There is a new way to unlock the awesome power of MITRE ATT&CK…, and it’s in your web browser. Let me introduce you to the ATT&CK Powered Suit!
The ATT&CK Powered Suit is a free web browser extension that provides easy access to the vast knowledge base of the MITRE ATT&CK matrix. It allows you to quickly research the tactics, techniques, and procedures (TTPs) you encounter daily as a cyber security professional without disturbing your workflow.
This guide will show you how to install this awesome browser extension, showcase its key features, and highlight several use cases where the ATT&CK Powered Suit shines. Let’s get started by exploring what makes this application so great!
What is the ATT&CK Powered Suit?
The ATT&CK Powered Suit is a project from MITRE Enginuity’s Center for Threat-Informed Defense (the great people who brought you CTI Blueprints, the ATT&CK Navigator, and recently MITRE ATLAS for securing AI systems).
It aims to streamline the process of using the MITRE ATT&CK knowledge base by reducing the friction between finding an attack method or ATT&CK technique ID in a cyber threat intelligence report and then researching it.
In the past, you would have to find the attack technique you wanted to research in the threat report, copy the ATT&CK ID, open a new tab, navigate to https://attack.mitre.org/, and search for that technique to find information about it (or worse yet, try to find the technique just using its name). This process was slow, tedious, and annoying. But no more!
The ATT&CK Powered Suit puts the entire ATT&CK knowledge base at your fingertips so you can quickly search for tactics, techniques, and more without disrupting your workflow. You click on the extension in your browser’s toolbar and search for any ATT&CK-related knowledge you want. This includes:
- Tactics
- Techniques
- Sub-techniques
- Campaigns
- Mitigations
- Software
- Groups
- Data sources
It even lets you search for this data across the Enterprise, Industrial Control Systems (ICS), and Mobile ATT&CK matrices!
This is a game changer for cyber threat intelligence (CTI) analysts who need to quickly reference the MITRE ATT&CK knowledge base when triaging a threat report, writing an assessment, or performing technical analysis. It keeps you in the “zone” whether you are consuming or generating intelligence.
Sounds good? Let me show you how to get started using this powerful tool.
Installing the ATT&CK Powered Suit
Installation is simple. Go to your favorite web browser’s extension store, search for “ATT&CK Powered Suit,” and install it in less than a minute.

Here, I have installed the extension on Firefox.
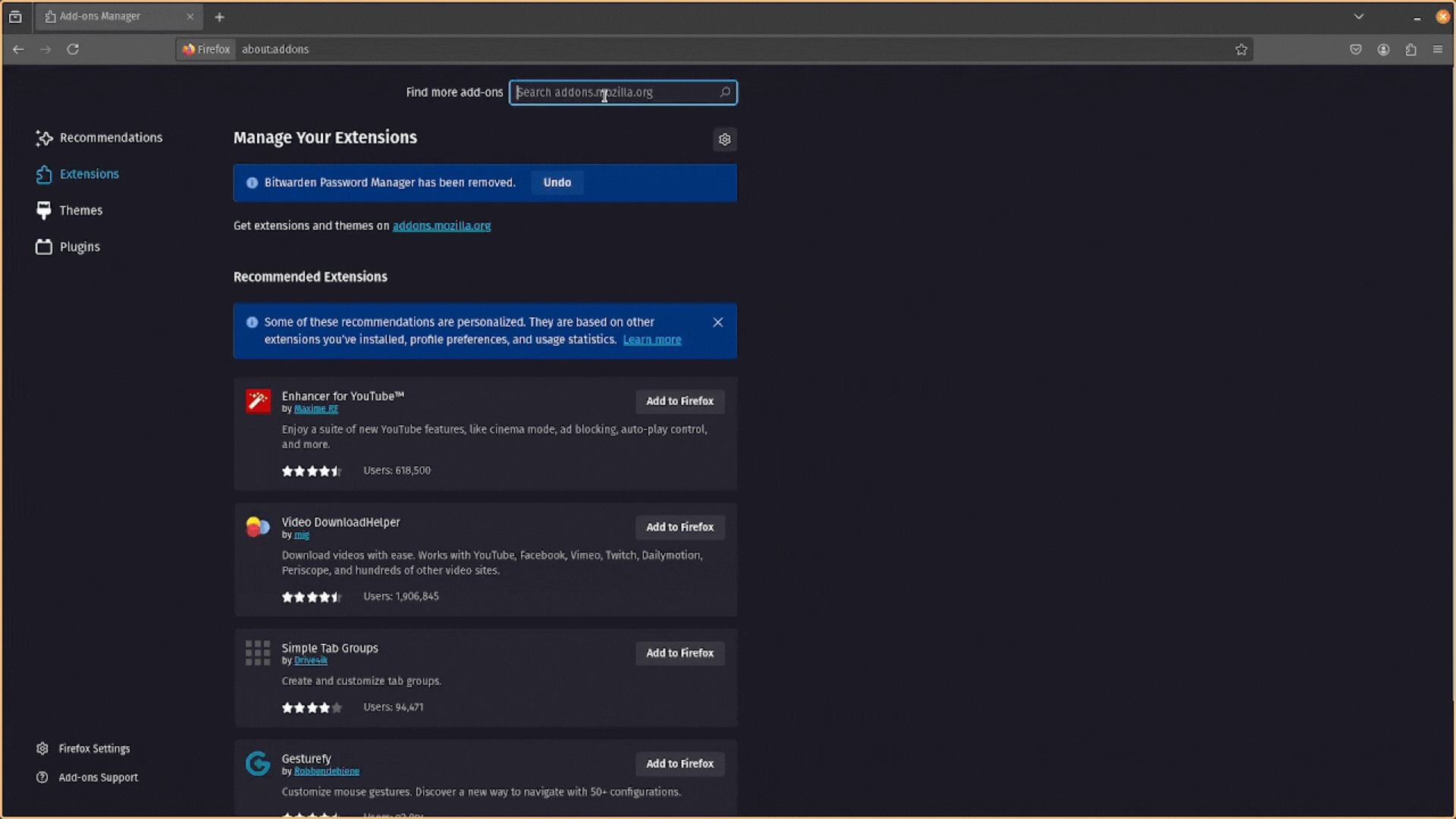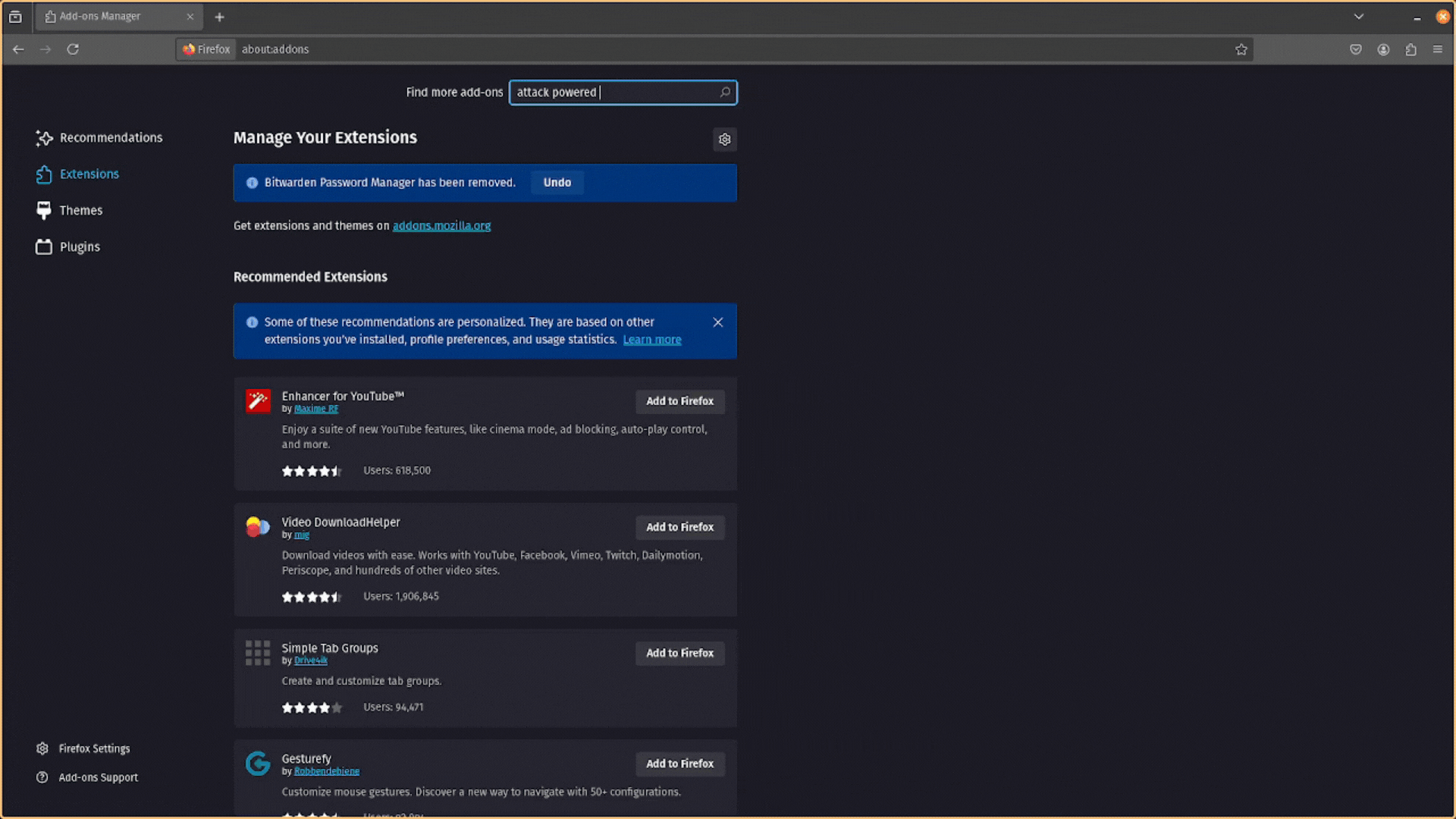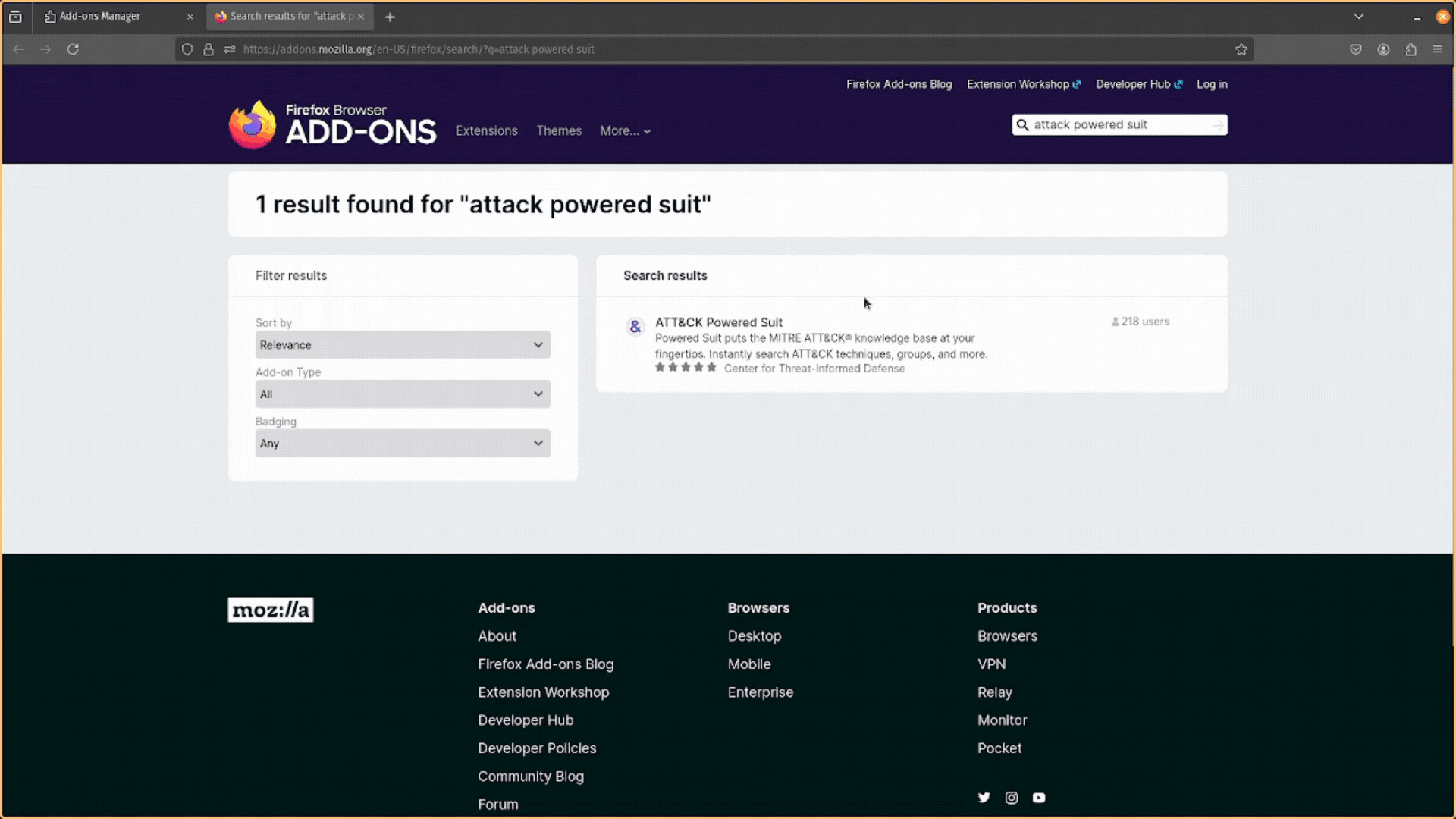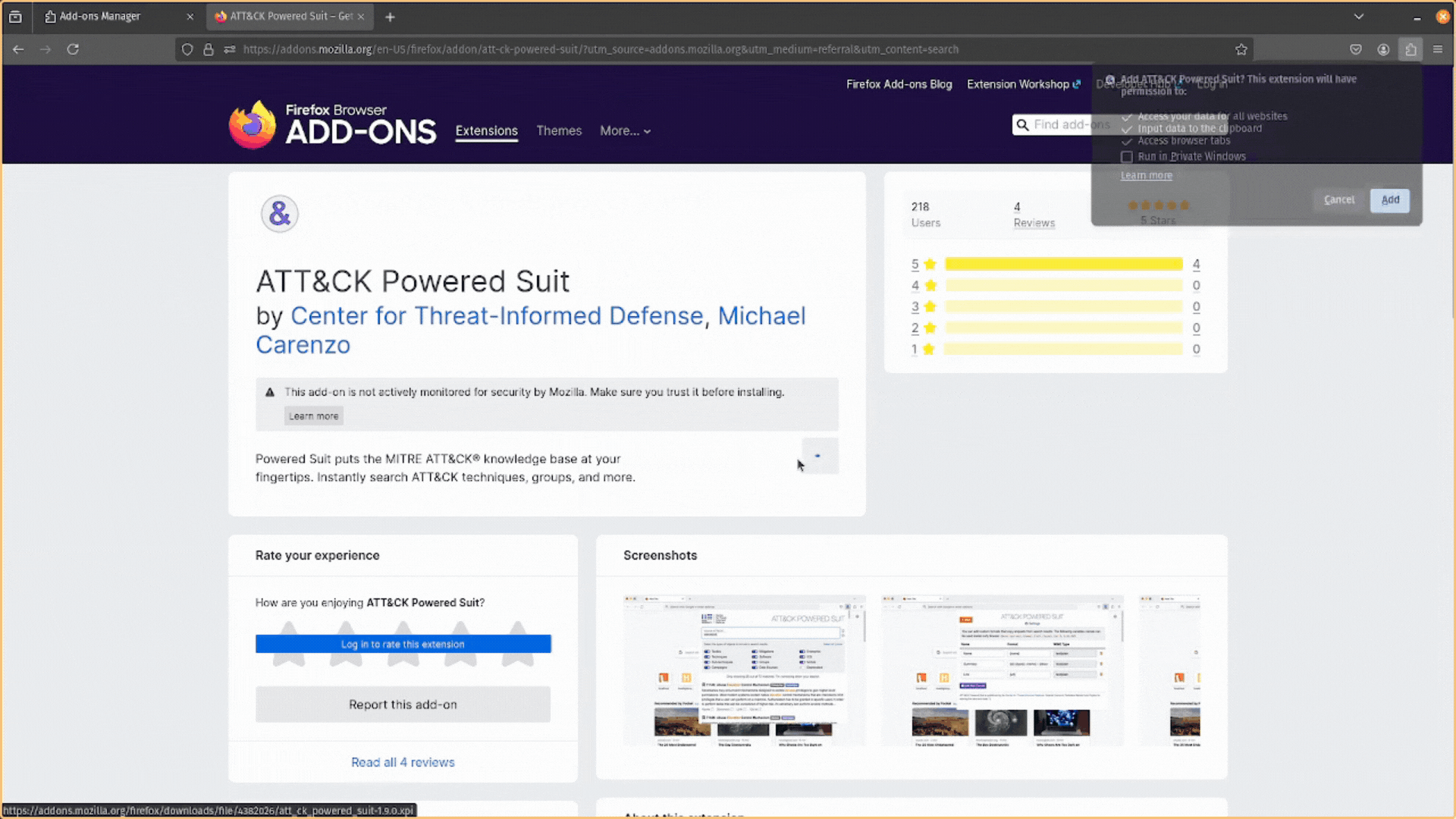
Once installed, make sure you add (or pin) the extension to your browser’s toolbar so you can quickly access it.
