-

Hunting for Persistence with Cympire: Part III — Services
Learn how attackers use Windows services to maintain persistence once they’ve compromised a machine. Then see how to hunt for these malicious services.
-

How to Arm Yourself with Threat Intelligence
Learn how to use threat intelligence articles, the MITRE ATT&CK framework, and Sigma rules to perform threat-informed hunting using Splunk queries.
-

Hunting for Persistence with Cympire: Part II — Scheduled Tasks
Learn how attackers use scheduled tasks to maintain persistence once they’ve compromised a machine. Then see how to hunt for these tasks.
-

MITRE ATT&CK Framework: Holy Bible of Threat Intelligence
Let’s explore the MITRE ATT&CK framework and find out why it’s a must know tool for any cyber threat intelligence analyst looking to tackle the latest threats.
-

Hunting for Persistence with Cympire: Part I — Registry Run Keys
Learn how attackers use Windows registry keys to maintain persistence once they’ve compromised a machine. Then see how to hunt for these malicious keys.
-
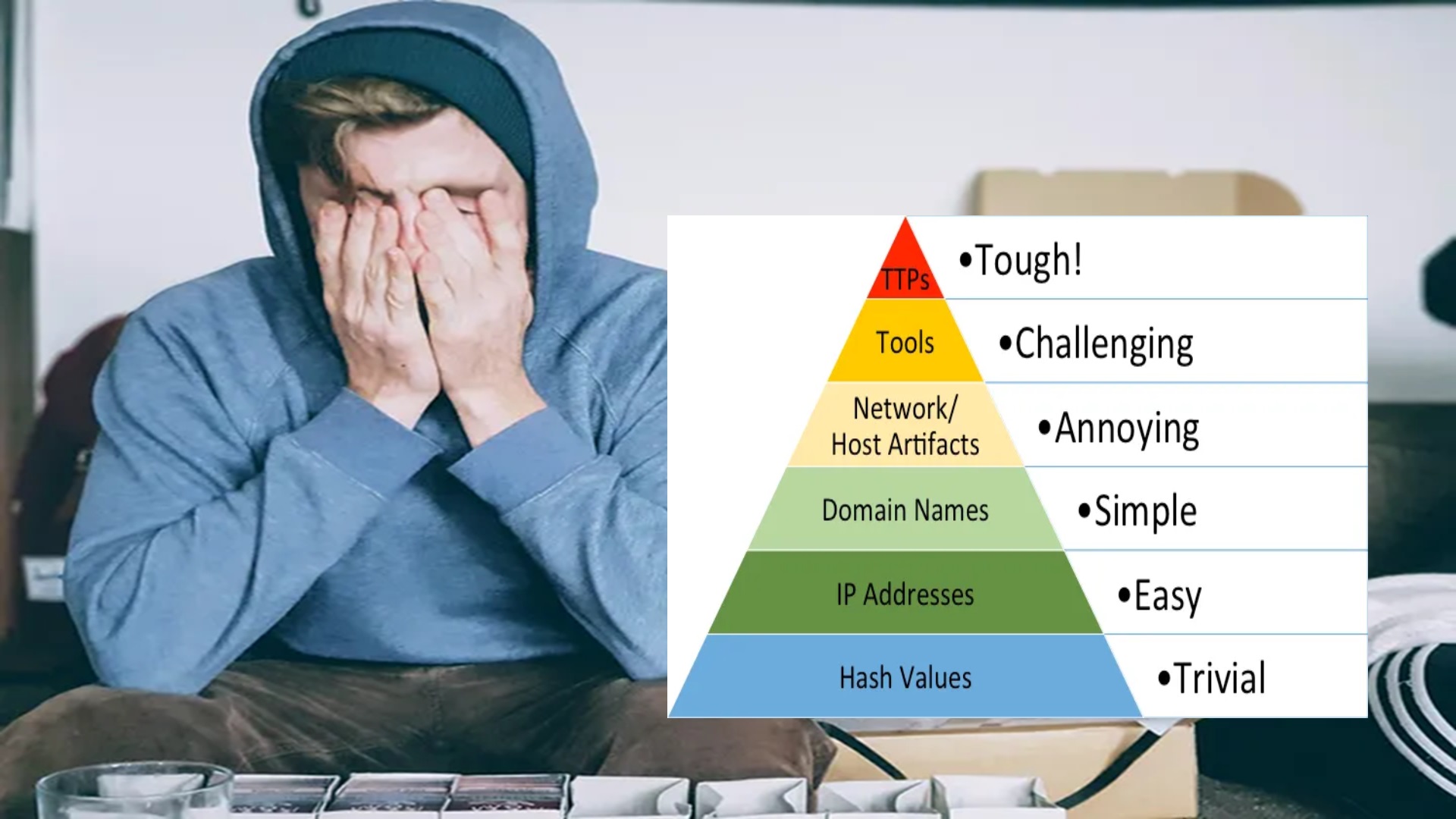
Elevate Your Threat Detections Using the Almighty Pyramid of Pain
Discover how to turn a bad guy’s day into a nightmare using the Pyramid of Pain to elevate your threat detections and increase the cost on adversaries.
-

Let Us Find Out Whodunit
Whodunit is a tool that can be used to identify the most likely Advanced Persistent Threat group responsible for an attack. Let’s find out how to use it!
-

Threat Hunting With Velociraptor III – Hunting Demo
Learn how to use Velociraptor’s threat hunting capabilities to identify malicious activity associated with real-world malware and threat actors in this demo.
-

Threat Hunting With Velociraptor II – Environment Setup
Discover how to create a virtualized threat hunting environment and use Velociraptor as a threat hunting tool to sniff out malicious reverse shells.
-

Threat Hunting With Velociraptor I – Introduction
Learn what threats are, what threat hunting is, and the basic security requirements needed to start a threat hunting program in this series introduction.
-
Creating a Virtualized Malware Analysis Lab Environment
Learn how to create a safe and secure malware analysis environment that is tailored towards your analysis needs using the power of virtualization.
-

How to Create a Home Lab: Virtualize all the Things!
Discover the power of virtualization and how to create your own home lab environment for malware analysis, threat hunting, and software development.

Blog
