Analyzing cyber threat intelligence can be hard. You are often overwhelmed with data, drowned in overlapping connections, and unclear where to start or when to finish your analysis. To help guide their analysts through the maze, intelligence organizations across the globe use the threat intelligence lifecycle.
The intelligence lifecycle is a structured approach to collecting, analyzing, and distributing intelligence. It acts as a template that analysts can follow to produce or consume intelligence. The cyber security industry has adapted this lifecycle to suit its needs by creating the cyber threat intelligence (CTI) lifecycle.
This article is your essential guide to the CTI lifecycle. You will learn about its six stages, how this model is used in the real world, and how you can get the most out of it. Let’s jump in!
What Is the Cyber Threat Intelligence Lifecycle?
The cyber threat intelligence lifecycle is a model you can use to structure your intelligence analysis from beginning to end. Using this model, you can create processes around gathering, analyzing, and distributing threat intelligence to your organization’s key stakeholders.
The lifecycle follows the idealized model of how Western intelligence organizations structure their intelligence work from collection to dissemination. It can be used as a guide for CTI analysts to follow when doing their work or as a template for CTI leads to use when designing processes for their teams.
Six stages comprise the threat intelligence lifecycle: Planning, Collection, Processing, Analysis, Dissemination, and Feedback.
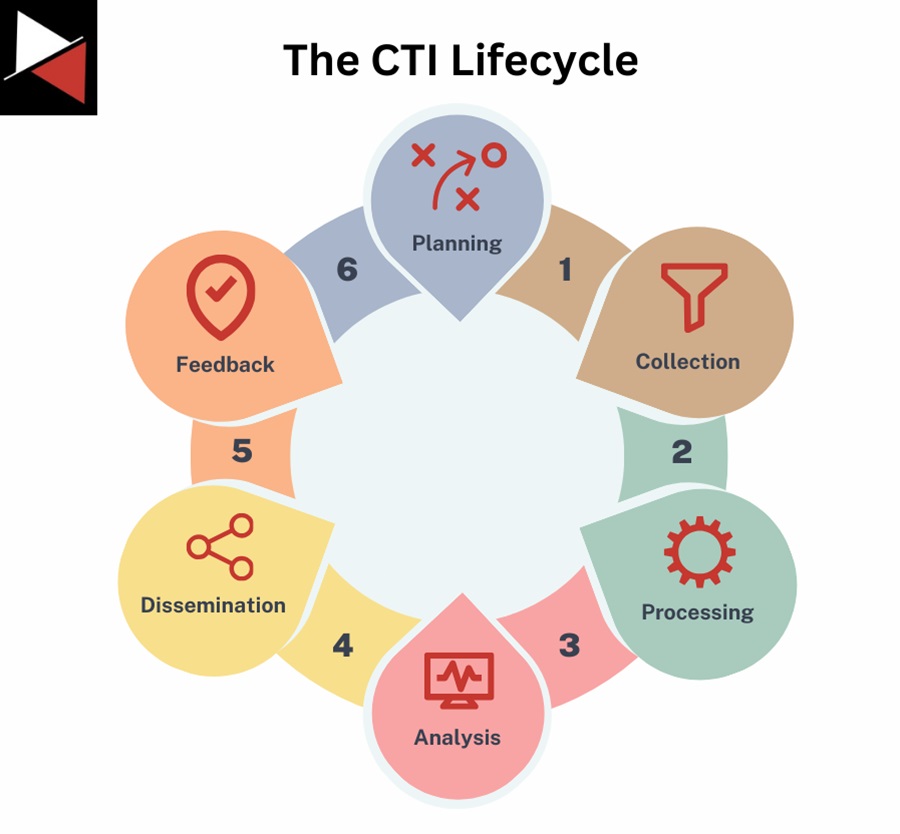
Let’s explore each stage to understand the key processes and objectives at each.
Stage 1: Planning
The first stage of the threat intelligence lifecycle is Planning. Here you will define the goals and objectives of your threat intelligence activity or plan out your entire program’s ambitions.
You will want to achieve the following at this stage:
- Identify the key stakeholders you will share your intelligence with and how you will achieve this.
