The Cyber Kill Chain is a framework for understanding cyber attacks, analyzing intrusions, and planning cyber defenses. It is used throughout the industry by cyber security professionals in security operations, incident response, and cyber threat intelligence to investigate and report how a cyber attack happened.
This article will provide you with an overview of the Cyber Kill Chain, why it is useful, and how to use it. You will see the kill chain in action as we go through a real-world case study focusing on Trigona ransomware. This will provide you with the knowledge and skills to use the Cyber Kill Chain in your work and analyze intrusions better.
Let’s get started learning this structured analytical technique!
What is the Cyber Kill Chain?
The Cyber Kill Chain is a structured framework for understanding the different stages a cyber attack must complete to be successful. It was created by Lockheed Martin, an American aerospace, arms, defense, information security, and technology corporation, in 2011 as part of their Intelligence Driven Defense initiative. Since then, it has become a staple in the cyber security industry.
It is primarily used as a tool for understanding the progression of an attack and then developing. strategies to detect and disrupt it (killing the chain). As a cyber threat intelligence analyst, you will use it as a structured analytical technique when analyzing intrusion data, categorizing intelligence in threat reports, and crafting reports for key stakeholders.
Structured analytical techniques like the Cyber Kill Chain, Diamond Model, and Analysis of Competing Hypotheses empower analysts to perform consistent, comprehensive, and thoughtful data analysis. These frameworks, models, and methodologies help you make better decisions when analyzing threat intelligence.
The 7 Stages of the Cyber Kill Chain
So what actually is the Cyber Kill Chain, and how does it describe the lifecycle of a cyber attack?
The Cyber Kill Chain consists of seven stages describing a key objective during a typical cyber attack. To succeed, a cyber attack must usually complete each stage sequentially. Let’s look at each stage in detail.
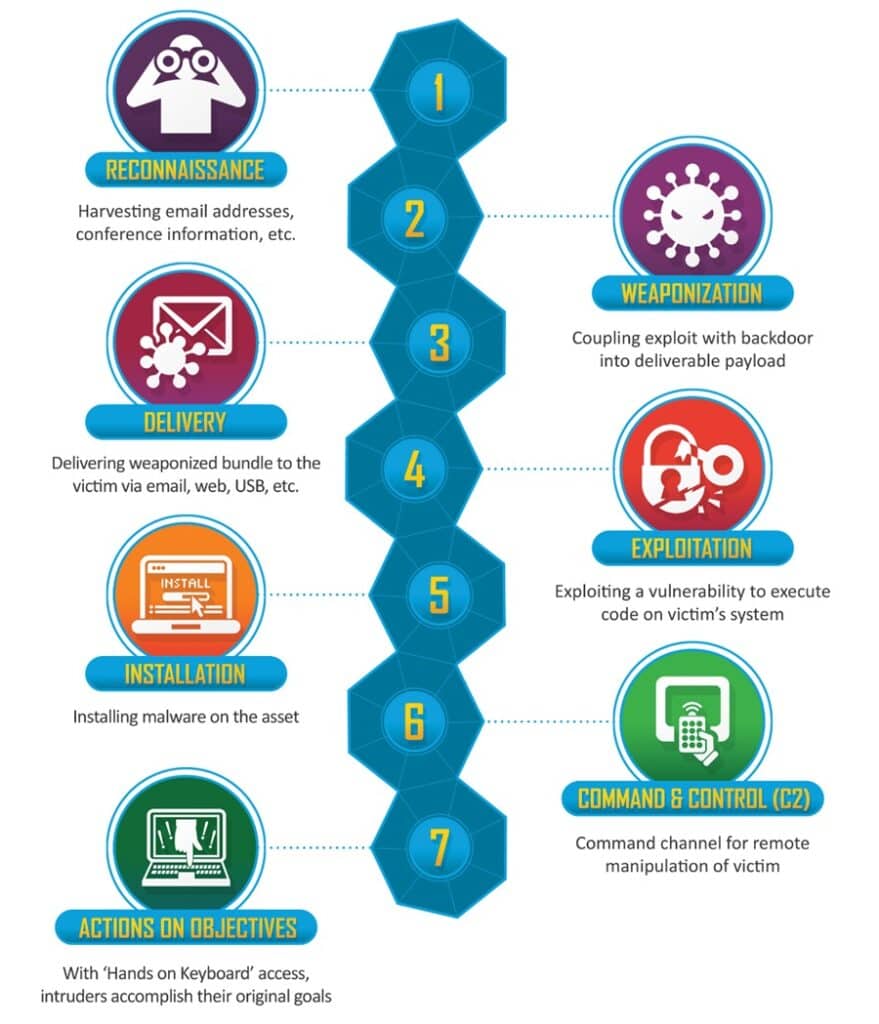
Stage 1: Reconnaissance
All cyber attacks start with gathering information about their target. This includes details like the target’s infrastructure, employees, technology stack, and potential vulnerabilities. This information helps adversaries plan out their attack, strategize how they will gain initial access, and solidify what objectives they want to achieve.
