Intrusion analysis is a fundamental skill that all cyber security and threat intelligence analysts must have. It requires detecting, triaging, investigating, and responding effectively to an incident – the bread and butter of cyber defense.
This guide will teach you how to do just that. You will learn what intrusion analysis is and how to perform it using a four-step process. You will also see some tools and technologies that will aid you. Also included are some cheat sheets to help you know what to look for, where to find it, and how to use it during your analysis.
Let’s jump in and start exploring intrusion analysis!
What is Intrusion Analysis?
Intrusion analysis is the art and science of detecting, investigating, and responding to a cyber security incident. It involves the systematic and structured interrogation of data sources and the individual intuition and critical thinking required to stop a cyber attack in its tracks.
A cyber security incident is an event (or series of events) that threatens the integrity, confidentiality, or availability of your data or IT systems. It could be a cyber attack, accidental misuse of company assets, or a system failure/misconfiguration.
The goal of intrusion analysis is to effectively detect, investigate, and respond to a cyber threat to minimize its impact on your organization. This is important for several reasons:
- Proactive Defense: Intrusion analysis enables you to detect and respond to threats promptly, reducing the impact of cyber attacks on your organization’s data, systems, and reputation.
- Incident Understanding: By analyzing intrusions, organizations can gain insights into the tactics, techniques, and procedures (TTPs) used by attackers. This allows you to defend against them more effectively in the future and enhance your overall security posture.
- Regulatory Compliance: Many industries require robust intrusion detection and response capabilities to comply with industry standards and regulations to safeguard customer data.
- Continuous Improvement: Lessons learned from intrusion analysis help you improve your cyber security defenses and incident response processes. This makes you more resilient against future threats and showcases where you need to prioritize resources.
To achieve this goal and reap the benefits, you must thoroughly analyze and investigate intrusions. This can be achieved by following a structured and methodological approach, which will be detailed later in this article.
That said, a guide is just a guide. You must follow some key best practices before and after an incident to ensure your intrusion analysis is consistent, efficient, and consistently improving.
- Regular Monitoring and Updates: Emphasize the importance of continuous monitoring and updating detection systems. This is key to triggering the intrusion analysis process and ensuring you are detecting the latest threats.
- Training and Awareness: Ensure analysts receive ongoing training to recognize and respond to threats. Your intrusion analysis process is only as good as your weakest team member.
- Incident Response Planning: All organizations must have a well-defined incident response plan. You must be prepared to jump into action at a moment’s notice. The best way to prepare is to run simulations, practice drills, and streamline workflows.
- Collaboration and Information Sharing: Regularly collaborate and share information with other organizations within your industry or community. Sharing threat intelligence allows everyone to bolster their defenses and proactively defend against threats.
Now that you understand intrusion analysis and its importance, let’s discuss how to perform it.
The Intrusion Analysis Process
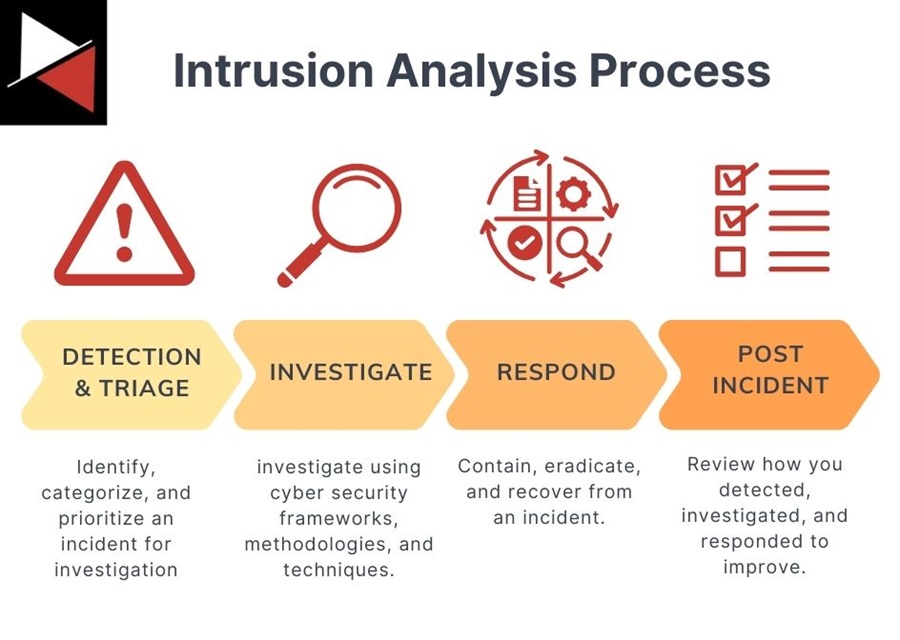
To effectively investigate cyber attacks, you must follow a four-step process.
