Good books on cyber threat intelligence are rare. Good books that craft visual illustrations to distill complex topics are even rarer. Visual Threat Intelligence by Thomas Roccia does both incredibly well.
Visual Threat Intelligence: An Illustrated Guide for Threat Researchers is an introductory book to the murky world of cyber threat intelligence (CTI). It familiarizes readers with the basics of threat intelligence, threat actors, indicators of compromise (IOCs), tactics/techniques/procedures (TTPs), and threat analysis. It then demonstrates these topics in action by applying them to real-world use cases where the author details his experiences.
These are all things you can learn online for free. What makes Visual Threat Intelligence unique and innovative is how it tells the story of threat intelligence through illustrations. These images transform complex topics into a form any reader can easily digest and understand. This makes the book a great resource for those wanting to learn about CTI and a handy reference guide for those already in the field.
But enough foreplay. What actually makes this book worth reading?
Beautiful Illustrations
The main selling point of Visual Threat Intelligence is its illustrations. The content isn’t groundbreaking. The example use cases aren’t new. However, the visual storytelling is unique and innovative.
The author uses illustrations to distill complex topics For example, take a look at this illustration of the traffic light protocol.
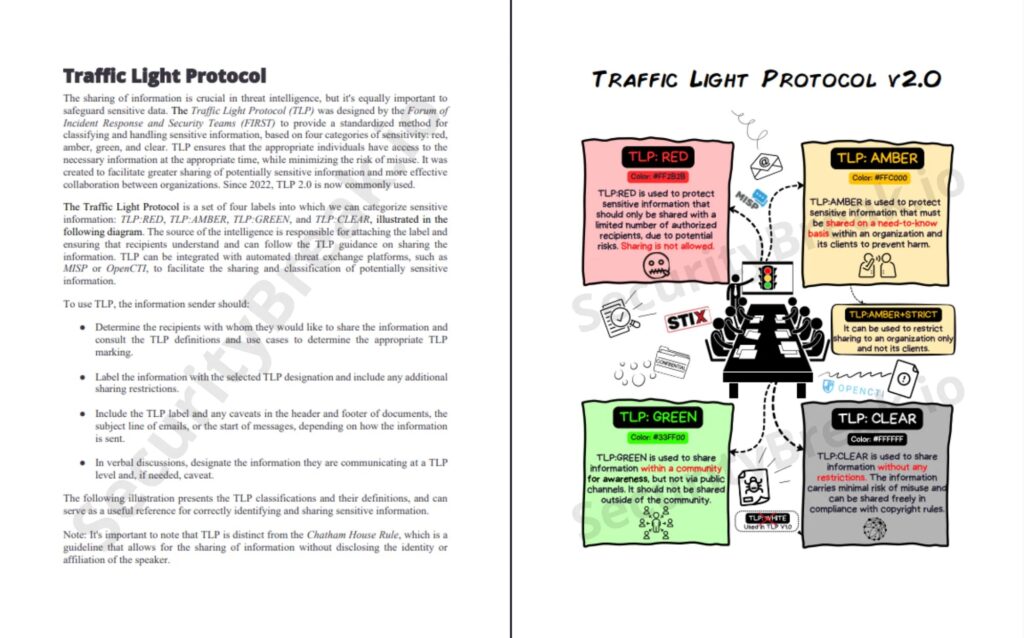
A reader learning about this data classification method might be confused about how it applies to the real world or when to use each classification if they just read the dense text block on the left-hand side. To make the usage of this method more apparent, the author uses the illustration on the right-hand side to show this method in action.
He adds additional context (e.g., data sharing platform/formats) so the reader can link this concept to other things they know; he adds visual elements (colors/icons) so the reader can draw associations in their mind; he ultimately combines different learning styles so that the reader has a better chance of understanding a concept.
The author does this throughout the book to make the content more accessible to those learning it for the first time and those who need a quick refresher or reference. The illustrations make the book a great resource for anyone in cyber security who needs to know how to use threat intelligence.
Well Organized
The book is split into five main sections:
- Threat Intelligence: A quick introduction to cyber threat intelligence and how it is used.
- Threat Actors and Operating Methods: A look at threat actors, how they attack targets, and how we share intelligence about them.
- Tracking Adversaries: A guide to indicators of compromise (IOCs) and how they are used.
