Do you know what defensive capabilities your organization has? Do you know what team is doing what to combat threats? Do you have a way of coordinating your defensive efforts? Let me introduce you to the Courses of Action (CoA) matrix.
This key strategic planning tool will allow you to assess your defensive capabilities, provide security teams with situational awareness, and enable you to coordinate defensive efforts. It provides a structured framework to help you organize your tactical and procedural responses to cyber threats.
In this article, you will see how to use the CoA matrix in the real world by mapping your defensive actions against an adversary’s actions using the Cyber Kill Chain and MITRE ATT&CK. This will enable you to assess how resilient your organization is against a cyber attack, help you answer intelligence requirements, and drive critical thinking about defensive capabilities.
Let’s get started!
What is the Courses of Action Matrix?
The Courses of Action (CoA) matrix is a strategic planning tool to identify, evaluate, and prioritize defensive actions against potential threats. It provides a structured framework that security teams can use to orchestrate tactical and procedural responses based on their defensive capabilities.
The CoA matrix is based on the US Department of Defense’s (DoD) defensive capabilities doctrine. These are outlined in Joint Publication 3-13, Information Operations (13 February 2006), which details the actions available to protect against an adversary in the cyber domain.
The matrix outlines seven courses of action that can be used to defend against an attack. These include:
- Discover: Uncover a threat actor’s past activity in the logs.
- Detect: Identify an attacker’s current activity using detection tools, such as anti-virus, EDR, and IDS.
- Deny: Block an adversary’s activities using firewall rules, email filtering, privilege restrictions, etc.
- Disrupt: Interrupt a threat actor’s activities or flow of information to cause them to fail. This could be interrupting spidering activity, quarantining files, exploit protections like DEP or ASLR, application sandboxing, and more.
- Degrade: Reducing the effectiveness of an adversary’s activities. These actions slow down potential malicious actions and give the defenders a chance to respond (e.g., rate limiting, attachment stripping, etc.).
- Deceive: Providing misinformation to the adversary intended to mislead their actions, such as a proxy, fake email address, or honeypot.
- Destroy: Damaging an attacker’s infrastructure so it is no longer operational (e.g., “hacking back”). This is usually not legal for most organizations and can cause many problems.
Aptly named the 7 D’s of action, you can split these courses of action into passive and active actions. Passive actions do not have any effect on any of the other actions. Meanwhile, active actions are used to actively mitigate threats and may inhibit other actions.
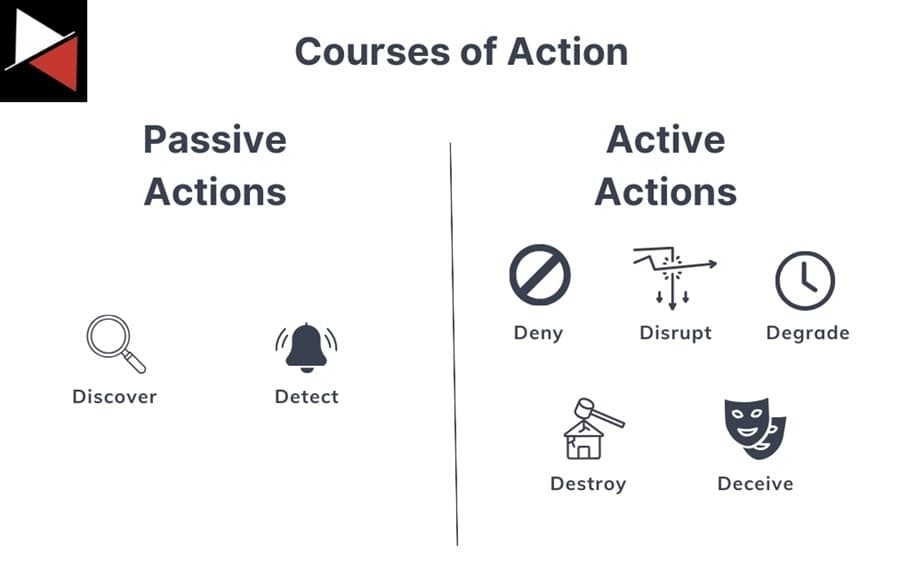
As a cyber threat intelligence (CTI) analyst you will be focused on passive actions, such as Discover and Detect.
