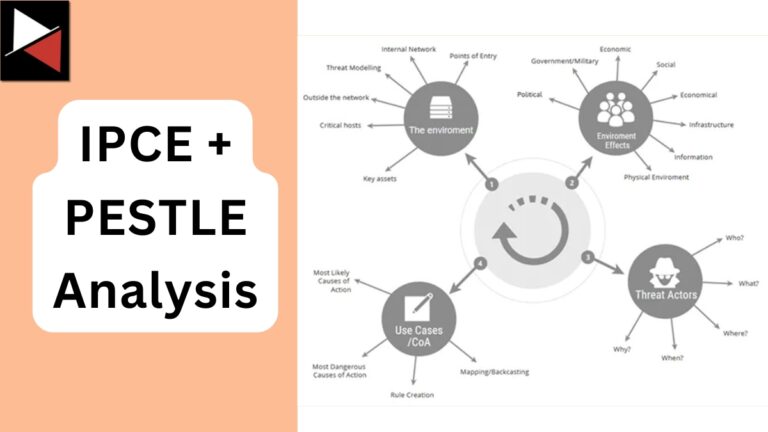
Threat modeling is a key component of any successful cyber security program. It allows you to identify and assess your organization’s threats, what risks to prioritize, and mitigation strategies that will significantly improve your security posture.
This guide will teach you what threat modeling is, why it is important, and five methodologies and techniques you can use to elevate your threat modeling skills. It will also walk you through how to start with threat modeling by demonstrating the methods described in a case study. The article wraps up with practical recommendations for applying threat modeling in the real world.
Let’s get started exploring this cornerstone of effective cyber threat intelligence and cyber security programs!
What is Threat Modeling?
Threat modeling systematically identifies, evaluates, and prioritizes the risks that threaten your systems, applications, or overall security. You methodologically analyze your assets and determine what vulnerabilities may exist, what attacks they are likely to face, and the potential impact if an asset is compromised. This allows you to mitigate or manage security threats effectively.
As a cyber threat intelligence analyst, threat models will be the primary way of generating intelligence requirements for your organization. You will use them to structure the relationships between threats (threat actors, behaviors, tools, exploits, vulnerabilities, etc.) and what your organization cares about (important assets, vital business functions, mission-critical data).
What is a threat?
A threat is any potential danger or activity compromising the confidentiality, integrity, or availability of your data, computer systems, or networks. It can be an entity (malicious insider, a ransomware gang, nation-state), an attack (malware, phishing, DDoS), or even an unintentional action like exposing sensitive information. In cyber threat intelligence, you typically focus on groups, attacks, and vulnerabilities as threats to your organization.
Threat modeling allows you to create intelligence requirements by identifying gaps in knowledge and what is core to your organization’s operations.
- Knowledge Gaps: Missing key information required to make an informed decision.
- Core operations: Business processes or systems fundamental to your organization’s functioning. This could be a payment service, sensitive client information, an e-commerce website, Active Directory servers, or anything else that would significantly impact daily work if compromised.
You use these two components to identify missing intelligence that will help you protect core operations.
Various threat modeling methodologies and techniques can be used to structure your threat modeling. That said, fundamentally, threat modeling is simply answering what is important to your organization, what must be protected, and how this is likely to be attacked. You then repeat this process over an extended period of time to proactively manage risk.
Before jumping to how to perform threat modeling, let’s first understand why it’s important.
Why is Threat Modeling Important?
Threat modeling helps analysts answer three simple questions:
- What is important to my organization?
- What should I prioritize protecting?
- What risks threaten these things?
Answering these questions gives you a better understanding of what to focus on securing and how to do it. The answers to these questions will inform key decisions on your security strategy, what security investments to make, and how to improve your security posture and align it with your organization’s needs.
It is important to answer these questions even if you don’t use a formal threat modeling methodology to generate the answers. These questions guide you from the mindset of doing security for security’s sake to doing security to protect key business requirements. This shift in perspective makes your security team, technologies, and processes effective in the real world.
With this in mind, here are the key benefits threat modeling provides.
