Welcome back to the Kraven Security weekly newsletter, triaging the week. We round up the week’s top news stories, highlight our featured article, give you some learning resources, and finish with a few personal notes about what’s happening at the company. Enjoy!
This week, the US Department of State offered a massive $10 million for information about Hive ransomware leaders. It is an eye-watering amount, but something we may see more of as malware continues to get more sophisticated, with the Glupteba botnet now exploiting an undocumented UEFI bootkit and hackers manipulating Ubuntu’s ‘command-not-found’ utility to trick users into downloading malicious.
We also learned about 200,000 Facebook Marketplace credentials being leaked and a new critical privilege escalation vulnerability in Zoom. Not a great time to be a user. However, to brighten up your weekend, I have included several fun learning resources for you, from interviews with industry experts to comical videos on the dangers of cloud computing for your wallet. Let’s get started.
Top 5 News Stories

Story #1: US Offers $10M Bounty for Hive Ransomware Leaders
The US Department of State has announced a $10 million bounty for information leading to the arrest of the Hive ransomware leaders, along with an additional $5 million for details that could result in arrests or convictions of those involved in the ransomware activity.
Hive has targeted over 1,500 victims and netted about $100 million in illegal revenues, making them a major player in 2023. A year, ransomware groups raked in $1.1 billion in extorted victims. The ransomware arena continues to evolve with a surge in new entrants and offshoots, a shift to big game hunting, a pivot to cross-chain bridges and gambling services for money laundering, and a weaponization of security vulnerabilities for initial access.
Story #2: Glupteba Botnet Exploits an Undocumented UEFI Bootkit
Glupteba botnet has resurfaced with a list of advanced evasion techniques. One of these is the ability to evade detection using an undocumented UEFI bootkit, adding a new level of sophistication and stealth to its operations. This feature enables Glupteba to conceal itself and establish a covert persistence that is exceptionally challenging to detect.
Glupteba has been seen distributed as part of a multi-stage infection chain that involves phishing and several other malware families, such as PrivateLoader, SmokeLoader, RedLine Stealer, and Amadey. Identifying an undocumented UEFI bypass technique within Glupteba underscores this malware’s capacity for innovation and evasion—a stand-out example of the complexity and adaptability of modern cybercriminals.
Story #3: Hackers Abuse Ubuntu “Command-Not-Found” Tool
New research has revealed that threat actors could manipulate Ubuntu’s ‘command-not-found’ utility to recommend rogue packages and compromise systems. The utility uses an internal database that attackers can exploit by registering rogue snaps with the same name or alias as legitimate commands, potentially leading to a supply chain attack.
Around 26% of the APT package commands are vulnerable to this impersonation attack. Users are advised to verify the source and credibility of the packages before installation. Developers should also claim the associated snap name for their commands to prevent them from being misused.
Story #4: 200,000 Facebook Marketplace User Records Leaked
A threat actor leaked 200,000 records of Facebook Marketplace users on a hacker forum, claiming another hacker stole them from a Meta contractor. The leaked data contains names, phone numbers, email addresses, Facebook IDs, and profile information of Facebook Marketplace users, which can be used for phishing, SIM swapping, and other malicious purposes.
This is not the first time Meta has faced data breaches and leaks involving its users’ personal information. In 2021, data from over 533 million Facebook accounts was leaked online, resulting in a hefty fine from the Irish Data Protection Commission.
Story #5: Critical Privilege Escalation Flaw in Zoom
Zoom has recently addressed a privilege elevation flaw affecting its Windows apps that could expose users to potential exploitation. The vulnerability exists in the Zoom desktop version for Windows, specifically the VDI client and the Meeting SDK for Windows, and has been rated a 9.6 CVSS score. It is being tracked as CVE-2024-24691.
Users are urged to upgrade to the latest desktop client release for Windows, version 5.17.7, which also addresses six other vulnerabilities with lower severity ratings.
Top Tips of the Week

