Crown Jewel Analysis teaches you what to protect and how to protect it. This fundamental risk management methodology has been used for decades to help organizations determine what is important to them and where to prioritize their resources to defend against cyber attacks.
This guide delves into this risk management methodology to show how to use it today. It explores Crown Jewel Analysis, its benefits, and how to perform it. There are also recommendations for tools to help you use this methodology in the real world and practical examples to show how to secure a fictitious hair salon against cyber threats.
Let’s jump in and learn Crown Jewel Analysis so you can focus on defending what is most important to your business today!
What is Crown Jewel Analysis?
Crown Jewel Analysis (CJA) is a risk management methodology used in cyber security to identify and prioritize the protection of an organization’s most valuable assets, which are its crown jewels.
A crown jewel can be anything essential to an organization’s operations, reputation, and success. These assets could be:
- Sensitive data = personally identifiable information (PII) or customer financial data.
- Intelligence property, trade secrets, propriety technology = source code, custom technology, or secret recipes/formulas.
- Key business processes = payroll, customer fulfillment, or physical security.
- Critical infrastructure = web servers, firewalls, or cloud resources.
If one of these assets became compromised, the organization would be unable to fulfill its mission and objectives. Look below to see what is and what isn’t a crown jewel:
Company Documentation
This may hold sensitive data that you don’t want to be public (e.g., what technology is used), and if lost, it could have an operational impact on your business. However, losing documentation rarely has a significant financial, reputational, or operational impact, so it is not usually considered a crown jewel.
DNS Server
Your DNS server allows employees to access shared resources and route their Internet traffic. I may also be a dependency for your security tools. Your DNS server should be built with resiliency and redundancy in mind. If designed appropriately, this should not be a crown jewel.
Payroll Information
Your employee pay information is very sensitive and usually regulated by compliance standards. If compromised, it will significantly impact your organization’s reputation and operations (leading to a financial impact). Payroll is a crown jewel.
Web Server
Depending on your business, your web server may or may not be a crown jewel. A compromised website will significantly impact business operations if your organization relies heavily on its website to attract new clients, communicate with existing clients, or sell services.
KFC’s “11 herbs and spices” recipe
This is (or was) a trade secret (a proprietary technology for stimulating your tastebuds by being “finger-licking good”). This data is a crown jewel that should be heavily protected. Read 3 Things KFC and Good Threat Intelligence Have in Common to learn how KFC and threat intelligence relate.
Crown Jewel Analysis aims to align business objectives with security and ensure an organization’s security team protects its most valuable assets (which must be protected at all costs).
This requires defenders to know three things:
- What needs protecting?
- Value of the thing based on the impact if it is compromised?
- How do we protect the thing?
Answering these three questions is the essence of Crown Jewel Analysis and, if accomplished, leads to the following key benefits:
- Focused Resource Allocation: CJA allows organizations to allocate resources, investments, and security measures more effectively by prioritizing what matters to them. Not all organizations are the same, and finding what matters reduces risk.
- Improved Risk Management and Incident Response: A key part of CJA is understanding risk and how to mitigate it. The process allows organizations to start simple with their risk management strategy and security efforts by focusing on protecting critical assets first to have the greatest impact.
- Alignment With Compliance and Regulatory Standards: Many regulatory frameworks and industry standards require organizations to protect sensitive data and critical assets. CJA helps you identify, prioritize, and implement security measures to protect these assets and ensure alignment with regulations.
- Business Continuity: CJA is a key strategic planning tool. It allows organizations to safeguard key business functions and operations, minimize the impact of security incidents, and ensure business continuity, which maintains customer trust and confidence.
- Aligning Cyber Security with Business Objectives: A common friction area for businesses is security; many see it as an expense they want to minimize. CJA allows organizations to align security with business objectives so stakeholders can more clearly see value. It allows decision-makers to understand the value and importance of critical assets and prioritize initiatives that address the most significant risks to the business.
Now that you know what Crown Jewel Analysis is and its many benefits, let’s explore how to conduct CJA so you can start prioritizing the protection of your organization’s most important assets.
Conducting Crown Jewel Analysis
Crown Jewel Analysis is not an overly complicated process. You can break it into three main components:
- Identifying critical assets to protect.