Key Benefits of Threat Modeling
- Helps generate intelligence requirements: Allows you to identify knowledge gaps that need to be filled, critical assets that need protection, and threats that need to be mitigated. This knowledge helps you generate effective intelligence requirements for your organization.
- Reduces risk: Allows you to identify and understand potential security risks threatening your systems, applications, or data, empowering you to implement mitigation strategies that reduce these risks.
- Prioritizes resource allocation: Highlights resources you need to prioritize protecting and where to invest your security resources. This ensures you optimize your security budget.
- Introduces security by design: Builds security into system designs so vulnerabilities are minimized and the likelihood of critical vulnerabilities is reduced.
- Improves situation awareness: Helps key stakeholders understand the security risks involved in a system or application so they can make informed decisions.
- Tailors your security to current threats: Threat modeling is a proactive process that adapts to new and emerging threats to keep your systems, applications, and data secure as the threat landscape evolves.
- You can match your security strategy against industry compliance requirements using a structured approach to identifying and mitigating security risks.
Threat modeling is a must-do activity for all organizations wanting to get serious about security. But how exactly do you perform threat modeling? Let’s explore!
Threat Modeling Methodologies and Techniques
You can use various methodologies and techniques to perform threat modeling. A model represents an idea, an object, or a system. The following methodologies and strategies help you build a picture of that model, including its components, importance, and associated risks or threats.
Here are five popular threat modeling methodologies you can use.
STRIDE
STRIDE is a threat modeling methodology developed by Microsoft to help developers identify and categorize threats during the design and development phases of the Software Development Life Cycle (SDLC). It is represented by six categories based on its acronym.
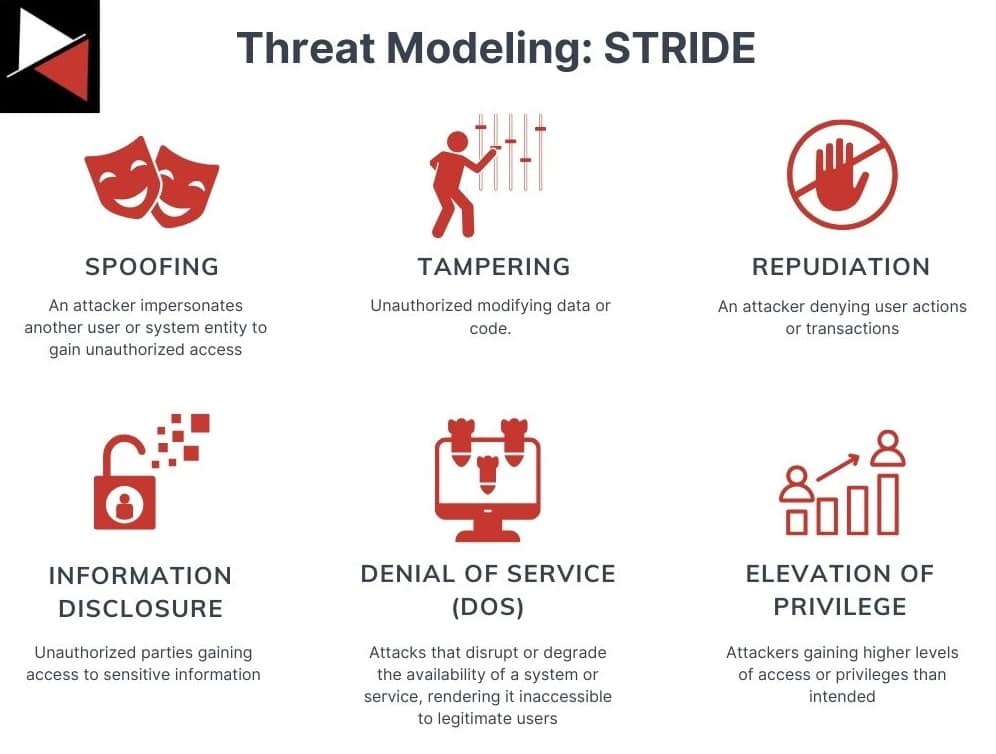
A software engineer will analyze the design of their software system using these six threat categories to identify potential vulnerabilities or missing security controls. As a security professional, you use crown jewel analysis to determine your organization’s critical assets and then apply the six categories to assess the security posture of these assets.
