Cyber attacks are everywhere. They are a constant in the news, they plaster social media, and your mate Steve won’t stop going on about them. All you hear is how hackers steal secrets and ransomware gangs extort businesses for thousands or even millions of USD, GBR, or EUR (no currency is safe). You don’t hear about how to fight back against these cyber threats.
To combat cyber threats, you need to understand the hacker mindset. What they are after, how they think, and the tactics/techniques/procedures (TTPs) they use to compromise systems.
This article explores how you can begin understanding the adversary by performing threat profiling to map out how they might attack your organization using the MITRE ATT&CK matrix. It goes into practical detail about performing threat profiling and generating a list of TTPs you need to ensure you have strong mitigations or detections in place to defend against.
Let’s get started by exploring what threat profiling is and how it can benefit you.
What is Threat Profiling?
Threat profiling is the process of identifying, assessing, and prioritizing threats an organization is likely to face. Using threat intelligence, you create profiles of the threats an organization might face and detail their capabilities, motivations, and potential impact on your organization’s assets (e.g., operations and sensitive information).
You can perform threat profiling on various threats:
- Groups (threat actors) who might target your organization
- Software that might be used against your organization
- Data sources that protect critical assets
- Incidents you have faced in the past.
Threat profiling gives you a comprehensive understanding of the threat landscape so you can create informed security strategies, know where to allocate resources, and produce mitigations to battle and neutralize attacks. Let’s look at how to perform threat profiling practically.
Profiling Threat Actors
Threat actors include ransomware gangs, cyber criminals, and Advanced Persistent Threats (APTs). They want to attack your organization because you have something of value to them, be it data they can sell for profit or operations they can hold for ransom. These groups are your primary threat and what you need to focus on defending against.
To defend against these adversaries, you need to understand them and answer questions like:
- Which group is likely to attack you?
- How will they likely attack you?
- What mitigations or detections can you create to defend against them?
Luckily, you can use MITRE as a starting point to answer these questions. MITRE has a framework called the MITRE ATT&CK matrix that contains a list of Tactics, Techniques, and Procedures (TTPs) adversaries use to perform a cyber attack. They also track threat actors, which they map to TTPs and software the group has been known to use on their MITRE Groups webpage. You can use these two resources to profile threat actors in two simple steps.
You can learn more about the MITRE ATT&CK framework in MITRE ATT&CK Framework: The Holy Bible of Threat Intelligence.
Step 1: Finding Threat Actors
First, you need to find threat actors likely to target your organization. You can do this by performing your own research on adversaries or by using the MITRE Groups webpage (if you are new to threat profiling, I recommend the latter).

For example, if you worked for a US-based company in the medical field, you could start by searching for all threat actors who target the medical sector.
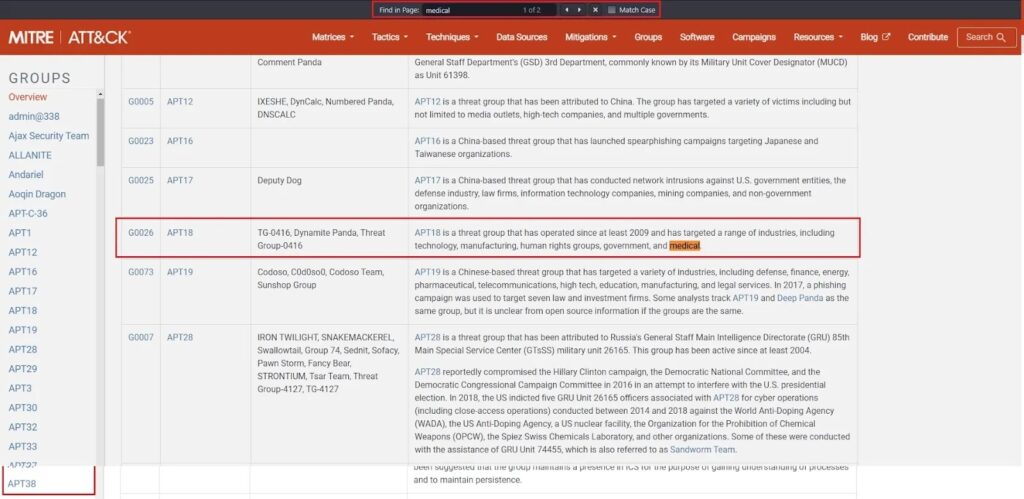
This lets you create an initial list of threat actors to focus on. To narrow down this list, you could focus on threat actors who target the medical sector AND target US-based companies.
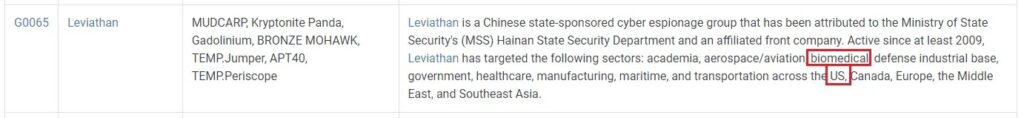
To further narrow down your list, you want to focus on threat actors who have been active within the last 12-18 months – no need to look at groups from the 1990s.