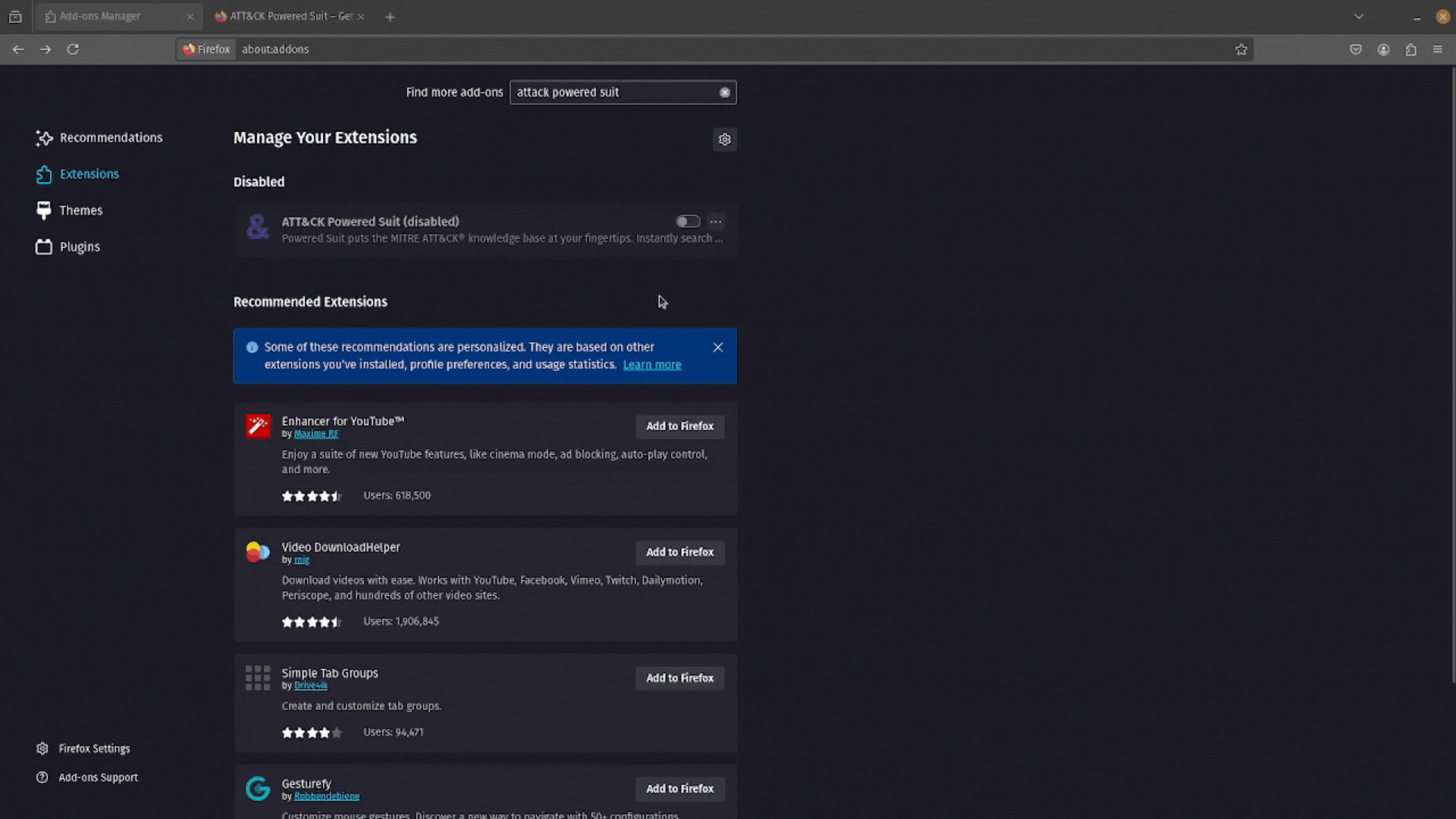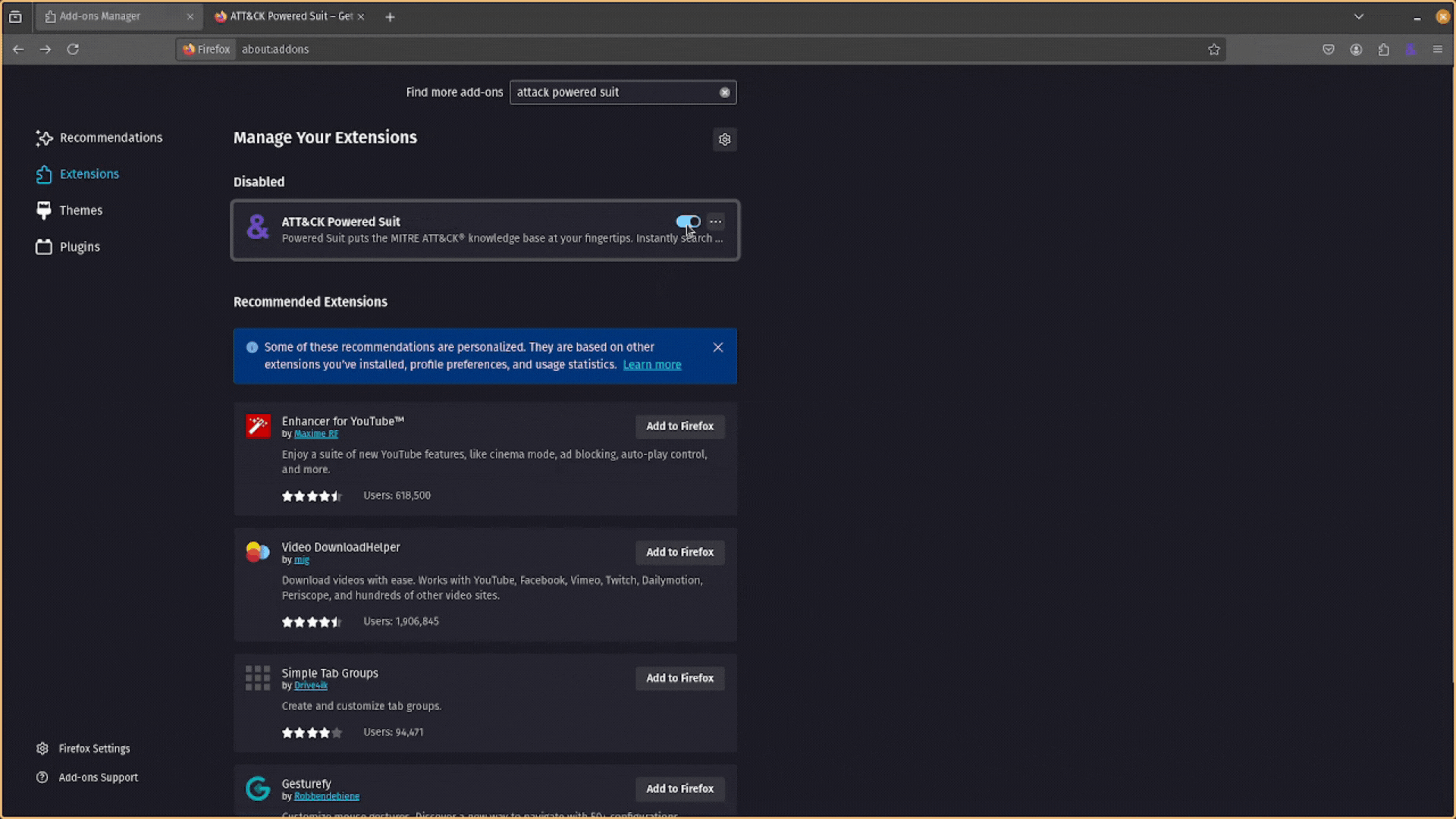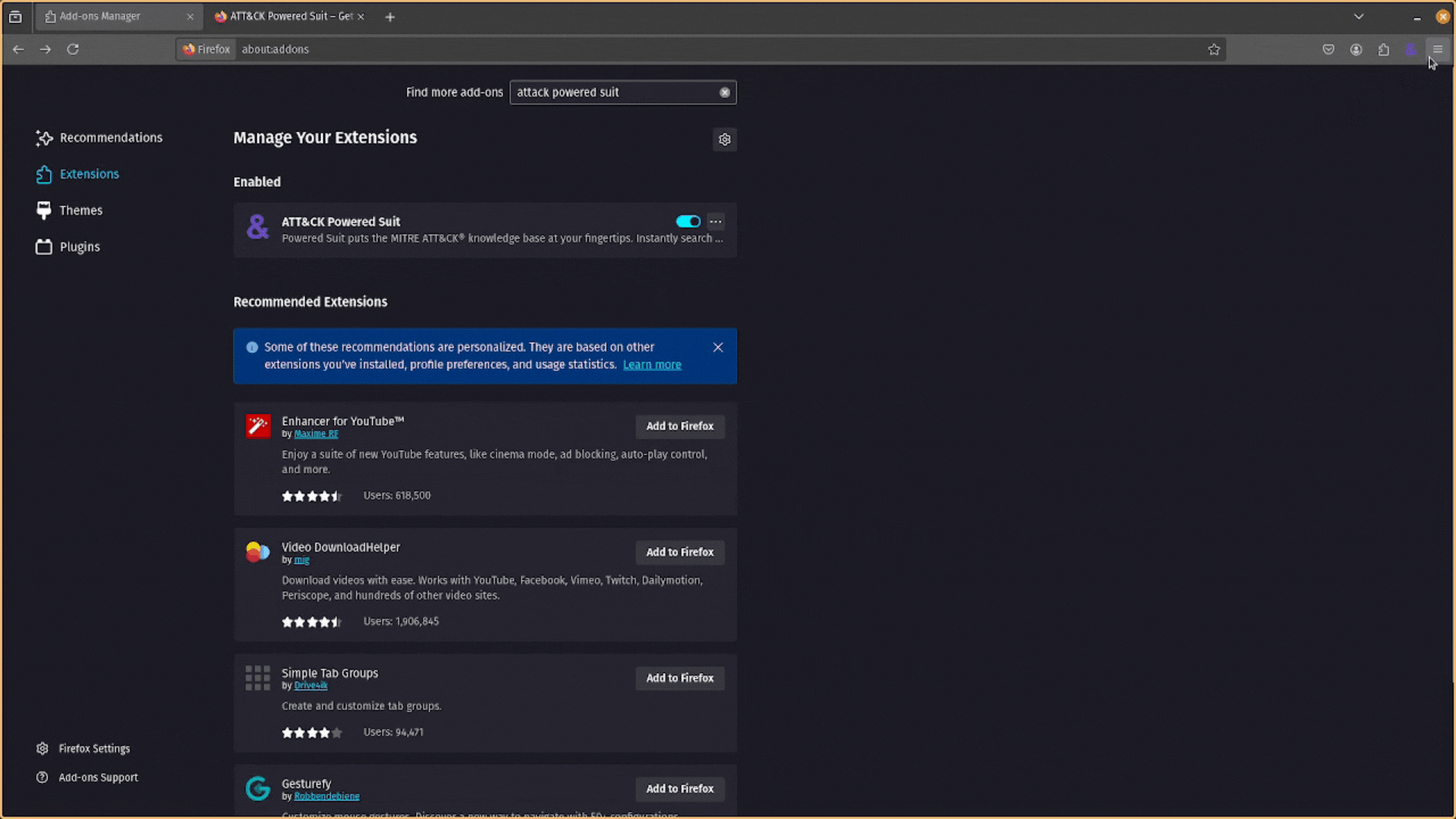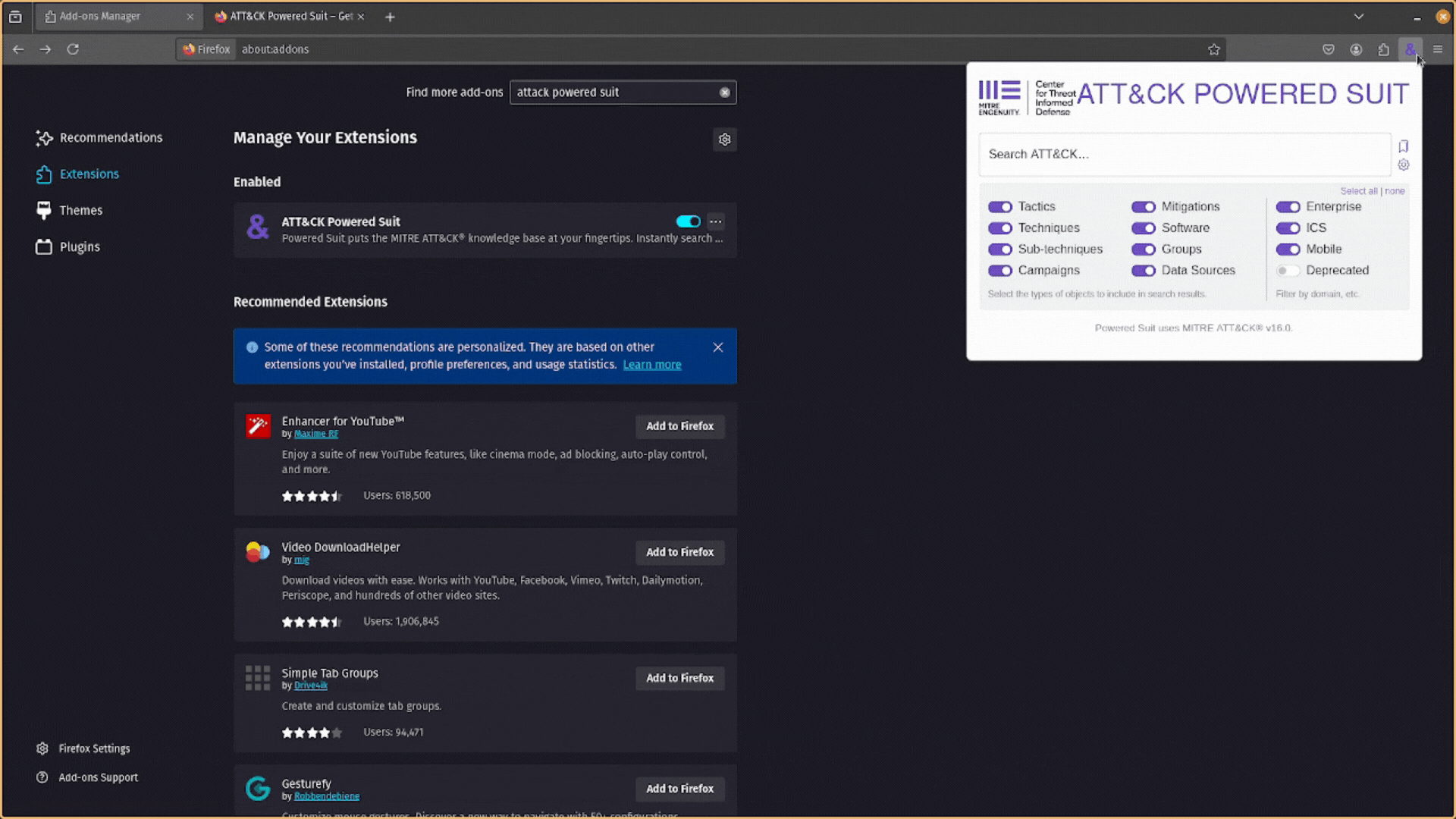
Perfect. Now, you can click on the ATT&CK Powered Suit extension to open a popup window and search for TTPs.

With the extension installed, let’s look at what it provides you!
Key Features of the ATT&CK Powered Suit
The ATT&CK Powered Suit is packed with awesome features that will save you valuable time when triaging intelligence reports or generating your own. Each of these features aims to bridge the gap between the knowledge in MITRE ATT&CK and you finding it so you can streamline your research. Here are the top features you should make use of.
Searching Through the Extension
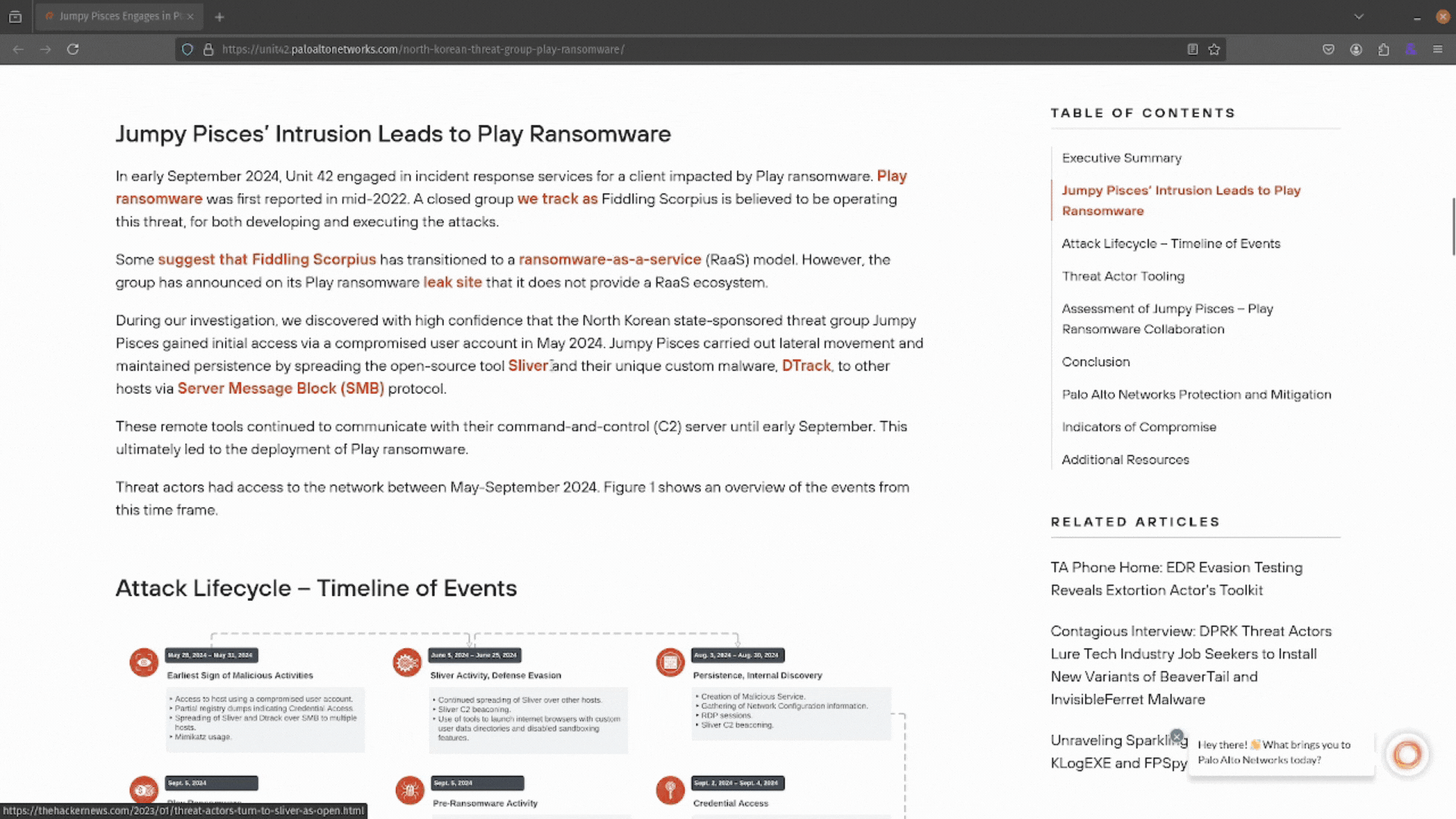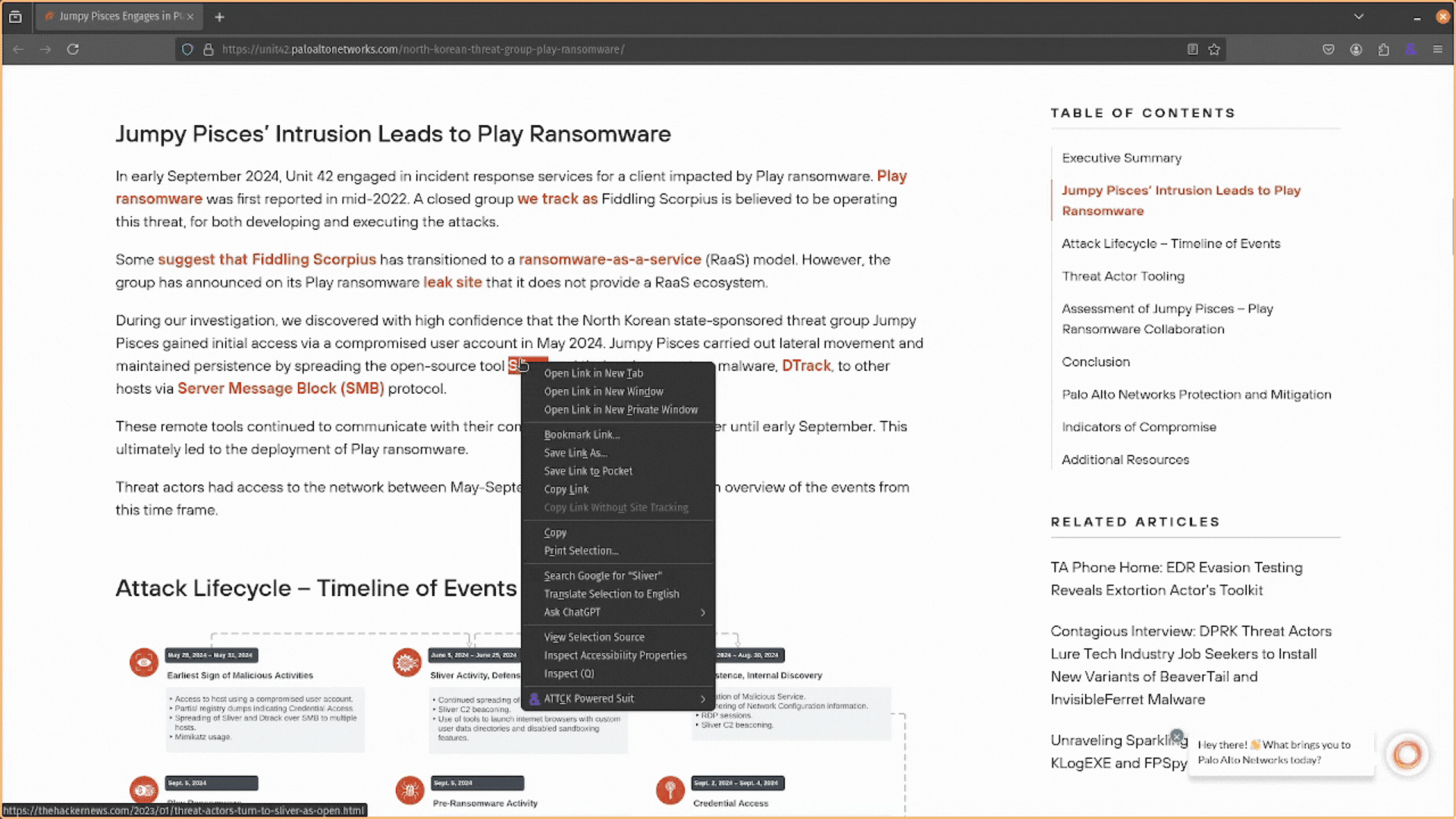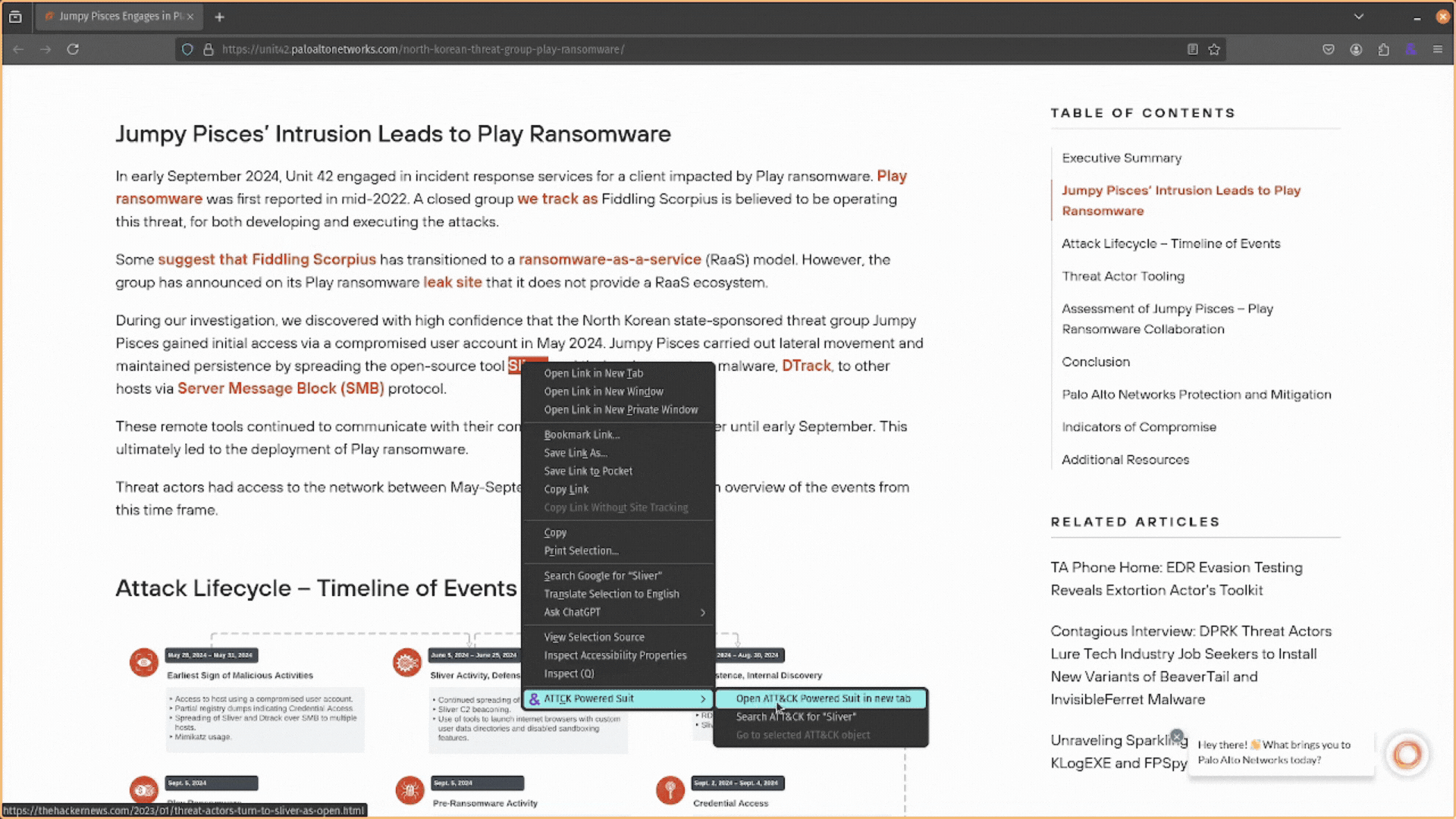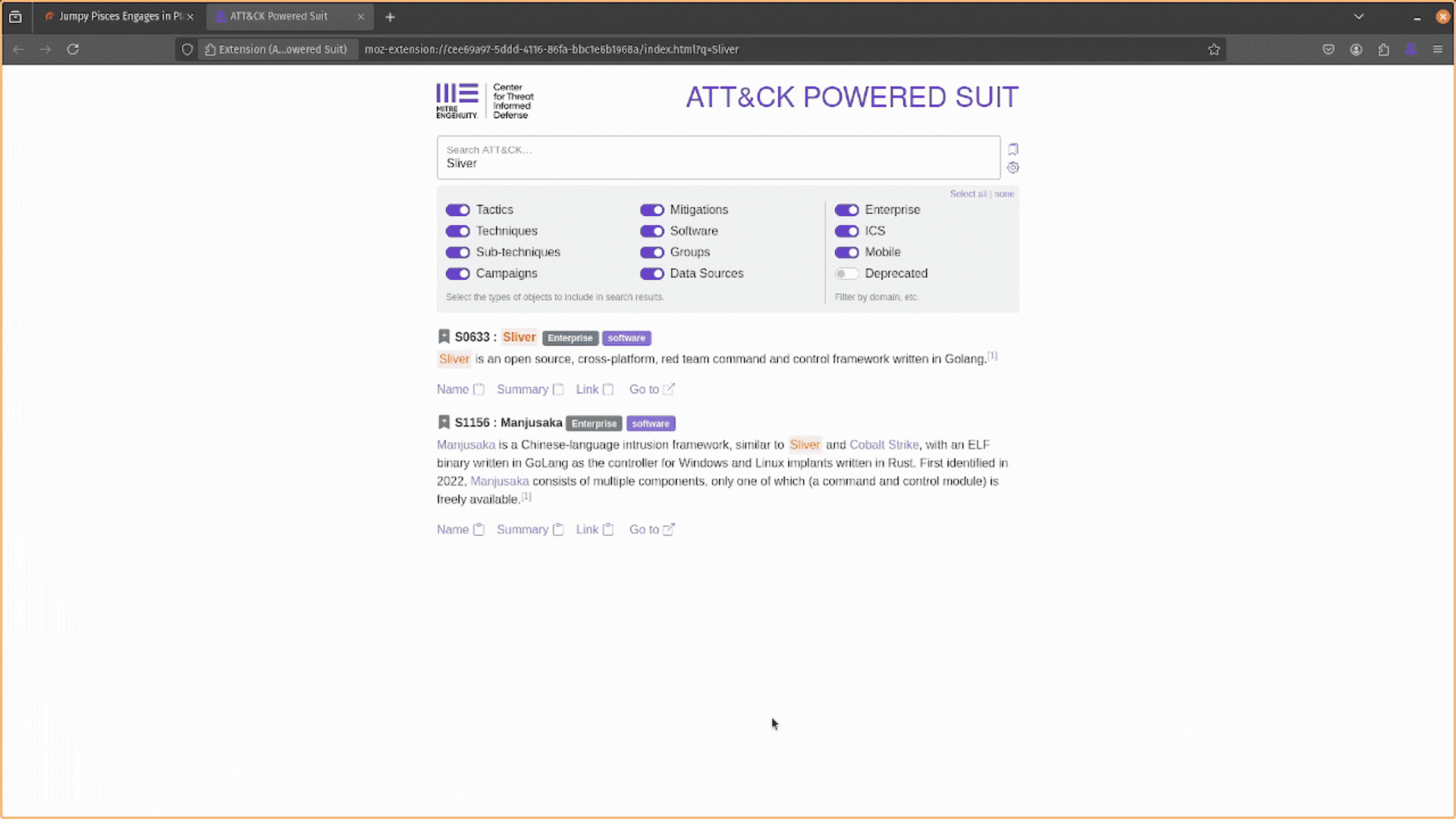
The basic way to use the ATT&CK Powered Suit is to click on the extension in your browser’s toolbar to reveal the popup window and then search for an attack technique using the technique’s name or ATT&CK ID.

