Let’s take a look at a cool new tool that we can add to our threat hunting arsenal!
The tool we’re taking a look at today is called whodunit and it’s goal is adversary attribution.
Whodunit is a tool that can be used to identify the most likely Advanced Persistent Threat (APT) group responsible for an attack. The tool ingests a cyber security report that contains MITRE ATT&CK techniques identified in an attack and then outputs the APT groups most likely to have been responsible for the incident.
Installation and Execution
The whodunit tool is written in Python and can be found on GitLab at https://gitlab.com/bontchev/whodunit and can be installed with the following commands:
git clone https://gitlab.com/bontchev/whodunit.git
cd whodunit
pip install -r requirements.txt
python3 whodunit.py -hThe install steps are shown below.
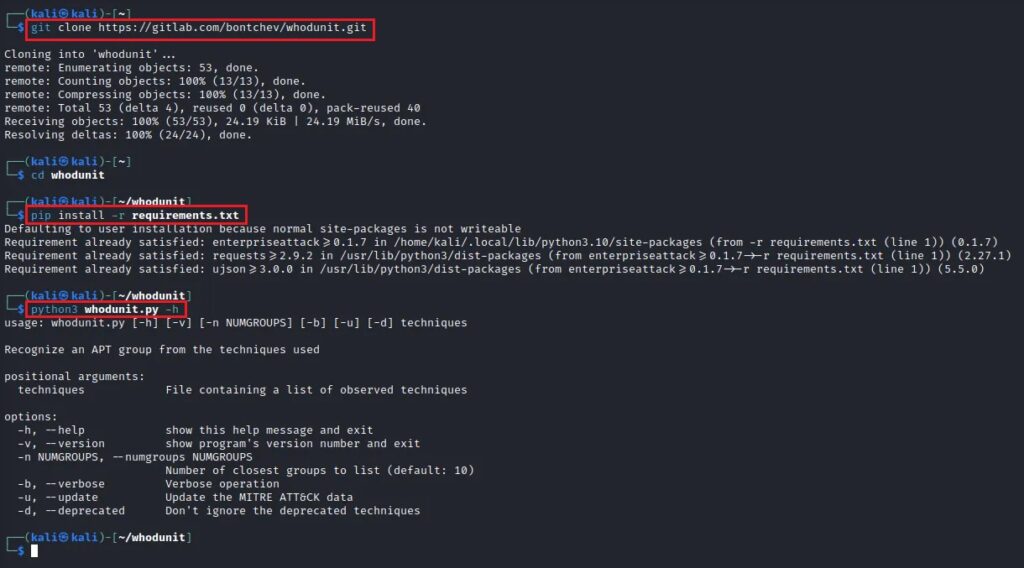
There is a small sample report that comes with the tool named report.txt which you can use to demonstrate the tool’s capabilities. This text file is a simple threat intelligence report which includes several MITRE ATT&CK techniques. Executing the tool, with this report as input, is shown below.