Use case: Assess the security of critical assets based on common system flaws.
DREAD
DREAD is a risk assessment methodology that evaluates the security of software systems or applications against five factors using a scale of 0 to 10. A 0 indicates minimal risk or impact, while a 10 indicates severe risk or impact. These five factors are based on the methodology’s acronym, as shown below.
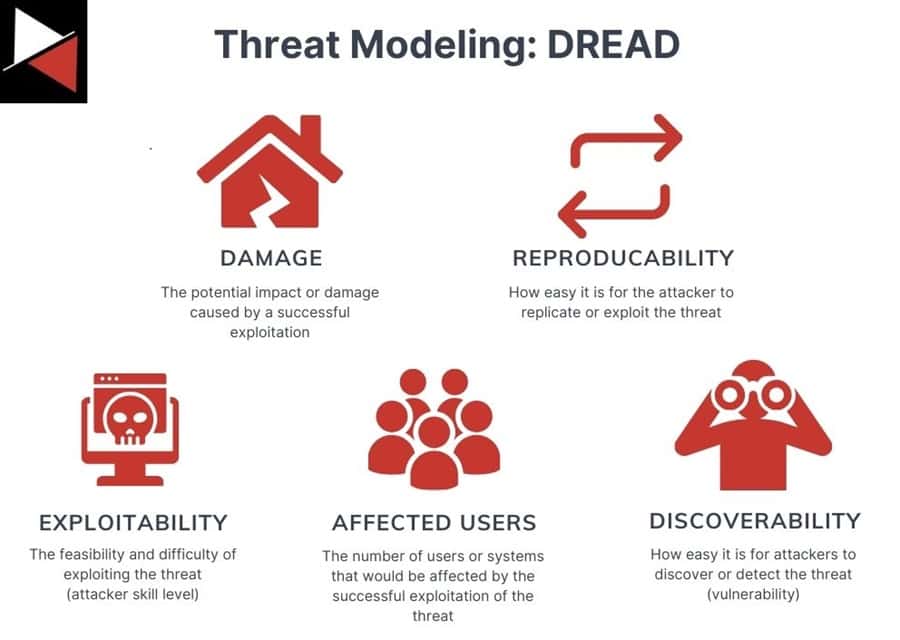
Evaluating threats using these five factors allows organizations to prioritize their mitigation efforts and allocate resources to address the most critical security risks first. You can use DREAD to assess threats against key assets within your organization. For instance, if a threat actor compromises your organization’s web server, how would it impact these five factors?
Use case: Determine the impact of an attack on critical assets and how difficult recovery would be.
PASTA
Process for Attack Simulation and Threat Analysis (PASTA) is a risk-centric approach to identifying and analyzing cyber security threats. It provides a structured framework for you to assess your security risks systematically.
The process is as follows.
- Define business objectives: Understand what business goals a system aims to fulfill so you can align your security measures with the overall mission and its priorities.
- Decompose the system into its components: Break the system into its various components (e.g., functionalities, interfaces, data flows, and dependencies).
- Identify potential threats and attack vectors: Identify potential attack vectors that an attacker could exploit within a system’s components.
- Identify weaknesses or vulnerabilities: Identify potential weaknesses and vulnerabilities within a system’s components.
- Model an attack scenario: Create a detailed attack scenario describing how an attacker could exploit attack vectors, weaknesses, or vulnerabilities to achieve their objectives.
- Evaluate the impact of identified threats: Assess the likelihood and potential impact of the identified threats on the organization’s objectives.
- Implement mitigation strategies to address risks: Develop and implement strategies to address identified security risks, such as security controls, patches or updates, awareness training, or redesigning system architecture to minimize risk exposure.
PASTA allows you to comprehensively assess your organization’s cyber threats and prioritize mitigation efforts.