- Assessing the value of those assets to prioritize their protection.
- Performing threat modeling and risk assessment to find ways of protecting them.
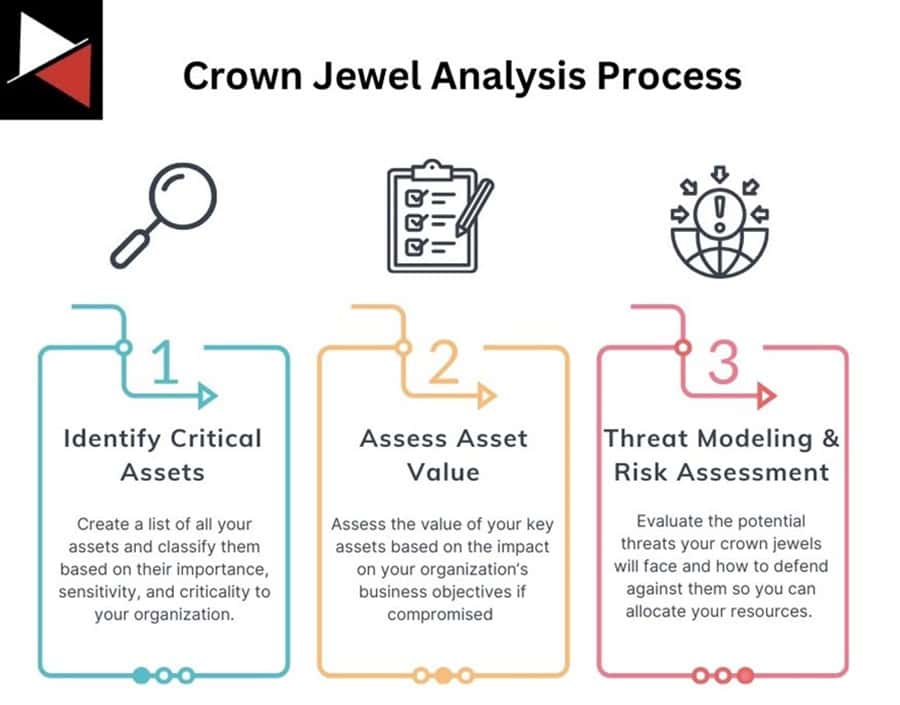
Step 1: Identifying Critical Assets
The first step in Crown Jewel Analysis is identifying and classifying all your critical assets. This is typically done by creating an inventory of all the assets within your organization (e.g., data, systems, applications, and infrastructure).
This “asset inventory” is a comprehensive list (or database) of all the assets owned or used by your organization, be it physical systems, software applications, or data. This list provides you with visibility over everything your company uses.
As you compile a list of assets, you should classify each asset based on its importance, sensitivity, and criticality to the organization’s operations and objectives using labels or categories. For instance, you could mark data as confidential, software applications as mission critical, or a customer fulfillment strategy as propriety. This will make the next steps easier.
Once you have documented everything your organization owns or uses, you can assess the value of each asset to determine what you need to prioritize protecting.
Step 2: Assessing Asset Value
Assessing the value of each asset your organization owns or uses is the most critical part of Crown Jewel Analysis. Unfortunately, it is also the most time-consuming.
With your list in hand, you must review each asset and assess its value to your organization’s business objectives and the impact if compromised. You can perform this assessment using the following factors:
- Operational impact: If this asset is taken down, will it affect business operations?
- Financial impact: Will we lose money if we lose access to this asset?
- Strategic importance: Does this asset provide us with a strategic advantage we would lose if it became unavailable?
- Regulatory compliance requirements: Do I need this asset working to remain compliant with regulatory standards?
- Potential reputational damage if compromised: What reputational damage will occur if this asset is compromised?
After assessing each asset’s value, you should now have a list of critical assets that, if compromised, would significantly impact your business.
If you are a smaller organization, you may have only a few. However, if you are a larger organization, you may have many. If this is the case, try to group these assets into key areas and then prioritize assets in each area. This will allow you to compartmentalize your concerns and provide a structure for protecting assets.
To save time, schedule a meeting with a key stakeholder who knows your organization’s business objectives and write them all down. Then, when you are performing CJA, you can reference this list rather than having the stakeholder sit in with you or wait for a reply.