At this stage, you will typically see attackers scanning networks, using social engineering tactics to get information from employees, and performing Open Source Intelligence (OSINT) gathering to collect as much public information about a target as possible.
Stage 2: Weaponization
After gathering information, attackers must create or acquire the tools, exploits, or other capabilities that will allow them to exploit vulnerabilities within the target’s systems and achieve their objectives.

This may involve building malware or custom hacking tools, crafting phishing emails and a convincing pretext, or developing any other capability to weaponize the information they gathered and perform a successful attack.
Stage 3: Delivery
Once an attacker has their weaponized payload ready, they must deliver it to the victim. This can be done through various phishing tactics (e.g., email attachments, a link to a malicious website, etc.). But can include other attack vectors, such as targeting vulnerable services that are public-facing, compromising the target’s website, or gaining physical access to the target’s offices.
The delivery mechanism heavily depends on the information gathered during the Reconnaissance stage. If the target has a vulnerable mail server, you could target this, or if the company is lax on email security, you may choose to use phishing.
This is why Reconnaissance is often the most important stage of any cyber attack. Limiting public information about your organization can often thwart a potential attack before it even starts.
Stage 4: Exploitation
After the malware payload has been delivered, it will execute on the target system and take advantage of software bugs, misconfigurations, weak authentication mechanisms, or missing security controls to provide the attacker with initial access to a system.
This stage may involve a vulnerability being exploited to gain remote access or a user inadvertently executing malware on their system after clicking on an email attachment in a phishing email. Either way, the goal of this stage is to get unauthorized access to a target system and an initial foothold in the target’s corporate network.
Stage 5: Installation
Once initial access is achieved, attackers will install persistence mechanisms that solidify this foothold and can withstand password resets, system reboots, or security updates. Common persistence mechanisms include registry run keys, scheduled tasks, cron jobs, Windows services, and the Windows Startup folder.
You can learn more about persistence mechanisms in the Hunting for Persistence With Cympire series. It covers common techniques attackers will use and how you can hunt for them in an interactive learning environment.
Stage 6: Command and Control (C2)
With persistent access to target systems, attackers will next try to establish communication channels between compromised systems and their command infrastructure. This allows them to remotely control compromised systems and perform post-exploitation activities, such as data exfiltration, escalating privileges, and lateral movement.
Many post-exploitation activities require attackers to upload hacking tools they developed or acquired during the Weaponization phase to compromised machines using C2 frameworks like Cobalt Strike, Slither, and PowerShell Empire.
Stage 7: Actions on Objectives
The final stage of a cyber attack is where a threat actor achieves their goals. This may include exfiltrating sensitive data, gaining access to a certain machine, sabotaging key infrastructure, performing espionage, deploying ransomware, or any other malicious action they were tasked with performing.

So that’s how the Cyber Kill Chain works. It describes the typical lifecycle of a cyber attack using seven key stages, from Reconnaissance to Exploitation to Actions on Objectives. But why is knowing this kill chain useful? Let’s find out.
Why Use the Cyber Kill Chain?
The Cyber Kill Chain provides a structured model for understanding how a cyber attack plays out, what an attacker must do to be successful, and where you can look for them. This understanding allows defenders to identify potential security measures they can create to detect or disrupt a cyber attack.
Perhaps a recent cyber attack was stopped at the Exploitation stage because your organization had strong endpoint detections in place. It would be best not to rely on these detections in the future and prevent the attack at the Delivery stage. Using the Cyber Kill Chain, you can strategize ways to do this, such as implementing better email protection to defend against phishing emails.
The Kill Chain allows you to map your defenses to each stage of a cyber attack and assess which ones are effective, which are getting bypassed, and any gaps where you need new ones to increase your resilience to attacks.