- Establish the intelligence requirements of your organization at the operational level by focusing on current threats and at a strategic level by evaluating future threats.
- Determine the scope and key objectives of your CTI program. This can vary greatly between organizations. For instance, one organization may want to protect its brand reputation, another wants to defend against ransomware gangs, and a defense contractor may wish to track advanced persistent threats (APTs).
- Prioritize what you want to protect. This includes sensitive information, key business operations, and assets.
- Identify gaps in current intelligence. If strategic objectives change or gaps were found in past CTI activities, you must identify and prioritize addressing these gaps. This could be by collecting more or different data, changing processing or analysis techniques, or adjusting distribution methods.
At the end of this stage, you should have a plan that details how analysts will collect, analyze, and share information that fulfills the organization’s intelligence requirements.
It is very important that the goals and objectives you define at this stage align with your organization’s needs and strategic direction. For example, if your organization plans to adopt AI, your CTI requirements must reflect this. Learn the language, pain puts, and what the teams in your organization need from the intelligence.
Stage 2: Collection
Once a plan has been made, you can move onto the Collection stage. At this stage, you will gather information that addresses the intelligence requirements you previously defined. This involves identifying relevant data sources to collect information from and storing it somewhere.
What is a data source?
A data source is a channel, system, or repository that you can use to gather information about cyber security threats relevant to your organization. They supply data you can collect using manual or automated techniques and prepare for Processing and Analysis.
Where can I store the information I gather?
The information you collect needs to be stored somewhere. This can be a simple storage solution like an Excel spreadsheet or a specialist threat intelligence platform. Popular open-source threat intelligence platforms include the Malware Information Sharing Platform (MISP) and OpenCTI. There are also commercial platforms commonly called Threat Intelligence Platforms (TIPs), like The Record Future Cloud.
Cyber threat intelligence collection can be done in a variety of ways. Depending on the data sources at your organization’s disposal, it may involve any of the following:
- Pulling metadata and logs from your organization’s security tools and networks.
- Gathering threat data from commercial or open-source threat intelligence feeds your company subscribes to.
- Talking to knowledgeable sources directly, such as journalists, insiders, or peers.
- Trawling through open-source news, blogs, and other OSINT sources.
- Scraping data from social media, websites, or forums.
- Stepping into the murky world of dark web forums and other cybercrime channels to extract data.
You will never be able to collect all the data. Where your organization operates will dictate your operational environment based on cultural, technical, and geopolitics. Your operational environment will dictate what data sources you have access to and what threats you see. For instance, the security firm collecting from customers in the US will see different data and threats than the security firms in Iran.
You will be able to collect a subset of the data available in your operation environment, use a subset of that data to create information (from Processing), and a subset of that information for intelligence (from Analysis). The quantity of data, information, and intelligence gets smaller and smaller as you progress through the lifecycle.
Stage 3: Processing
With raw data collected, you need to process it to transform it into information for analysis. Welcome to the Processing stage.
During the Processing stage, you will organize and structure the collected data to prepare it for analysis. This often involves:
- Cleaning the data to remove any garbage.
- Normalizing the data so it can be uploaded to your data storage solution.
- Verifying the data is legitimate and trustworthy based on the source you collected it from and what others are saying about it. For instance, is an IP address recognized as malicious by multiple intelligence vendors or no one outside the blog post you found it on?
Processing the data you collect is vital in ensuring efficient analysis. If you analyze garbage data, you will get garbage intelligence, and the insights you extract from this intelligence will be… garbage.
Processing is usually done by machine nowadays. Your SIEM or EDR solution will turn the data (logs) into a human-readable format, making it easier to understand. Nevertheless, it is always useful if you, an analyst, have the capability to manually process, read, and interpret the data in case a fancy tool is unavailable.
Stage 4: Analysis
The Analysis stage turns the information you have gathered into actionable intelligence that your organization can use to defend itself or inform its strategic decisions. It involves a human operator using their knowledge and experience to identify patterns or trends in the information collected. Once identified, these patterns are interpreted to produce insights the organization can use to inform decisions.