This will populate the popup window with a list of search results. Each result includes a snippet of text under its name that provides more details. This lets you quickly identify if this attack technique (group, mitigation, or software) is relevant to you.
Underneath the description are several buttons that provide further functionality:
- Name: Copies the name of the ATT&CK technique, group, mitigation, or software to your clipboard.
- Summary: Copies the description.
- Link: Copies a link to the ATT&CK technique, group, mitigation, or software on the https://attack.mitre.org/ website to your clipboard.
- Go to: Opens the link to the ATT&CK technique, group, mitigation, or software in a new tab.
These buttons are useful for quickly using your search results or finding more information in the MITRE ATT&CK knowledge base.

Searching through the popup window is the simplest way to use the ATT&CK Powered Suit extension. There are more powerful ways to integrate the extension into your workflow, so let’s look at those.
Highlight Searches
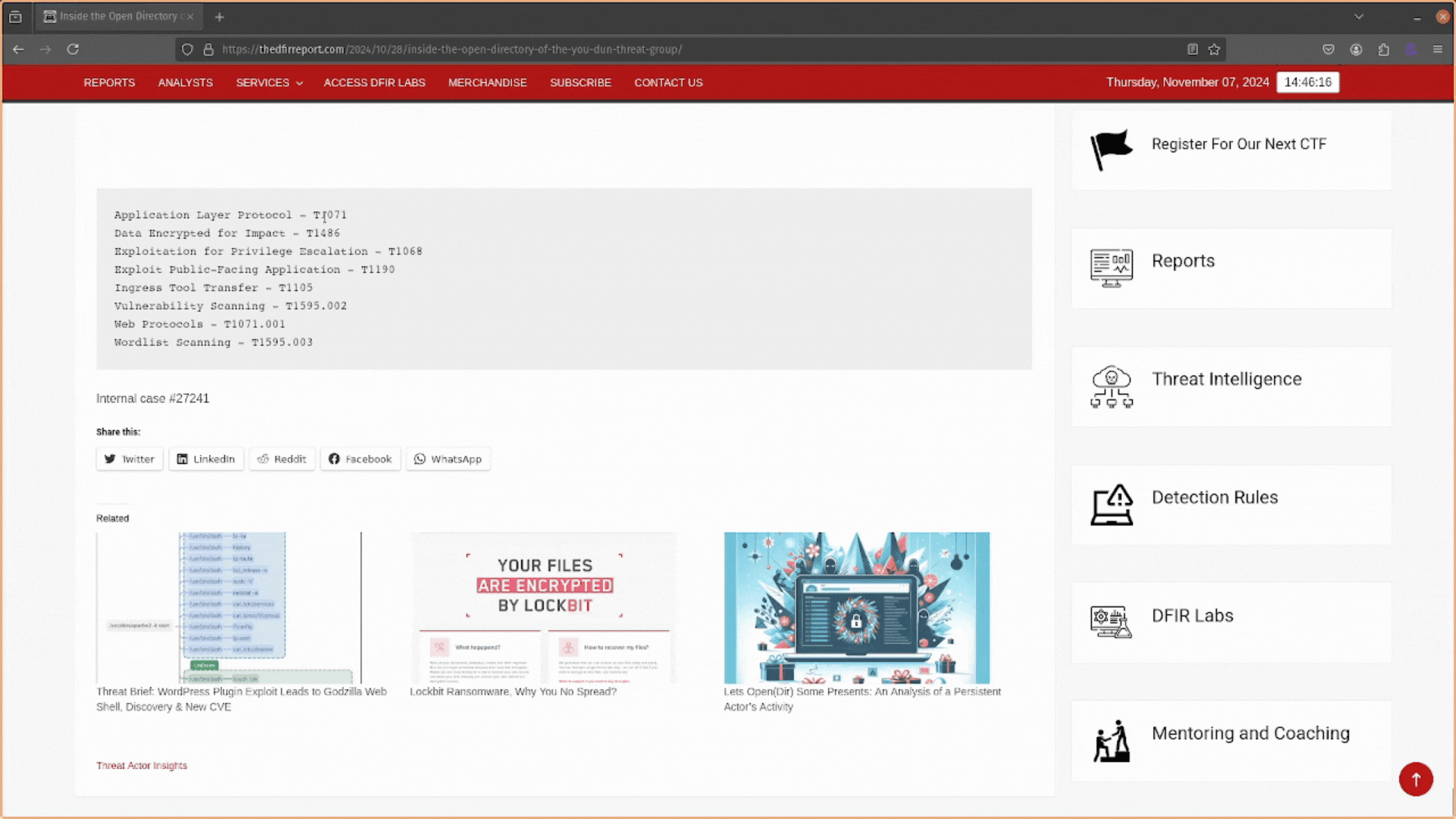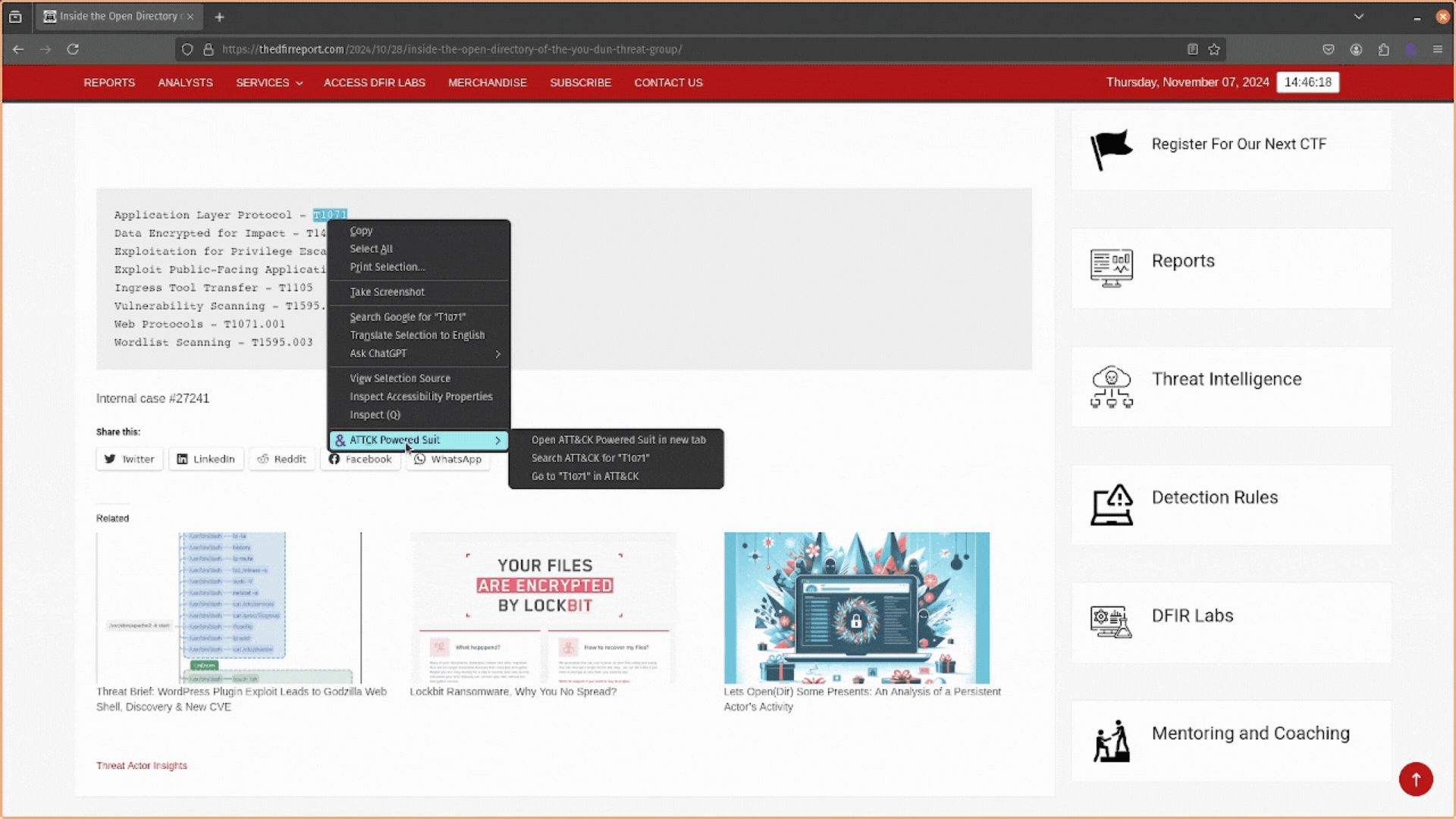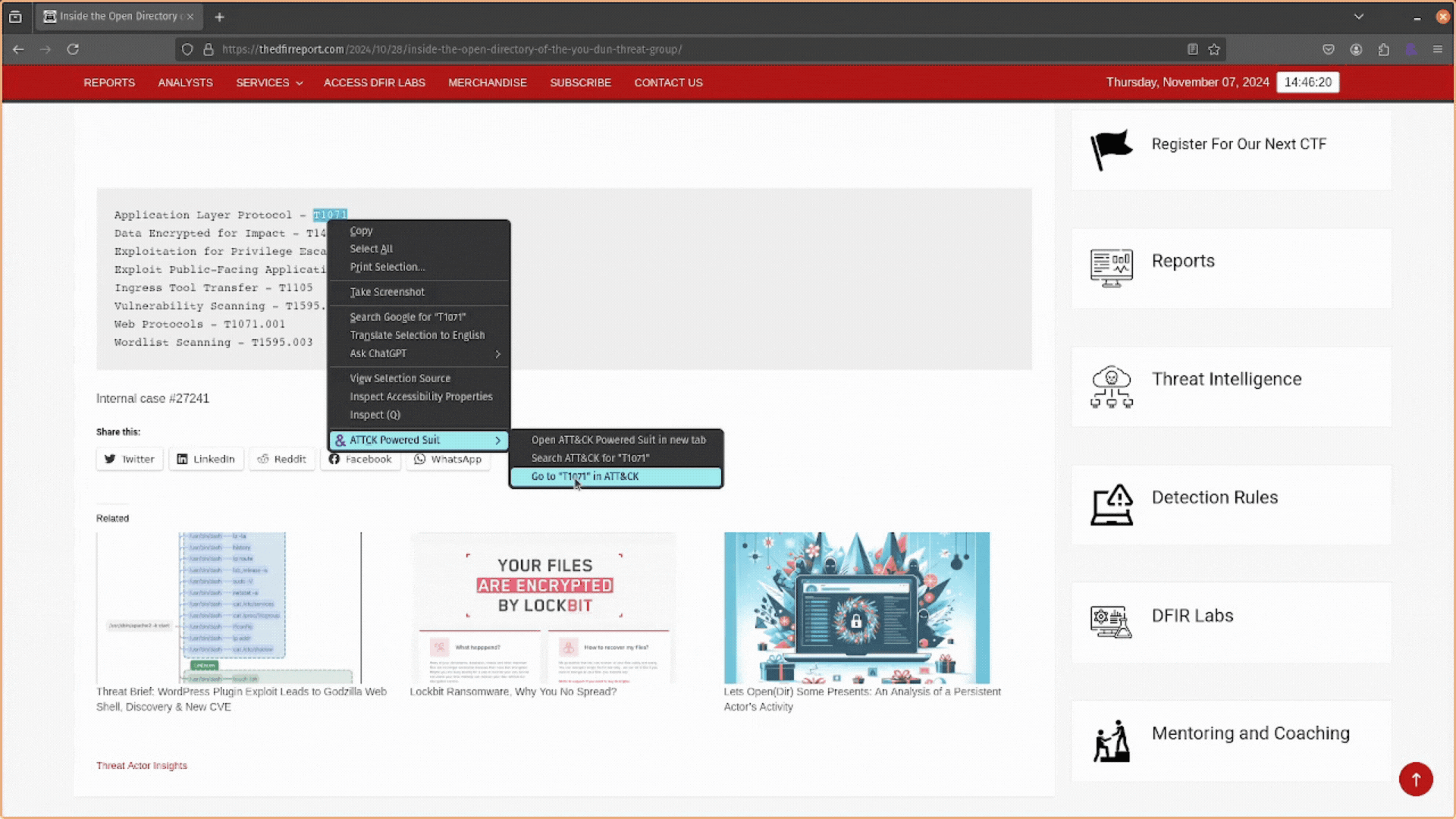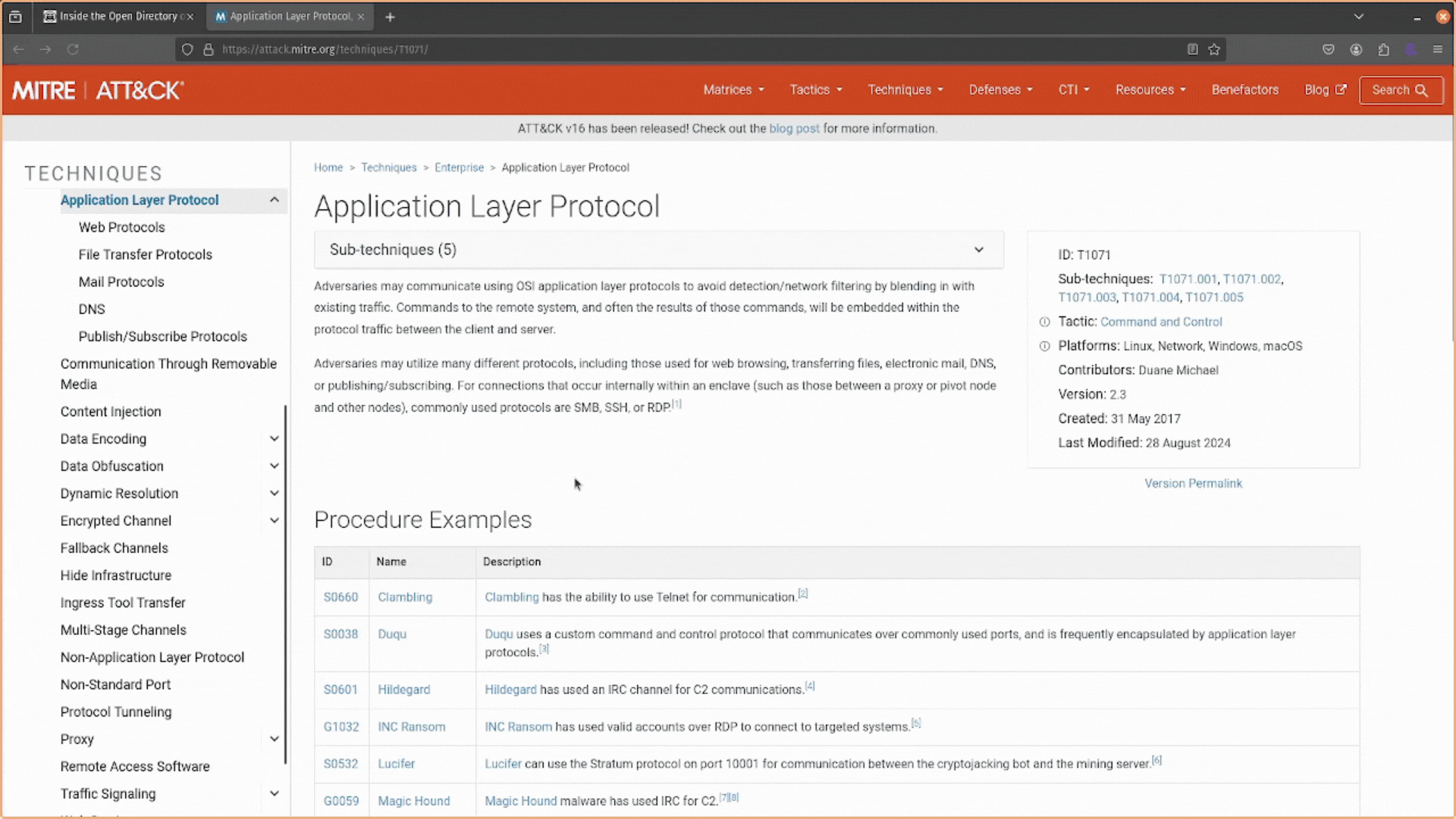
The ATT&CK Powered Suit does not limit searches to the popup window. It also allows you to search for attack techniques by highlighting them in threat intelligence reports, right-clicking, and selecting the ATT&CK Powered Suit option.
This will provide you with several options:
- You can use Open ATT&CK Powered Suit in new tab to open a new tab with the extension loaded and ready to search for attack techniques.
- You could use Search ATT&CK for “…” to open a new tab and search for the highlighted keyword using the extension.
- Or, if you highlight an ATT&CK ID, you can open that up directly on the https://attack.mitre.org/ website with the Go to “<ATT&CK ID>” in ATT&CK.
But there is more! You can search for ATT&CK techniques, groups, mitigations, or software directly in your web browser’s search bar.
The Omnibar