Use case: Provide systematic and thorough threat modeling of your organization’s threats, vulnerabilities, and risks.
Attack Trees
Attack tree threat modeling involves visualizing the various steps an adversary would take to achieve their goals and the impact these steps would have on your organization. You start at the root goal (node) and branch into sub-goals and attack steps (leaf nodes). Here is what a typical attack tree looks like.
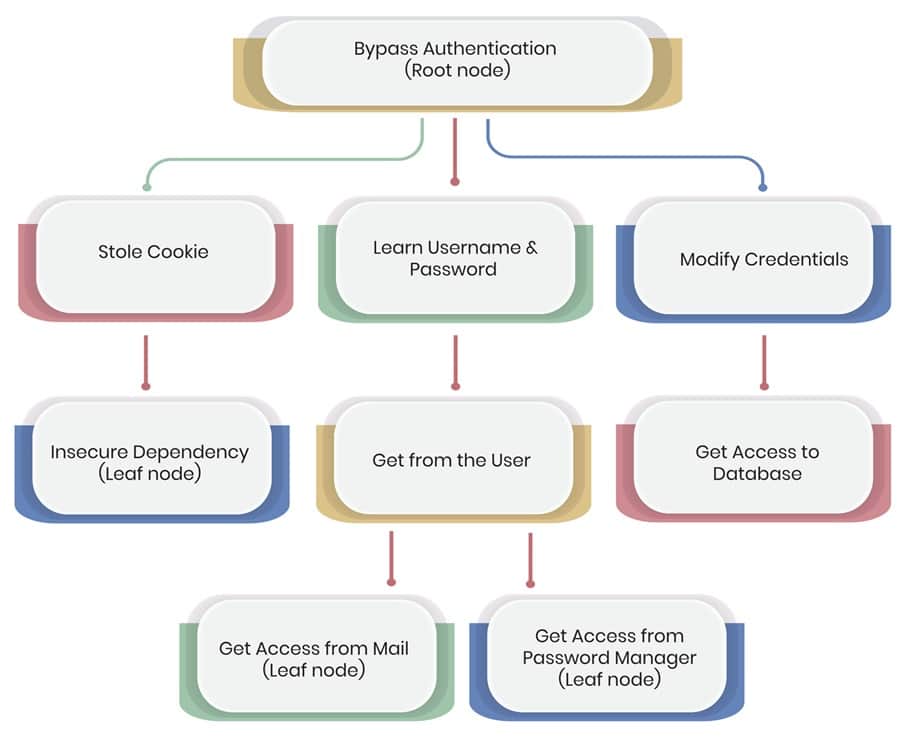
Visualizing attack scenarios is a great way to demonstrate threats to non-technical stakeholders or visual learners. It also allows you to highlight points within an attack chain where security controls can be placed to prevent or disrupt an attacker.
Use case: Create a graphical representation of your attack surface and how an attacker may reach critical assets.
VAST
Visual, Agile, and Simple Threat Modeling (VAST) is another threat modeling methodology focusing on identifying and mitigating threats during the SDLC. However, it aims to streamline the process by emphasizing simplicity, agility, and visualization, making it accessible to a wider audience.
Here is an overview of the key components of VAST.
- Create visual representations: Use visual aids (e.g., diagrams, flowcharts, and mindmaps) to represent the system architecture, potential threats, and mitigation strategies. This helps better understand complex relationships and dependencies within your systems.
- Use an agile approach: Incorporate the principles of agile software development, such as iterative development, collaboration, and flexibility, rather than conducting a single, exhaustive threat modeling session upfront. This ensures you continuously refine your threat model based on feedback, evolving requirements, and emerging threats.
- Keep it simple: Identify the most critical threats and prioritize mitigation efforts to protect them. Don’t try to catalog every vulnerability, and ensure that teams with varying levels of expertise can contribute to the threat modeling process.
- Encourage collaboration: Foster collaboration between stakeholders with diverse backgrounds, expertise, and perspectives so that all relevant concerns are addressed, and mitigation strategies are aligned with business objectives.