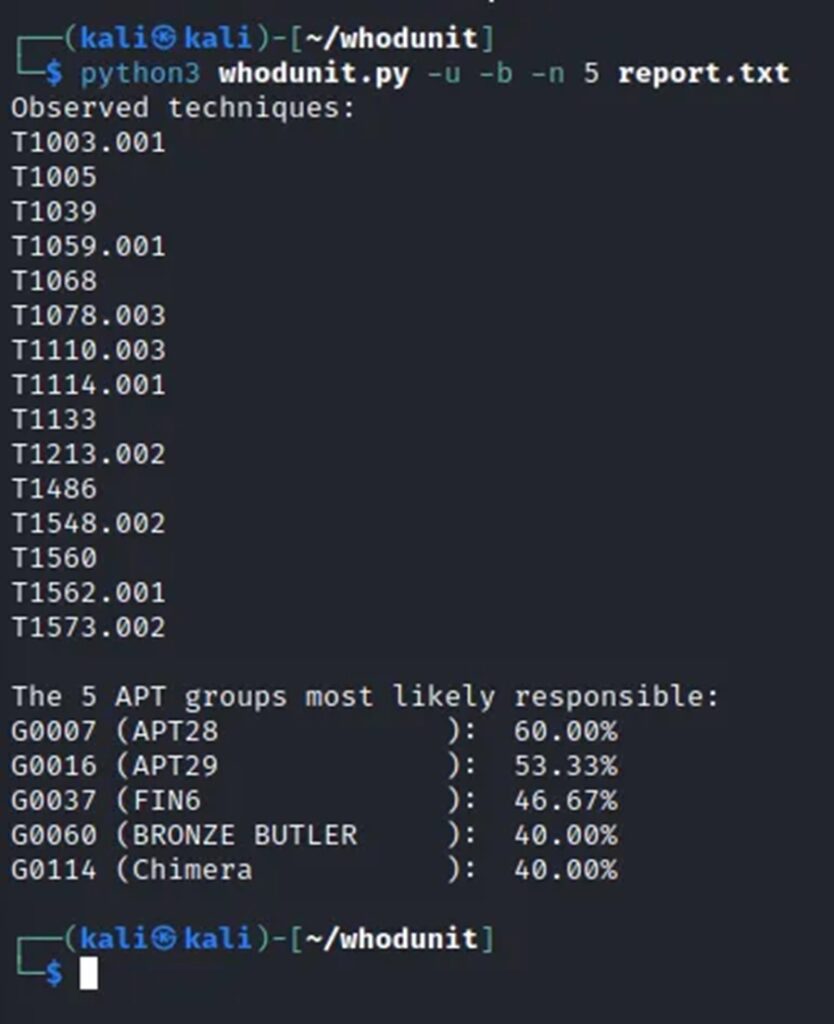
So it’s APT28 we need to take off our Christmas card list.
How Can whodunit Help Me?
Adversary attribution is a very difficult problem to solve.
- Did the Russians do this cyber attack?
- Did China do this cyber attack but pretended to be Russia to avoid blame?
- Did the US do this cyber attack but framed China framing Russia to achieve some political motive?
As you can see, there is a lot of whodunits in there.
However, this is at the international espionage level where tradecraft and deceit are the pillars of a successful operation. In the world of cyber crime, the world the majority of Threat Intelligence Analysts interact with (despite the news paper headlines being keen to attribute an attack to a nation), mimicking another cyber crime group to a degree where it is indistinguishable it considerably less likely. Hence, for your everyday analysts this may be a useful tool.
“I am here to make money from my ransomware, not spend millions trying to reverse engineer someone Barry.” I imagine Bob the ransomware lead would say.
Now how can I use this to actually help me with my work? Saying APT28 probably did it to my boss isn’t going to cut it.
I agree! Attribution without action is as useful as ice cream without a freezer. To make this information actionable we need to look at ways attributing an attack to an APT group may help us take steps to recover or prevent breaches in the future.
The use case I see this tool fulfilling is expanding existing threat intelligence during an investigation. For instance, if you discover several MITRE ATT&CK techniques in your environment, you can plug them into this tool to deduce who the likely culprit is. From this output, you can then research the APT group identified, which will lead you to discover more MITRE ATT&CK techniques you can then hunt for in your environment.
Take this as an example. You, a Threat Intelligence Analyst, receive a report from the Security Operations Centre (SOC) team that technique T1078.003 (Valid Accounts: Local Accounts) has been observed in your environment along with T1059.001 (Command and Scripting Interpreter: PowerShell) T1110.003 (Brute Force: Password Spraying), and T1114.001 (Email Collection: Local Email Collection). You now use these techniques as input for whodunit and get back APT28 as the likely group.
You can now research that group using Google or MITRE’s Groups database to get a list of techniques and software that the group is known to use. Using this list you can check if your environment has security solutions in-place to detect/mitigate these potential techniques. For instance, APT28 utilises T1003.001 (OS Credential Dumping: LSASS Memory). Do you have protections that defend against this? (like an EDR rule).
You can see how to extract MITRE ATT&CK techniques from threat intelligence articles in this post.
Going from “Oh this tool is interesting” to “This tool makes my investigations more efficient through automation” involves just a little extrapolation. This will certainly be a tool I will add to my threat hunting arsenal and one I hope you will consider playing around with at the very least.