Discover
Actions under Discover rely on searching through captured data to answer a question. For instance, “Are there any signs we have been compromised by threat actor XYZ in the past 30 days based on campaign ABC?” This question is an intelligence requirement. To answer it, you could find all Indicators of Compromise (IOCs) associated with campaign ABC and search for them in your log files, following the indicator lifecycle.
If you find an indicator, then you may have been compromised. If not, you can form an assessment based on your confidence level. You may say, “I am relatively certain we are not compromised because we searched for all IOCs and TTPs associated with that campaign and found none.” You utilized Discover to take action and answer an intelligence requirement (a priority intelligence requirement, to be exact).
Detect
Discover looks at what has already happened, focusing on the past, Detect focuses on what is currently happening by identifying malicious activity as it occurs. It is the future complement to Discover and nicely pairs with other courses like Deny, Disrupt, and Degrade.
An example would be setting a detection rule in your Security Information and Event Management (SIEM) solution to trigger whenever a certain action was seen on an endpoint machine or a specific network packet traveled across the network. When this behavior or indicator was detected, you would receive an alert in your SIEM’s management console that you could then investigate.
Discover and Detect are courses of action that do not impact other potential actions (they are passive). You can look through past data or get an alert about what is happening without interfering with another defender’s actions. This is not the case for active actions that often prevent other actions. You should always have passive actions as part of your defensive strategy.
Applying the Courses of Action Matrix
The CoA matrix is just a way of categorizing defensive capabilities. To use it in the real world, you need to map these defensive capabilities to a framework that describes how an adversary performs an attack. This mapping allows you to match your defensive capabilities against an adversary’s actions and assess your organization’s coverage against a cyber attack.
There are two main frameworks that security teams will map their CoA matrix against. These are Lockheed Martin’s Cyber Kill Chain and MITRE’s ATT&CK knowledge base. Let’s look at both.
Mapping Actions Against the Cyber Kill Chain
The Cyber Kill Chain was one of the first frameworks created to describe a cyber attack. It contains seven stages that detail each step an attacker usually performs when attacking a target. Each step builds on the previous one, eventually concluding with an attacker accomplishing their goal (Actions on Objectives).
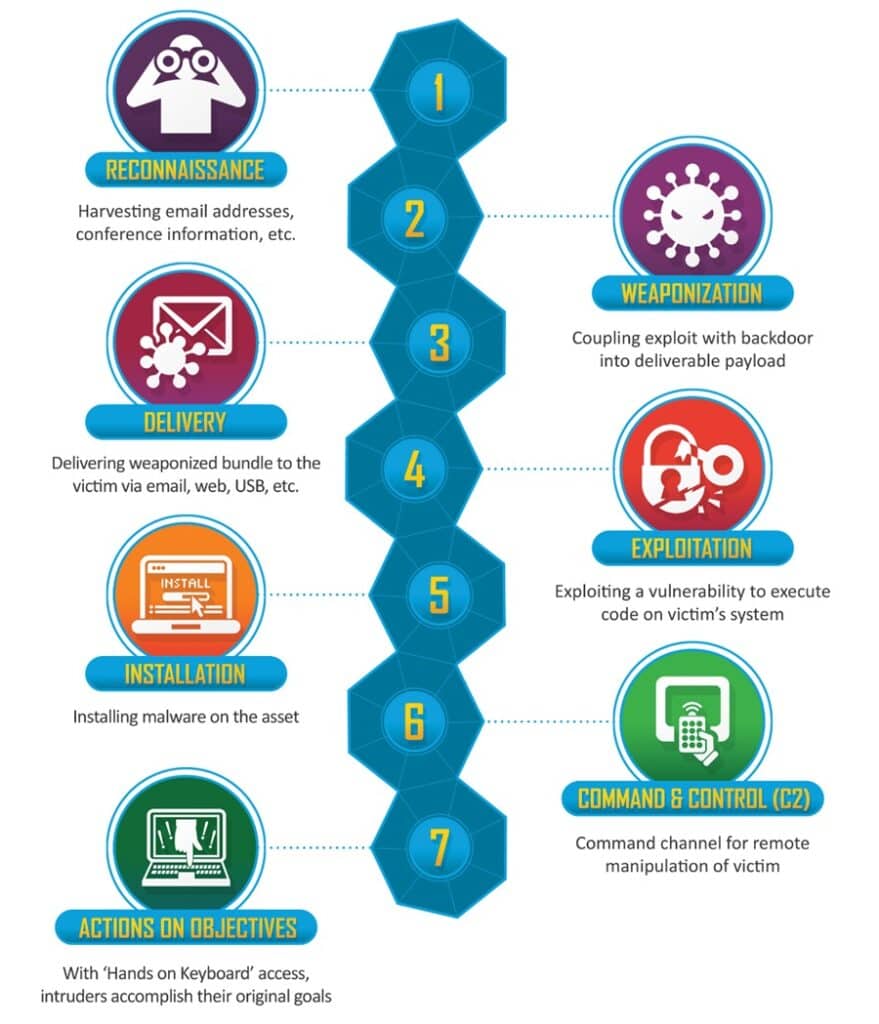
Security teams will map their CoA matrix against the Cyber Kill Chain to correlate their defensive efforts against a threat actor’s attack path. The chart lets everyone in the organization know what security actions are taking place, what each team is working on to defend against attacks, and what stage of an attack is being defended against.