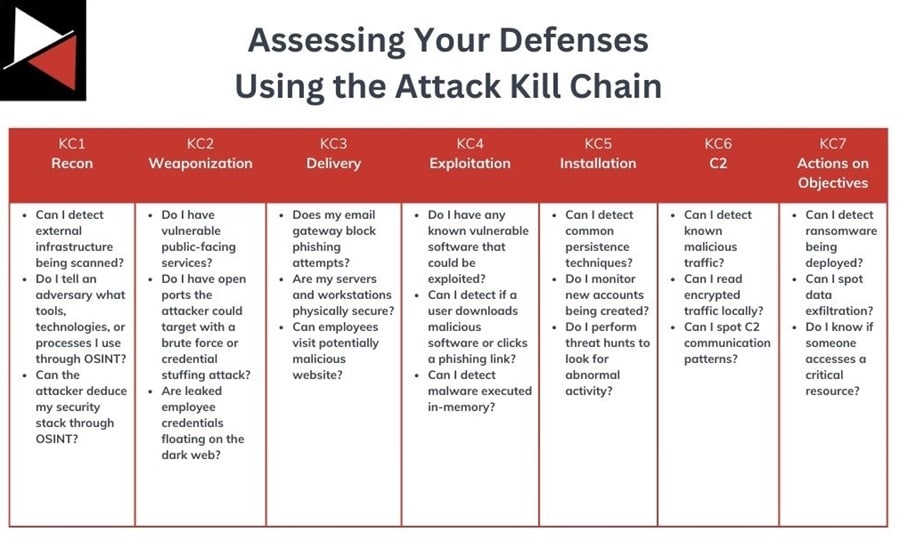
Aside from strategic planning, the Cyber Kill Chain is also a great reporting tool. It allows you to create an attack narrative that describes how an attack happened in a structured way. This helps non-technical audiences understand what an attacker did, what made them successful, and what can be done to stop them in the future.
Your report doesn’t just help your organization. It can also help other defenders learn from your intrusions and better defend themselves. Cyber security companies will often share intelligence reports that detail cyber attacks. The Cyber Kill Chain provides a common language that analysts can use to describe attacks and share intelligence with one another, fostering communication and collaboration against threats.
To summarize, here are the key benefits the Cyber Kill Chain provides.
Key Benefits of the Cyber Kill Chain
- Provides a structured approach to defending against cyber attacks and investigating intrusions.
- Helps non-technical stakeholders understand the lifecycle of cyber attacks.
- Great for visual reporting and providing a high-level overview of an intrusion using an attack narrative.
- It can be easily integrated with frameworks and methodologies that provide more granular technical details on what exactly an adversary did, like the MITRE ATT&CK matrix.
- Helps foster communication and collaboration across organizations by providing a common language for analysts to communicate their findings.
The Cyber Kill Chain in Action
Now you know what the Cyber Kill Chain is, how it works, and why it is useful, let’s look at a practical example of using the framework. This will show how cyber security professionals use the Cyber Kill Chain to analyze intrusions, share cyber threat intelligence, and report findings to key stakeholders.
Case Study
For our demonstration, we will use this excellent write-up by the team at the DFIR Report: Buzzing on Christmas Eve: Trigona Ransomware in 3 Hours. It describes how attackers exploited a publicly exposed Remote Desktop Protocol (RDP) host to gain initial access and deploy Trigona ransomware against an organization.
The report includes comprehensive details on TTPs used, IOCs found, and a timeline of events. Much of this data is irrelevant as we only care about how the attack maps to the Cyber Kill Chain. That said, I highly recommend reading the report in full and learning the technical details of how real-world cyber attacks unfold.
Applying the Cyber Kill Chain
When applying the Cyber Kill Chain to a real-world investigation, it can be useful to map out the seven stages of the kill chain and fill in each as you gather data about the intrusion. For instance, if you find a phishing email, you can add this to the Delivery mechanism, then pivot off of this email (data point) to add the malware attached to the Exploitation stage. Creating a narrative of how an attack unfolds.
Once you have mapped out all your current data, you can identify what you are missing. You might have spotted the Exploitation method but missed anything related to the Command and Control stage. At this point, you want to work your way up the kill chain and race to the end to complete it. This will allow you to assess the damage caused by the intrusion and contain or mitigate any remaining threats.
