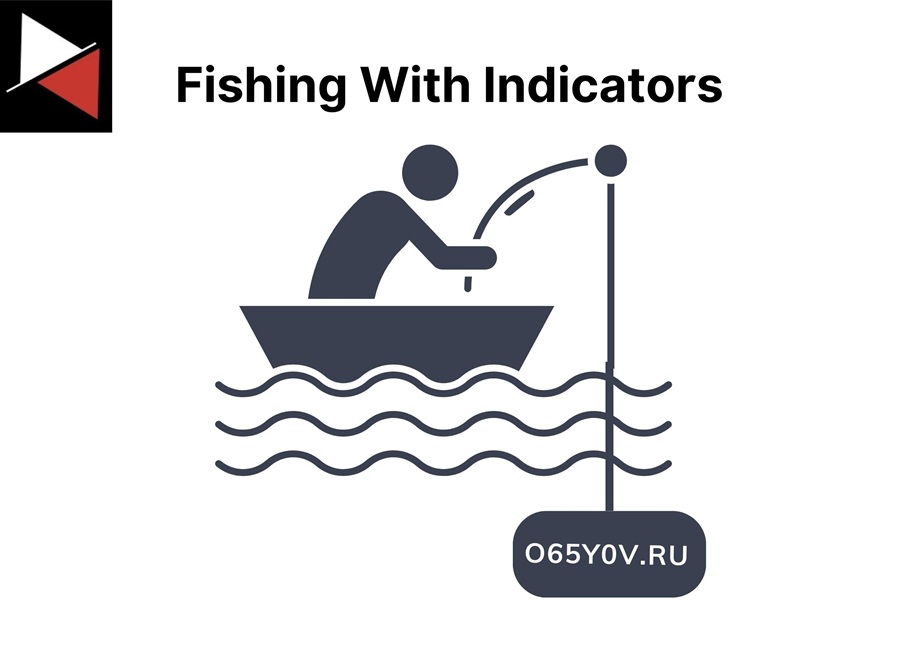
In this approach, you gather a list of relevant IOCs, attach them to a single hunting query, and run that query once against all your systems (daily or weekly). You can choose to use only the indicators you collected that day, that week, or that month. Beyond this, you will have too many indicators.
Indicators have a shelf life, and their value degrades over time, so retire indicators when they are no longer useful. An attacker dictates the shelf life of all indicators. Once an attacker changes their indicators, you must forget their past indicators and focus on their new ones.
Sharing Indicators
Sharing threat intelligence is a challenge all CTI teams face. Indicators are no exception. It can be difficult to agree on what indicators should be shared and with what context based on their sensitivity and uniqueness to your organization. It can be difficult to share indicators fast enough to have any value to the recipient. It can even be difficult being the recipient of shared indicators to know if they will generate too many false positives in your environment.
Sharing indicators is difficult. It takes some planning to get it right to avoid over-sharing, under-sharing, and using shared indicators effectively.
Solution
Sharing indicators is always difficult and depends on both the organization sharing and the recipient to ensure the effective distribution of intelligence. Here are some solutions that can be helpful:
- Use a threat intelligence platform: CTI platforms allow you to automatically collect indicators from threat intelligence feeds and share your indicators with others through mechanisms like sharing groups and synchronization. Automating sharing makes it easier for everyone involved, and a platform like MISP allows you to set rules about what gets shared, with whom, and how with tagging.
- Use tools that help you with CTI reporting: Threat intelligence reporting has been like the Wild West for years. Thankfully, a recent project by MITRE Engenuity has brought some order to this chaos in the form of CTI Blueprints. This project aims to improve the distribution and sharing of CTI using structured templates and automation tools. It raises the quality of reporting, provides a standardized process, and makes it easier to share indicators.
- Verify indicators: Many novice cyber security analysts overlook verifying indicators they collect from third-party intelligence providers. Just because an indicator is included in a threat intelligence report does not mean it is malicious! Often, reports will contain legitimate executables or domains used as part of an attack campaign. If you add these to your IOC list, you will generate a lot of false positives.
Conclusion
To use indicators effectively, you will need to overcome several significant challenges. This article covered five main ones: indicator overload, collecting key indicators, rabbit holes, using indicators effectively, and sharing indicators.
It also detailed solutions that can help you overcome these problems. These focused on aligning indicators with your intelligence requirements and threat model, using threat intelligence platforms to automate processing and sharing indicators, and better understanding how to assess and use indicators effectively.
I highly recommend trying some of the solutions outlined in this article and discovering what allows you to best utilize the indicators you collect. For a comprehensive guide to indicators, read What Is the Indicator Lifecycle? A Guide to Using Indicators.
Frequently Asked Questions
What Makes a Good Indicator?
Like all good cyber threat intelligence, a good indicator must be relevant, timely, and actionable. To meet these requirements, you must have defined your intelligence requirements and have a comprehensive threat model that helps you identify and prioritize threats your organization faces. These two documents will help you determine whether an indicator is relevant and worth searching for in your environment.
Why Are Indicators Important?
Indicators are quick and easy wins for defenders. If an attacker uses the same malware, infrastructure, or TTPs to attack multiple organizations, you can quickly detect them using indicators shared through threat intelligence reports. Regardless of size, all organizations should use indicators to address common cyber threats, trigger threat hunts, and build detection rules.
What is a Key Indicator?
Key indicators are the most valuable form of indicator you can find. They remain consistent across intrusions, uniquely distinguish an attack campaign or attacker, and help you track threats. You can use these indicators to write detection rules, trigger intelligence-driven threat hunts, and track adversary campaigns.




