In this digital age of online work, we are bombarded with information from work, school, and daily life. We are in the era of knowledge work, where people gather, process, and distribute information as a job. There has been an explosion of notetaking applications to aid in this work, but none have been tailored to cyber security professionals until now.
There are notetaking applications for organizing our daily lives, interacting with large teams effectively, and rapidly taking notes on the go. Until now, there has been none dedicated to cyber security professionals. But that has now changed with the advent of Polarity.
Let’s dive in and explore this new notetaking tool that has been developed specifically to enhance your cyber security workflows by fusing disparate systems into one unified application.
What is Polarity?
At its heart, Polarity is a search tool. It integrates with internal and external data sources so you can search your entire organization’s resources simultaneously. For instance, you can search for a domain name you come across. Polarity will search your organization’s internal datasets and external datasets through one of its integrations and return all the information it has to you in a single pane of glass. You can then run tool integration to gather more information or execute a workflow.
You can even build your own custom integrations with Polarity for in-house applications or tools specific to your company.
Internal integrations could be your case management platform, Endpoint Detection and Response (EDR) tool, or Security Incident and Event Management (SIEM) solution. Meanwhile, external integration may be your threat intelligence platform, a network information database, or a social media site.
Once you find the information you are looking for, this is when Polarity’s notetaking capabilities come into play. You can use Polarity to add annotations to enrich the information you discovered. Annotations are attached to the item (e.g., domain name, IP address, file hash, etc.), so your team (or the entire organization) can see your work and avoid duplicating analysis effort.
Polarity also allows you to add tags to information. Some of these are autogenerated (e.g., where data about an item came from), but you can add custom ones to help your team track threat actors, campaigns, incidents, and more.
Polarity’s power as a notetaking application is that it is tailored to cyber security professionals. Unlike other notetaking apps, it is designed to bridge the gap between your security tools and datasets so you can efficiently gather, analyze, and distribute information.
Use Cases
Polarity can serve several different use cases for your organization’s security team.
Incident Response
Polarity can be used as a free-floating overlay that ingests command lines, raw logs, and search indexes and then automatically searches your internal and external data sources in parallel to provide context to this information. This streamlines your incident response analysis as every piece of information you discover is enriched and contextualized automatically.
Threat Intelligence
Polarity allows you to collect and distribute threat intelligence easily. Every indicator in every report can be automatically enriched with data from internal and external sources and annotations added to these indicators by intelligence analysts. This makes it easy for key decision-makers to keep their finger on the pulse of current cyber security trends and what is affecting their organization.
Threat Hunting
Polarity lets you quickly pivot and investigate suspicious indicators with its many integrations. You can trigger automated workflows to investigate other assets or kick off entire playbooks to mitigate threats. All information is available in a single pane of glass so you can see the whole picture.
SOC
Context and enrichment are two key components of running an effective SOC. Polarity can seamlessly provide these with its free-floating overlay that allows SOC analysts to investigate threats efficiently, work in tandem with other analysts, and keep others informed about critical developments.
Penetration Testing / Red Teaming
Polarity can be used to automate common penetration testing and red teaming tasks, so your team can scale their capabilities. It can automate scans, find exploitable vulnerabilities from threat intel reports, and more.
To see it in action check out the video below.
Pros and Cons of Polarity
Polarity offers several key benefits as a notetaking application. However, it’s not all sunshine and rainbows. Let’s take a look at the pros and cons of Polarity.
Key Benefits of Polarity
- Great Integration Support: Polarity supports a wide range of integrations (over 200). This includes internal integrations like security tools, case management platforms, databases, and external integrations such as threat intelligence platforms, network information databases, etc. These integrations let you automate searching, kick-off response activities, and more!
- Quick and Easy Knowledge Sharing: Polarity runs in your environment and can be configured to connect with your security team or entire organization so everyone can keep up-to-date with the latest information about threats, assets, and indicators. Analysts can add annotations to items and tag them to keep track of related items (e.g., an ongoing incident, threat actor campaign, etc.).