After reaching the end of the kill chain and containing the threat, you will want to work your way back down the stages to map out the attack and create a complete attack narrative. This lets you identify any visibility gaps or stages that need further investigation to connect the dots
If you are still missing stages, you must prioritize investing resources into bolstering defensive strategies that can detect threats related to these stages. This ensures you are better prepared for the next intrusion.
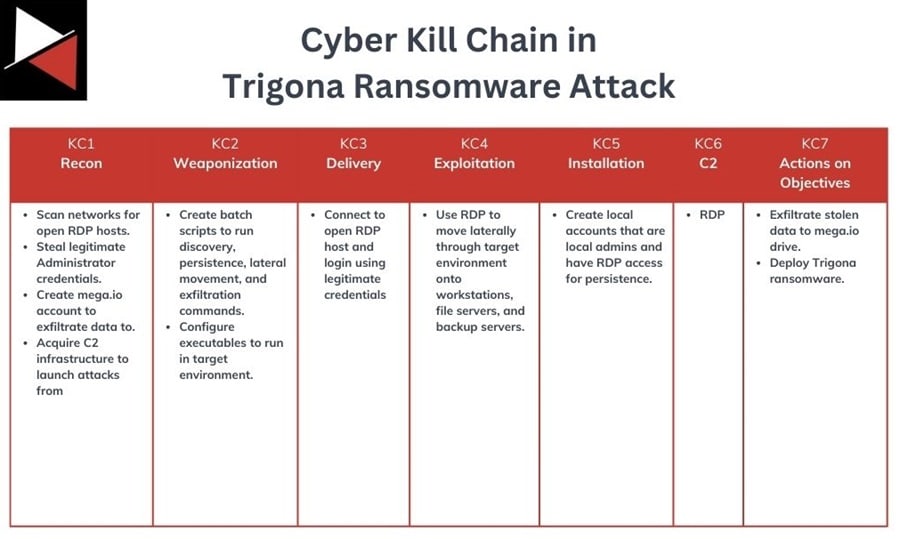
The report Buzzing on Christmas Eve: Trigona Ransomware in 3 Hours maps to the Cyber Kill Chain as follows (stages are denoted KC in red).
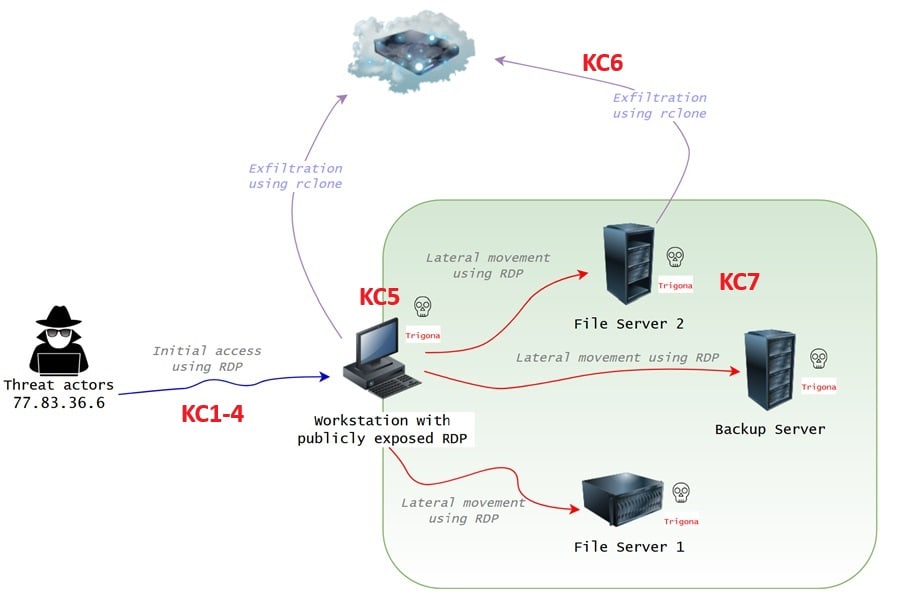
Stage 1: Reconnaissance
This attack used an open RDP connection and legitimate Administrator credentials to gain initial access. The attackers then deployed various bash scripts, executables, and the SoftPerfect Netscan tool for internal reconnaissance and lateral movement. Finally, exfiltrating data with rclone and dropping Trigona ransomware for impact.