Step 3: Threat Modeling and Risk Assessment
Once you have a list of critical assets to protect, you can move on to threat modeling and risk assessment.
Threat modeling is a structured approach to identifying and analyzing potential threats and vulnerabilities that impact critical assets. These could be insider threats, external attacks, malware, or vulnerabilities in your organization’s software.
You can use one of the many methodologies and techniques available to perform threat modeling, such as STRIDE, DREAD, PASTA, attack trees, and VAST. Which one you choose will depend on the asset you are threat modeling.
If it’s software, STRIDE or VAST are good options. If you want something more generic, DREAD and PASTA are great. If you want to focus on threat actors and their TTPs, attack trees are the best choice.
When creating a threat model for each of your critical assets, you can be as detailed as you want. You may want to go as deep down as the specific software versions an attacker will target or TTPs they will use. However, you can keep it simple and rate the risk or impact against the five DREAD factors. The choice is yours. For more details on how to perform threat modeling, check out this complete guide.
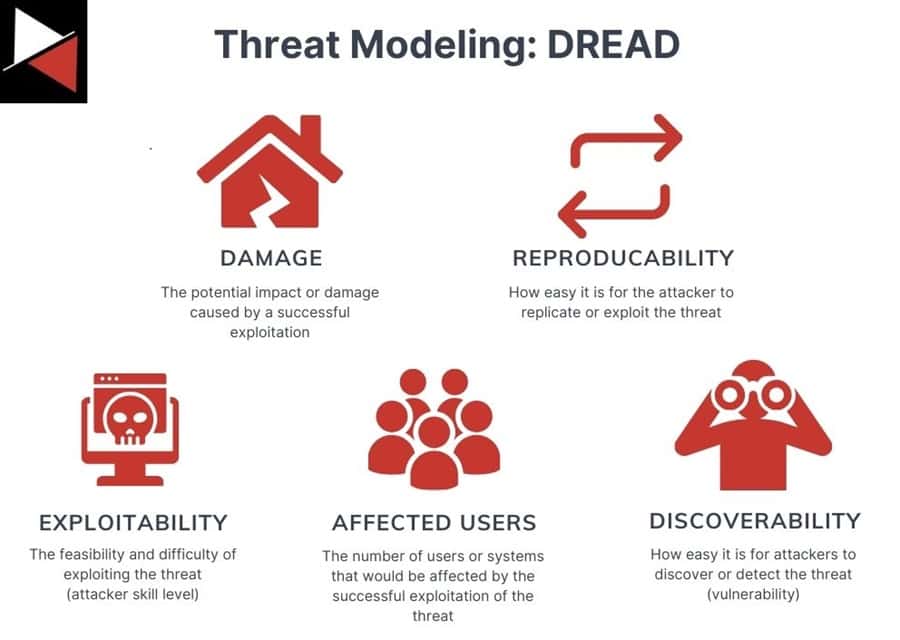
After completing a threat model for each of your critical assets, you can move on to performing a risk assessment. This assessment evaluates the likelihood and severity of potential risks to critical assets. For example, will my webserver, running the latest software and having all security updates, likely be compromised?
A risk assessment of each critical asset allows you to discover what acceptable risks your organization is willing to tolerate and the ones that must be protected against at all costs. This will enable defenders to prioritize their security efforts.
The threat model tells you what attacks you will face, and the risk assessment tells you which to prioritize. Now, it’s time to start building your defenses.

Using the Course of Action matrix, you can discover what defenses you can build. Read Unraveling the Courses of Action Matrix: Full Guide to CoA to learn more.
Tools for Conducting Crown Jewel Analysis
Here are a few useful tools and methodologies to help you get started performing Crown Jewel Analysis.
Asset Management Systems
These systems help you maintain an inventory of all your assets and include features for tracking asset details and changes over time. They are a must-have for accurately managing all your organization’s assets.
You can use a simple spreadsheet (or Microsoft List) or a commercial option like ServiceNow, SolarWinds Asset Management, or the open-source Snipe-IT.
Data Classification Tools
These tools help you classify and label sensitive data based on its importance to your organization, sensitivity, and regulatory requirements. They automate the identification and categorizing of data assets to save time and money when assessing asset value (step 2).
