Threat intelligence platforms help organizations collect, analyze, and share information about potential cyber security threats.
They enable businesses to proactively detect and respond to threats by aggregating data from various sources into a single screen. This data is correlated, enriched, and made actionable through visualization tools so security analysts can quickly identify potential threats and prioritize their responses.
The top businesses worldwide invest in these platforms to keep safe, with an estimated market size of $11.27 billion in 2023 and growing at 14.9%. As a senior threat intelligence analyst, I have seen the great value they have brought to multiple large businesses across various industries. If you want to start getting serious about cyber security, you should too.
Let’s explore the five reasons why a threat intelligence platform can transform your business’s cyber security program from average to exceptional!
Reason #1: Keep up-to-date with the current threats
Cyber threats are evolving daily, with 39% of businesses suffering from a cyber attack in 2022. Every business should have a comprehensive cyber security program that protects them from the latest threats. Unfortunately, if your program does not use a threat intelligence platform, you are probably not protected.
Traditional security mechanisms like firewalls and anti-virus software only alert on well-known threats that have been seen hundreds of times before. These mechanisms are not designed to keep up with the latest 0-days, ransomware strains, or malware that threat actors use to carry out cyber attacks against reputable businesses. To protect against these threats, you need a solution that is continuously updated with the latest information about new and emerging threats. The timeliness of this information can be the difference between thwarting an attack or losing millions in revenue.
Threat intelligence platforms (TIPs) are dedicated to keeping your cyber security program in sync with the latest threats. This is why they are a key piece in solving the problem of securing complex systems today.
Keep up-to-date with threats or get left in the dust by the bad guys.
Reason #2: Detect current threats in real-time
Can your cyber security program detect the current threats in real time?
Many organizations use threat hunting queries to search for Indicators of Compromise (IOCs) or adversary tactics/techniques/procedures (TTPs). For instance, they may manually assemble a list of IOCs and search for them in their environment using a SIEM or EDR solution. This is slow, ineffective, and could let bad guys slip through your fingers.
Many modern security solutions are set up to create a pipeline that ingests threat intelligence and automatically alerts when it is seen in your environment. Say APT29 is using a malicious executable. A threat intelligence platform will gather this information, enrich it with context, and give you this data. You can then feed this data into your security solution to automatically alert you if this executable is seen in your environment. There is no need to clumsily put together a list of IOCs and run a threat hunting query. Integrating a TIP into your chosen security solution does this for you. This saves you time and manpower that can be better used elsewhere.
Keeping up-to-date with current threats and automatically alerting is made easy with a TIP. Tailor the threats you want to ingest based on who is likely to target your organization and integrate the TIP with your chosen security solution to detect the latest threats hassle-free.
Reason #3: Distribute threat intelligence to the right people swiftly
How does your business distribute the threat intelligence it ingests?
You could do this manually, where a lone analyst will compile and email key members of your organization information about the latest threats. Or your cyber security program has not yet reached maturity to integrate with threat intelligence. Suppose either of these scenarios describes your cyber security program. In that case, it is time to upgrade and use the power of automation to ensure decision-makers have the information they need.
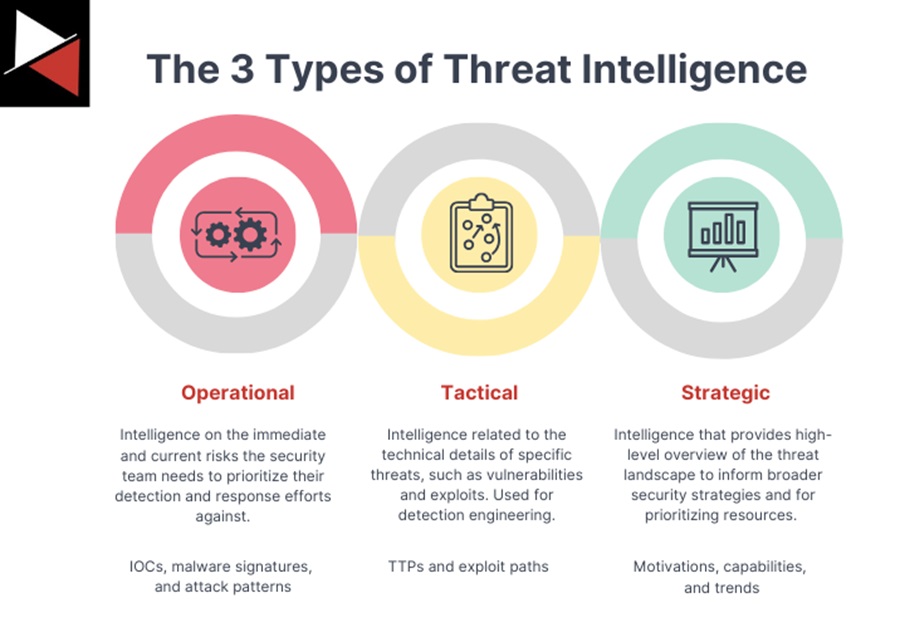
Threat intelligence platforms can ingest multiple threat feeds, analyze this data, and then distribute it to the appropriate teams within an organization. For instance, a security analyst needs operational threat intelligence to identify IOCs in the environment. In contrast, their manager needs strategic intelligence to discover trends across the threat landscape and areas their team needs to focus on. A threat intelligence platform can make this distinction and even automate the distribution of this data. It can automatically ingest and feed your security solution with the IOCs from the latest threats, email C-suite with a high-level overview of the threat landscape, and add contextual data to alerts to streamline investigations.