- Detection and Triage: You identify, categorize, and prioritize an incident for investigation.
- Investigation: You investigate the incident using various cyber security frameworks, methodologies, and analytical techniques.
- Response: You contain, eradicate, and recover from an incident.
- Post-Incident: You review how you detected, investigated, and responded to an incident to identify areas for improvement. Here, you create a Lessons Learned document to improve your incident response process.
These four steps make up the intrusion analysis process. Performing each one comprehensively will ensure an incident is handled appropriately, rapidly resolved, and the correct action is taken.
These four steps align with the NIST and SANS incident response steps.
Detection and Triage
The first step in the intrusion analysis process is detection and triage. You must first detect and assess a threat before you can start investigating and responding to it.
Detection is typically an automated activity performed by various security tools and technologies, such as SIEM (Security Information and Event Management), Intrusion Detection Systems (IDS), and Endpoint Detection and Response (EDR) solutions.
These tools have detection rules that trigger when an Indicator of Compromise (IOC) is spotted, a threshold is reached, or suspicious behavior is observed. Once triggered, an alert kickstarts the intrusion analysis process. An analyst will pick up this alert and move on to performing triage.
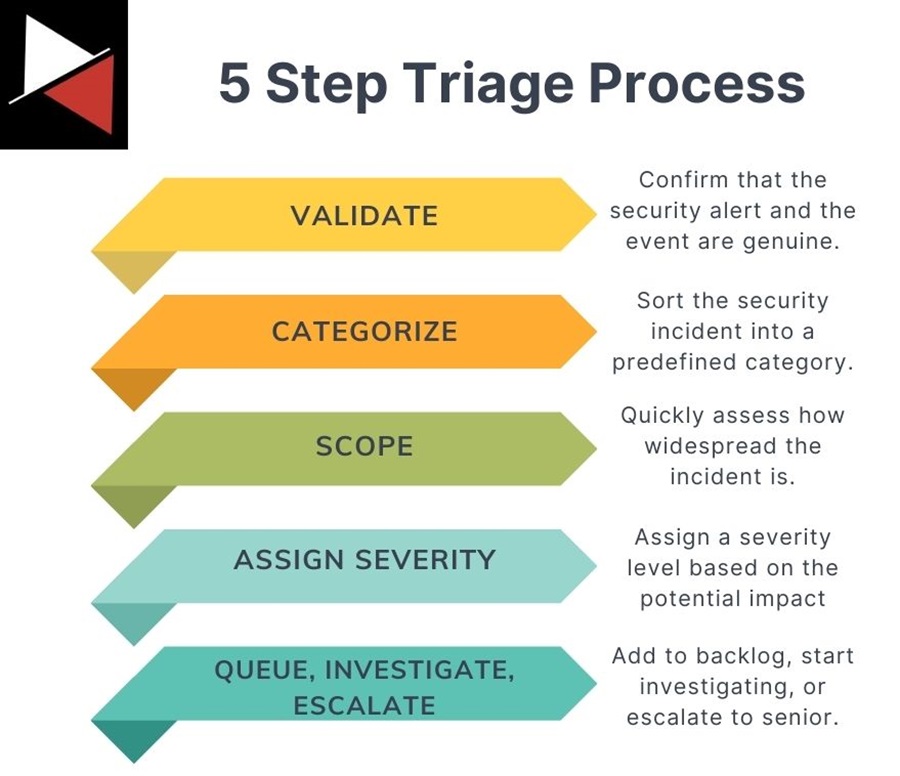
Triaging involves several steps:
- Validation: Confirm that the security alert and the event are genuine incidents, not false positives triggered by testing or legitimate activity. You can do this by contacting the system owner or your internal IT team or comparing it to previous detections. Validation requires knowledge of your IT environment and what is considered normal.
- Categorization: Sort the security incident into a predefined category (e.g., malware, ransomware, suspicious activity, potentially unwanted program, hacking tool, etc.). These should be defined in your Incident Response Plan and have an associated playbook for efficient investigation.
- Scoping: To help assign a severity level to an incident, you must quickly assess the attack surface details, number of affected assets, and related indicators. This lets you determine how widespread a threat is.
- Assigning a Severity: Assign a severity level (e.g., low, medium, or high) based on the potential impact or damage an incident could cause. Many security tools will do this automatically but often lack the context of other impacted assets, your crown jewels, and internal business processes.
- Queuing, Investigating, or Escalating: Once you have performed initial triage on a security incident, you can decide whether to add it to your backlog queue, start investigating it, or escalate it to someone with more seniority and experience.
After triaging an incident and deciding it needs to be explored further, you can start the second step of the intrusion analysis process: Investigation.