Examples of data classification tools include Varonis Data Classification Engine, Fortra’s Data Classification Products, and Microsoft Azure Information Protection.
Threat Modeling Methodologies
These were previously discussed in Step 3: Threat Modeling and Risk Assessment. Popular threat models include STRIDE, DREAD, PASTA, attack trees, and VAST. You can even get software to perform this threat modeling, like Cairis, IriusRisk, OWASP Threat Dragon, and the Microsoft Threat Modeling Tool.
Risk Assessment Frameworks
Risk assessment frameworks provide a structured methodology for performing a thorough, consistent, and efficient risk assessment of all critical assets. They are great for producing comparable risk assessments that allow you to prioritize which critical assets are most at risk.
Popular risk assessment frameworks include the NIST Cybersecurity Framework, ISO 27001, and FAIR (Factor Analysis of Information Risk).
Threat Intelligence Platforms
Threat intelligence platforms (TIPs) provide the insights you need to accurately assess the threats and risks your critical assets will face. They showcase the current threat landscape and emerging threats and help you identify potential threats you must factor into Step 3: Threat Modeling and Risk Assessment.
Examples of threat intelligence platforms are ThreatConnect, Recorded Future, and Anomali.
Demo: Performing Crown Jewel Analysis
Now you know what Crown Jewel Analysis is, the steps to performing an effective analysis, and some tools to help you along the way, let’s look at an example. In this demonstration, you will see CJA applied to a simple case study and how you can perform this analysis technique in the real world.
Case Study
Let’s use a hair salon (or hairdresser if you’re less fancy) for this demonstration. A client makes a booking online and pays at the same time. They arrive at their scheduled appointment time, get their hair cut and styled, and then leave happy.
You oversee security for this hair salon, and the owner asks you where to invest the security budget. To do this, you decide to perform a Crown Jewel Analysis on the organization and report your findings. Let’s explore how you’d go about that.

Applying Crown Jewel Analysis
To apply Crown Jewel Analysis, you can follow the steps outlined previously.
Step 1: Identifying Critical Assets
First, you must create an asset inventory of everything the hair salon owns or uses to conduct its business operations. Then, you must classify each asset based on its importance, sensitivity, and criticality to the organization.
Step 1 is a broad sweep where you gather all the assets and group them into categories, usually by giving them labels like confidential, mission-critical, or propriety. This sweep helps you identify what assets require further scrutiny as you assess their value to the organization’s objectives and operations.
Here is a partial asset inventory for a hair salon.
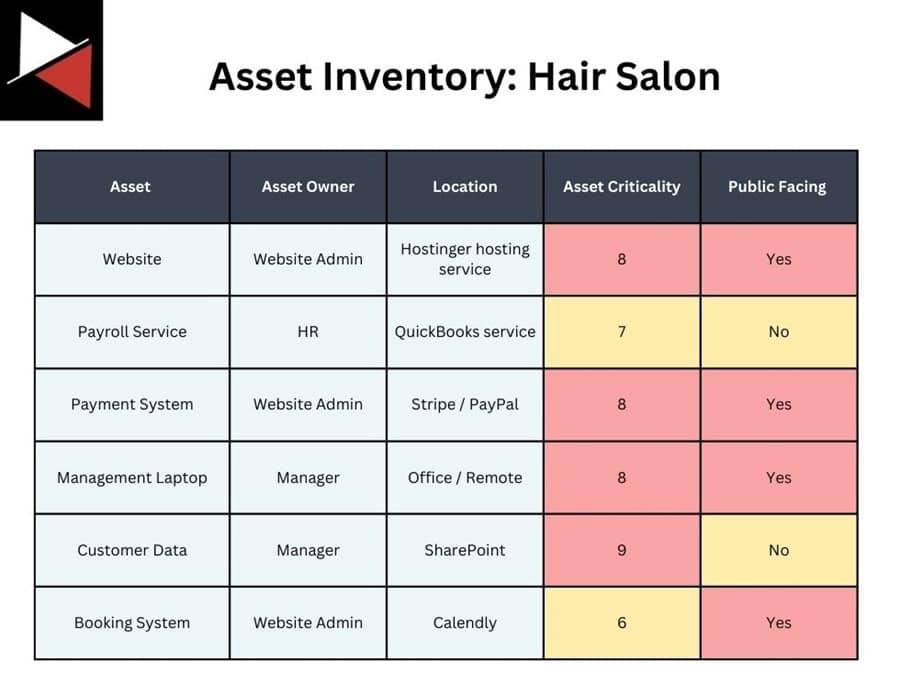
Step 2: Assessing Asset Value
Now, you must assess the value of the key assets you identified in your asset inventory. This can be time-consuming and difficult if you don’t understand how your organization uses each asset or its potential dependencies.