- Integrate with the SDLC: Integrate threat modeling at the outset of any project and continue to threat model throughout the development process to ensure security is not treated as an afterthought and systems are secure by design.
VAST is a more practical and flexible approach to threat modeling, making the process easier for a vast majority of organizations. It also makes performing continuous threat modeling significantly less resource-intensive by minimizing complexity and maximizing collaboration.
Use case: A more modern approach to threat modeling that aligns with agile software development and fast-paced environments.
That’s enough theory. Let’s look at how you would actually perform threat modeling using a real-world example.
Case Study: Threat Modeling a Pizza Delivery Service
Let’s step into the shoes of a pizza delivery service. They have a website and a mobile application where customers order pizza, which they deliver straight to the door.

After performing a crown jewel analysis, you identify four key assets the pizza company must protect to continue its business operations.
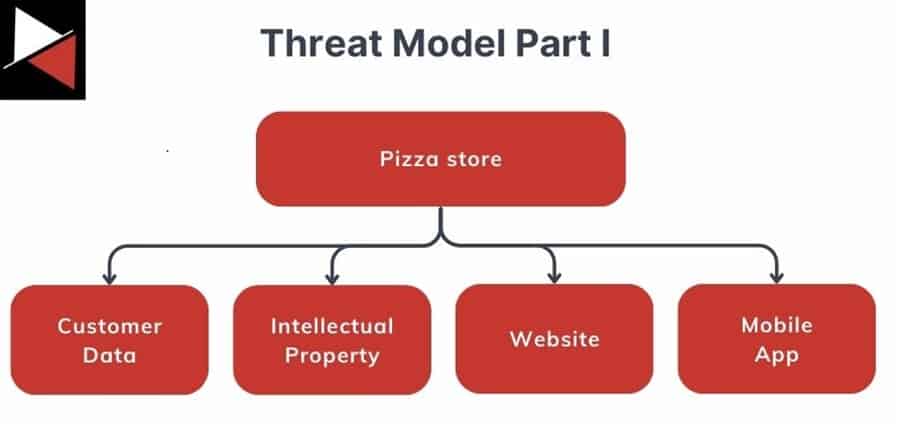
With these key assets in mind, you can now add adversaries that usually target them. For instance, script kiddies (low-skilled attackers) may target your pizza website for fun, but more sophisticated actors may try to steal your customer’s sensitive information for fraud.
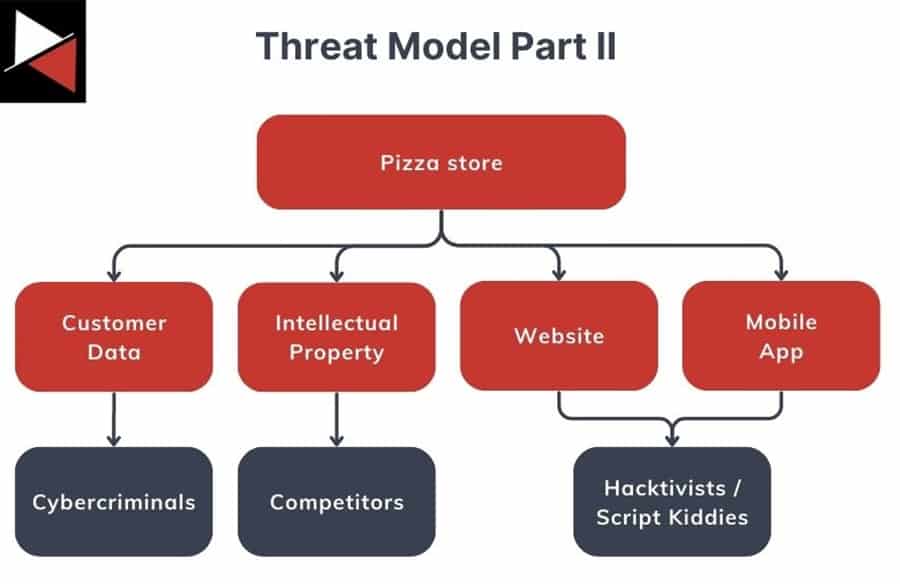
Next, you can overlay how an attacker would target these key assets – their tactics, techniques, and procedures (TTPs). You can also include what they would go after and the impact on the organization.