At the Reconnaissance phase, the attackers would have run scans for machines with open RDP, stolen the legitimate credentials they abused, and acquired the tools/scripts to perform this attack. They would have also had to acquire the infrastructure used to launch the attack, buy an account on mega.io to exfiltrate stolen data to, and scout what security solutions the organization used.
Generally, you will not have visibility into the recon stage. You might see some scans or a threat actor buy credentials if you are performing dark web monitoring. But, often, the best way to defend against Reconnaissance is to have fully patched external facing services and good operational security that doesn’t divulge key security details, tools, or strategies your organization uses.
Stage 2: Weaponization
In this attack, the adversary solely relied on external RDP for access and persistence. No custom malware was needed. They still would have had to configure or create the batch scripts and executables they ran, the commands used to disable Windows Defender and exfiltrate data using rclone, and adjust the Trigona ransomware settings.
Again, defending against an attack during the Weaponization stage is difficult. Your best course of action is to ensure you have a small attack surface with no public-facing vulnerabilities an attacker could exploit for initial access.
This stage is more interesting from an intelligence prospective after an attack when you begin looking for human fingerprints, asking questions like why you chose a certain software, what malware configuration they used, and aim to find patterns in their choices. Finding a human link allows you to track intrusions, create campaigns, and predict what adversaries may do next.
Stage 3: Delivery
The adversary gained initial access through an open RDP host with stolen credentials. They likely gained these credentials and discovered the exposed RDP host before targeting this organization specifically. Making this a target of convenience rather than a targeted attack.
Cybercriminals will buy large quantities of leaked credentials and constantly scan the Internet for vulnerable services. If they find one, they will target it. This was likely an untargeted attack and leaked credentials and exploitable public-facing service led the attacker to target this organization.
Stage 4: Exploitation
No technical vulnerabilities were exploited in this attack. The threat actors could compromise machines due to poor security and mismanaged credentials. They used batch scripts not detected by security tools, legitimate executables to live off the land, and RDP to blend into legitimate network activity.
They also moved quickly, gaining initial access and deploying ransomware within three hours, and chose a time when most of the security team would be away. This speed allowed them to circumvent defenders and was fuelled by a poor security architecture.
Defending against exploitation can be difficult because you cannot account for every vulnerability in your organization’s software. This is why defense in depth, segregated networks, role-based access control (RBAC), and a focus on limiting what an attacker can do once they are inside your internal network are so important.
Stage 5: Installation
For persistence, the attacker used local accounts that they added to the local administrators group and Remote Desktop Users group. However, the speed at which they pivoted around the network, exfiltrated data, and dropped the ransomware meant these accounts were not used in the end.
Defending against installation comes down to having technical controls that can detect or hunt for persistence techniques and ensuring defenders have strong situational awareness. Your security operations team must monitor when new accounts are created and added to privileged groups and respond efficiently.
Stage 6: Command and Control
This attack is what is commonly called a “smash and grab.” The attackers did not use complex C2 infrastructure or custom implants that evaded security controls through sophisticated mechanisms. Instead, they relied on the organization’s free use of RDP to pivot between machines and exfiltrate data.
Defending against the Command and Control stage requires network monitoring and endpoint detection tools. Sophisticated attacks often use encrypted or obfuscated traffic to evade detection. Defenders must be vigilant of new network connections in their environment.
Stage 7: Actions on Objective
In this attack, the adversary exfiltrated data to mega.io using rclone and then deployed Trigona ransomware. Seeing these two actions take place in the system logs confirmed that this cyber attack was successful and the threat actor had achieved their objectives.
Exfiltration can be one of the hardest actions to defend against. If done “slow and “low,” where an attacker transfers small amounts of data over an extended period of time, it can be very difficult to detect. On the other hand, ransomware is often detected by even the most basic security endpoint tools. The difficulty with ransomware is containing it.
Once you have mapped an attack to the Cyber Kill Chain, you can use other frameworks like the MITRE ATT&CK matrix to add more granular technical details about what the attacker actually did to complete each stage. For example, they may have used a phishing email to complete the Delivery stage, but was this a phishing link, email attachment, or service? MITRE ATT&CK lets you add these details to your report, making it easier to operationalize the intelligence.
To learn more about the MITRE ATT&CK framework and how you can use it for cyber threat intelligence, read MITRE ATT&CK Framework: The Holy Bible of Threat Intelligence.