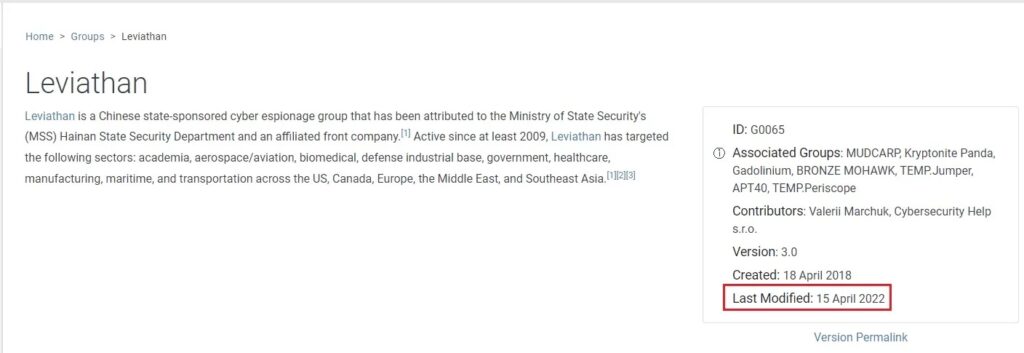
Great! You have a list of threat actors who might target your company. It’s time for the next step of the threat profiling process.
Step 2: Mapping their TTPs
Once you have a list of threat actors, you now need to know what TTPs these groups use when they attack an organization. You can get this list of TTPs by performing your own research or using the MITRE Groups webpage (again, the latter is the easier option).
Let’s say we want to map the TTPs of groups APT18, Leviathan, and HAFNIUM. First, you need a way of mapping these TTPs, which you can then analyze. The easiest way is with an Excel spreadsheet or Google sheet. Column 1 contains the list of MITRE ATT&CK techniques, and columns 2 onwards contain the names of the threat actors you are profiling.
You can find the latest list of MITRE ATT&CK techniques in Excel form here under ATT&CK in Excel. Just download the Excel file and copy the techniques to your spreadsheet. This will save you from manually filling in each one.
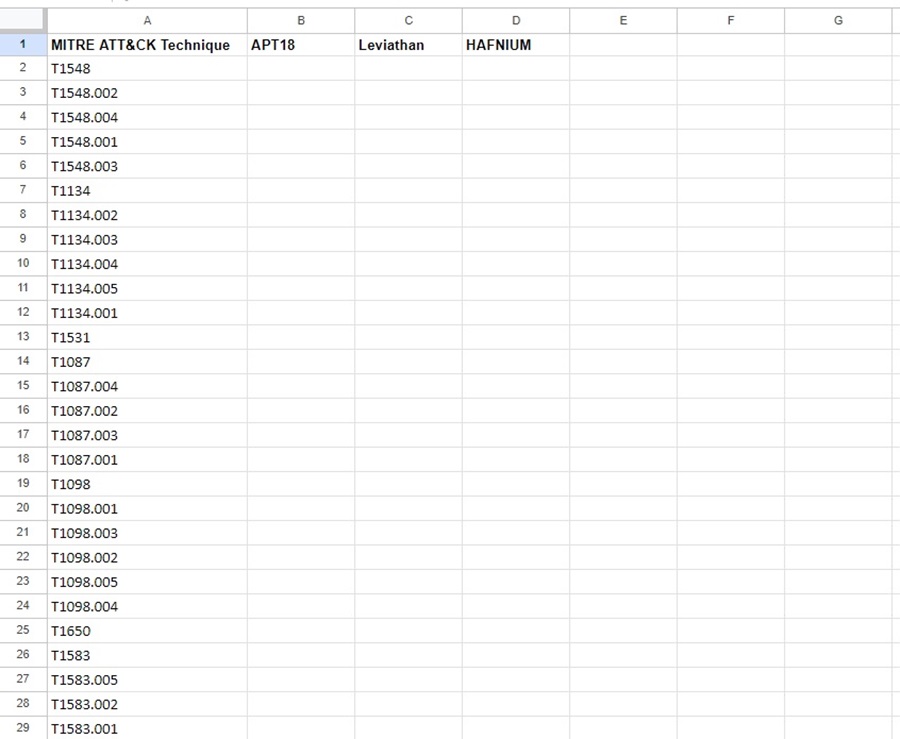
With your threat profiling documentation created, you can now move on to the “fun” part, finding all the TTPs a threat actor has been known to use. You can do this using MITRE Groups by visiting the group’s page and scrolling down to the Techniques Used section.

I like to put an “x” next to the technique if the group uses it so I can use an Excel formula to filter and cross-correlate the common TTPs used across groups.