The Omnibar (omnibox) is your browser’s combined address and search bar. It allows you to enter web addresses or search for terms in one convenient place. No more navigating to google.com to search for cat pictures.
The best thing about the Omnibar is that it allows browser extensions to use its functionality. You can search through your Google Drive, connect to an SSH host, manage an Amazon EC2 instance, and more. The ATT&CK Powered Suit comes with Omnibar support, so you can use it to search for attack techniques!
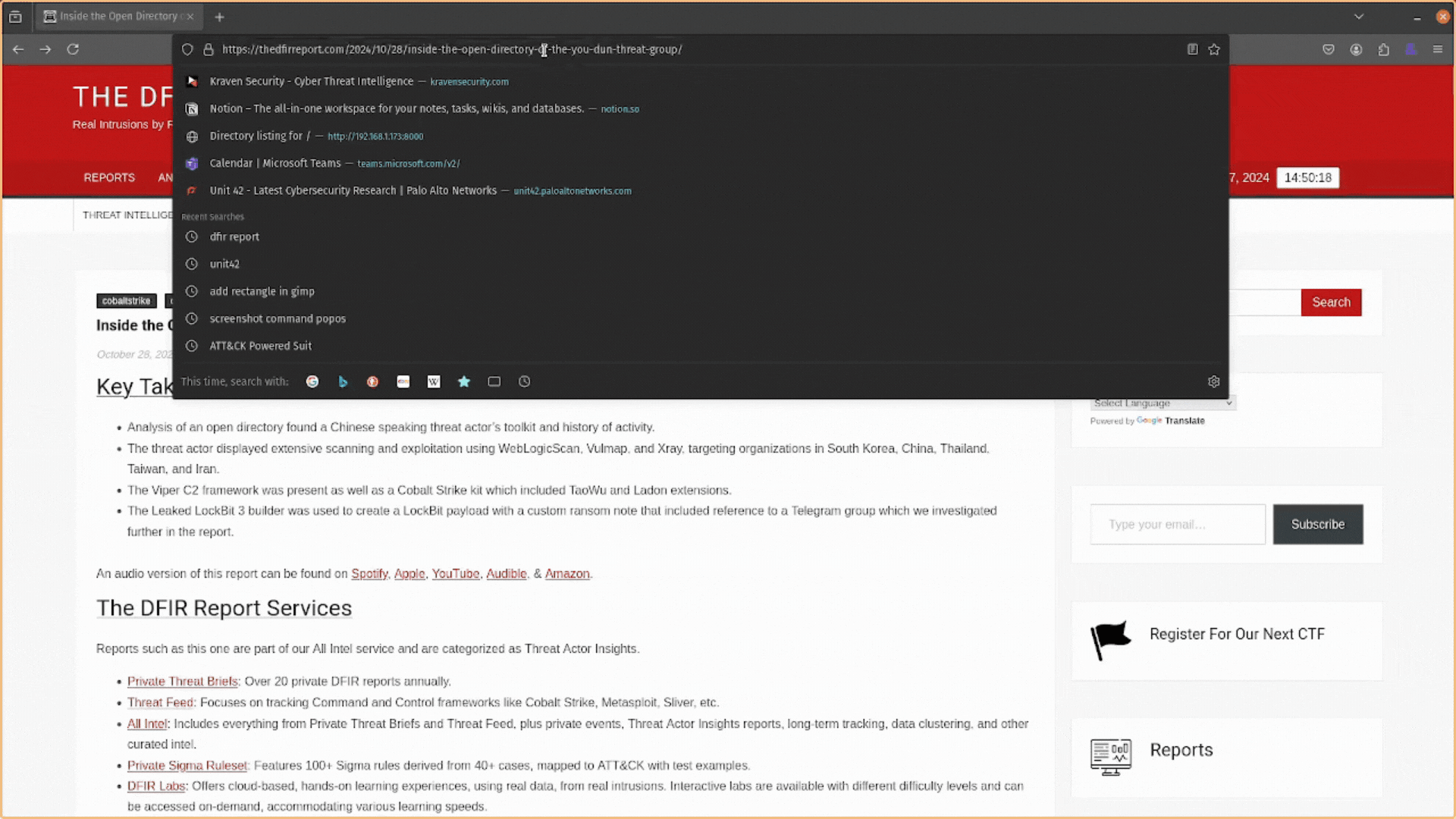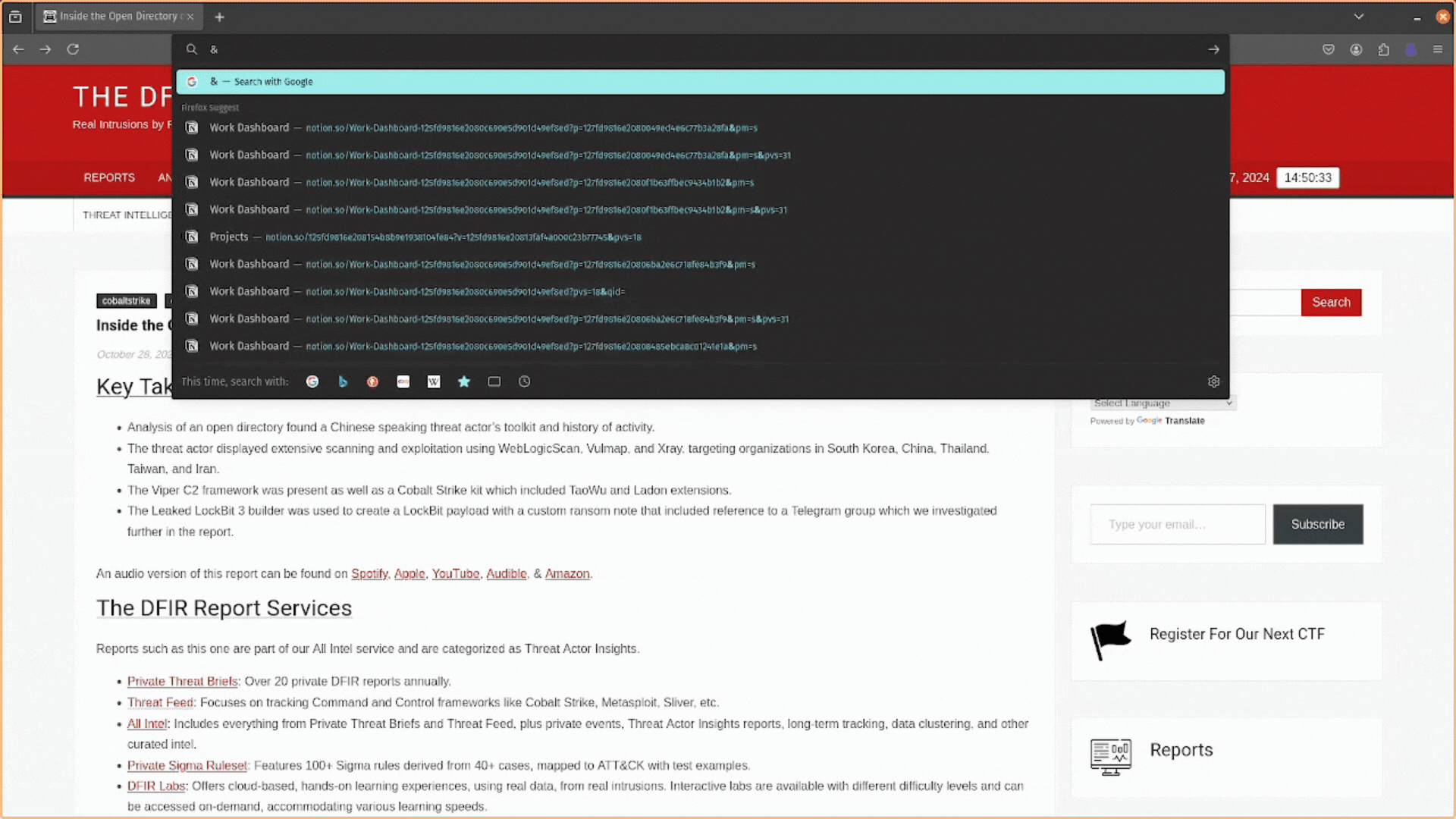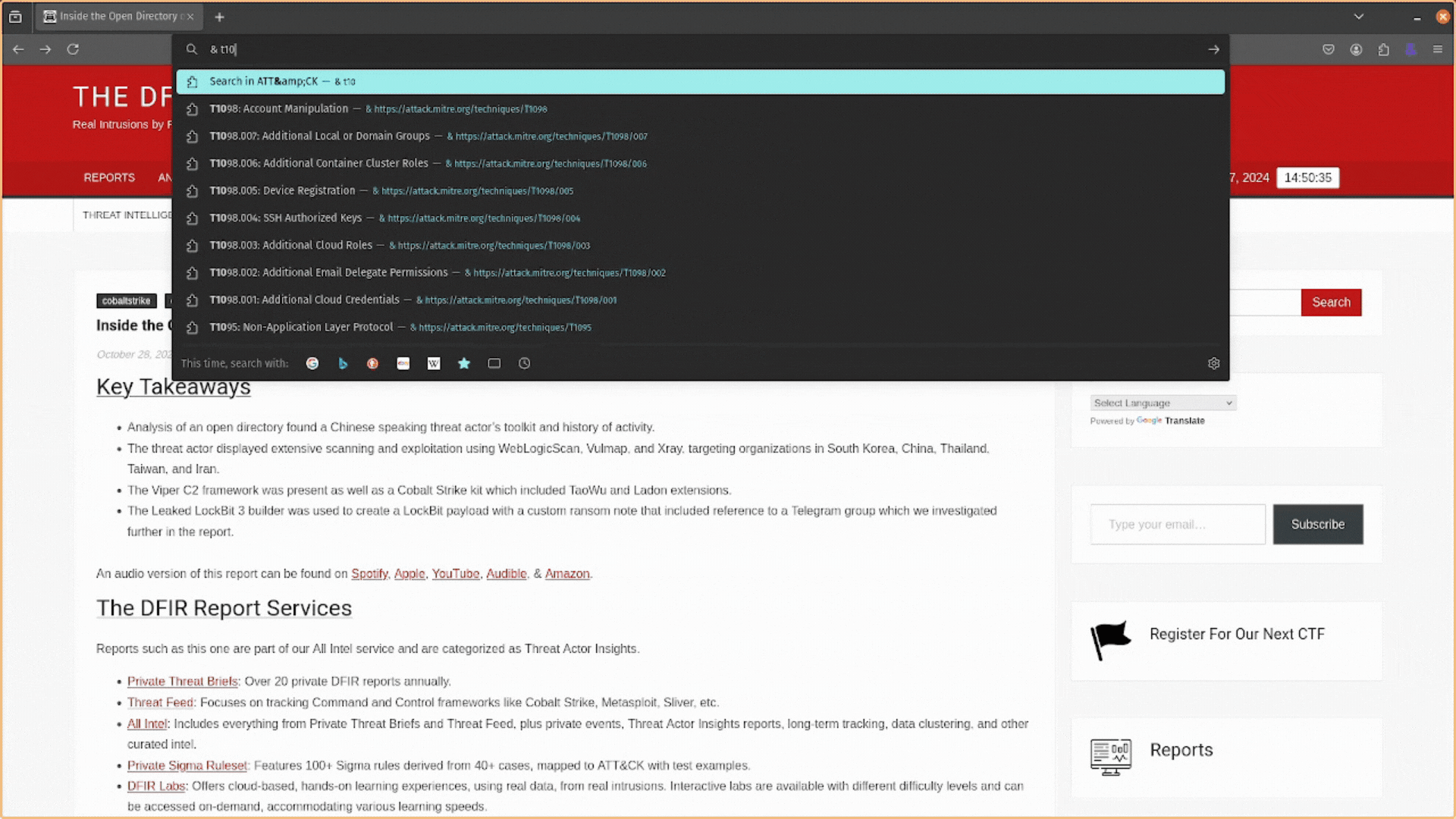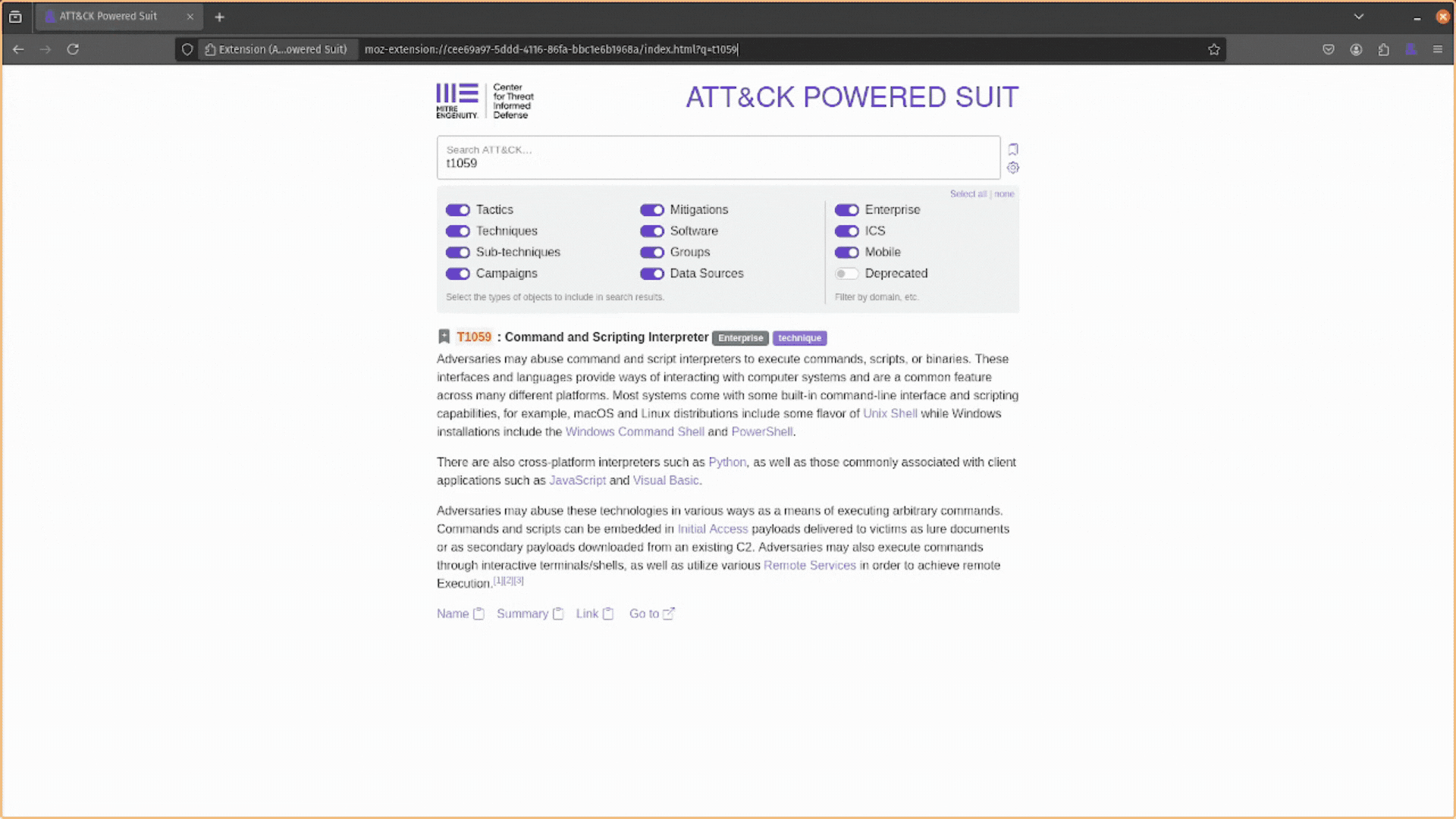
Navigate to your web browser’s address bar at the top and type &. Then hit the <space> key, and you can use the ATT&CK Powered Suit to search the ATT&CK knowledge base for whatever you want.
This all looks awesome. You can search for attack methods in numerous ways that streamline your research workflow. But there’s more still! You can customize what is returned in your search results. Let me show you.