Now that you’ve seen the Cyber Kill Chain in action, here are some practical recommendations for using it.
Practical Recommendations on Using the Cyber Kill Chain
The Cyber Kill Chain is a great framework for structuring your analysis and reporting findings. However, translating this theoretical model into the real world can be challenging. To help you get started, here are some practical recommendations for using the Cyber Kill Chain for your daily work:
- Integrate the Cyber Kill Chain with other frameworks: Integrate the Cyber Kill Chain with other frameworks like MITRE ATT&CK matrix, NIST Cybersecurity Framework, and Diamond Model to develop a more complete and comprehensive defense strategy.
- Use the framework for reporting strategic threat intelligence: The kill chain is well-suited for reporting strategic intelligence aimed at key stakeholders who don’t need the deep technical details of an attack. Instead, it provides a high-level, narrative-driven overview of an attack that can be easily visualized.
- Create an attack narrative using the framework: All reports should include an attack narrative that intuitively communicates how a cyber attack happened. The kill chain is perfect for this. It provides a structure for showing how an attack progressed and can be tuned to be technical or non-technical to match your intended audience.
- Categorize and group data based on the kill chain: When investigating an intrusion, categorize IOCs, TTPs, and other data into each stage of a Cyber Kill Chain. This will make tracking what happened and what data you still need to find much easier. It also makes reporting easier as you already have a structure to follow.
- Use it to structure your investigations: The kill chain is a great tool to structure your investigations and ensure they are systematic, organized, and complete. It empowers analysts to quickly spot gaps in their investigations and fully understand how a cyber attack was successful.
To discover the real-world challenges you will face when using the Cyber Kill Chain, read 5 Cyber Kill Chain Challenges and How to Prevail. This will guide you through overcoming common struggles cyber security professionals face when using this analysis technique.
Conclusion
In this article, you learned about the cyber kill chain, its value to defenders, and how to use it best. You even saw the kill chain applied to a real-life case study where we discussed how a Trigona ransomware attack unfolded on Christmas Eve.
You should now have the knowledge and skills to use this fundamental framework. I suggested revisiting the practical recommendations detailed when it comes time to use the kill chain, and remembering the Cyber Kill Chain is just there to structure your analysis. You need to investigate and fill in the technical details. Good luck!
Frequently Asked Questions
What are the 7 Stages of the Cyber Kill Chain?
The Cyber Kill Chain describes the seven high-level stages of a cyber attack. These include:
- Reconnaissance: The attacker gathers information about their target to plan their attack.
- Weaponization: The attacker creates or acquires the tools required to exploit vulnerabilities within the target’s systems. This ends when a weaponized payload is created.
- Delivery: The weaponized payload is delivered to the target.
- Exploitation: The payload is executed, exploits vulnerabilities within the target’s systems, and initial access is gained.
- Installation: Malware is installed on target systems to establish a foothold and maintain persistence.
- Command and Control (C2): The attacker establishes a communication channel between the compromised systems and their command infrastructure. This allows them to remotely control the comprised systems.
- Actions on Objectives: The attacker achieves their strategic goals against the target. This could include data exfiltration, sabotage, espionage, deploying ransomware, or other malicious actions.
What Is the Difference Between the Cyber Kill Chain and MITRE ATT&CK?
The Cyber Kill Chain and MITRE ATT&CK matrix are both frameworks for describing how a cyber attack happens. The Cyber Kill Chain focuses on providing a step-by-step, high-level overview to a non-technical audience. It is used for strategic planning, visualization, and reporting.
The MITRE ATT&CK matrix focuses on describing the tactics, techniques, and procedures (TTPs) used by adversaries across various stages of an attack. It is a much more detailed framework that aims to provide a comprehensive catalog of attacker behaviors so defenders can understand and respond to a wide range of threats.
Is the Cyber Kill Chain Still Relevant?
Yes. The Cyber Kill Chain is still a useful framework for describing the key stages of cyber attacks and is widely used in the cyber security industry for analyzing intrusions, reporting, and strategic planning.
To get the maximum benefit from the framework, it is recommended to integrate it with other, more technical frameworks and methodologies like the MITRE ATT&CK matrix, NIST Cybersecurity Framework, and Diamond Model. These frameworks provide more details and help you implement specific mitigations to defend yourself from cyber attacks.