Threat Intelligence
- Stay informed on emerging threats. Regularly update your threat intelligence sources for accurate and relevant insights.
- Engage in threat intelligence forums in cyber threat hunting. Participate in discussions to share insights and learn from others in the field.
- Foster cross-industry threat intelligence collaboration. Learn from and share insights with organizations facing similar threats.
Threat Hunting
- Develop threat hunting playbooks in cyber threat hunting. Standardize procedures for consistent and effective detection and response.
- Investigate patterns, not just incidents, in cyber threat hunting. Recognizing patterns aids in understanding tactics and identifying potential threats.
- Simulate tabletop exercises for threat scenarios. Practice response strategies for effective threat hunting.
Custom Tooling
- Educate your team on using custom tools. Provide training and resources to maximize the benefits of your creations.
Feature Article
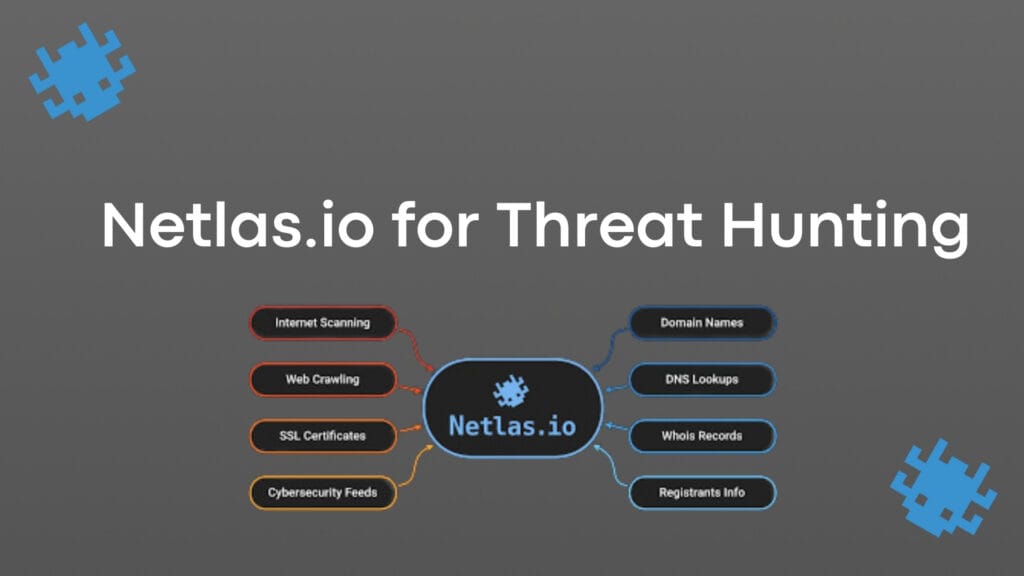
There is a powerful new suite of tools for threat hunting called Netlas.io. This innovative platform allows you to hunt across a vast network dataset collected from across the globe. You can use this data to enrich your threat hunts, add additional threat intelligence to your investigations, and map the attack surface of adversaries.
In this article, you will discover what makes this platform so powerful and how to use it to perform link analysis that takes your threat hunts to the next level. Let’s jump in and get started by learning what Netlas.io actually is.
Learning Resources

AMA With the Pentesting Team at Trustedsec
Listen to this great Ask Me Anything on pentesting, hosted by the team at TrustedSec. These seasoned professionals share their insights on everything from their tools to dealing with clients. A video for anyone interested in pentesting or red teaming.
Master the Power of grep
Learn about the powerful Linux command line pattern matching tool grep. This quick guide will show you the basics of grep, popular use cases, and how to make the most of this epic core utility.
Interested in the Cloud? Don’t Fall into These Traps
In this video, the legendary faceless YouTube creator Fireship walks you through how big cloud providers like AWS, Microsoft Azure, and Google Cloud operate from a business perspective. Then, he reveals how you can optimize your cloud computing costs and avoid vendor lock-in.
Discover a Better Way to Navigate the Terminal
A new directory navigation tool is out, and it is awesome! Check out this quick guide on zoxide, a “smarter cd command, inspired by z and autojump.” If you love using the Linux terminal, then this is a must-watch.
Personal Notes

🤔 It was my birthday this week at Kraven. To commemorate another year around the sun, I got a fancy new coffee warmer to heat up cold coffee. Who says gifts get boring the older you get? 😆
More importantly, the team took strides in bolstering our business consultation portfolio and finding new clients to help. Our mission at Kraven is to help businesses and individuals learn to make the most of threat intelligence to drive their cyber security forward. Bolstering our consultation services is a huge pillar in this mission.
Another pillar is providing accessible content so you can learn more about threat intelligence and acquire skills that will make you a key asset in any organization. As such, we are working on a series that delves into key analytical techniques that will empower you to get the most out of your intelligence. We look forward to sharing these articles with you!