Customization
Depending on how you plan to use your research results, the default format may not be up to scratch. You might want to integrate the results in your own notes, in a technical format you can upload to a tool, or in a format targeted at a non-technical stakeholder.
To support this, the ATT&CK Powered Suit allows you to customize the snippets generated from your search query. Click on the ATT&CK Powered Suit extension in your toolbar and select the View settings button (cog icon) to open the extension’s settings page.
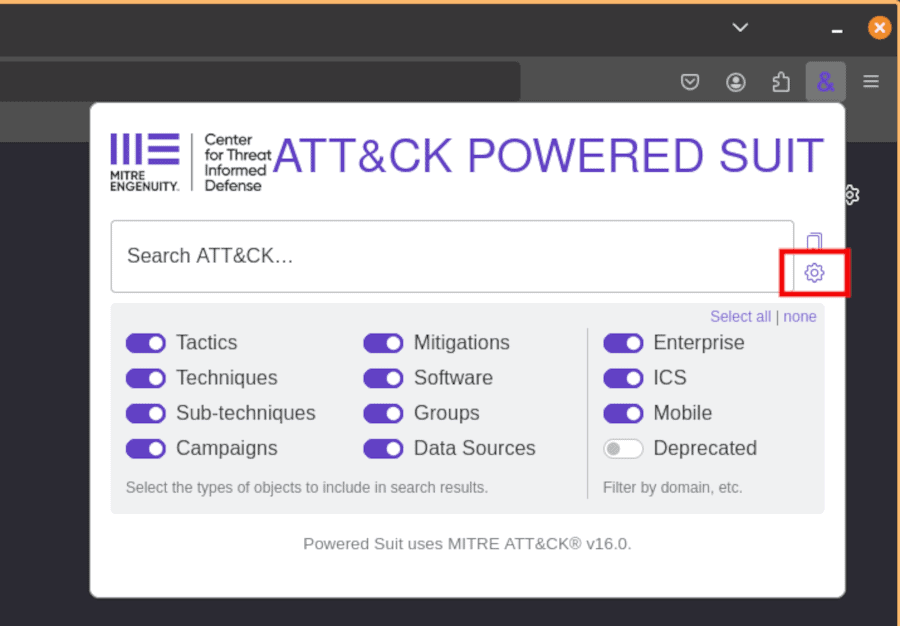
From here, you can adjust the search result snippet using the {description}, {name}, {fullName}, {parentName}, {id}, {type}, {url}, {stixId} variables.
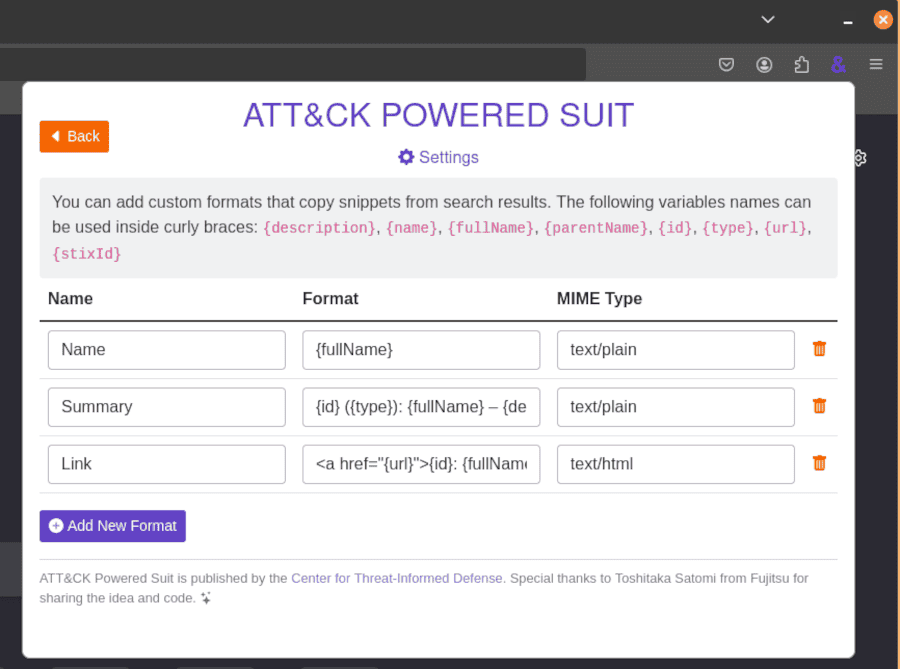
You can adjust what is returned from your searches, how you see fit, what format is returned, and how it appears in the interface. For instance, if you wanted the summary returned as JSON data, adjust the Format column to return a JSON object.