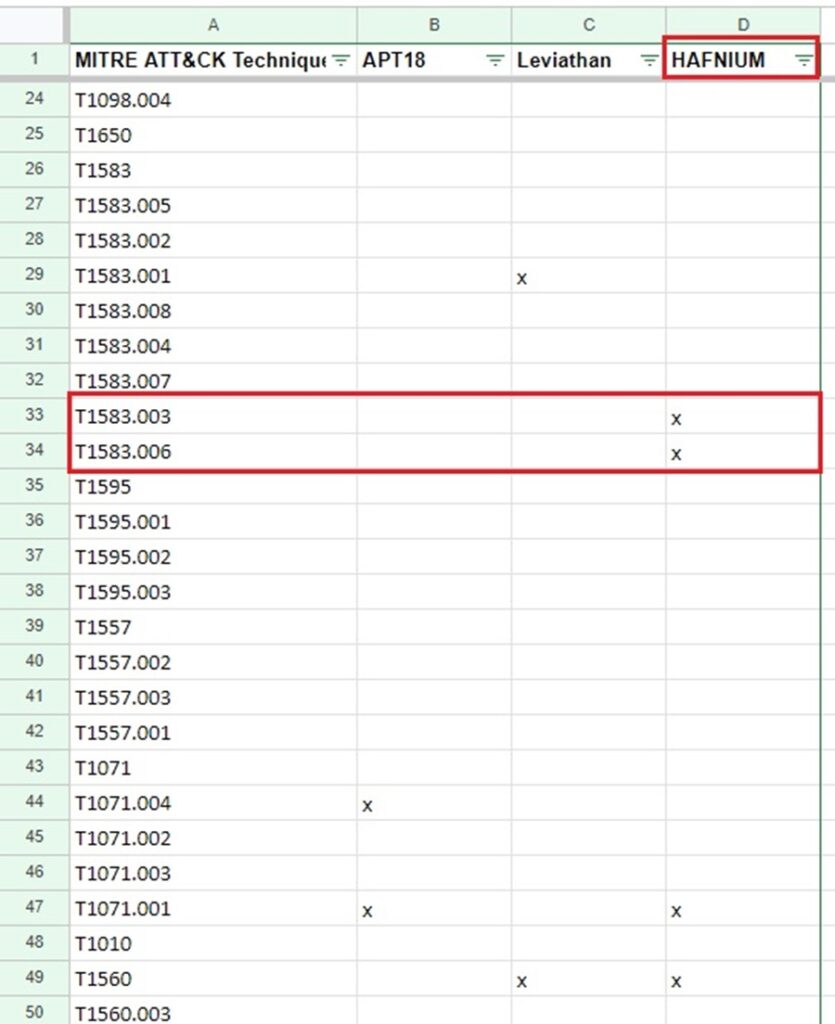
Now you can filter to see what TTPs a group uses by displaying only cells that have an “x” for a particular column in your spreadsheet.
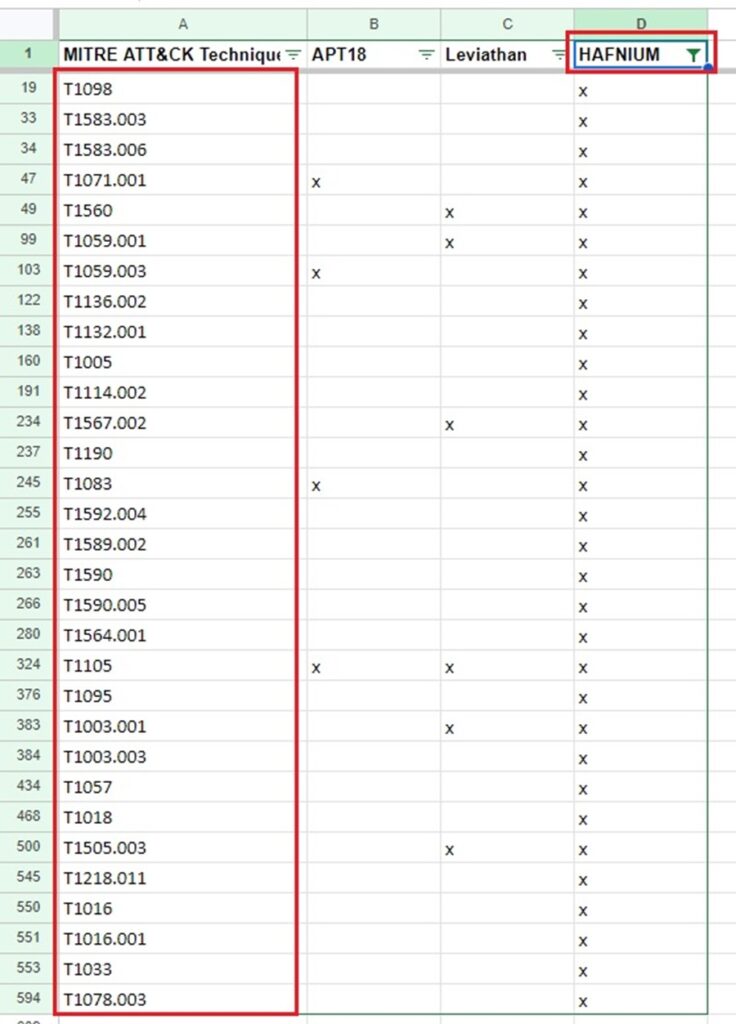
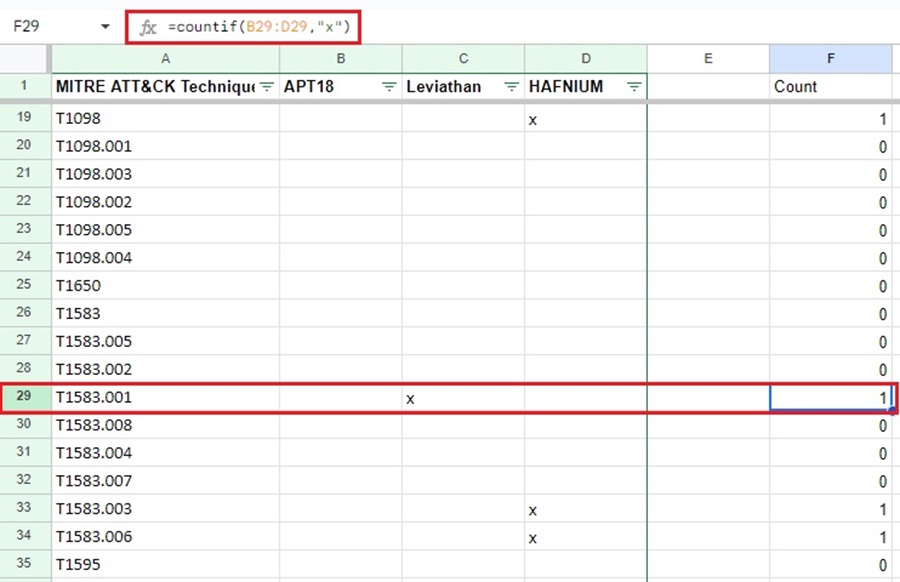
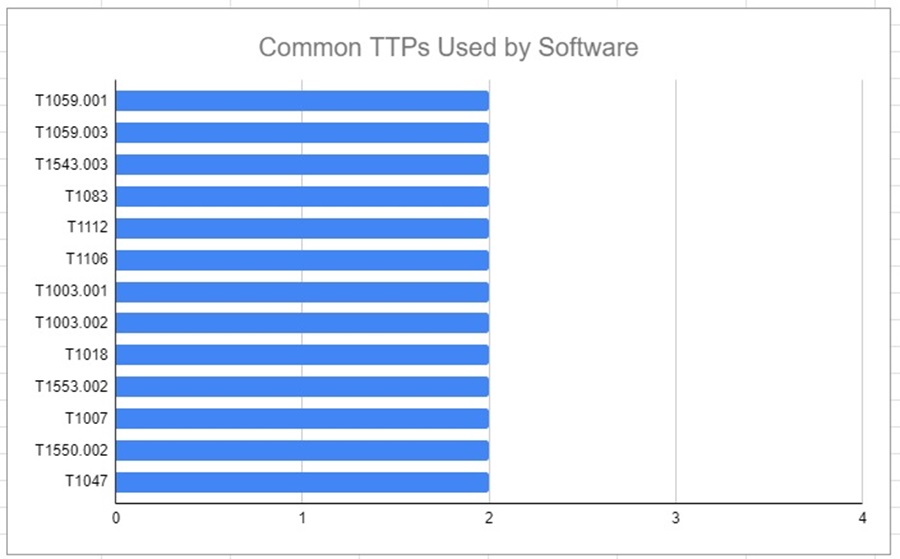