Investigation
Investigation is the most important step of the intrusion analysis process. Here, you will perform root cause analysis to pinpoint exactly what happened, how it can be prevented, and what course of action to take immediately to limit potential damage.
There are many methods and techniques for investigating a security incident. The most effective process I have found is using the Diamond Model, MITRE ATT&CK framework, and Cyber Kill Chain to gather data, tag data, and paint a picture of what happened.
Here are the steps involved.
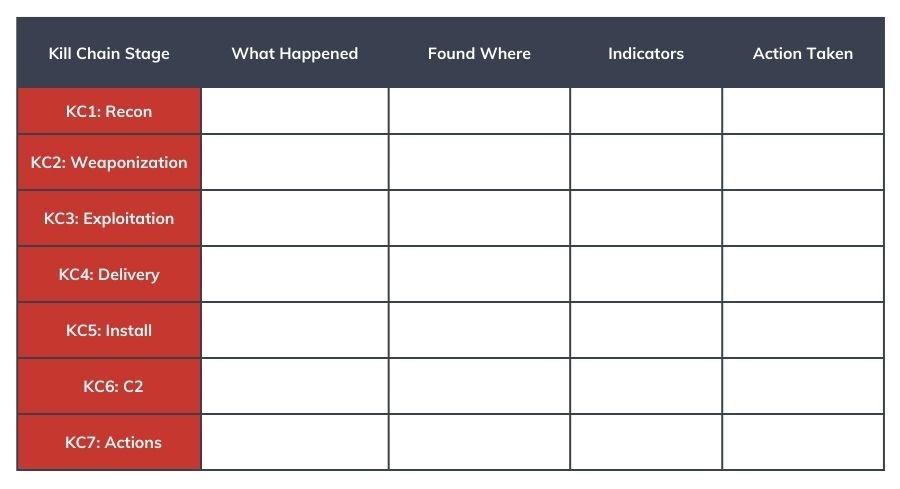
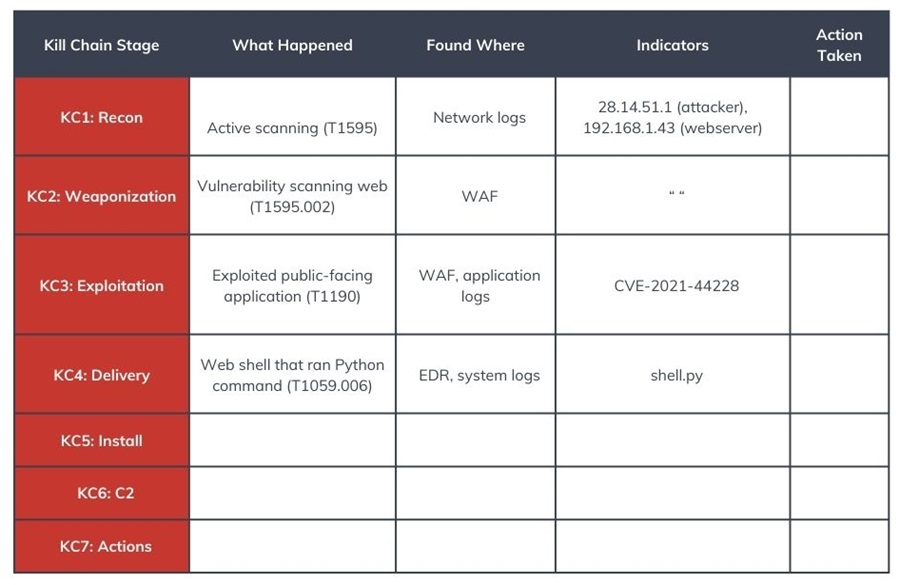
Step 1: Create a Blank Cyber Kill Chain
First, create a table that includes each stage of the Cyber Kill Chain, what you found, where you found it, indicators (IOCs), and action taken.