- Super Charges Investigations: Polarity provides you with access to your entire organization’s data resources at your fingertips. Every indicator that you, your team, or anyone in your organization has seen and investigated is coupled with your organization’s external data repositories. This power lets you streamline your investigations, eliminate duplicate work, and make better decisions quicker.
- Provides Source Analytics to Track ROI: Polarity is installed locally on your server. This means you have access to Polarity’s Source Analytics which gives a bird’s eye view of all your organization’s resources, how they are being used, and the return on investment (ROI) for leadership. You can see what tools are providing value and what ones are not.
The team at Polarity includes a whole library of great training material to help you unlock all these benefits.
Drawbacks of Polarity
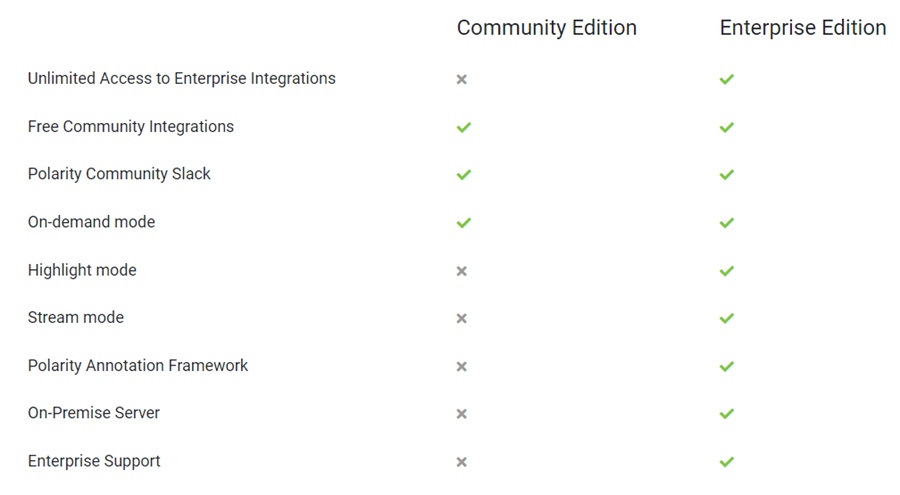
- Notetaking is Only Available in the Commercial Version: Polarity has two versions. A Community edition you can use for free and a fully-featured Enterprise version. The community edition does not come with many of the features that make Polarity such a great tool, such as the Polarity Annotation Framework (notetaking), highlight and stream mode, and more advanced integrations.
- Lack of Advanced Notetaking Features: Despite Polarity having some great notetaking features, like tags, Markdown support, and a commenting/voting system, it lacks some of the other notetaking features applications like Notion and Obsidian have been pushing. There is no cloud storage option, no graph view to link indicators/entities, and no reporting features.
Here is a quick comparison of the Community and Enterprise editions of Polarity. As you can see, Polarity holds much back in its Community option.
How I Use Polarity
To help you better understand Polarity, I will walk you through how I use the platform to help me as a threat intelligence analyst. This can be split into two main parts: analyzing threat intelligence reports and analyzing intrusion data.
You can learn more about my typical day in a Day in the Life of a Senior Threat Intelligence Analyst.
Analyzing Cyber Threat Intelligence Reports
A large part of my day is spent consuming threat intelligence reports, analyzing them, and distributing relevant threat intelligence to teams within the organization. This could be operational intelligence that aids the day-to-day security operations of the SOC or strategic intelligence that helps leadership make key decisions.
When I review these reports, I want to quickly understand if they match my organization’s intelligence requirements and require further analysis. For instance, I may come across the following questions when triaging a report:
- Is this threat actor likely to target my organization?
- Is this threat actor linked to another threat actor or campaign I am tracking?
- Is this at MITRE ATT&CK tactic, technique, or procedure (TTP) that will affect my organization?
- Has my organization done work to mitigate this threat already?
- Have I seen this report before?
- Does this report contain any Intelligence Requirements my organization wants me to prioritize?
- Is the data in this report reputable and trustworthy?