However, more powerfully, you can insert a Count column and use an Excel formula to count the number of cells in a row with an “x” present. This lets’ you cross-correlated TTPs among several groups so you can see what TTPs each group has in common.
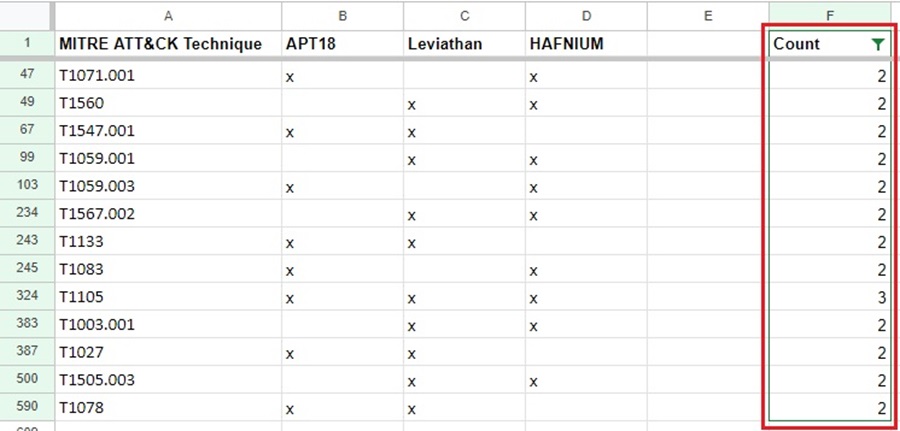
You can even turn this data into a pretty graph to show your manager.