You need to keep the MIME Type as text/plain if you want to be able to use the copy to clipboard button.
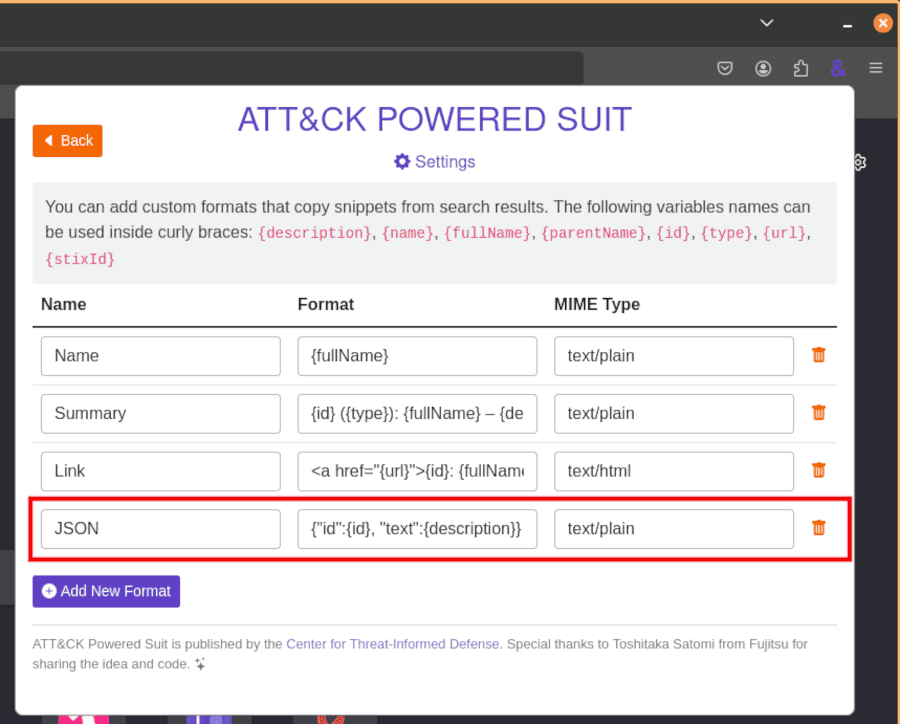
Now, when you search for an attack technique and copy the Summary provided, it will copy it as a JSON object to your clipboard.
Bookmarks
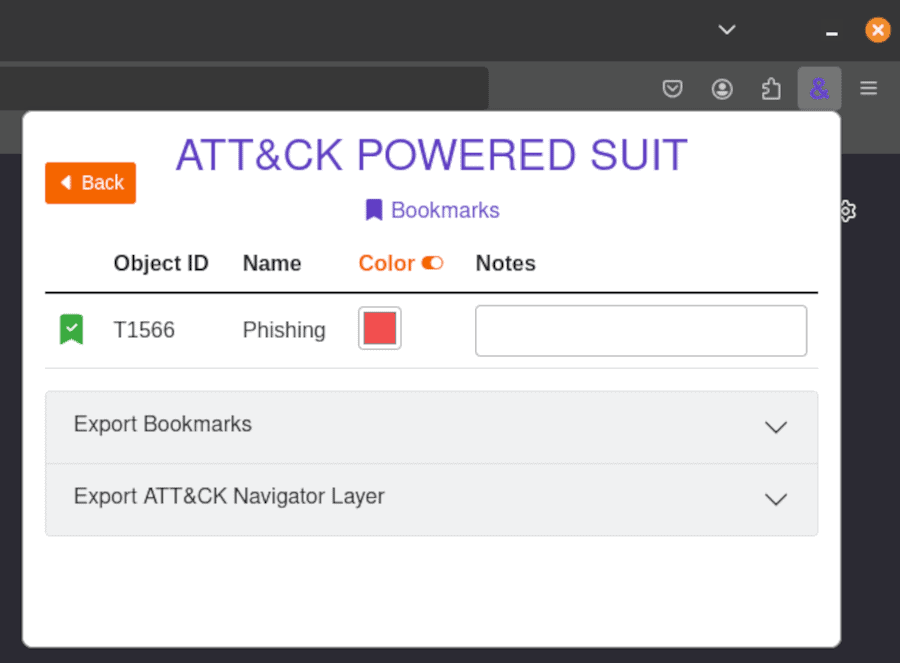
The final powerful feature of the ATT&CK Powered Suit you should know about is bookmarks. Bookmarks allow you to flag an attack technique as you work and then return to it.
To do this, click the Bookmark this object button on the left of the technique ID. This will give the technique a green tick so you know it is bookmarked.

Select the View bookmarks button at the right of the extension’s search bar to view what techniques you have bookmarked.
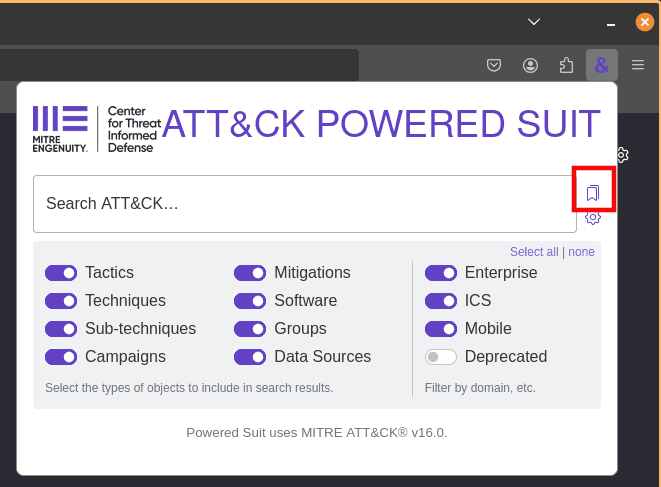
This will take you to the Bookmarks windows, where you can see what techniques you’ve bookmarked and export them as a CSV file or an ATT&CK Navigator layer (a JSON file).
The ATT&CK Navigator is an awesome tool that lets you visualize MITRE ATT&CK tactics, techniques, and sub-techniques. You can add your bookmarked techniques to this tool by uploading the JSON file created after an export.
The ability to bookmark attack techniques and then export them for use in other tools is a fantastic capability that the ATT&CK Powered Suit offers out of the box. I highly recommend playing around with it!
So, now you know the features the ATT&CK Powered Suit offers, how do you use them in the real world?
Use Cases for the ATT&CK Powered Suit
You can use the ATT&CK Powered Suit extension to streamline your CTI investigations and research in three main ways. Let’s take a look at each.
Investigating Threat Intelligence Reports
Perhaps the most obvious use case is to improve the efficiency of your threat intelligence investigations and research when reading threat reports.
These reports detail how an adversary performs a cyber attack and how you can defend against it. They often contain MITRE ATT&CK techniques, campaigns, mitigations, software, groups, and data sources you can research using the ATT&CK Powered Suit extension.

You can do this by using the extension’s popup window for a quick summary or, if you want more detailed information, highlight the technique in the report, right-click, and select Search ATT&CK for “<ATT&CK ID>.”
Also, use the extension’s bookmarking feature if you come across multiple techniques you want to research later or use within another tool like the ATT&CK Navigator.
Writing CTI Assessments and Reports
The MITRE ATT&CK knowledge base provides a common language for cyber security professionals to communicate intelligence about a cyber threat. You should use it in your CTI assessments and reports to accurately describe a threat’s TTPs and how they can be defended against.
Suppose you are reporting on an intrusion or threat your organization has faced. In that case, you can use the ATT&CK Powered Suit to quickly get ATT&CK IDs for the TTPs associated with that threat. Use keywords like “phishing” or “PowerShell” to get details on attack techniques that are related to what you are reporting on.
This will make your reports easier to read, more professional, and shareable with the wider cyber security community.
The ATT&CK Powered Suit saves you countless hours researching technique IDs. Just enter a few keywords, and you will quickly find the corresponding MITRE ATT&CK technique (along with information on how to defend against it.
Fulfilling Intelligence Requirements
CTI work is not just about reading and writing reports. It can be very technical. For instance, during an investigation, your Security Operations Center (SOC) may see an alert on the security tools that says T1092 was detected and raise a Request for Information (RFI) about this attack technique from you.
This RFI might include:
- What does this ATT&CK ID indicate?
- How would an adversary perform this technique?
- How can we defend against it?
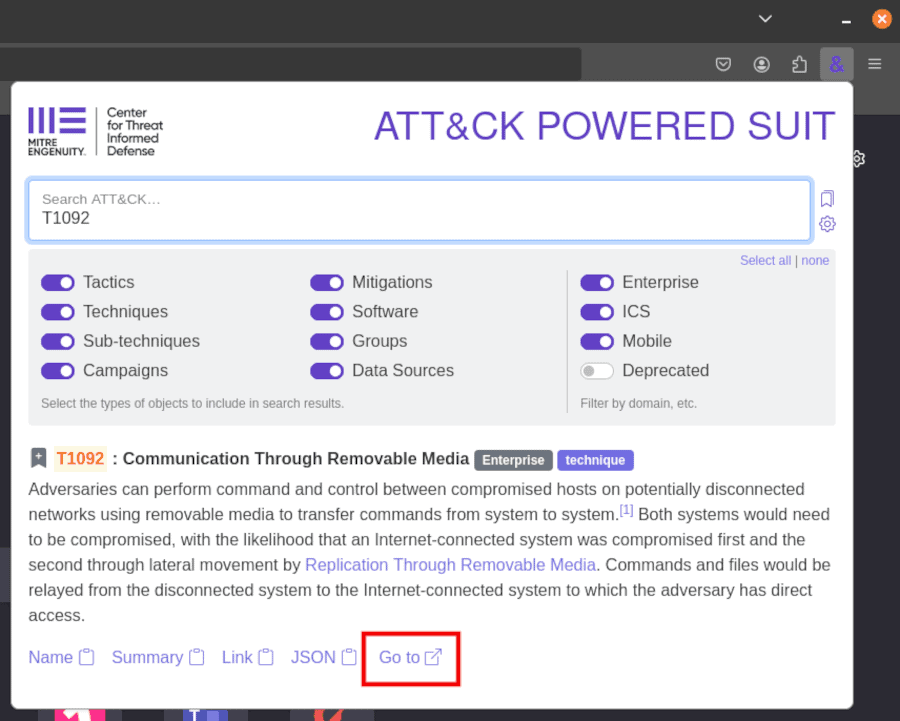
The ATT&CK Powered Suit makes answering these questions easy. Click on the extension icon in your toolbar and search for “T1092.”

It turns out this attack technique references “Communication Through Removable Media.” Interesting. You can learn more about it by clicking the Go to button at the bottom of the description.
It looks like this attack is as simple as jamming a USB stick into a machine, transferring sensitive data, and then walking away. You can also see some mitigations and detections you can use to defend against this technique.