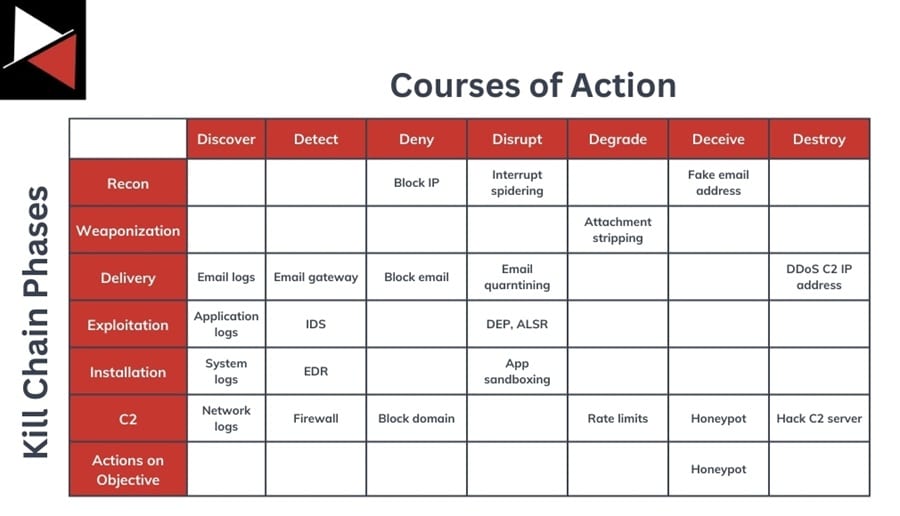
You may have a general chart outlining all ongoing actions and more detailed charts that teams use to track a specific campaign or threat actor.
- Once your organization acquires a new CoA capability, add it to the main chart.
- If a new IP address is found related to a campaign you are tracking, add it to its chart (e.g., block IP 10.0.0.1 as a Deny action).
Keeping track of actions being taken lets you identify what security tools provide value to your team, what stage of an attack you are defending against, and what capabilities you are missing. These are all useful metrics to report when it comes time to prioritize the investments your organization is making in security.
Every organization should have a chart similar to this. It is a great way to provide situational awareness of your defenders’ actions and allows defenders to answer CoA questions. For instance, if a CoA is to sink hole a malicious IP address (Disrupt), there is no point performing a Detect or Discover action against it.
Mapping Actions Against MITRE ATT&CK
Another framework you can map your defensive actions against is MITRE’s ATT&CK matrix. This is a knowledge base of tactics, techniques, and procedures (TTPs) that threat actors use to perform cyber attacks. It goes into more detail than the Cyber Kill Chain and even includes specific mitigations or security controls to combat attack techniques.

The ATT&CK matrix comprises 14 high-level tactics an adversary may perform during a cyber attack. Each tactic consists of various techniques that an attacker can use to achieve a given tactic and specific procedures they can use to perform a technique. Read MITRE ATT&CK Framework: The Holy Bible of Threat Intelligence for more details.
Most security teams will map their CoA matrix to the 14 ATT&CK tactics. If you want to provide more granular details, you can map actions to specific ATT&CK techniques, such as an email gateway to Phishing (T1566). This allows you to track what techniques an action defends against.