- Threat Analysis: How to analyze threats using YARA, Sigma, and MSTiCpy.
- Notorious Cyber Attacks: How threat intelligence was used to combat cyber attacks.
Each section builds on the last. You will learn about threat actors, then you will learn how they operate and how to track them, then you will learn how to analyze the indicators they leave behind, and finally, you will see all these concepts are applied together. I found this accumulative approach to knowledge building, which finished with a practical demonstration, incredibly useful in tying related concepts together.
When first learning about cyber threat intelligence, it can seem like a bunch of random concepts you need to piece together to solve a puzzle, and you never know if you have aligned the puzzle pieces correctly. The author solves this puzzle for you. He organizes the content so that it builds your knowledge from the ground up. Each threat intelligence puzzle piece (concept) is explained and put together with the others so that you can examine a cyber attack effectively by the end of the book.
This makes the book ideal for those who need to apply threat intelligence in their daily work, be it threat hunters, threat intelligence analysts, security researchers, SOC analysts, or any other cyber security professional.
Demonstrations of Practical Usage
As mentioned, the book finishes with a practical demonstration of the taught threat intelligence concepts. It uses several notorious cyber attacks from the last decade to do this, such as NotPetya, Sunburst, and Hermetic Wiper.
Each cyber attack described represents a change in how threat actors target a victim or their goal. The author gives an overview of the attack to provide some basic background knowledge and then jumps into applying the threat intelligence concepts previously discussed to the cyber attack in question. This includes; showing the attack kill chain, visually representing the diamond model, and listing the MITRE ATT&CK techniques used in the attack.
I loved this inclusion. It was not an exhaustive report, as you’d find in the DFIR Report (a great resource for all cyber security professionals). Still, it was a great introduction to applying threat intelligence to real-world attacks. It showed you how to succinctly map out an adversary, its motivations, capabilities, and TTPs using clear illustrations. This made it easy for beginners to understand how to apply the concepts taught to their daily work.
A Vast Collection of Resources
The book concludes with an appendix filled with a collection of useful resources that you can use during your threat intelligence journey. These include open-source platforms, tools, intelligence-sharing formats, online resources, sandboxes, and more!
These, along with a list of further reading materials recommended by the author, allow the reader to take what they have learned in the book and jump further down the threat intelligence rabbit hole. They provide pivots into threat intelligence topics that may interest you or relate to your work.
I found this a great way to finish the book. It lowers the barrier of entry for readers to explore the field by providing a list of resources and learning material the reader can jump straight into. There is no need to research open-source platforms or tools; start with the ones the author recommends and discover what you can accomplish!
Criticisms
Despite how good this book is, I do have some criticisms:
- A lack of threat hunting material: The book does not cover using threat intelligence to hunt for threats.
- A lack of practical technical demonstrations: There are no demonstrations or discussions around making threat intelligence actionable using SIEM, EDR, or other security solutions.
- A lack of content: Although the content in the book is great, there is a lack of it. The book is only 113 pages long, with the main content concluding on page 84.
You could argue that these criticisms are undue. The book is meant as an introductory guide to threat intelligence and does pack a lot in with its storytelling illustrations. As such, I believe all these criticisms would be best resolved with a second edition (“Visual Threat Intelligence: A Practical Guide”), which details how to threat hunt, how to use SIEM/EDR tools, and expanded content like threat profiling or distributing threat intelligence effectively.
You can find out how you practically apply cyber threat intelligence in Lock & Load: Arming Yourself with Threat Intelligence and Threat Intelligence vs Threat Hunting: What is the Perfect Pipeline?
Summary
Visual Threat Intelligence by Thomas Roccia is an awesome book. It marries together cyber threat intelligence with visual storytelling so that anyone can get quickly up-to-date with complex and abstract topics. The author does a great job of building up your knowledge and then showing how you can apply the concepts you learned to real-world cyber attacks. He even includes a comprehensive list of resources and further learning material to learn more about threat intelligence!
Although I have some criticisms about the lack of threat hunting or technical content, the book is a great introductory guide and reference for all cyber security professionals. If you want to purchase Visual Threat Intelligence, you can find it on Amazon or Security Break. I also highly recommend checking out Thomas Roccia’s other work (the Unprotect Project).