Polarity helps answer these questions with the integrations it offers. It can help you quickly get information about a threat actor, find campaigns you are currently tracking in your threat intelligence platform, give context to TTPs, and connect your work with other analysts using its Annotation Framework.
For example, I may encounter a threat actor named Cyb3r Drag0nz and have no idea who they are. Thankfully, I don’t need to query multiple threat intelligence providers to understand who this threat actor is, what organizations they target, and their TTPs. I can just highlight the name and press and hold <cmd/ctrl> + c to execute a search and run Polarity’s threat intelligence integrations.
Here the Mandiant Threat Intelligence integration provides me with reports about the group targeting Industrial Control Systems (ICS).
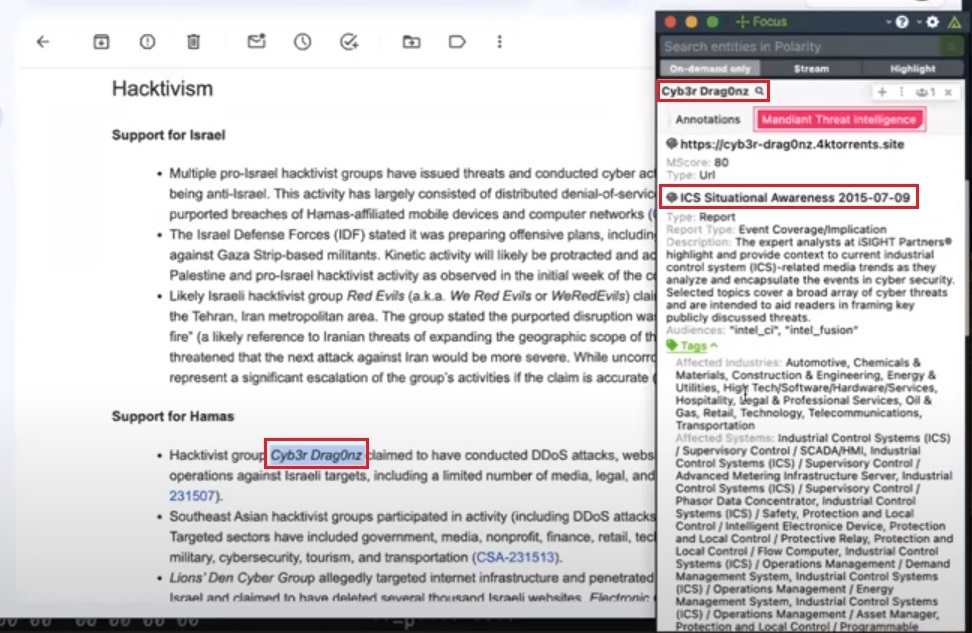
Now I know what industry this group attacks and can quickly determine if they are a threat that my organization needs to prioritize.
Analyzing Intrusion Data
My time is also taken up analyzing intrusion data. This could be some suspicious activity that needs to be investigated and enriched with intelligence or actual malicious behavior, which needs to be given context so detection and mitigation opportunities can be discovered.
Analyzing intrusion data is very similar to the work many blue team roles entail; sifting through logs, pivoting around datasets to uncover malicious activity, and good old-fashioned investigation work. Polarity is an incredibly valuable tool for this work because of its vast library of integrations and the streamlined workflow it provides.
Polarity provides you with an overlay window that acts as a digital assistance in your investigations. You navigate to your investigation tool of choice (e.g., EDR, SIEM, manual log parser), and with a quick key combination, you can have Polarity search your entire organization’s resources for an indicator. The tool automatically runs all its integrations and enriches the indicator with intelligence to inform your next decision.
In the Community Edition, Polarity runs in On-Demand mode. This is where you highlight an indicator you want to query and press and hold <cmd/ctrl> + c to execute a search, running Polarity’s integrations. The Commercial Edition of Polarity allows you to streamline your workflow further by offering three additional modes:
- Stream: Polarity automatically streams information shown on your screen in real-time to the overlay window to provide context on the go.
