You have probably heard of the term cyber threat intelligence (CTI) before. It is constantly cited on social media, makes cyber security news daily, and is a top feature on every security vendor’s newest tool. But what is cyber threat intelligence?
CTI is a game changer for many organizations that need to battle the latest threats that are emerging on the cyber security landscape and can be used at both the operational and strategic levels. This guide dives into what CTI is, its key components, and how it is used in the cyber security industry. You will discover how to use CTI to enhance your security operations, streamline your incident response capabilities, hunt for the latest threats, and more!
Let’s dive in and demystify the murky world of CTI.
What is Cyber Threat Intelligence?
Cyber threat intelligence (CTI) is a proactive approach to defending an organization against cyber threats. It involves collecting, analyzing, and disseminating intelligence about cyber threats and potential risks an organization will face.
This definition probably makes you wonder what a “threat” is and what “intelligence” actually consists of. Use the dropdowns below to find out.
What is a threat?
A threat is any potential danger or activity that aims to compromise the confidentiality, integrity, or availability of your data, computer systems, or networks. A threat can be an entity (malicious insider, a ransomware gang, nation-state), an attack (malware, phishing, DDoS), or even an unintentional action like accidentally deleting or exposing sensitive information. In CTI, you typically focus on groups, attacks, and vulnerabilities as threats you want to track and mitigate.
What is intelligence?
Intelligence is collected, processed, and analyzed information about a competitive entity. In cyber threat intelligence, the competitive entity is someone who may affect your organization’s security, and the information about them provides insights into the threat they represent.
The primary goal of CTI is to empower operators and key stakeholders to make informed decisions.
- It empowers operators to make informed decisions when triaging, analyzing, and responding to incidents. This includes security analysts, incident responders, and threat hunters.
- It empowers key stakeholders to make informed decisions about what threats to prioritize, what technologies to invest in, and the right strategic direction to follow. This includes managers and C-suite executives.
Without CTI, organizations would be silos, each responding to threats that are hitting their front line in a reactive manner.
An organization won’t know if an indicator is associated with a particular attacker, if this is a new threat actor, or if there is existing mitigation advice to deal with a threat. They won’t know what trends are happening across the cyber security landscape and how they may need to realign their strategy to combat emerging threats. They won’t be able to make efficient, informed decisions to respond to threats effectively.
CTI is important for all businesses. The mom and papa shop down the right needs to know what threats target small businesses, just as much as Walmart needs to know how a sophisticated threat actor may try to extort them with ransomware, or a defense contractor needs to know how to defend against nation-states. The stakes are significantly different, but the underlying need to make informed cyber security decisions remains.
With this in mind, let’s take a look at the key objectives CTI aims to achieve to provide value to an organization.
Key Objectives of CTI
CTI aims to empower operators and key stakeholders to make informed decisions about everything related to cyber security. You can break the key objectives that CTI aims to deliver into operator-focused and stakeholder-focused objectives.
Operator Objectives
- Proactive defense: Empower defense against emerging threats by providing information about the latest developments.
- Enrichment: Enrich alerts with insights that streamline investigations and help prioritize incidents.
- Inform business strategy: Provide actionable intelligence to support strategic decision-making based on business goals.
- Prioritize mitigation efforts: Allow defenders to focus on the threats that are relevant to their organization and prioritize mitigations that defend against them.
- Early threat detection: Enable organizations to recognize potential cyber threats at the earliest possible stage so they can respond to them before they escalate.
- Vulnerability management: Enable organizations to identify and prioritize vulnerabilities that could be exploited by an attacker.
- Improve incident response: Enhance an organization’s incident response capabilities by providing timely and relevant intelligence about cyber incidents so they can respond swiftly and effectively.
Stakeholder Objectives
- Inform business strategy: Provide actionable intelligence to support strategic decision-making based on business goals.
- Risk mitigation: Reduce risk by keeping key stakeholders informed about the latest trends across the cyber security landscape.
- Inform business strategy: Provide actionable intelligence to support strategic decision-making based on business goals.
- Information sharing: Foster collaboration and information sharing within the cyber security community and allow organizations to build relationships.
- Compliance and regulation adherence: Ensure compliance with relevant cyber security regulations and standards by demonstrating a commitment to cyber security best practices.
To achieve these objectives, CTI collects, analyzes, and disseminates three different types of threat intelligence.
The Three Types of Threat Intelligence
Not all threat intelligence is the same. Intelligence about real-time attacks and vulnerabilities differs from intelligence about geopolitical events and emerging threats that are exploiting technological trends.