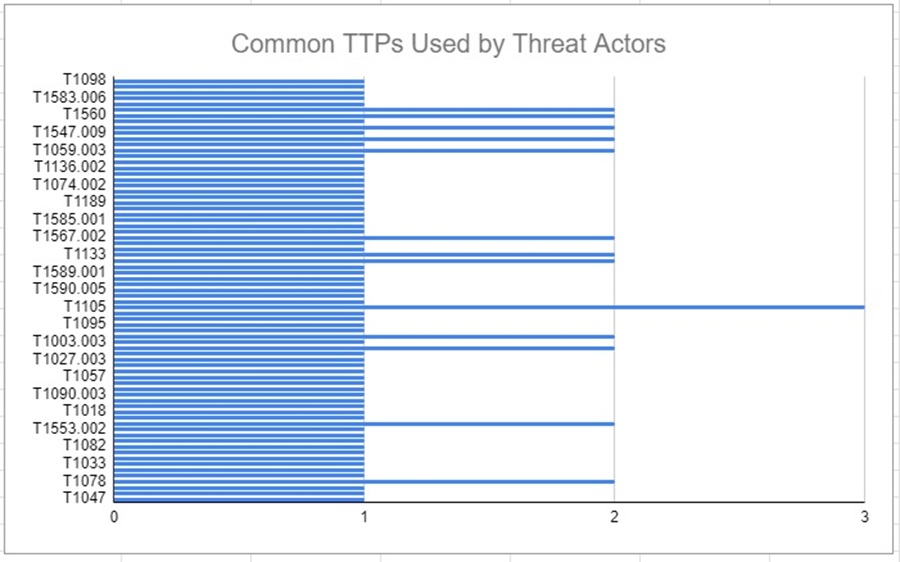
You can play around with this data to show TTPs common across multiple groups (e.g., TTPs that appear across 2 or 3 groups) and create a list of TTPs you want to focus on mitigating and detecting based on the threat intelligence you gathered.
You can learn how to mitigate and detect TTPs by visiting the TTP on MITRE’s Enterprise Techniques page, selecting the TTP, and scrolling down to the Mitigations and Detections sections.
Profiling Software
Software is the malware or hacking tools threat actors use against your organization during a cyber attack. It can be anything from ransomware, post-exploitation credential stealers, or living off-the-land software (LOLBAS). To defend against malicious software, you need to know what TTPs this software uses to achieve its objective. Again, you can use another MITRE resource to simplify this process.
The MITRE Software webpage lists the “custom or commercial code, operating system utilities, open-source software, or other tools used to conduct behavior modeled in ATT&CK” framework. You can use this resource to perform threat profiling by
- Finding software that is likely to be used against your organization
- Mapping its TTPs to create a prioritized list.
You can learn how to defend yourself from TTPs using Sigma rules in How to Arm Yourself with Threat Intelligence.
Step 1: Finding Software
To find software that is likely to target your organization, you can focus on
- The assets your company uses (e.g., Windows or macOS endpoints, Windows or Linux servers, etc.).
- The priority of malicious software you want to mitigate or detect (e.g., ransomware or crypto-miners).
- The software that is popular among threat actors (e.g., mimikatz or Cobalt Strike).
How you prioritize which software you want to focus on threat profiling is specific to your organization. However, let’s say you want to focus on the mimikatz password stealer, the C2 Cobalt Strike, and Black Basta ransomware because they are popular among threat actors. You can find details about each of these on the MITRE Software webpage and their associated TTPs.