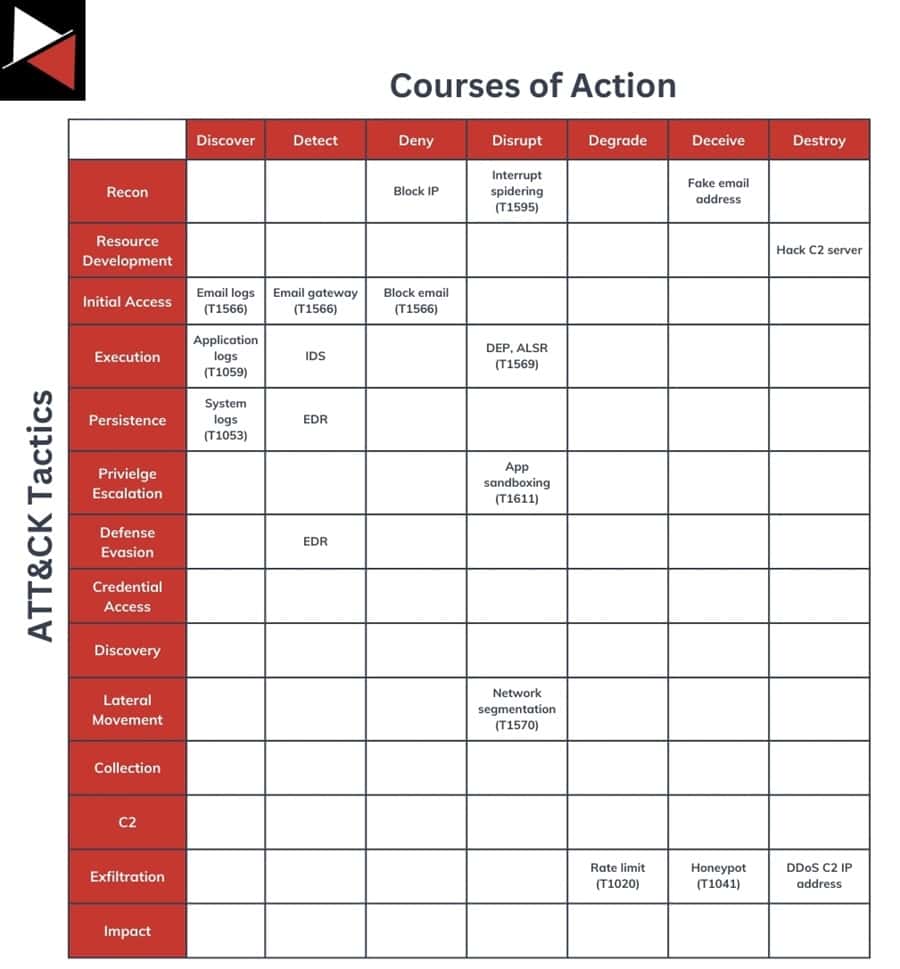
The ATT&CK matrix is a great framework for security teams to use and has been widely adopted by the security community as the defacto language for describing how an attack was performed. However, it is exhaustive and can often confuse non-technical stakeholders so you may find more benefit using a simpler model like the Cyber Kill Chain when reporting to executives.
I recommend tagging all your data using the ATT&CK matrix and having this as a policy throughout your security team. This lets you quickly reference data, share a common language, and characterize your defensive CoAs against an attacker’s actions without the overhead of looking up actions in the ATT&CK matrix every time. You can also use the ATT&CK Navigator to get a heatmap of TTPs you see or cover.
Why Is the Courses of Action Matrix Useful?
So you know what the CoA matrix is and how security teams use it, but why bother? There is an overhead in tracking all your defensive actions. Is it worth it?
The short answer is yes. It can be used to prioritize security investments by identifying what security tools are providing value, what stage of an attack you are defending against, and what capabilities you are missing, but there is more. Here are the key factors that make the CoA matrix an essential planning tool in your arsenal.
Key Advantages of the CoA Matrix
- Coordination and collaboration: Security teams can coordinate their defensive actions to minimize redundant efforts and maximize the efficiency of security tools.
- Strategic planning: Key stakeholders can quickly analyze what actions are being taken to combat what threats. They can also track and prioritize security investments based on the benefits they provide or missing capabilities that are needed.
- Tactical decision-making: Operational teams can track and assess the organization’s defensive capabilities based on TTPs and prioritize security efforts. They can also see the options available to combat new and emerging threats for efficient decision-making.
- Evidence-based resiliency: The matrix allows an organization to assess its defensive capabilities accurately using collated evidence, allowing them to understand how resilient they are against a cyber attack.