There are three primary types of threat intelligence that you can broadly categorize a piece of intelligence into; operational intelligence, tactical intelligence, and strategic intelligence.
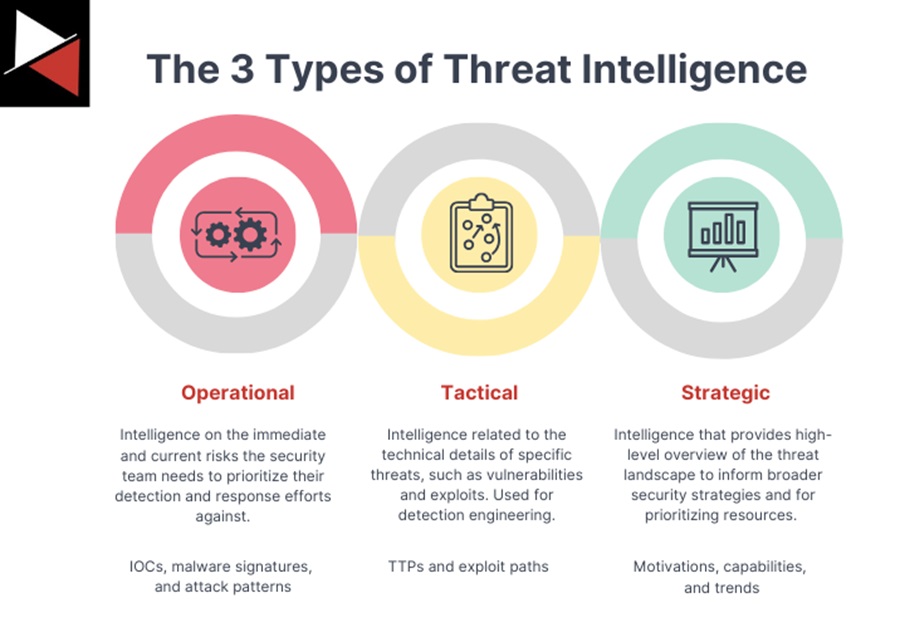
Operational Intelligence
Focus: Day-to-day security operations.
Purpose: Provide intelligence on the immediate and current risks the security team needs to prioritize their detection and response efforts against. It includes Indicators of Compromise (IOCs), malware signatures, and attack patterns.
Tactical Intelligence
Focus: Short to medium-term actions and operations.
Purpose: Provide intelligence related to the technical details of specific threats, such as vulnerabilities and exploits. Defenders use this to identify and mitigate particular threats using detection rules and mitigation policies using security tools. The focus is on targeting threat actors’ tactics, techniques, and procedures (TTPs) rather than individual indicators.
Strategic Intelligence
Focus: Long-term planning and decision-making.
Purpose: Provide a high-level overview of the threat landscape to inform broader security strategies (e.g., developing policies and procedures, resource allocation, and prioritizing investments). It includes the motivations, capabilities, and trends.
There can be confusion between operational intelligence and tactical intelligence. It is best to think of tactical intelligence as intelligence further up the pyramid of pain – indicators that are more difficult for an attacker to change.
This includes specific vulnerabilities, exploit code, and TTPs, rather than atomic indicators like IP addresses, domains, and hashes that are relatively easy to change to evade detection. Building mitigations for indicators derived from tactical intelligence takes longer, but they will be more robust.
Each of these intelligence types is collected, analyzed, and disseminated following a model known as the Cyber Threat Intelligence Lifecycle (or CTI Lifecycle for short).
It is also important to point out that tactical and operational intelligence can be defined differently, depending on who you are talking to in CTI. This is often the case in North America where tactical and operational intelligence are flipped (CrowdStrike). The descriptions above align with how operational, tactical, and strategic intelligence are defined in the United Kingdom and Europe from my experience (CREST).
The CTI Lifecycle
The CTI lifecycle encompasses the stages involved in collecting, analyzing, and disseminating threat intelligence. You will see the lifecycle explained in more detail later in this series. Here is a basic overview so you can get to grips with the CTI process.