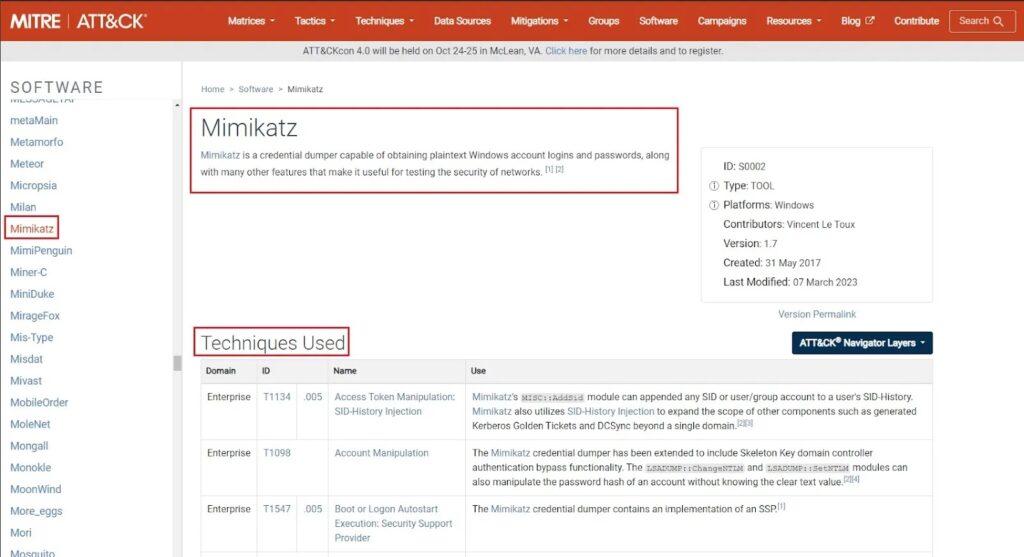
Step 2: Mapping TTPs
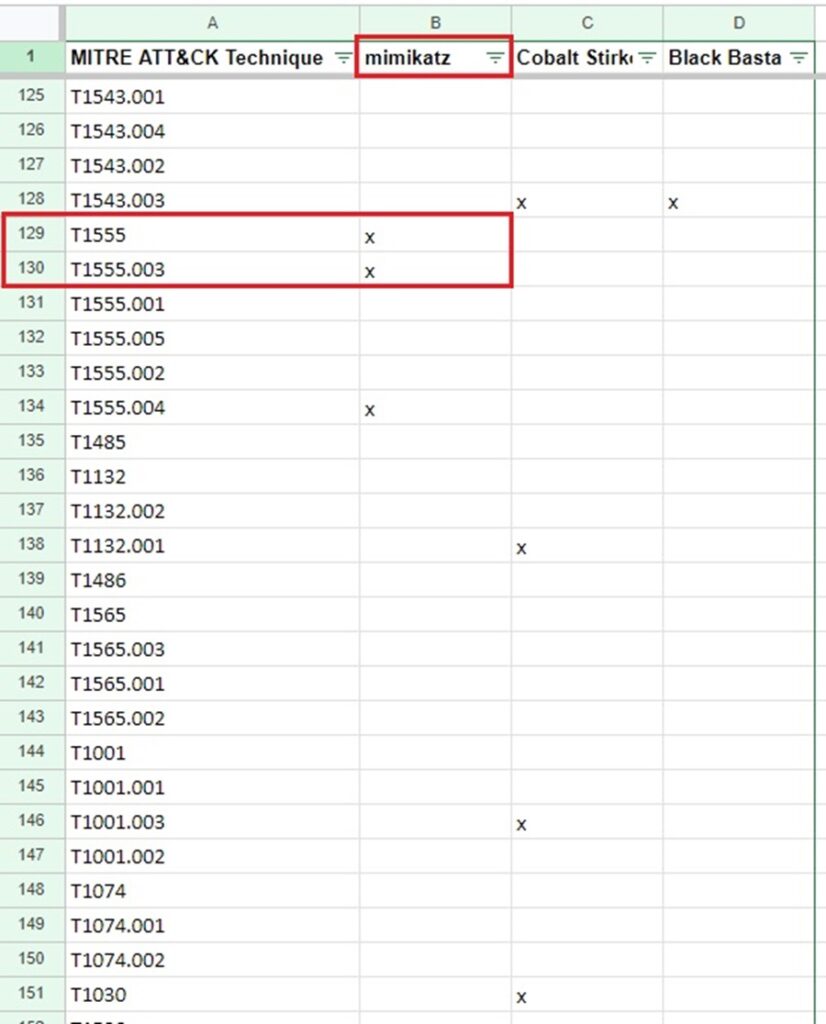
Scrolling down to the bottom of each software’s page, you will see their associated TTPs under the Techniques Used section. You can follow the same process as you did when mapping out threat actor TTPs with each software you identified. Column 1 contains the list of MITRE ATT&CK techniques, and columns 2 onwards contain the names of the software you are profiling.
Again, you put an “x” next to the technique if the software uses it, and you can then create filters and formulas to analyze this data.