- Does it mean your organization needs to block certain indicators (e.g., IP addresses, domains, file hashes)?
- Does it mean your organization needs to focus its efforts on hardening a particular security gap?
- Does it mean your organization needs to invest in a new technology, move away from an old one, or spend more time training their employees?

Understanding the nature, scope, and implications of the threats present in the data collected is the ultimate goal of this stage. The CTI analyst is the key interpreter in formulating actionable intelligence.
There are a variety of structured analysis techniques and tools you can use at this stage to help you (e.g., the diamond model, the cyber kill chain, etc.). You must also be aware of biases that could creep in and cloud your judgment when performing CTI analysis. We will discuss structured analytical techniques and biases in later articles.
Stage 5: Dissemination
Once you have turned the collected data into actionable intelligence, it is time to share it with the relevant stakeholders.
This is one of the key stages in the threat intelligence lifecycle that you want to get right. You may have the best intelligence in the world, which may save your company from an imminent attack or steer your cyber security program back on course. However, it is useless if you fail to communicate this information to the right stakeholders in a timely manner.
Like Kentucky Fried Chicken (KFC), good threat intelligence is relevant, timely, and actionable!
The Planning and Preparation stage usually dictates the success of the Dissemination stage. The following questions should have been answered before you reach the Dissemination stage:
- How do you plan on distributing the intelligence you consumed or produced to others?
- Who are the relevant stakeholders, and what type of intelligence will you give them?
- What intelligence-sharing channels can you use?
If you answered these questions, you should know what intelligence you want to share, with whom, and how to share it efficiently.
You might share it via email, in an instant message on Microsoft Teams or Slack, or in a weekly presentation on a video call. The dissemination method just needs to ensure the intelligence you share is received in a timely manner and is actionable for the recipient. For instance, a list of IOCs or TTPs to hunt for is relevant to your security operations team but not to the CISO.
Try to make the dissemination stage as automated as possible. Automatically upload IOCs for detection to your SIEM or EDR platform, use pre-defined templates when writing emails, reports, or presentations, and create information-sharing groups so you don’t need to contact every stakeholder individually.
Stage 6: Feedback
An often neglected stage of the threat intelligence lifecycle is the Feedback stage. Every CTI analyst is eager to collect, analyze, and share intelligence. They are less eager to receive feedback on the effectiveness of the efforts or if the intelligence they are consuming/producing is any good.
The Feedback stage is crucial if you want to see your CTI work continuously improve and add value to your organization. You need to know if your CTI efforts are making a difference to your organization at the operational or strategic level and, if not, how to adjust things to ensure they do.
Too often, CTI teams will blindly share intelligence with people in their organization and never stop to consider if what they are sharing adds value. You need a two-way communication channel between the CTI team and key stakeholders. The stakeholders need to provide feedback on the effectiveness of the intelligence being shared with them, how they use it, and if any improvements can be made to aid them in making informed decisions.

Examples of questions to ask when requesting feedback include:
- Is the intelligence being shared actionable, relevant, and timely?
- Can the CTI process be more efficient? (i.e., adding automation or investing in new tools and data sources)
- Is the amount of intelligence being shared too much or too little?
- Have the intelligence requirements of the organization changed?
- Can the intelligence be shared with the wider community?
Using the Threat Intelligence Lifecycle
The CTI lifecycle is used by many organizations all over the world. It does not matter the size of your organization or the resources at your disposal, the CTI lifecycle is a model that all CTI teams can use to structure their processes.
The specifics of how you use the CTI lifecycle will depend on two main things:
- The intelligence requirements of your organization
- The resources you have at your disposal
Your Intelligence Requirements and the Threat Intelligence Lifecycle
Broadly speaking, your intelligence requirements will fall under one of the main three types of threat intelligence; operational, tactical, or strategic.