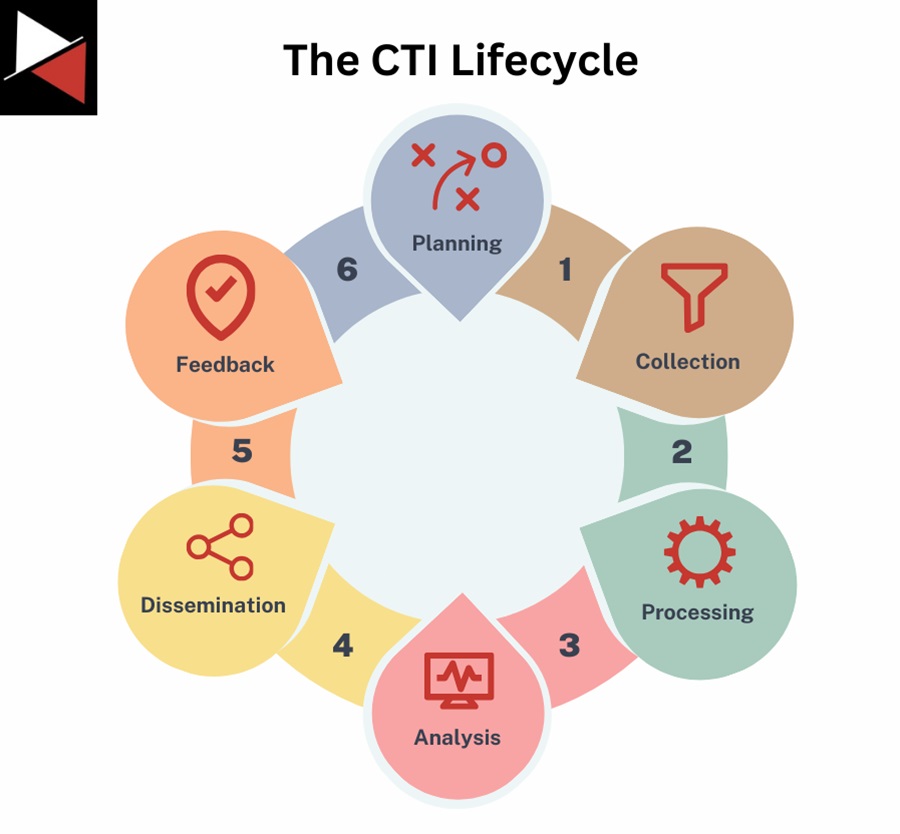
The CTI lifecycle consists of six stages:
- Planning: Defining the goals and objectives of your CTI collection, such as your intelligence requirements, what assets you want to prioritize defending, and how you will communicate the intelligence you find.
- Collection: Going out and collecting threat intelligence relevant to your goals and objectives. This could be open-source intelligence (OSINT), intelligence from proprietary feeds, or engaging with information-sharing communities.
- Processing: Organizing the collected intelligence into a form that allows it to be analyzed. This includes normalizing and structuring data, enriching the data with contextual information, and assessing the credibility and reliability of the intelligence sources where you collected the data.
- Analysis: Analyzing the processed intelligence for meaningful insights that can be used to defend your organization (operational/tactical intelligence) or inform strategic decision-making (strategic intelligence).
- Dissemination: Sharing the intelligence and insights the intelligence provides with relevant stakeholders. This includes tailoring the presentation of the intelligence to suit the recipient so they can use it effectively.
- Feedback: Collecting feedback about the intelligence you shared and the efficiency of your CTI process. This is used to assess intelligence requirements and make adjustments to align with business objectives.
Operational, tactical, and strategic threat intelligence all flow through this cycle. The actions performed at each stage vary depending on the intelligence; some stages can be automated, while others require a human. You will learn more about the CTI lifecycle using real examples later in this series.
You will see the term “indicators” constantly popping up in CTI. An indicator is just a piece of information that can be used to identify or characterize a threat. They can indicate different things, such as an IOC or an IOA.
An Indicator of Compromise (IOC) is an atomic indicator (e.g., IP address, file hash, domain, etc.) that has been seen in a previous cyber attack. An Indicator of Attack (IOA) indicates a behavior associated with an attack, such as an attacker’s tactics, techniques, and procedures (TTPs).
Now you have a general overview of CTI, let’s dive into how CTI is used within the cyber security industry.
Role of CTI in Cyber Security
CTI plays a crucial role across various cyber security jobs, from deeply technical ones like incident responders to key decision-makers like managers or directors. It provides valuable insights into potential threats, vulnerabilities, and risks that help cyber security professionals make informed decisions. Let’s look at some examples.
Security Operations
For those working in security operations roles, such as Security Operations Center (SOC) Analyst, CTI can support them in the following ways:
- It can help them efficiently triage incidents by enriching them with contextual information.