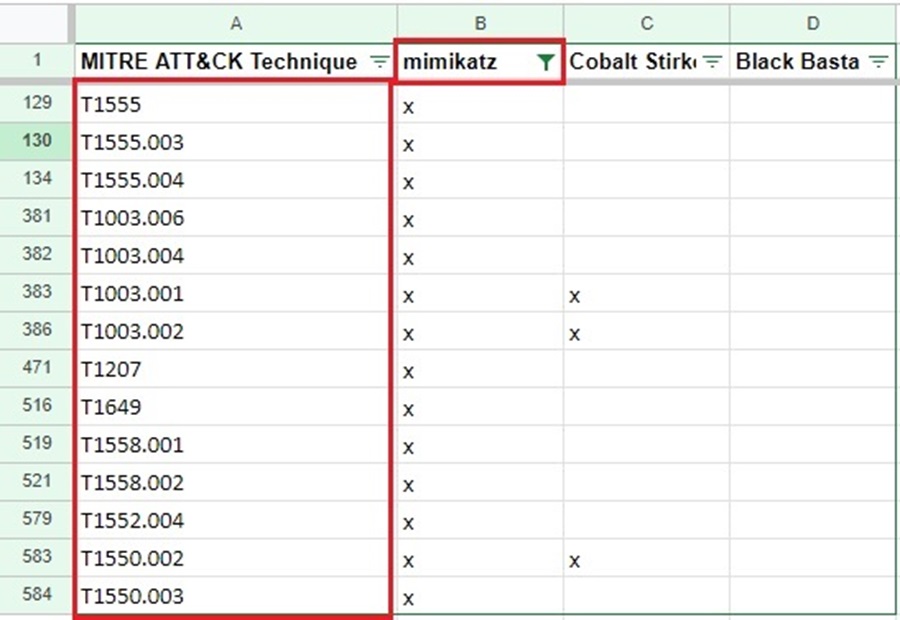
Profiling Data Sources
According to MITRE, “Data sources represent the various subjects/topics of information that can be collected by sensors/logs. Data sources also include data components, which identify specific properties/values of a data source relevant to detecting a given ATT&CK technique or sub-technique.” This can be application logs, Active Directory (AD) logs, system logs, etc.
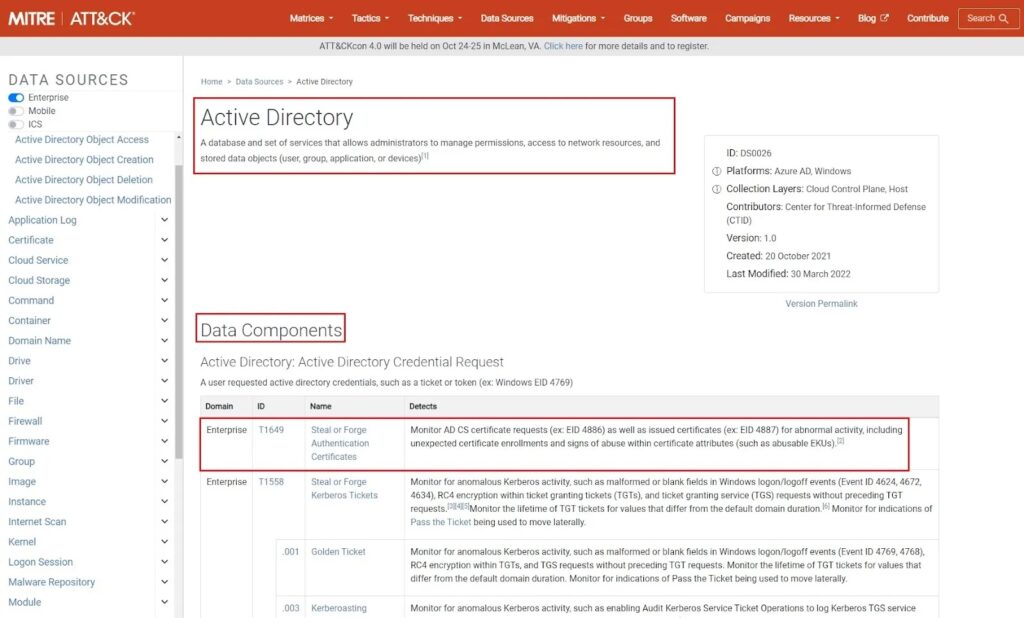
You can perform threat profiling on data sources that protect or log the activity of your organization’s critical assets. This will reveal what TTPs these data sources can be used to detect/mitigate and provide you with a list of TTPs to prioritize. Again, this is a two-step process.
Step 1: Identifying Data Sources
First, you must identify the data sources that protect or log the activity of your organization’s critical assets. You can do this by performing a crown jewel analysis, looking at data sources affected by past incidents, or focusing on assets that will have the greatest impact on your organization if compromised.
How you prioritize the data sources you want to focus on threat profiling is specific to your organization. However, common ones include Active Directory, Application Log, and Firewall. You can find details about each of these on the MITRE Data Sources webpage and the TTPs they can be used to detect or mitigate.
Step 2: Mapping their TTPs
The Data Components section on each data source page contains a list of the TTPs each data source can be used to mitigate or detect. You can use this information to perform a threat profile of each data source your organization wants to prioritize creating mitigations/detection for.
You can follow the same process as you did when mapping out threat actor and software TTPs by using column 1 as a list of MITRE ATT&CK techniques and columns 2 onwards for the names of the data sources you are profiling. Put an “x” next to the technique if the data source can be used to detect or mitigate it, then you can create filters and formulas to analyze this data.
Profiling Past Incidents
Past incidents are previous cyber-related incidents that have been detected, investigated, and remediated by your organization. There should be detailed notes that describe the incident. You can use these notes to deduce the TTPs seen in the incident for your threat profiling.
