Your organization’s incident response playbook can be the difference between defending against a cyber attack and becoming a victim.
An incident response playbook is a step-by-step guide on how your organization should
respond to and manage cybersecurity incidents. It provides your security team with instructions to follow when they encounter a potential cyber attack and are a proactive approach to minimizing the impact of an attack.
All organizations with a mature cybersecurity program extensively use incident response playbooks to ready their team, quickly resolve incidents, and effectively defend against attacks.
This article will detail the key components of these playbooks, teach you how to create your own, and advise you on the best implementation practices. Let’s get started on your journey to building enterprise-ready incident response playbooks!
Key Components of an Incident Response Playbook
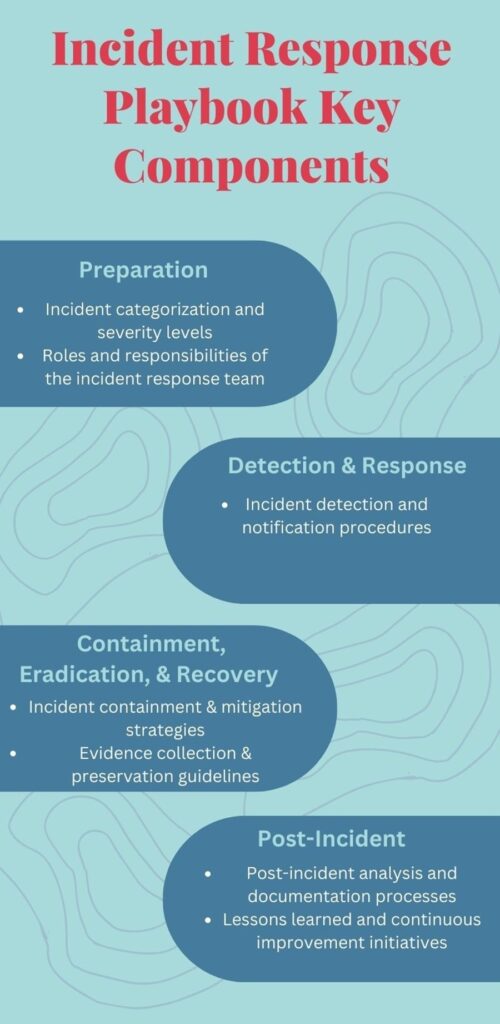
Incident response playbooks contain several key components you must address if yours will be effective. You can ensure you cover them all by following the National Institute of Standards and Technology’s (NIST) Incident Response Lifecycle. This model maps the lifecycle of a cyber incident and provides guidance on how to respond at each phase.
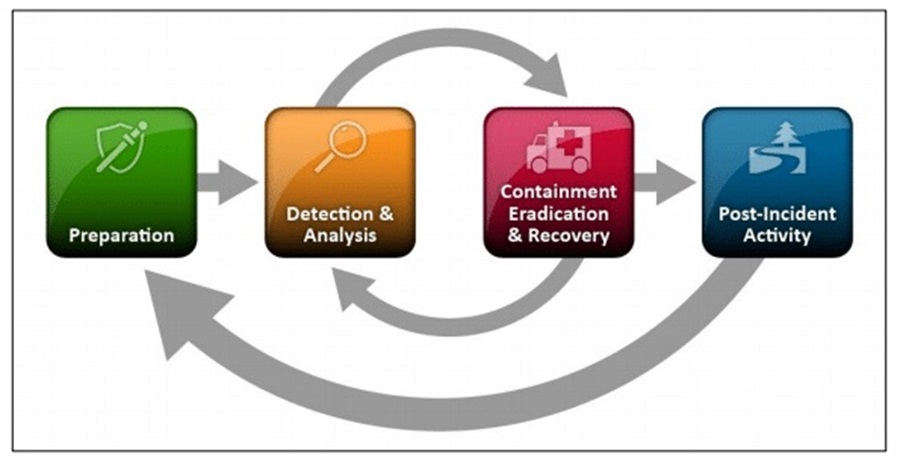
Phase 1 – Preparation
This first phase of the lifecycle lays the foundation for an effective incident response capability within an organization. It involves setting up vital resources and tools, creating policies, defining key roles and responsibilities, and establishing communication channels. There are several key playbook components you must create to cover this phase of an incident.