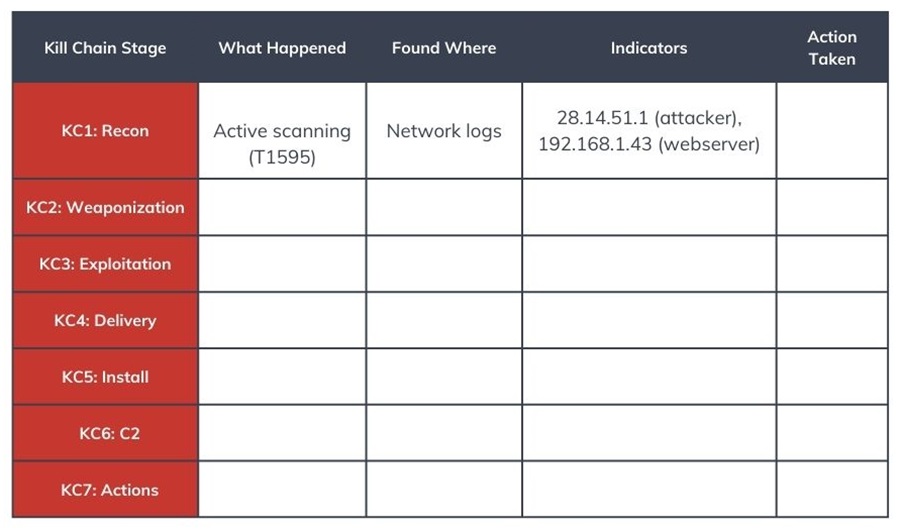
Step 2: Identify Where the Security Incident Was Detected
Next, identify at what stage the incident was detected on the Cyber Kill Chain and use the Diamond Model and MITRE ATT&CK framework to fill in the details.
For example, start with the Diamond Model and identify the Infrastructure used to perform the attack, the Victim impacted, and the Capability (TTP) performed. The Infrastructure could be the attacker’s IP address, the Victim your web server’s IP address, and the TTP used network scanning (T1595). Make sure to map the TTP to the MITRE ATT&CK framework.
Step 3: Work Down the Cyber Kill Chain
Once you have your starting point, work your way down the Cyber Kill Chain and fill out anything you find in your log sources. This will determine an attacker’s success and the impact on your organization. Aim to complete each kill chain phase with as much detail as possible.
Step 4: Go Back Up the Cyber Kill Chain
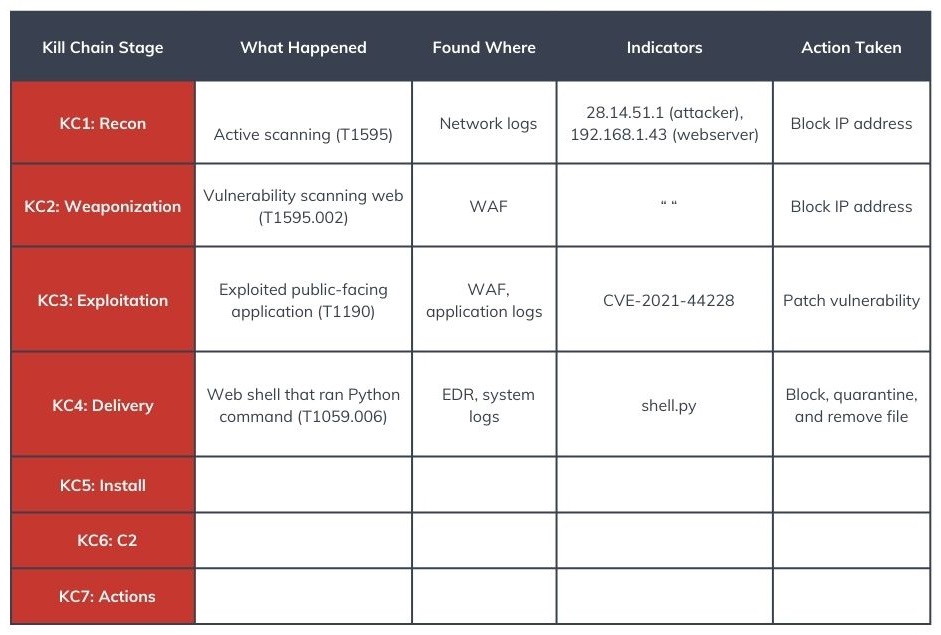
Once you reach the end of the kill chain and determine that the attack was stopped at a certain stage, you can begin working your way back up the kill chain. Ideally, you want to work your way all the way back to Stage 1. However, this will depend on your environment’s visibility, log sources, and data retention.
As you work your way down the Cyber Kill Chain, you may need to perform immediate response actions to contain a threat, such as quarantining files or machines, resetting user credentials, or cutting off network access.
Step 5: Expand the Scope of Your Investigation
After investigating one machine and completing the kill chain, you can expand the scope of your investigation to other machines within your environment. You want to determine if any other assets have been affected by this incident and if you need to perform any other response actions.
Use the indicators you gathered from your initial investigation as data points to pivot. For instance, search for the malicious IP address in your network logs to see if any other machines have visited it or run a threat-hunting query in your EDR tool to see if a malicious file has been executed on any other endpoint.
Expanding your investigation will allow you to add more infrastructure, victims, and TTPs to your original diagram. It may even kick off new investigations.
After completing the investigation step, you can take action to respond to the incident.
Response
The response step is where you take action against a threat. After a thorough investigation, you should know what the adversary did and how they did it. Now, it’s time to choose how you want to respond.
Typically, this will follow three stages:
- Containment: Strategies to limit the impact of the intrusion.