To threat profile past incidents, you cannot just rely on MITRE. You need to do some of your own work. You must research the past incidents at your organization (hopefully, they have a comprehensive documentation system), use your knowledge of cyber attacks to deduce the TTPs seen in an incident from the language used to describe what happened, and then look up these TTPs using the MITRE ATT&CK framework.
Step 1: Researching Past Incidents
How you research past incidents at your organization is specific to your company. However, here are some common things to use:
- Past penetration testing, red teaming, or purple teaming reports.
- Service desk reports.
- SOC documentation of detections, investigations, and remediations.
- Discussions with colleagues or your manager about what threats your organization has previously encountered.
The research phase ends when you have several case descriptions of past incidents your organization has dealt with. These will often be in text form and require deducing the TTPs involved.
Step 2: Deducing TTPs
The next step is to deduce the TTPs involved in the incidents you have researched. You will need to find “attack language” in the descriptions of these incidents and match it to MITRE’s descriptions of the techniques in its ATT&CK matrix.
Examples of “attack language” include:
- Phishing email
- DDoS (Distributed Denial of Service ) or DoS
- Lateral movement
- Initial access
- Stolen credentials
- Elevated privileges
- Exfiltrated data
- C2 (Command and Control) server
- Brute force attack
Looking for phrases like these in the description of the incident lets you understand (a) which stage of the attack kill chain they cover (what MITRE tactic) and (b) the possible technique used at this stage. To answer (b), you must look for more context around the incidents.
For example, if it says an email was involved. Try answering:
- Was it a general phishing email aimed at many employees?
- Was it a specific phishing email only sent to a high-value target (e.g., manager, executive, etc.)?
- Was there an attachment that was executed or a link that was clicked?
If you can find the answers to these questions, you can determine the specific MITRE technique
Used.
Often, mapping past incidents to the MITRE ATT&CK matrix can be difficult, and you will need to do some Googling to find an answer that fits. I find it useful to search the “attack language” used to describe an incident directly in MITRE.
For instance, if a report describes that DDoS occurred, I would just search for that term using MITRE’s search bar to find possible techniques that could be used.
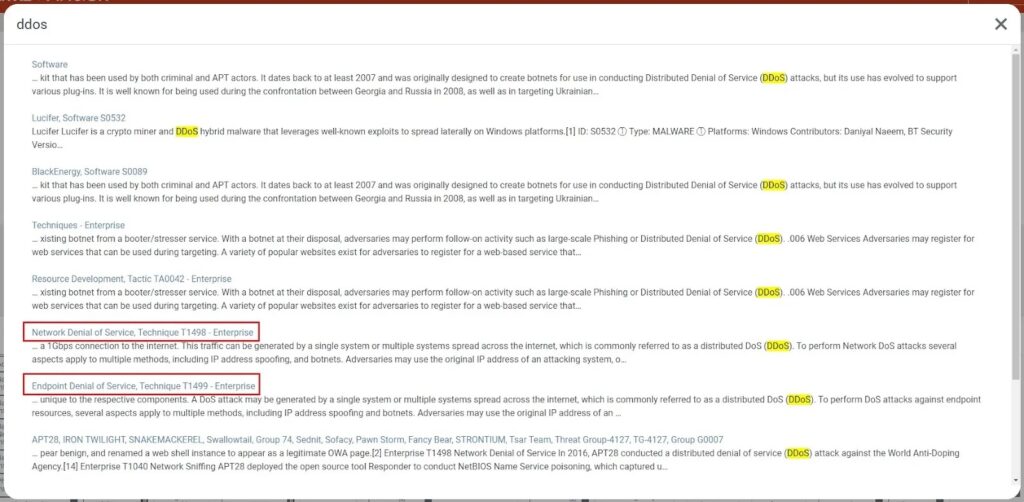
Here, a denial-of-service attack technique matches one of two descriptions. To answer which description, I need to know whether the attack was against a network device or an endpoint by trying to find additional context in the incident report.
Step 3: Mapping TTPs
Once you have deduced what TTPs were present in past incidents, you need to map it to the MITRE ATT&CK matrix as you did before. You can follow the same process as before by putting an “x” next to the technique in the Excel spreadsheet and then analyzing the data.
Summary
Threat profiling involves identifying, assessing, and prioritizing threats your organization will likely face. These threats could be threat actors that target you, the software used against you, or past incidents you can learn from. You can also find what threats you must protect against in the data sources used to protect your most critical assets.
Once you identify the threats, you need to map these to the MITRE ATT&CK matrix to discover what TTPs a threat will likely use against you. By doing this, you can generate a list of detections or mitigations that you can put in place to defend against these threats.
This article detailed how to use MITRE and a simple Excel spreadsheet to perform this process. As threats evolve over time, you need a way to keep up with the TTPs they use. One option is to redo this threat profiling exercise, another option is to track the TTPs using a dedicated threat intelligence database like MISP.
I will be exploring MISP in future articles, so stay tuned to discover how you can utilize this open-source threat intelligence platform.