Incident Categorization and Severity Levels
You need to define clear criteria for how an incident should be categorized and prioritized by your cyber security team. Common categorizations include Ransomware, Potential Unwanted Program (PUP), Malware, and Risky Behavior. You can then use a severity scale to assign an incident a priority level from one (P1) to four (P4), with P1 being the most severe.
Roles and Responsibilities of the Incident Response Team
Your playbook should include the key roles and responsibilities and who these have been assigned to on your cyber security team. Clearly defining roles and responsibilities before an incident occurs ensures no time is wasted when an incident arises, and everyone involved knows what is expected. Some key roles and responsibilities include
- Incident Response Manager – Coordinates activities among team members, communicates with key stakeholders, determines the allocation of resources, and is responsible for the overall incident response effort.
- Technical Analyst – Conducts technical analysis of network and endpoint indicators to determine the nature and scope of an incident. They gather evidence, analyze logs, and investigate suspicious or malicious activity to identify the affected assets and attack vectors. They are responsible for root cause analysis of an incident, and the SOC usually performs this role.
- Forensic Expert – Conducts in-depth analysis of systems to reconstruct the sequence of events. This often involves collecting and preserving digital evidence for potential legal action. This role is usually performed by an external third party who has specialized expertise and the organization has on retainer.
- Vendor Manager – Coordinates with external vendors or service providers to address the incident and ensures third-party involvement aligns with incident response goals.
- Executive Manager – Receives regular updates on the incident’s progress and impact. They are responsible for making critical decisions regarding resource allocation, communication strategies, and potential escalation.
- Legal and Compliance Manager – Ensures incident response activities adhere to legal and regulatory requirements. They are responsible for providing guidance on data breach notification laws and compliance obligations.
Escalation and Communication Channels
Cyber security incidents will require different levels of expertise to handle. A level 1 Security Operations Center (SOC) analyst may be able to handle a PUP incident, but they will need to escalate it to a more experienced analyst for a Ransomware incident.
This is where having clear escalation paths and efficient communication channels is vital. An incident needs to be communicated with the right person in the shortest time possible to generate an effective response. Once you have clearly defined the roles and responsibilities of your incident response team, you can create communication channels between these roles to handle an incident effectively.
Phase 2 – Detection and Analysis
In this phase, the SOC first detects and analyzes an incident. The SOC will monitor systems, networks, and other devices for signs of malicious activity. If detected, they will investigate this activity to determine its severity, the impact on the organization, and how they can potentially mitigate it.
Incident Detection and Notification Procedures
Your security team is responsible for creating detections that alert your SOC when malicious activity occurs on your organization’s network or endpoint devices. In your incident response playbook, you must define how these alerts are investigated and how key personnel are notified.
There are several benefits to having a documented procedure that analysts can follow whenever an incident arises:
- A consistent approach to investigating incidents.
- Analysts can investigate incidents more efficiently using a shared knowledge base.
- You limit the chances of incidents being missed.
- Key details are captured and documented for every incident. These can be used to prepare for future incidents and inform your defensive strategies.
When I worked as a SOC analyst at a large Managed Security Service Provider (MSSP), we used a Security Orchestration, Automation, & Response (SOAR) tool that provided templates for security incidents.
If our security tools detected a PUP, we would use our PUP template and fill out the investigation details that the template requested. If malware was detected, we would use our malware template, which included additional investigation details.
Templates are a great way to help analysts consistently investigate incidents and allow for many tedious details to be automated away. This frees an analyst to investigate more incidents or perform other tasks.
Phase 3 – Containment, Eradication, and Recovery
Once an incident has been analyzed, the security team needs to take action to contain, eradicate, and recover from any potential impact. This typically involves your SOC and Digital Forensics and Incident Response (DFIR) team working together to minimize the impact of an incident and prevent any further damage.
Your incident response playbook should cover two key essentials during this lifecycle phase.
Incident Containment and Mitigation Strategies
Different incidents require different containment and mitigation strategies. How you approach generic malware (e.g., an information stealer) will differ from your ransomware strategy. Each strategy must be documented in your incident response playbook so your security team can follow the relevant strategy to contain and mitigate an incident effectively.