- Eradication: Methods to remove the threat from the affected systems.
- Recovery: Steps to restore and verify the integrity of affected systems.
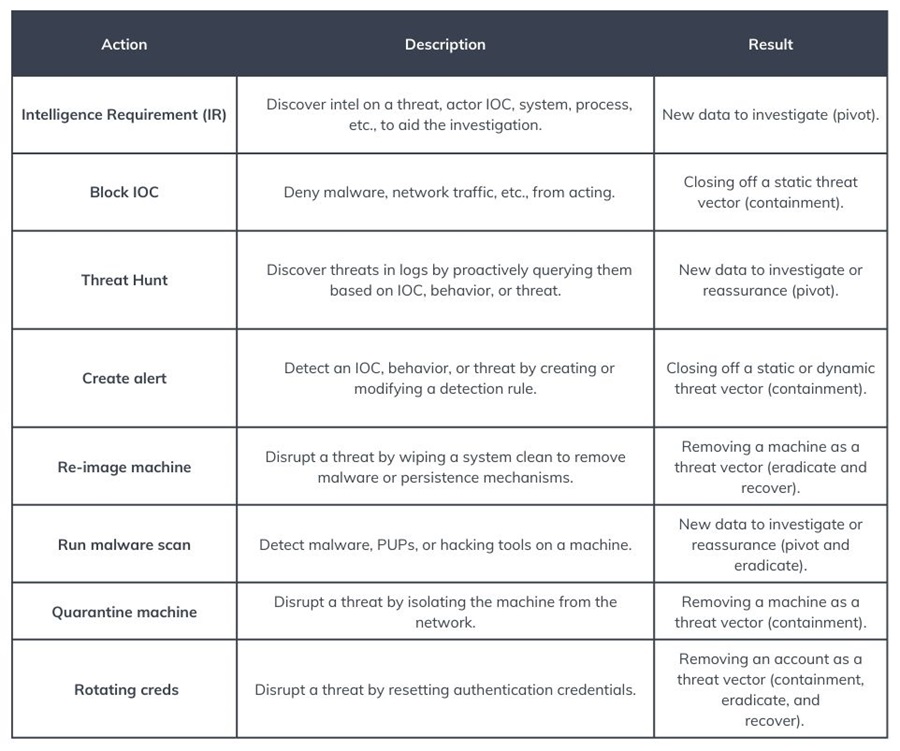
Depending on an attack’s success, you may need to perform one or all of these stages on anything from a single workstation to an entire Windows Active Directory domain. Each stage has actions that you can use to defend against a cyber attack. These map to the Courses of Action matrix (CoA) and are as follows:
Discover
You are uncovering a threat actor’s past activity in the logs. This includes other threats to your environment that came from the single incident you are investigating. You will “pivot” between data points to uncover malicious activity.
Detect
The intrusion analysis process starts by identifying an attacker’s current activity using detection tools such as anti-virus, EDR, and IDS.
Deny
Block an adversary’s activities using firewall rules, email filtering, privilege restrictions, etc. This is one of the first actions defenders take to contain a threat.
Disrupt
It is interrupting a threat actor’s activities or flow of information to cause them to fail. This is a containment strategy to prevent a threat from spreading and could involve interrupting spidering activity, quarantining files, exploit protections like DEP or ASLR, application sandboxing, quarantining a machine, and more.
Degrade
They are reducing the effectiveness of an adversary’s activities. These actions slow down potential malicious actions and give the defenders a chance to respond (e.g., rate limiting, attachment stripping, etc.). Again, containing a threat would fall under this category (e.g., locking out a machine from the internal corporate network).
Deceive
They are providing the adversary with misinformation intended to mislead their actions, such as a proxy, fake email address, or honeypot. Typically, this is not used for incident response.
Destroy
Damaging an attacker’s infrastructure so it is no longer operational (e.g., “hacking back”). This is usually not legal for most organizations and can cause many problems. Again, this is typically not used for incident response.
Here are examples of each strategy and course of action that a typical security operations team can use.
Choosing which response action to take usually requires knowledge of key business processes and choosing whichever action will cause the least harm to the business. For instance, you may want to quarantine the Active Directory Domain Controller, but doing so would significantly impact business operations.
Once you decide on a course of action, remember to add it to your investigation diagram to record what actions you took and why. This is used during the post-incident step to find areas for improvement.
Post-Incident Activities
After the dust has settled and everything is back to where it was before the incident, you can perform post-incident activities to review how things went, areas to improve, and changes that will make the process more efficient in the future.
Post-incident activities generally include three main components.
- Debrief: A meeting to summarize the events that occurred during the incident, discuss the response actions taken, and allow those involved to provide feedback about how well the incident was handled.