- It enables them to proactively defend their organization by supplying information about the latest attacks and vulnerabilities.
- Aids in the development of detection rules and signatures.
- Facilitates threat hunting by providing insights into adversary behavior that may go undetected.
- Helps identify and understand new attack techniques and tactics.
Incident Response
Incident responders are called in when a security incident arises to minimize the impact on the business. They are often there on people’s worst days to provide technical support, contain an incident, prevent escalation, and remediate. CTI can help them achieve this by:
- Supporting the creation and refinement of incident response playbooks that ensure a swift, consistent, and comprehensive response to cyber incidents.
- Helping incident responders understand the tactics, techniques, and procedures (TTPs) an attacker uses so they can direct their investigation efforts.
- Providing IOCs for identifying malicious activities on endpoints and networks.
Vulnerability Management
All organizations need a vulnerability management program that discovers, prioritizes, assesses, and remediates vulnerabilities in the infrastructure, applications, and services an organization uses for its operations. It is a cornerstone of all organizations that want a strong cyber security posture, and CTI can support vulnerability management in the following ways:
- Enriches vulnerabilities with contextual information to help vulnerability prioritization and assessment.
- It helps discover the latest vulnerabilities.
- Provides information about the exploitability of a vulnerability, its potential business impact if exploited, and if attackers are using it in the wild.
- Supports remediation by providing mitigation advice.
Management
CTI is not just technical, it can help key stakeholders make informed decisions that keep their organization safe in the ever-evolving cyber landscape. CTI can be used by security managers, directors, or executives by:
- Providing a comprehensive view of the organization’s cyber security posture and the threat it faces to support informed decision-making.
- Facilitate strategic planning for security improvements and investments based on trends seen in the cyber landscape.
- Aid in communicating the importance of security measures to stakeholders by providing real-world data about geopolitical events, security breaches, and trends.
Conclusion
Cyber threat intelligence (CTI) is a proactive approach to defending an organization against cyber attacks. It involves collecting, analyzing, and disseminating intelligence about threats an organization will likely face. Technical operators and key stakeholders can use CTI to improve the cyber security posture of their organization and make informed strategic decisions.
You discovered threat intelligence can be grouped into three main buckets (operational, tactical, and strategic intelligence) and uses the CTI lifecycle to collect, analyze, and distribute this intelligence. You also learned about the role of CTI in different cyber security jobs and the benefits it can provide.
This is just scratching the surface of CTI. A quick guide to get you up and running. Keep following this series to learn more about CTI and the key definitions and concepts you will encounter as you dig deeper.
Discover more in the Definitions and Key Concepts series!
Frequently Asked Questions
Who benefits most from CTI?
CTI can benefit everyone, from technical operators who need to have the latest intelligence about real-time events to key stakeholders who need to make informed decisions about strategic direction. It is crucial in supporting many different roles in cyber security, including SOC analysts, incident responders, threat hunters, vulnerability managers, and more.
You can learn more about how a Threat Intelligence platform (TIP) might help you in 5 Reasons Why a Threat Intelligence Platform Will Improve Your Business.
Can CTI be used by the Security Operations Center (SOC)?
Yes. CTI has a very important role in modern SOCs. It is used to enrich alerts so analysts can efficiently triage and prioritize them, it informs managers of the latest threats affecting their organization so they can prioritize detection engineering efforts, and it facilitates threat hunting to find threat actors that have slipped past traditional security technologies like firewalls and anti-virus.
How can I become a CTI analyst?
Becoming a CTI analyst requires a strong knowledge of IT and security fundamentals and a broad understanding of offensive testing like penetration testing and red teaming – you need to know how systems are attacked. You also need to stay up-to-date with the latest developments in the cyber world and have a keen eye for performing analytical work.
Most people who become CTI analysts start in security operations or penetration testing and move to a CTI role once they build their knowledge base. To discover what a CTI does as part of their daily work, read Day in the Life of a Senior Threat Intelligence Analyst.
What is the future of CTI?
There are a lot of huge technological developments going on today in the world of cyber. Artificial intelligence (AI) and machine learning are gaining mainstream traction and will likely be the focus of many people in the immediate future. Businesses are still catching up with the cloud computing revolution and its implications on security. Finally, the constant evolution of the Internet and social media is exposing more and more people to new information and opportunities every day.
I think over the coming years, we will see the rapid development of AI and machine learning provide people access to intelligence sources that were isolated in the past. This will facilitate more collaboration and information sharing, with a need to integrate this into security tools and business processes so it can be used effectively.