By developing a strategy before an incident occurs, you can thoroughly test and refine it to ensure it is fit for purpose. You can also consult with industry experts to ensure your containment and mitigation strategies are thorough enough.
Evidence Collection and Preservation Guidelines
Once you have contained an incident and mitigated any further threats, you can begin collecting evidence to determine the impact of the incident and ways you can prevent it from occurring again.
You must provide your DFIR team guidelines around collecting evidence, as your organization may have legal or regulatory requirements for digital forensic data. For instance, you may need a specialist forensic investigator to collect this digital evidence.
Phase 4 – Post-Incident Activity
The final phase of the incident response lifecycle involves an organization analyzing the incident and documenting lessons learned. This allows you to be better prepared when a similar incident occurs.
Post-Incident Analysis and Documentation Processes
After an incident has been contained and mitigated, you need to perform a post-incident analysis to determine why the incident occurred and its impact on your organization.
Legal or regulatory requirements may require you to disclose the impact of the incident. However, even if these are irrelevant, it is still important to document your findings to improve your organization’s cyber security posture and fill any holes.
Lessons Learned and Continuous Improvement Initiatives
Your post-incident analysis will help you identify any security gaps or vulnerabilities that allowed the incident to impact your organization. Your findings should be documented as lessons learned, and you must prioritize filling these gaps through improvement initiatives.
By documenting and analyzing your organization’s incidents, you can ensure your cyber security program continuously improves and adapts to the ever-evolving cyber security landscape.
Developing an Effective Incident Response Playbook
Now you know the key components to include in your incident response playbook, let’s look at how you can develop an effective playbook for your organization.
Step 1: Establish Which Security Teams Will Use Your Incident Response Playbook
The first step in playbook development is deciding what security teams will use it. You may have one playbook designed for your SOC team and another for your DFIR team. On the other hand, you may choose to create incident response playbooks based on the nature of the incident and have both teams use the same playbook.
A clear picture of who the playbook is for will help you define its objectives and incident response procedures based on the team’s expertise.
Step 2: Define Clear Objectives and Goals
Once you have established who will use your incident response playbook, you need to define the objectives and goals of your playbook. These describe the playbook’s scope and will help you detail how the playbook is used.
Step 3: Conduct a Risk Assessment
With the scope of the playbook determined, you can move on to conducting a risk assessment of your organization. This involves identifying your organization’s threats and the risks you must mitigate. By identifying these threats, you can prioritize the assets you need to allocate resources to protect and the key incident response tasks that must be performed if they come under attack.
Step 4: Map Incident Response Procedures
Incident response procedures are the main part of any playbook. They provide a step-by-step guide to handling an incident, from the detection and analysis phase to the post-incident phase.
Your incident response procedures should look like a cooking recipe with the tools and resources required to respond to an incident listed first and then details about the tasks that must be completed to respond to an incident. They should also detail any dependencies the playbook user may need to rely on or communication/escalation channels they may need to use.
Optimizing your incident response procedures, and the workflow of your security team, is imperative for quickly mitigating threats and reducing the impact of security incidents.
Step 5: Collaborate With Key Stakeholders and Subject Matter Experts
When you conduct your risk assessment and develop your incident response procedures, you may be unclear on how to handle certain incidents best. This is when you should consult key stakeholders and subject matter experts for guidance.
These experts can direct you on the best practices for quickly resolving incidents and the important workflows that need to be created to optimize your incident response. They can also evaluate your playbook procedures to determine if they will stand up to a real incident and offer advice on improving them.
Step 6: Document Step-By-Step Incident Handling Instructions
Once you have your incident response procedures mapped out, you must thoroughly document these incident handling instructions step-by-step so your security team can easily follow them. This is anomalous to filling in the cooking recipe you previously mapped out with the specific steps the cook must take.
This documentation should include the reporting requirements that the team should complete during and after an incident. Reporting is required to ensure all best practices were followed, to meet regulatory requirements, and to present to key stakeholders.