- Lessons Learned document: A formal document that describes what was learned from the cyber incident. This includes things the team did well, things that need improving, and actions to improve the incident response process.
- Action Items: A document detailing the actions that individuals, teams, or the company must complete to improve the incident response process.
Depending on the severity of the incident, other post-incident activities, such as PR statements, legal actions, etc., may also be necessary.
Let’s explore tools and technologies to help you with these four steps.
Tools and Technologies for Intrusion Analysis
Intrusion analysis is always limited by your visibility into your environment and your capabilities to respond to threats. Many large organizations struggle to comprehensively cover their IT estate, while smaller organizations (with a smaller budget) typically lack the automation capabilities required to respond to threats rapidly.
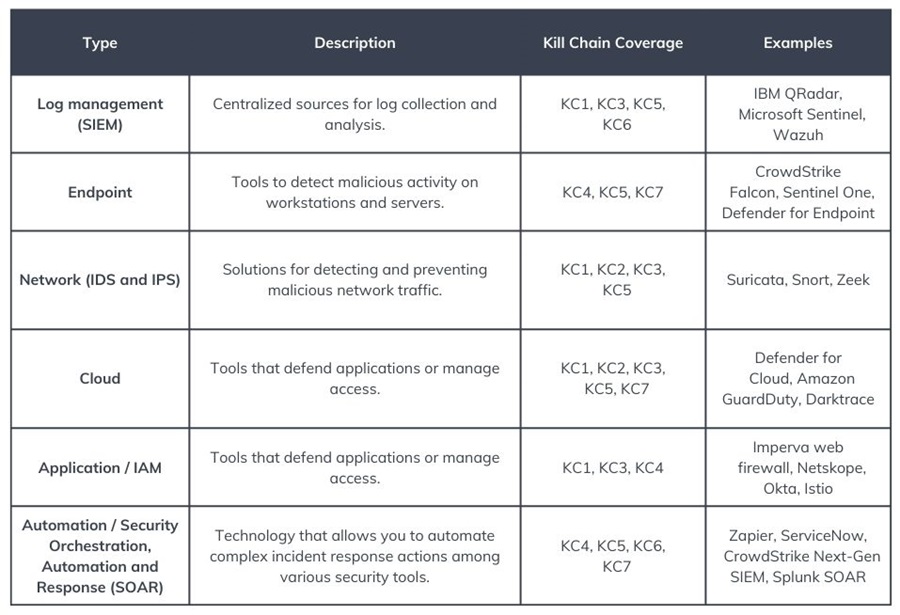
Here are some essential tools for an efficient intrusion analysis process and the kill chain stages they cover.
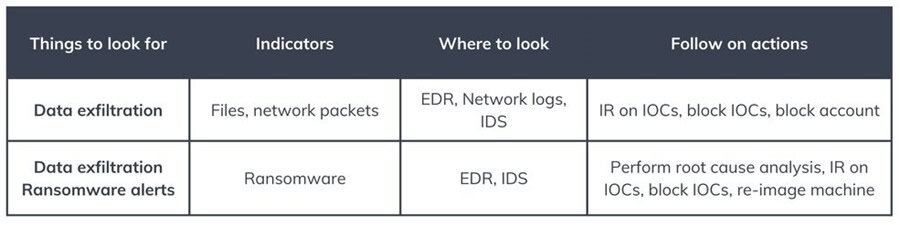
Cheat Sheet: Things to Look for at Each Kill Chain Stage
Intrusion analysis is all about knowing what to look for and where. A great way to streamline this process is to create a Collection Management Framework (CMF) that outlines your data sources and the questions they can answer.
It is also important to know what to look for at each stage of the Cyber Kill Chain. The cheat sheets below detail some things you can expect to find at each stage, where you can look, and possible follow-up actions to take. This will help you get started performing intrusion analysis in your environment.
In these examples, you have an EDR (Endpoint Detection and Response) tool, network/ application/system/email logs gathered in a SIEM, an IAM (Identity and Access Management) solution, a web firewall (WAF), an IDS (Intrusion Detection System), and code review tool like Snyk.
Additionally, you have a cyber threat intelligence team that can perform Intelligence Requirements (IRs) to gather more information for you. In the real world, you may have to do this yourself.
