Exciting news! We have two new initiatives at Kraven that have gone live this month. Let me introduce you to our new free training courses and threat hunting packages.
These two initiatives bring actionable cyber threat intelligence to everyone, whether you want to learn something new through a zero-cost, self-paced online course or hunt for the latest indicators derived from open-source threat intelligence reports.
Each initiative focuses on providing you with practical knowledge to bolster the cyber security posture of your organization. To start with, let me share with you the latest details on our new free training courses!
New Free Training Courses
Finally, we have training courses at Kraven! This has been a long-requested feature which we are pleased to have released. You wanted structured learning all in one place. Here you go!
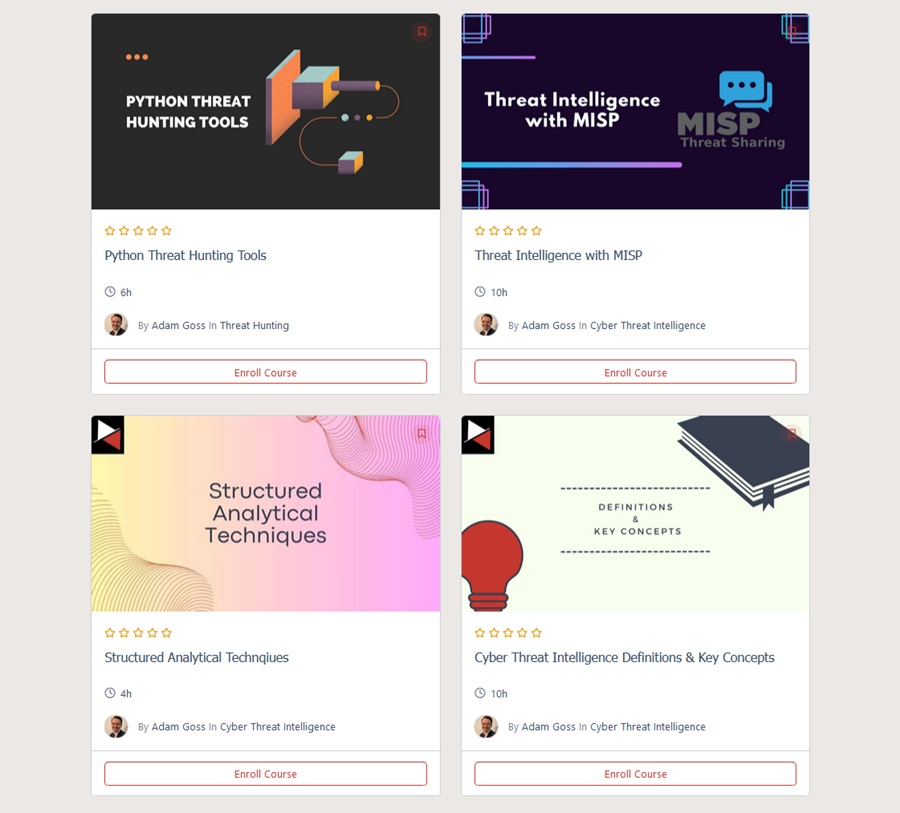
We are kicking off with the following self-paced courses:
- Python Threat Hunting Tools: Learn to build custom tools that you can use to hunt for threats, automate tedious processes, and extend to create your own toolkit using Python.
- Threat Intelligence with MISP: Discover how to use a popular open-source Threat Intelligence Platform (TIP) to gather, analyze, and disseminate cyber threat intelligence.
- Structured Analytical Techniques: Structured Analytical Techniques (SATs) empower analysts to perform consistent, comprehensive, and thoughtful data analysis. Learn to use these frameworks, models, and methodologies to help you make better decisions when analyzing threat intelligence.
- Cyber Threat Intelligence Definitions & Key Concepts: Cyber threat intelligence is built on models, frameworks, and analytical techniques. To master it, you must learn the definitions and key concepts used within the industry, so we gather them in one place for you.
Each course is free and aims to deliver high-impact learning wherever you might be in the world. They are built around instructional videos, engaging text-based lessons, and fun quizzes to boost your understanding of the topics taught.
“Why free?”
Simple. We believe everyone should have access to high-quality cyber threat intelligence (CTI) training regardless of their budget. That’s why we wanted to kick off our training course catalog with the free stuff!
But don’t be mistaken. Just because it’s free, it doesn’t mean it’s cheap, low-quality, or subpar. We strive to make our free stuff good (if not a little better) than our competitors’ paid stuff!
These courses are packed with expert insights and practical advice from industry professionals but, most importantly, they focus on actionability so you can make a difference in your organization.
“So, what is the catch?”
No catch. Just try the course.
- If you enjoy them, great. We’d love to hear what you enjoyed
- If you hate them, it’s also great. Just let us know how we can make it better for you.
We aim to deliver content that is approachable to anyone. It’s our mission to provide you with training that will make a real difference in our collective effort, as cyber defenders, to make the tech space a little more secure.
“You sold me. Where do I sign up?”
Easy. Head over to kravensecurity.com, hit that Training Courses button to see our catalog of free training courses to get started with, and sign up today!
“Okay. Free training courses are great, but what about when I’ve completed them all?”
Well, CTI is just not for Christmas. You must care for and nurture it every day… like a dog (or spouse). That’s why we are releasing another initiative to focus on delivering daily threat hunting packages.
P.S.
If you’re looking for more training, don’t worry. We will be releasing additional training courses this year that will be even more impactful with all the bells and whistles!
Threat Hunting Packages
So, what are threat hunting packages?
Simple. They are just a collection of indicators extracted from CTI reports that a threat hunting team can use to start a threat hunt.
They include host-based indicators like file hashes, registry keys, filenames, or processes. As well as network-based indicators like IP addresses, hostnames, URLs, or domain names. They can even include behavioral indicators like MITRE Tactics, Techniques, and Procedures (TTPs).
CTI reports are littered with indicators, usually in an appendix at the end. Unfortunately, this means that your lone CTI analyst must go through each report, extract the indicators, and store them somewhere before they can even think about beginning to use them.
This is tedious. Trust me, I’ve been doing it for a long time now.

That’s why we launched our threat hunting package initiative. We sift through these reports for you and put all the indicators in one place (a GitHub repository), so you can start using them straight away! Saving you time, effort, and headaches.
The repository even includes two threat hunting scripts designed to make the indicators easy to operationalize:
verify-iocs-vt.pyfor verifying IOCs are malicious by using VirusTotal Community API.iocs-to-cs.pyfor uploading IOCs to CrowdStrike Falcon IOC Management for detection and blocking.
Is this perfect? No. We can’t cover every threat report (yet). But we can give you a hand when it comes to the high-impact ones that affect a ton of people.
Just follow my social media channels to stay informed about what’s going on in the world of cyber threat intelligence and get updated whenever a new threat hunting package drops:
You can even head over to the project’s GitHub repository now to see what these threat hunting packages look like.
“But why bother doing this?”
This initiative is another one we added to our repertoire to help demystify cyber threat intelligence, make it actionable for more people, and ensure everyone can unlock the power of threat intelligence!
If you have any other ideas about how we achieve this aspirational goal. Please reach out. We’d love to hear from you!
TLDR
We have launched two new initiatives. One is our new free training courses designed to deliver high-quality, impactful cyber threat intelligence content. The other is our threat hunting packages that extract and collate indicators from open-source threat intelligence reports, so you can start using them faster.
Both align with our goal to demystify cyber threat intelligence and make it actionable for more people. I hope you enjoy them!