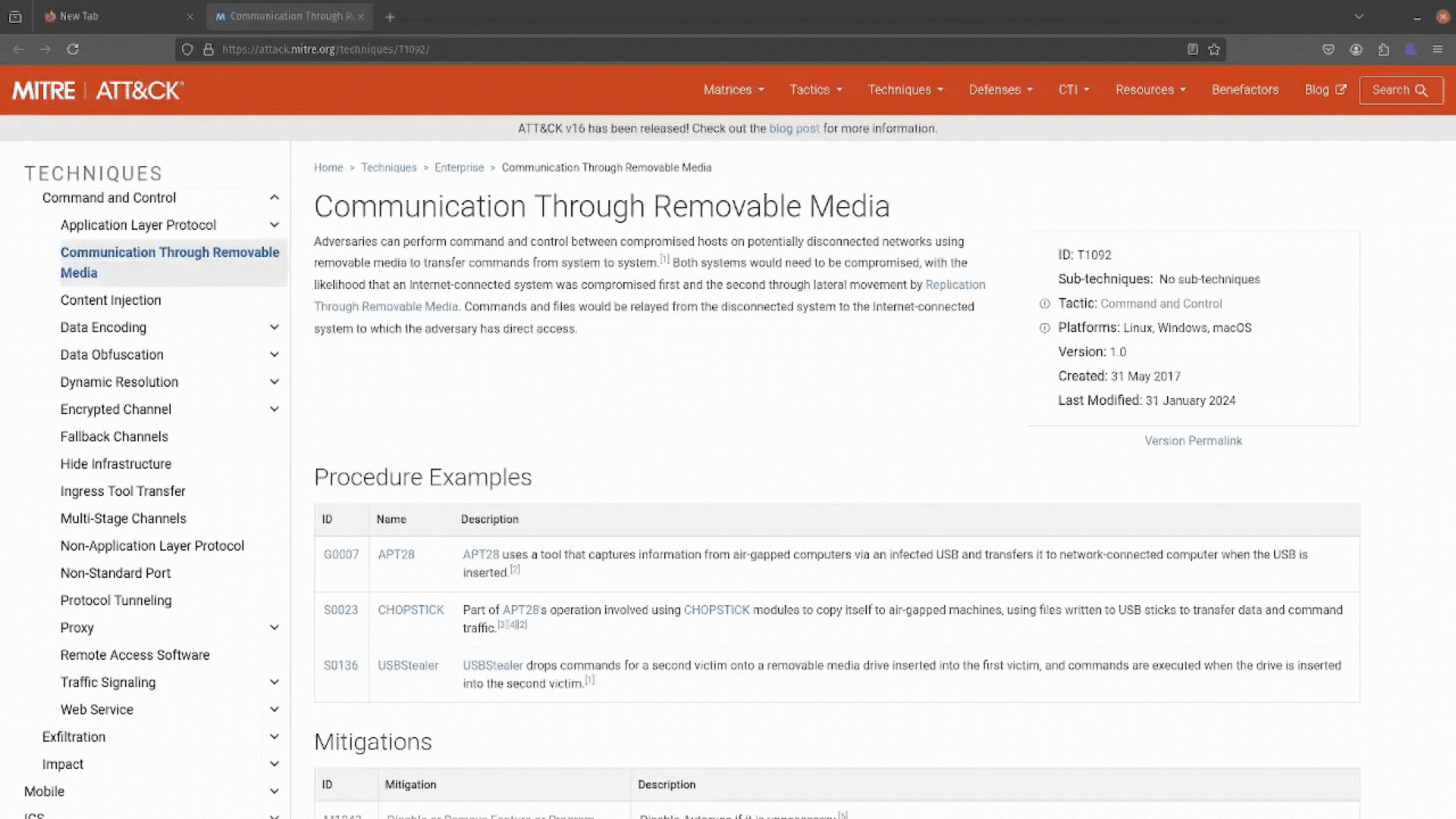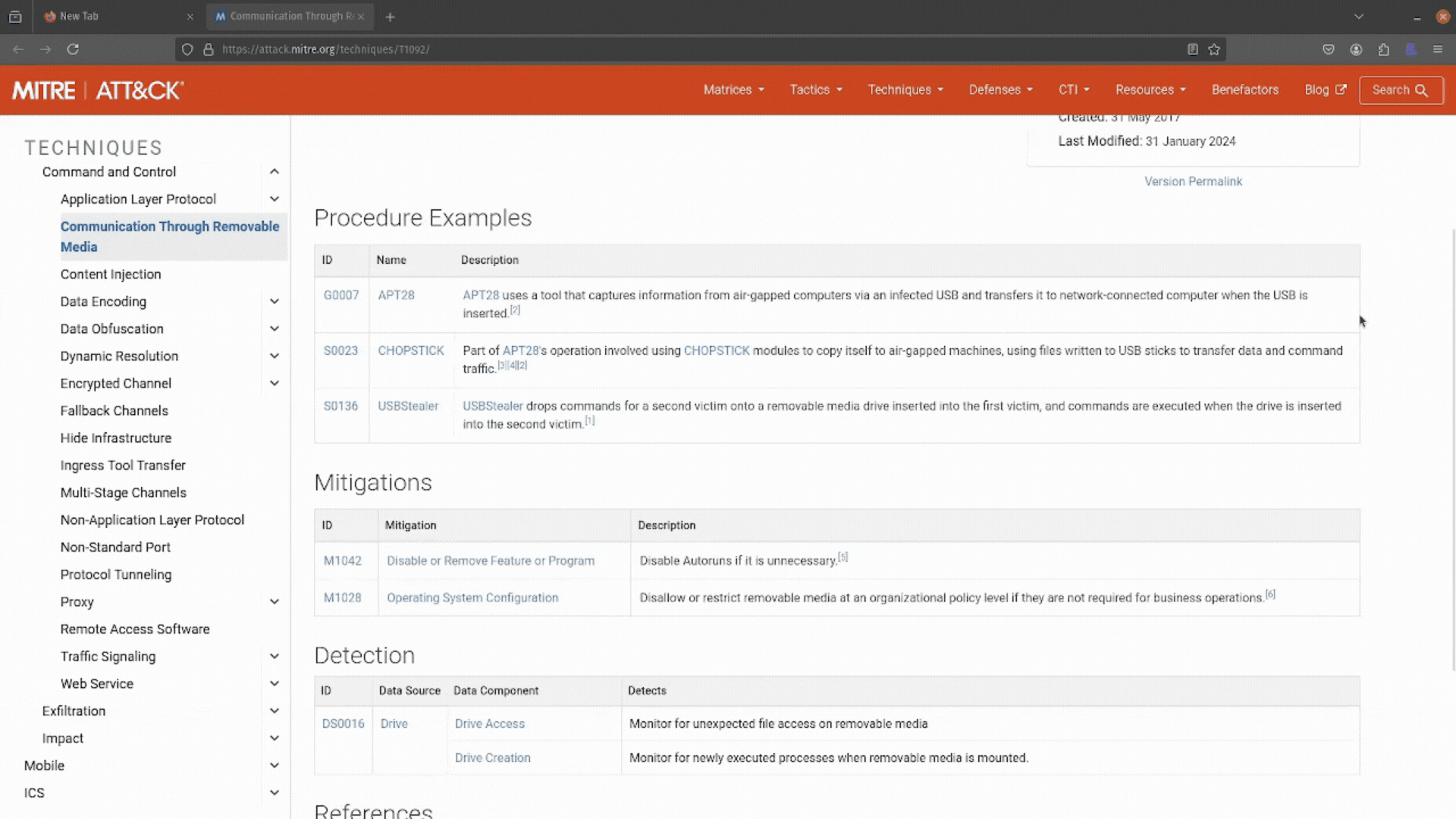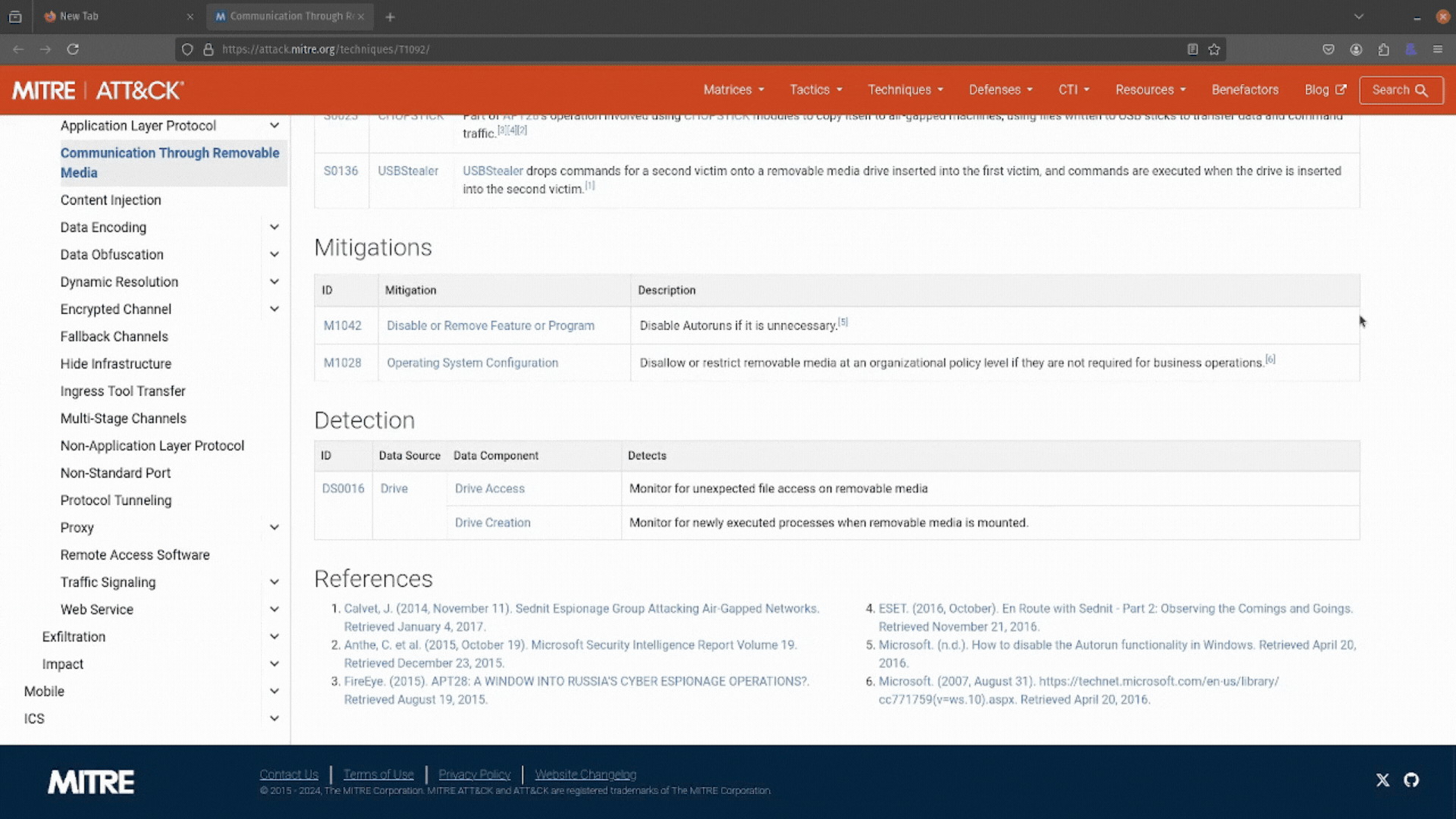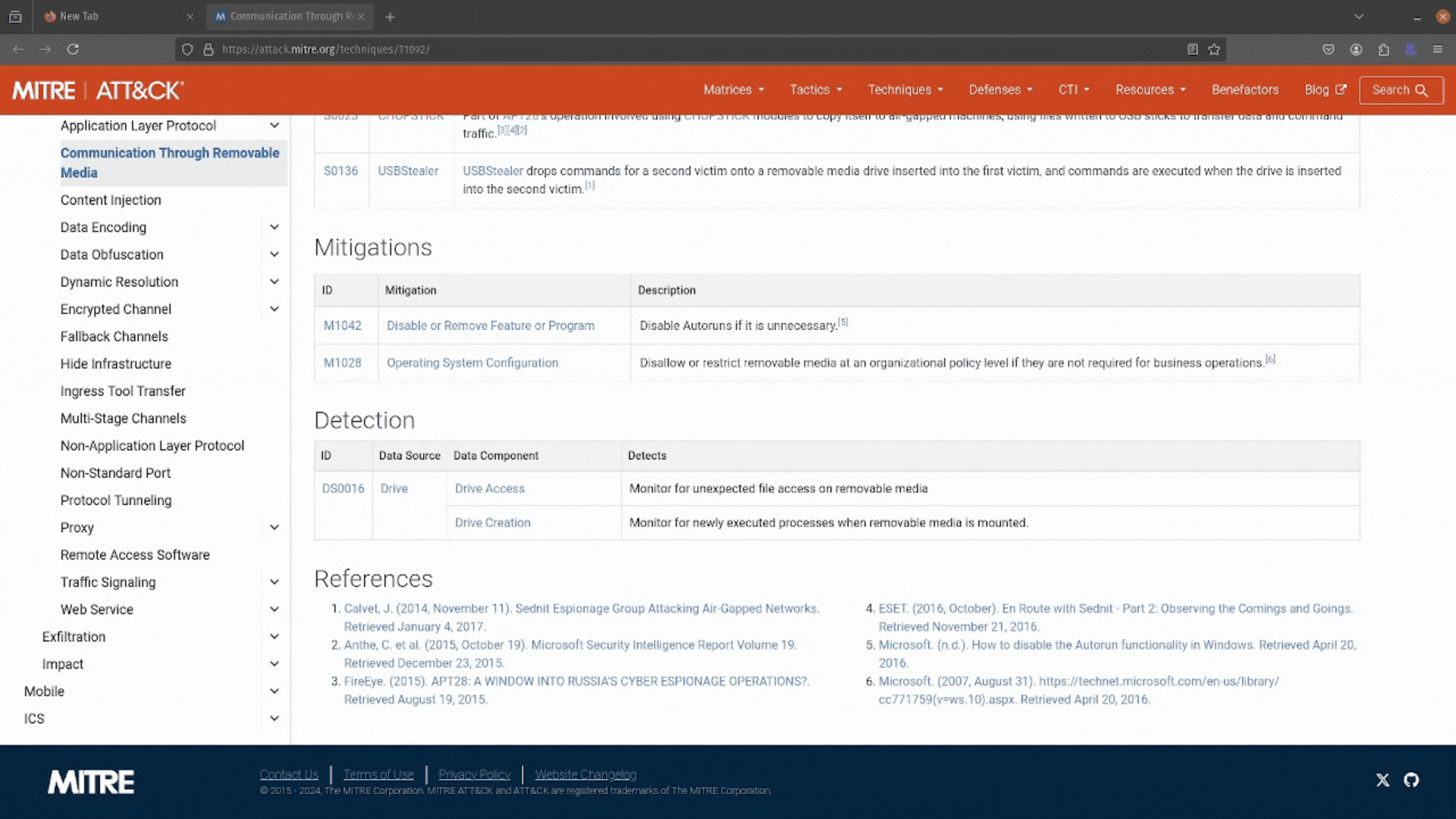
Perfect! You have all the information you need to answer this RFI and help your SOC team. Job well done, thanks, ATT&CK Powered Suit.
Conclusion
The ATT&CK Powered Suit is a game-changing tool for CTI analysts and cyber security professionals. It empowers you to quickly look up, research, and gather MITRE ATT&CK techniques through several great features, including highlight searching and the Omnibar.
You need this extension if you work in cyber security and consume or generate intelligence.
This guide has shown you how to use the ATT&CK Powered Suit, showcasing everything from bookmarks to customization. Take what you’ve learned and start putting this extension to work!
Use it the next time you come across an attack technique you need more details about, use it when researching techniques and need to export them to ATT&CK navigator, but most importantly, never go through the pain of using Google to search ATT&CK IDs ever again.
Frequently Asked Questions
What does MITRE ATT&CK Stand For?
MITRE is the organization that developed the ATT&CK framework, while ATT&CK is an acronym for Adversarial Tactics, Techniques, and Common Knowledge. The MITRE ATT&CK framework is a knowledge base for how hackers perform cyber attacks.
It is one of many MITRE projects that focus on threat-informed cyber defense. Other projects worth checking out are CTI Blueprints, the ATT&CK Navigator, and MITRE ATLAS for securing AI systems.
What is the ATT&CK Framework?
The MITRE ATT&CK Framework is a comprehensive and structured knowledge base of cyber adversary tactics, techniques, and procedures (TTPs) used in cybersecurity. It is designed to help organizations understand and defend against the tactics used by threat actors in real-world scenarios.
You can see how cyber security professionals use the ATT&CK framework to investigate cyber attacks in this article – Intrusion Analysis: How to Fully Investigate Cyber Security Attacks.
Is the ATT&CK Powered Suit Free?
Yes. The ATT&CK Powered Suit is a completely free browser plugin from the MITRE Engenuity Center for Threat-Informed Defense. It enhances cybersecurity research by providing direct access to the MITRE ATT&CK framework, a widely used knowledge base of cyber adversary tactics, techniques, and procedures (TTPs). This extension streamlines searching for attack techniques, groups, mitigations, and software references directly from your browser.
Where Can I Get the ATT&CK Powered Suit?
The ATT&CK Powered Suit is available for Google Chrome, Microsoft Edge, Firefox, and Apple Safari web browsers. You can download it from their respective browser extension stores for free. Once installed, it appears in your browser’s extension menu.
Pinning the extension to your browser’s toolbar is recommended for ease of use. You can then click on the extension’s icon to begin using it and search the MITRE ATT&CK knowledge base.