- Empower critical thinking: Requires defenders to think critically about actions they can take to combat threats, assess new actions available, and maximize value from their existing security tools.
Challenges With the CoA Matrix
Despite the CoA matrix being an invaluable tool for security teams, you will likely find several challenges when working with it. Let’s look at the most common ones.
Communication Between Security Teams
For the CoA matrix to be useful, you need strong communication channels between your organization’s security, infrastructure, and IT teams:
- Everyone needs to report what actions they are taking.
- Everyone needs to be aware of what actions other teams are taking.
- Everyone needs to be invested in collaborating with other teams to enhance defensive capabilities and not perform redundancy work.
A failure to communicate and collaborate will negate the whole point of the matrix.
Blocking Actions
The active actions on the CoA matrix will block other actions. For instance, a Deny action will prevent you from running a Discover or Detect action. This might mean you lose out on intelligence; you don’t see the malware execute, so you cannot pick up the other IOCs or TTPs it exhibits.
You need to carefully consider all the courses of action available to you based on your current defensive capabilities, what actions will drive the most value, and weigh that against the risk certain actions have. It may be too risky to let malware detonate in your environment. That’s okay. Just consider the losses.
Balancing Operational Security and Intelligence
The CoA matrix will put your security operations and intelligence teams in conflict. The intelligence team will want all the intel and not have other teams performing any active actions blocking this intel generation. The operations team will want to make their life easy by running as many Deny, Disrupt, or Degrade actions as possible – stopping the threat immediately.
You must balance intelligence requirements that gain a deeper insight into adversary activity against operational demands that lower risk. This requires comprehensively assessing all actions available across various security teams and accepting a certain level of risk for a greater payoff in the long run.
Navigating Legal and Compliance Frameworks
As you move to the right of the CoA matrix, the legality of some actions can be questionable, particularly Destroy actions. Offensive actions that reduce the ability of an adversary to operate are not legal for most entities. This “hacking back” activity can cause substantial trouble if not done legally and has far-reaching consequences that you may not be aware of, such as disrupting law enforcement operations.
Additionally, you may need to implement certain actions based on compliance requirements, such as security controls that can inhibit other actions. This goes back to the challenge of balancing operational security and intelligence generation.
As a rule of thumb, stay away from Destroy actions. They will likely only cause you more trouble and put a bigger target on your back.
Keeping Up With New Capabilities
Many security teams fail to perform the ongoing maintenance required to derive full value from the CoA matrix. As your security team gains new capabilities, these must be added to your CoA matrix and shared with other teams. This ongoing maintenance is required to make informed decisions across teams when assessing which actions to take. The CoA matrix is not a set-and-forget tool.
I recommend reviewing your CoA matrix monthly to accurately assess your capabilities and available actions. New capabilities can come from investing in new tools or updates, discovering tool features, or developing team members’ skills.
Conclusion
The Courses of Action (CoA) matrix is a tool every security team should use. It allows you to assess your defensive capabilities, coordinate efforts across your security teams, and drive critical thinking. You must map out your defensive actions to know how resilient you are from attacks.
Every security team should use a CoA matrix to track their capabilities. From a threat intelligence perspective, it will provide your team with situational awareness and help answer intelligence requirements. I recommend implementing a basic one right now and making it more granular as you dive deeper into specific TTPs you can defend against.
Frequently Asked Questions
When is the Courses of Action Matrix Used?
The CoA matrix is used whenever an organization needs to assess its preparedness, defensive capabilities, or overall security posture in relation to a cyber attack. This is common when coordinating defensive efforts among security teams, incident response planning, and risk management. That said, cyber threat intelligence teams often use the CoA matrix to help an organization respond to emerging threats and guide strategic decision-making.
What are the Actions in the CoA Matrix?
The CoA matrix consists of seven actions. Two passive actions that do not impact other actions (Discover and Detect) and five active actions may inhibit you from performing other actions (Deny, Disrupt, Degrade, Deceive, and Destroy). Choosing which action to take will depend on your security role, available defensive capabilities, and intended outcome.
Who Invented the Courses of Action Matrix?
The CoA matrix is based on the US Department of Defense’s (DoD) defensive capabilities doctrine that outlines the actions available to protect against an adversary in the cyber domain. This was originally published in Joint Publication 3-13, Information Operations (13 February 2006). The matrix has been adopted by many security teams outside of the government as a way to coordinate, assess, and track their defensive capabilities.