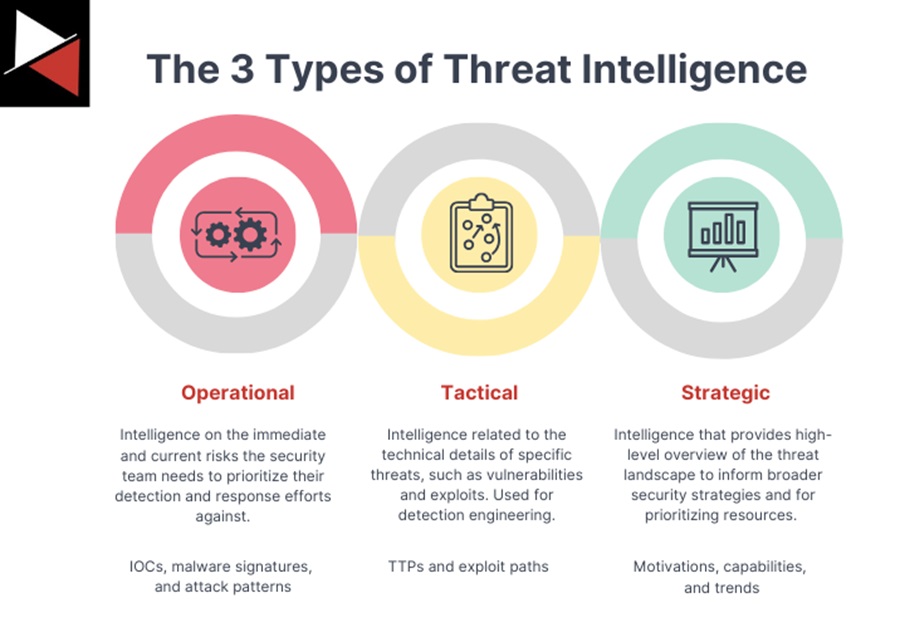
Each time you run through the threat intelligence lifecycle, you will focus on one of these three main types of threat intelligence, and which one you focus on will dictate how you use the model. Let’s look at examples of each:
- Operational: If your intelligence requirements are to combat an ongoing phishing campaign, you will want to focus your efforts on collecting operational intelligence. Your security operations team can use this intelligence to block IOCs with your SIEM or EDR solution, detect malware signatures with YARA rules, or identify attack patterns with Sigma rules.
- Tactical: If your intelligence requirements are to identify technical security controls that will detect ISO files being used as an initial access vector, you need to gather tactical intelligence. Your security operations team uses this intelligence for detection engineering, whereby they use the tactics, techniques, or procedures (TTPs), you identify to create detection rules for your SIEM or EDR solution.
- Strategic: If your intelligence requirements focus on identifying ransomware trends, you will want to collect strategic intelligence that provides an overview of what is being seen across the threat landscape in relation to ransomware. You want to ask questions like what ransomware is emerging, what vulnerabilities ransomware is exploiting, and how I can best defend against new ransomware trends. These questions will help inform your organization’s broader security strategies.
To provide more context, here is how you would use the threat intelligence lifecycle based on the intelligence you choose to focus on at each stage.
The Threat Intelligence Lifecycle: Operational Intelligence
- Planning: Define what information you need to collect to address an immediate and ongoing cyber attack, such as a phishing campaign. This may include IOCs, malware signatures, attack patterns, or vulnerability details.
- Collection: Collect the data you outlined in the Planning stage. You could use open-source intelligence by searching for information about a recent campaign, collecting data from a cyber attack against your own network, or using a commercial threat intel feed your organization pays for.
- Processing: Upload the data you collected to your threat intelligence database so it is organized and structured. This may include adding IOCs to an Excel spreadsheet or automatically ingesting data into a threat intelligence platform. Make sure you verify the data you upload.
- Analysis: Analyse the data you collected. Enrich it with other data to find other IOCs to detect, block, or hunt for. Aim to provide more context to the security operations team.
- Dissemination: Share your intelligence with the security operations team. This will be technical data that should be used immediately. As such, you may automatically upload these IOCs to your security solutions from your threat intelligence database or quickly distribute them to the operations team in an instant message or email.
- Feedback: Gather information from the security operations teams if the IOCs you shared were detected, if they were found in any threat hunting activity, or if the CTI process was efficient enough. A key requirement of operational intelligence is efficiency because it addresses immediate and ongoing threats.