- Highlight: Key information is highlighted in real-time. Hovering over these highlights populates the overlay window with additional context.
- Focus: Allows you to take a screenshot of a section of your screen and look up indicators within that section.
You can learn more about Polarity’s different modes in the Enterprise Guide.
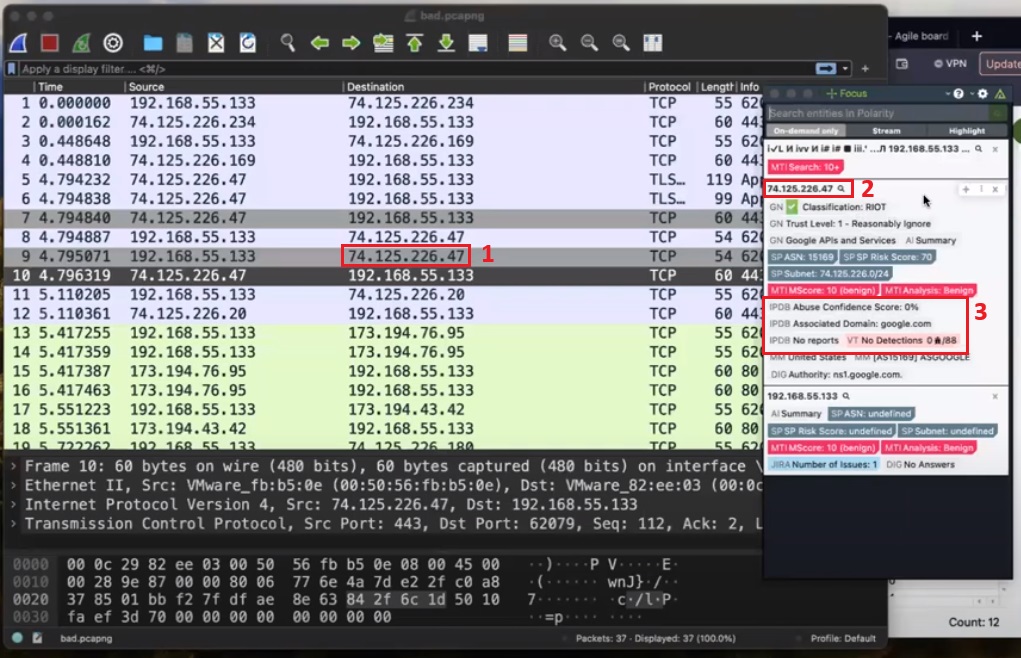
Here a network packet capture has been loaded into Wireshark for analysis. Highlighting the external IP address 74.12.226.47 (1) and pressing and holding <cmd/ctrl> + c triggers a Polarity search for that indicator. Polarity queries all the integrations you configured related to IP addresses and returns the information about 74.12.226.47 in the overlay window (2). We can probably conclude it’s benign from the VirusTotal and AbuseIPDB information (3). This quick lookup saves you querying every integration separately to determine if the IP address is malicious.
I have found this the most useful feature of Polarity. Using the application as an augmentation tool to help you quickly resolve key questions during an investigation. In this capacity, it can substantially reduce the time you spend investigating, allowing you to respond more efficiently to cyber incidents.
Conclusion
Polarity is the ultimate notetaking application for cyber security professionals who need to integrate many internal and external tools or data into a simple, clean interface. It will streamline your investigations, provide easy access to mission-critical information wherever it is stored, and allow for better distribution of information throughout your organization.
The Community Edition is a great option to get started using Polarity. However, it lacks many of the features that make Polarity such a great tool, including the Annotation Framework, different modes of operation, and more. It would be great to see a trial version of the Polarity Commercial Edition or a cloud offering that lets users experience the full capabilities of this great tool. More advanced notetaking features would also be a welcome addition.
Overall, this is not a tool you want to pass over. Its ability to act as a copilot during incident response, threat intelligence, and SOC investigations makes it an invaluable tool for your front-line cyber security defenders. I highly recommend trying it and seeing how it can make your team more efficient.