As such, having an executive or department head with you is best when assessing asset value. They should know how their team or direct reports use each asset. Just remember that everyone will think their assets are the most important, so aim to make the measuring as subjective as possible and use your critical thinking skills.
To measure the value of each asset, you can use a matrix such as the following:
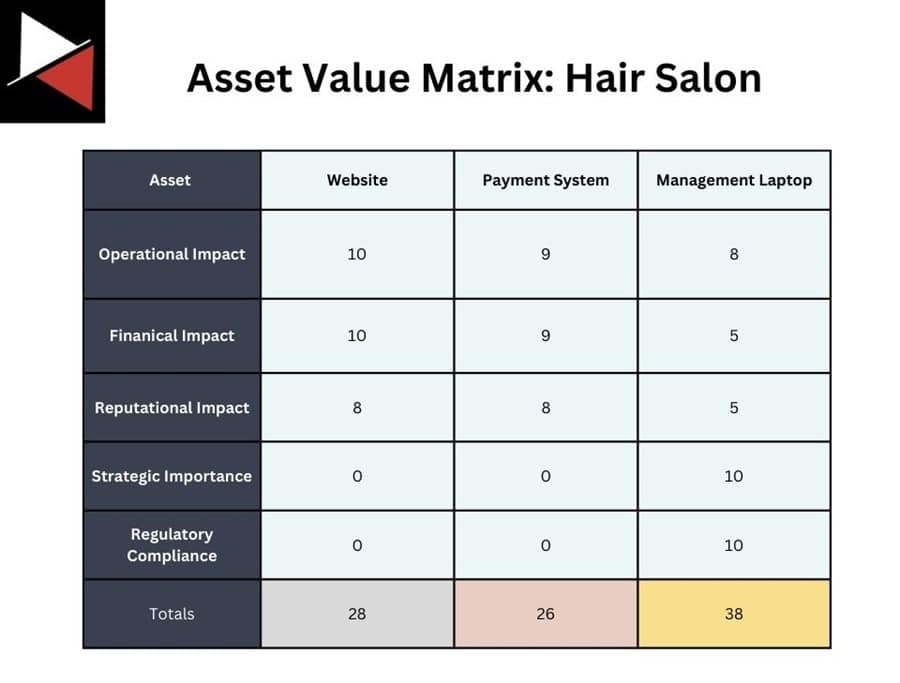
Assets are listed on the X axis, and the five key factors used to determine value are listed on the Y axis. You rate each asset on a scale of 1-10 (low to high) against each factor, then tally the scores. The top-scoring assets are your crown jewels. Here, the Management Laptop comes out as our primary crown jewel.
Remember to consider inter-dependencies between crown jewels. For instance, you may rate your website higher than your organization’s domain name, but it is useless if it gets compromised.
Step 3: Threat Modeling and Risk Assessment
Once you have identified your crown jewels and prioritized their importance, you can assess the potential threats these assets face and how to defend against them.