The Threat Intelligence Lifecycle: Tactical Intelligence
- Planning: Define what information you must collect to address the tactics, techniques, and procedures adversaries use or exploit paths commonly abused. This intelligence targets detections higher up the Pyramid of Pain.
- Collection: Collect the data you outlined in the Planning stage. This data will likely be in threat intelligence reports describing the technical details of how an attack was performed. Ideally, the reports will map attack techniques to the MITRE ATT&CK framework so you track TTPs between reports. Threat intelligence reports can be open-source or supplied by a commercial vendor.
- Processing: Upload the data you collected to your threat intelligence database. This helps you keep track of the TTPs, exploit paths being abused, and the mitigations you can implement to protect yourself against them.
- Analysis: Analysis plays more of a role when dealing with tactical intelligence than operational intelligence. You need to assess the information you gathered to identify patterns, prioritize which TTPs or exploit paths to defend against, and enrich the data you collected with supplementary intelligence. Enrichment may include attributing the TTPs to a threat actor or campaign, adding mitigation advice, or providing additional context.
- Dissemination: Tactical intelligence typically goes to more experienced security operations team members with the technical capability to perform detection engineering and advanced threat hunting. These individuals can transform the intelligence you provide into detections, mitigations, or threat hunts that are more effective at dealing with threats. This intelligence will be shared in a detailed technical report.
- Feedback: Gathering feedback on tactical intelligence is usually a cyclical process. You will provide the security operations team with intelligence about a TTP, and they will ask you to find more information so they can make their detections/mitigations more robust. This cycle continues as new TTPs emerge that circumvent existing detections or mitigations.
The CTI Lifecycle: Strategic Intelligence
- Planning: Define the information you must collect regarding the larger cyber threat landscape. This is usually the evolving trends in attacks, technologies, threat actors, malware, and ransomware.
- Collection: Collect the data you outlined in the Planning stage. You will find trends in monthly, quarterly, or yearly reports from threat intelligence vendors or major technology firms like Mandiant, Cisco Talos, Red Canary, Record Future, Kaspersky, Microsoft, and many more. Commercial TIPs also provide intelligence trend reports.
- Processing: You will likely upload the information you collect outside of a threat intelligence platform, usually in a spreadsheet, as it is only reviewed monthly, quarterly, or yearly and is not designed to be shared. Make sure you follow a structured format so it is easy to compare this new information against past data.
- Analysis: You will review the reports you collected and compare the data to the current strategic threats, trends, and organizational security objectives you are tracking. It is important to track if your organization’s strategic objectives align with the current trends or if a course correction needs to be made.
- Dissemination: Strategic intelligence is distributed to key stakeholders who influence the strategic direction of the organization’s security or technological investments. This could be managers or executives, depending on the size of your organization. You will share strategic intelligence monthly, quarterly, or yearly depending on how frequently your organization’s strategic positioning is reviewed. As such, this intelligence is usually presented in a video call (briefing), where questions can be asked and supplied in a formal report that key decision-makers can review.
- Feedback: Clear feedback is very important after you share strategic intelligence. It is vital that your strategic intelligence requirements are informed by the needs of key stakeholders within the organization. Based on your intelligence, stakeholders may realign their strategic objectives, expand strategic intelligence requirements, or change them entirely. As such, feedback is crucial to inform the Planning stage of the next threat intelligence lifecycle round.
Your Resources and the Threat Intelligence Lifecycle
The second factor that plays a role in how you use the threat intelligence lifecycle is the resources at your disposal. This is the time, manpower, and money you can expend collecting, analyzing, and sharing intelligence. Let’s look at each.
Time
Time is perhaps the greatest factor in how you use the threat intelligence lifecycle. It is a limiting factor for us all, and finding ways to maximize our time is crucial for creating an efficient threat intelligence lifecycle. Ideally, you want to spend as much time as possible at each lifecycle stage, yet this is not a reality. Instead, you need to prioritize certain stages and automate where you can to save time.
I recommend prioritizing the following stages:
- Planning: This is the most important stage of the lifecycle because it has the most influence on the success of your CTI work. Good planning will ensure you know where to find information, understand how to turn that information into actionable intelligence, and can choose the right distribution channel to share that intelligence efficiently.