Find out more about turning threat intelligence to threat hunting material in Threat Intelligence vs Threat Hunting: What is the Perfect Pipeline?
The timeliness of information is vital for decision-makers up and down the hierarchy at any business. To ease the burden of ensuring consistent distribution of intelligence, a TIP can be used to automate this process and free up an analyst’s time for more important work.
Analysts want to build detections or investigate real threats, activities that improve the security posture of organizations. The re-packaging and distribution of threat intelligence are better left to a computer that can do this job 24/7 and more efficiently.
Reason #4: Give context to alerts to streamline investigations
Modern Security Operations Centers (SOCs) are flooded with alerts that they need to rapidly investigate and respond to.
Unfortunately, many security solutions lack context around the alerts they generate which forces analysts to chase up users and system administrators to make a best guess about whether an alert is genuine or just a false positive. This saps their time and energy, decreasing the SOC’s ability to quickly respond to real incidents.
A TIP offers a solution to this problem. They can provide additional context around an IOC that may have triggered an alert. This context provides insight into what things to expect if a malicious actor triggered this IOC, such as the adversary associated with the IOC, the common TTPs seen used in conjunction with the IOC, etc. If my days working in a SOC taught me anything, it is that the more context you have around an alert the easier it is to decide whether or not it is a false positive.
A TIP provides this additional context and provides it on one pane of glass. An analyst does not need to trawl through resources or web pages to find an answer. Anytime analysts can find what they need on one screen the better!
To cope with the number of alerts generate by modern IT environments a SOC needs a streamlined approach to investigations, incorporating a TIP goes a long way to doing this.
Reason #5: Automation is the king, let it scale your processes
Automation allows you to distribute threat intelligence to the right people quickly and can also be used to scale your cyber security program to new heights.
As any business scales, its cyber security program must scale to match. More employees mean more alerts are generated for the SOC to investigate. This was a major pain point for many businesses in the past, as it was expensive and time-consuming to grow a SOC. However, with the advent of automation, this process can be made a lot simpler.
Threat intelligence platforms allow you to ingest many data points (e.g., IOCs, TTPs, etc.) into a single security solution (e.g., SIEM) and automate alerting, distribution, and investigations. This is great for any business but can be a game changer for a growing start-up or company looking to expand its operations.
Why?
Because the security team can focus on a single pane of glass, the IOCs all come through to one place, the information that provides context to these IOCs comes to one place, the alerts come to one place, and investigations are all done in one place. Once a TIP is integrated with your chosen security solution, analysts do not need to jump between platforms to piece together information (or at least significantly less of this), as everything they need (and need to do) can be found at a central location due to automation.
If a new IOC is found for the latest malware strain and this is present in your environment, all an analyst needs to do is log in to your security solution, see the alert, and respond in the platform. There is no need to find the IOC on some website, manually search for it in the environment, create an investigation, and then respond. The process is automated so your business can scale rapidly!
New endpoints can be added, new networks can be added, and they can be protected against automatically by integrating the latest threat intelligence (automatically). Harnessing the power of automation lets your business and security program grow in sweet unison when you invest in a TIP.
Things to consider before investing
If you are now itching to buy into a threat intelligence platform, there should be some things you keep in mind before investing.
Despite all the benefits they can bring to any business, there are some things that a TIP may struggle with:
- Triaging intelligence — These platforms are very good at scoring static IOCs (rating the likelihood of a real incident if an IOC is seen). However, they struggle with behavioral detections (TTPs). For instance, if an executable runs from a zip file (a potential TTP), they may either escalate this as high severity and generate too many false positives or completely ignore it. They work well for static intelligence (hashes, IPs, domains), but for TTPs, you need a well-trained human to decide what is malicious or not.
- Enriching intelligence — Despite the best effort to provide context to every piece of intelligence, these platforms can fall short, and you may need to enrich the intelligence by searching other data sources. A TIP is limited in the context it can provide (compared to the entire Internet), so some IOCs may only be enriched with a generic context or not enriched at all. This then forces an analyst to move away from the single pane of glass.
- Automating the entire pipeline — These platforms are designed to ingest intelligence and allow users to integrate this aggregated intelligence with other platforms or applications. The TIP alone cannot generate alerts to investigate. Your security program still needs a SIEM or EDR tool that integrates with a TIP.
Threat intelligence platforms can significantly boost your cyber security program and dramatically improve your cyber security posture. That said, they are just a piece of the puzzle. Your security program still needs other tools and skilled analysts to protect your business’s assets. Use a threat intelligence platform to automate tedious processes and augment investigations, but don’t rely on them for all your security needs.