The threat modeling process is explained in-depth in this article. However, for a simple example, you could apply DREAD threat modeling to the hair salon website as follows:
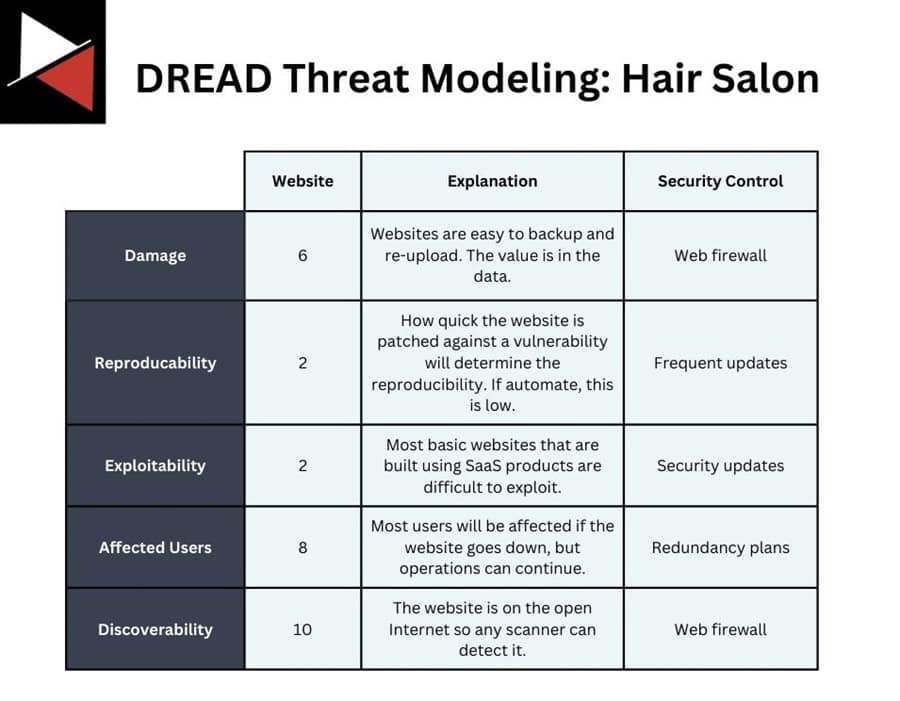
Once you complete your threat modeling for each crown jewel, you can move on to risk assessment. This assesses which threats are most likely to happen based on your current defenses and the threat landscape.
You should now have a list of crown jewels and security recommendations to protect them that you can report to your boss.
I always find it useful to show your work by drafting a report that explains the process you followed to reach your conclusions. Start with an executive summary, then provide a high-level overview of the process, and finally add any specific details (e.g., your asset inventory list, value assessment matrices, and threat models).
Conclusion
Crown Jewel Analysis is a fundamental risk management methodology that helps organizations identify what is most important to them and how to protect it against cyber attacks.
This guide detailed this methodology, its importance, and how to use it. Along the way, you discovered the three-step process for performing Crown Jewel Analysis and tools that can help you. You also saw a practical example of applying this analysis technique to a hair salon.
Remember to (1) identify critical assets with an asset inventory, (2) assess the value of your key assets by measuring their impact on the business if compromised, and (3) perform threat modeling and risk assessment to identify threats your crown jewel will face and how to protect them!
Frequently Asked Questions
What Is a Crown Jewel in Cyber Security?
An organization’s most valuable assets, resources, or data are its crown jewels. They are essential to its business objectives, operations, and success. If compromised, they can lead to significant reputational damage, have a major financial impact, or adversely affect mission-critical operations.
Your organization’s crown jewels will depend on various factors. However, common examples include sensitive customer data, company web servers, cloud resources, communication systems, and proprietary information.
How to Identify Crown Jewels in Cybersecurity?
To identify your organization’s crown jewels, you must create an asset inventory that details everything your organization uses or owns. Next, you must classify each asset based on its importance, sensitivity, and criticality to your organization’s operations and objectives. This will give you a list of key assets to focus on assessing.
Finally, you must assess the value of each key asset using factors like its operational and financial impact if taken offline, its strategic importance, whether regulatory compliance standards must be met, and the potential reputational damage if the asset is compromised. This will reveal your organization’s crown jewels.
How Do You Conduct Crown Jewel Analysis?
Conducting Crown Jewel Analysis is a three-step process:
- Identify Critical Assets: You list all the assets your organization uses or owns and classify them based on their importance, sensitivity, and criticality to your organization’s operations and objectives.
- Assess Asset Value: Once you have key assets, you can assess their value based on the impact on your organization’s business objectives if compromised (e.g., financial, reputational, operational impact).
- Threat Modeling and Risk Assessment: Once you have a list of crown jewels, you can evaluate the potential threats these assets will face and determine how to defend against them.
These steps will reveal your organization’s crown jewels and how you can protect them from threats.