KC1: Reconnaissance

KC2: Weaponization
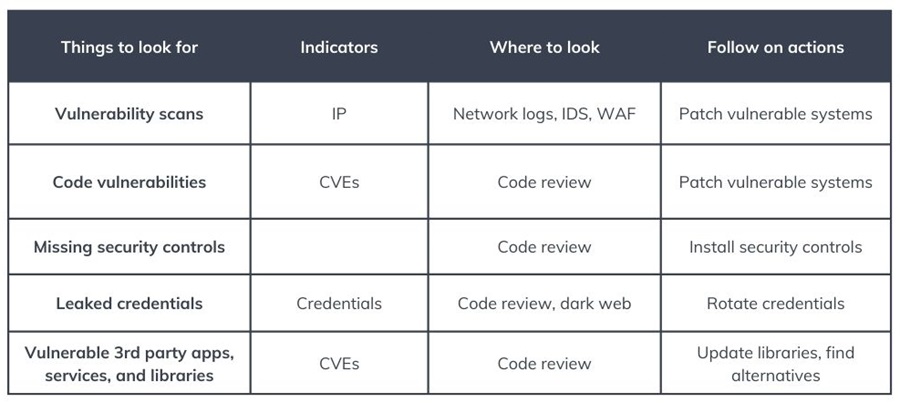
KC3: Delivery
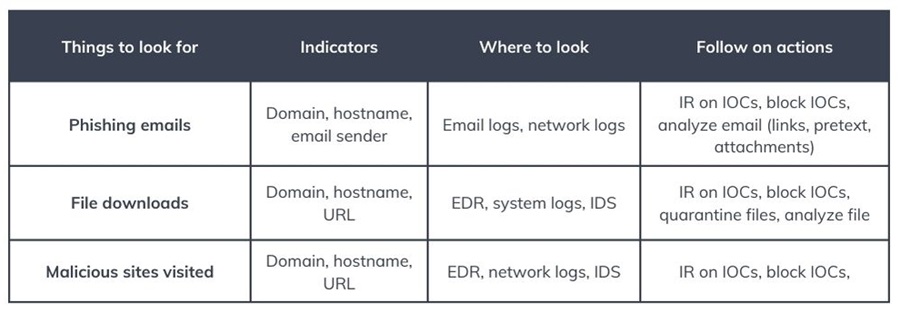
KC4: Exploitation
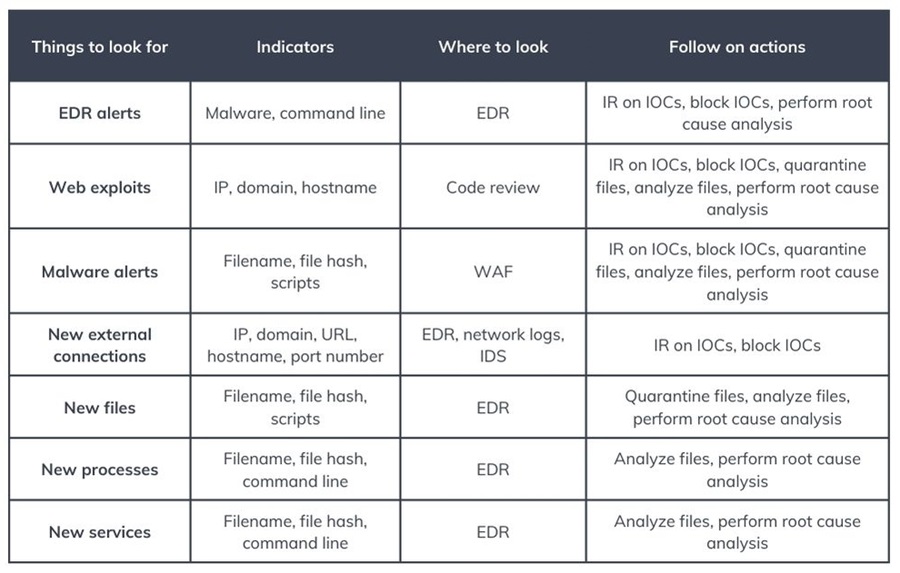
KC5: Installation
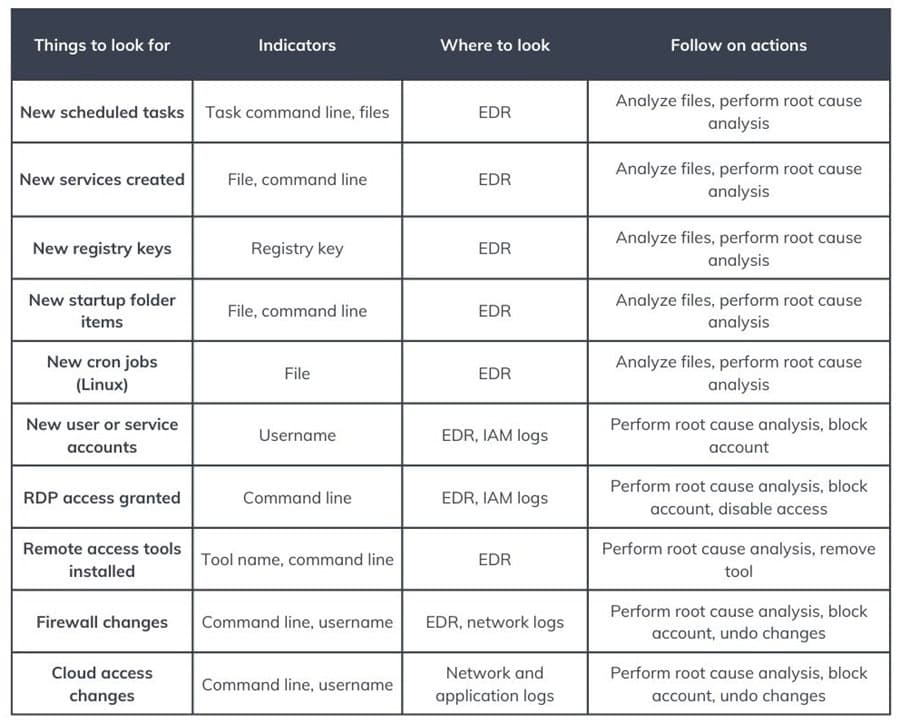
KC6: Command & Control (C2)
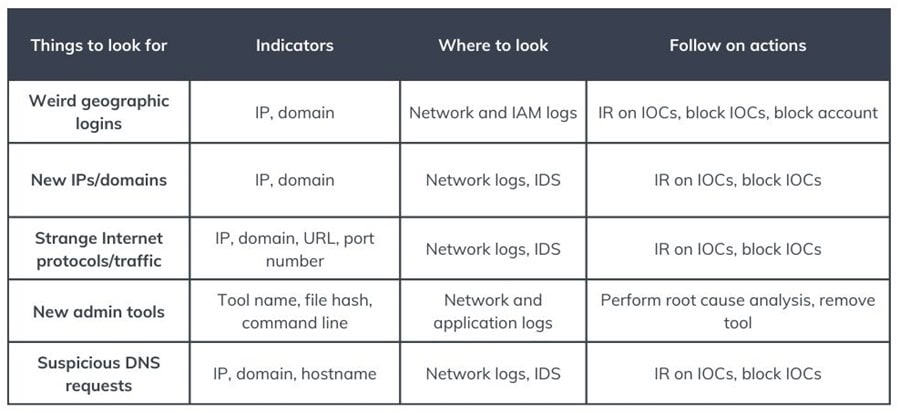
KC7: Actions on Objective
Conclusion
Intrusion analysis is about detecting, triaging, investigating, and responding to cyber security incidents. It requires tools and technologies, a structured methodology, and an analyst’s intuition to determine what happened and how best to respond.
This guide showcased how to perform intrusion analysis, the four-step process to effectively resolve cyber incidents, and the tools and technologies to help you along the way. It also included cheat sheets detailing indicators to look for at each stage of the Cyber Kill Chain so you can start improving your intrusion analysis skills today!
Use this guide as a model to ensure you follow a structured approach to resolving cyber attacks your organization faces. Just remember to complete the kill chain!
Frequently Asked Questions
What Is an Intrusion in Cyber Security?
In cyber security, an intrusion is an event or series of events that leads to an adversary gaining unauthorized access to information, systems, or networks. It can result in the confidentiality, integrity, or availability of these resources becoming compromised. Typically, intrusions are performed by threat actors for financial gain (e.g., ransomware) or political advantages (e.g., nation-states).
How Do You Identify an Intrusion?