- Analysis: Analysis turns the information you gather into actionable intelligence that others can use, be it IOCs you can share, TTPs you can mitigate, or insights that inform key decisions.
- Dissemination: Intelligence is not useful if it is not shared with the right people in a timely manner. Ensure you target your intelligence at the right people and in a manner they can easily digest.
You can then try to automate the remaining stages to save you time:
- Collection: Build a CTI aggregator to automate open-source intelligence collection or invest in a TIP to fine-tune intelligence specific to your organization.
- Processing: Use a specialist threat intelligence platform like MISP or OpenCTI to automatically structure and share your data. You can even automatically ingest data into these platforms by setting up a threat intel feed.
- Feedback: Create a Google Form with questions other security teams or personnel can fill out to give quick, structured feedback you can action.
Manpower
The manpower you can dedicate to CTI processes will affect how you use the threat intelligence lifecycle. There are only so many automations or time-saving tools you can invest in to claw back time for your team and maximize your limited manpower. To account for limited manpower, you must prioritize the intelligence you invest your team’s time in. Ensure you thoroughly discuss with key stakeholders what intelligence requirements they want to prioritize, set expectations, and plan accordingly.
Manpower is often a limitation on the amount of intelligence you can process. If you face manpower limitations, you will follow the CTI lifecycle, you will just limit the number of cycles you go through or the amount of intelligence you collect. Clear intelligence requirements will make it easier to collect only relevant information.
Money
Money is a factor for all security teams. The more you have, the easier things are. However, today there are plenty of free resources where you can collect information, open-source solutions for storing that information, and free-to-use tools you can find online for analyzing that information and transforming it into intelligence.
Don’t be swayed by the latest and greatest intelligence tool. Threat intelligence tools are just wrappers that vendors will put on data. You are paying for the data in threat intelligence, so if one vendor can provide access to that data for cheaper, you are better off going for them and spending time building your own tools that integrate into your CTI team’s workflow.
Conclusion
The cyber threat intelligence lifecycle is a model that CTI analysts and teams follow when collecting, analyzing, and sharing threat intelligence. How you use the CTI lifecycle depends on two main factors; your organization’s intelligence requirements and the resources you have at your disposal.
Intelligence requirements can be grouped into three main categories; operational, tactical, and strategic. The intelligence you choose to ingest into the lifecycle will dictate the specifics of each stage. For instance, operational intelligence will involve sharing IOCs your security operations team can use, whereas strategic will require analyzing trends in data that can help inform key decisions.
This article has shown you how to use the threat intelligence lifecycle, some key considerations you must make, and a few useful tips that will aid you in your CTI work. Remember to plan your CTI process thoroughly, collect intelligence relevant to your organization, and present the intelligence you consume or produce to the right people in an appropriate format.
Frequently Asked Questions
Which Stage of the Cyber Threat Intelligence Lifecycle is Most Important?
The Planning stage is the most important stage of the CTI lifecycle because it has the most influence over the success of your CTI work. In this stage, you will define the goals and objectives of your threat intelligence activity. You must identify the key stakeholders you will share your intelligence with, clearly detail intelligence requirements, and outline how you will collect, analyze, and share the intelligence that fulfills these requirements.
Who Invented the Cyber Threat Intelligence Lifecycle?
A single individual did not create the CTI lifecycle. It has evolved over time as a methodology for managing the collection, analysis, and distribution of threat intelligence in the field of cyber security. The model is intended to be used and refined by CTI analysts to suit their individual use cases and the organization’s needs. As you saw in this article, how you use the CTI lifecycle will depend on the type of intelligence you ingest and the resources at your disposal.
Why Should I Use the Cyber Threat Intelligence Lifecycle?
The CTI lifecycle is a fundamental model used in the cyber security industry to manage threat intelligence collection, analysis, and sharing. It provides a structured methodology to handle threat intelligence operations systematically from beginning to end. Following a methodology ensures you are thorough in your processes and encourages continuous improvement and refinement.