It’s important to be very clear and precise with your documentation. During an incident, a lot of people panic and waste valuable time. If you can succinctly document all the actions required to respond to an incident in one location efficiently, your team won’t waste time panicking or trying to generate a response on the spot.
Step 7: Periodically Review the Incident Response Playbook
Once you complete your playbook, scheduling a time to review it periodically is important. During this review, you should ensure that your playbook:
- Covers all possible use cases and incident scenarios based on your risk assessment.
- Aligns with the latest cybersecurity best practices in the procedures and workflows you have mapped out.
- Your cybersecurity team can follow the step-by-step incident handling instructions in the playbook.
- Any key dependencies have changed (e.g., key personnel, contact details of employees or contractors, tools, resources, etc.).
- Automation has been created to improve the efficiency of your incident response procedures.
Regularly reviewing your incident response playbooks is crucial for keeping up with the ever-evolving cybersecurity landscape.
Best Practices for Implementing Incident Response Playbooks
Incident response playbooks can be notoriously difficult to get right on your first try. There are various variables to account for and nuances that arise from different situations. This is why it takes organizations many revisions to optimize their incident playbooks and put themselves in the best possible position to combat cyber attacks.
That said, there are several best practices that you can follow to aid you in the successful implementation of your incident playbooks.
Training and Educating the Incident Response Team
Your security team should have the skills to perform every action detailed in your incident response playbook. They should be able to efficiently analyze, investigate, and mitigate cyber threats and be trained on the tools used by your organization.
It is critical that your incident response team has the prerequisite skills to execute your playbook and continues to develop its skill sets to keep up with the changing cybersecurity landscape.
Testing and Validating the Playbook Through Simulations and Drills
To ensure your playbook will work during an incident, you should schedule a time to test and validate the incident response procedures and workflows you have mapped out. You can run your security team through simulations that mimic a real-world cyber attack or use drills that allow the team to practice specific procedures.
Integrating the Playbook With Existing Security Tools and Systems
A successful playbook must integrate with your security tools and systems. If you use an Endpoint Detection and Response (EDR) solution, for example, your incident response procedures must align with this tool’s specific features and capabilities.
If you fail to consider your current cybersecurity capabilities provided by your tools and systems, your playbook will not be specific or detailed enough for your security team to follow.
Establishing Metrics and KPIs to Measure Playbook Effectiveness
You must continually improve your playbook as the cyber landscape changes. To do this, you need a method to measure your playbook’s effectiveness in allowing your team to respond to incidents. This is often done using KPIs and metrics that measure the effectiveness of your team’s response efforts. Common metrics include; mean time to detect (MTTD), mean time to respond (MTTR), and your incident resolution rate.
By having predefined measurements established, you can track the maturity of your playbooks and identify areas for improvement.
Continuously Updating the Playbook to Address New Threats and Vulnerabilities
Step 7 of incident response playbook development involves scheduling time to review your playbooks periodically. This is crucial to ensure that your playbooks are continuously updated and improved.
Creating an incident response playbook is an iterative process that involves refining current procedures and adding new ones as emerging threats are discovered. Your playbooks should continuously evolve as the cybersecurity landscape changes, with each iteration improving on the last.
Building in Automation Where Possible
You should automate playbook tasks whenever possible to limit the strain on your security team, reduce errors, and speed up the incident response process. Automation is game-changing for cyber security as it allows you to scale your existing processes exponentially. You should always be on the lookout for chances to utilize it.
Common incident response playbook automation includes; generating templates for certain incidents, automatically collecting data from a machine to investigate when an incident occurs, and gathering additional context around an incident to aid an analyst in their investigation.
Conclusion
Incident response playbooks are indispensable resources that guide your security team to resolve incidents and combat cyber threats efficiently. Your playbooks should provide your team with step-by-step instructions on responding to and managing cyber security incidents based on industry best practices.
To mature your organization’s cyber security posture, you must begin developing and implementing incident response playbooks today using the steps discussed in this article. Once complete, train your team to use this resource as an anchor to stir your organization to safety when everyone else is panicking.
Remember to address the key components every incident response playbook should include and follow the best implementation practices described. This will help you create a playbook that thoroughly details the practical steps to resolve an incident using your organization’s tools and technologies.
Good luck creating your incident playbooks!