An intrusion is usually identified by monitoring applications, networks, or system logs using detection rules. If malicious or unauthorized activity is detected, these rules trigger an alert that prompts a cyber security analyst to investigate and perform intrusion analysis. These detection rules can be based on IOCs, known malicious behavior, or thresholds.
What Is the Intrusion Analysis Process?
The intrusion analysis process is a structured methodology used to investigate a cyber incident thoroughly. It consists of four main steps:
- Detection and Triage: A detection raises an incident, which is then assessed by an analyst who validates, categorizes, scopes, and assigns a severity level.
- Investigation: An analyst performs root cause analysis on an incident to determine what happened and why it happened, using cyber security frameworks like the Diamond Model, Cyber Kill Chain, and MITRE ATT&CK framework.
- Response: Actions are performed to contain, eradicate, and recover from the incident based on the courses of action matrix.
- Post-Incident Activities: Actions performed after a cyber incident has been resolved, such as a debrief, a document including lessons learned, and action items to improve the intrusion analysis process and incident response plan.
What Causes an Intrusion?
An intrusion can be caused by various factors that allow an adversary to gain access to an organization’s systems, network, or data. Common initial access methods include weak or missing security controls, unpatched software vulnerabilities, social engineering attacks targeting employees (e.g., phishing emails), third-party data breaches, and supply chain attacks.