The DREAD methodology is a great one to model the impact of an attack on your assets.
To model how an attacker may target your assets, you can pivot off of target information or adversary intelligence:
- Target information: This is specific information an attacker would go after. Customer data can include financial information or PII, so add these two subcategories to your model.
- Adversaries: These are the tools, TTPs, or events an adversary may trigger when attacking your systems. You break events into reactive detections and proactive threat hunts and add them to your model.
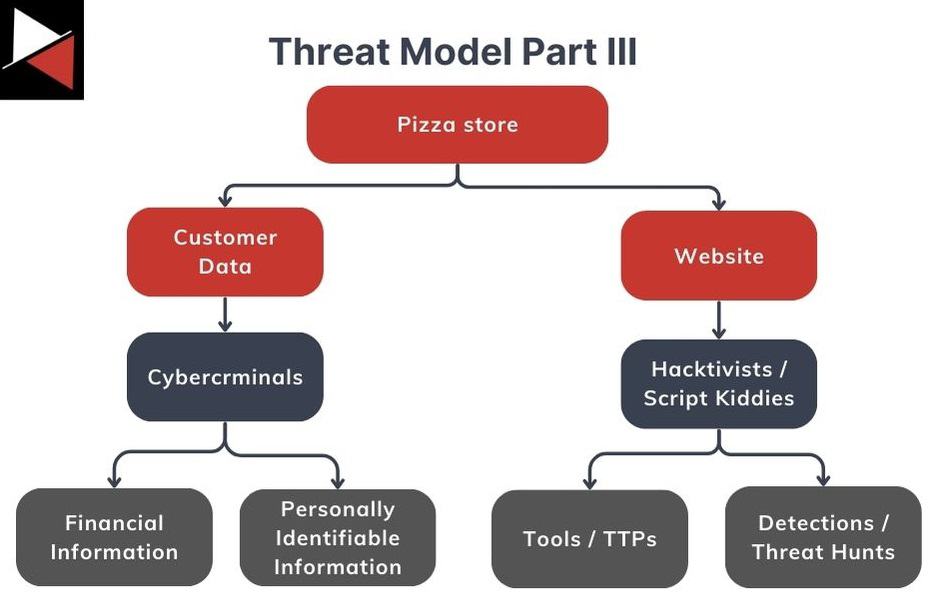
You can go as deep as you want into this layer, using attack trees to visualize the steps the attacker would take or using PASTA to assess vulnerabilities that may arise in the software you use. Start at the top, add your key assets, and then work down to granular details about subsystems, security controls, and software versions.
Once complete, your threat model can fulfill various use cases.
Threat Hunting
You can select a threat from your organization’s threat model and generate a hypothesis about the tradecraft (TTPs) you would expect to see if this threat was present. Next, you can map this hypothesis to your Collection Management Framework (CMF) to identify what is needed to test the hypothesis and execute an effective threat hunt.
Incident Response
If an incident occurs, a threat model can provide context about potential threats and attack vectors that could be targeted. This allows the incident response team to prioritize their efforts, contain outbreaks more effectively, and reduce the impact of an incident.
Security Operations
Threat modeling allows operational teams to identify and assess potential risks and vulnerabilities in their IT environment. From here, they can prioritize mitigation strategies, implement security controls, and allocate resources to defend critical assets.
Strategic Planning
A threat model helps security architects and system engineers identify potential security vulnerabilities and weaknesses in their system designs. They can then incorporate security controls and best practices into their design to ensure security is built into the system from the outset.
Practical Recommendations
Threat modeling can be difficult if you haven’t done it before. Using a structured approach and adopting one of the methodologies above can ease this burden. However, performing threat modeling in the real world can raise all sorts of unforeseen challenges. To help you out, here are some practical recommendations to keep in mind when you perform threat modeling.
- Don’t overtax yourself. Start with what your organization cares about and go from there.
- Never complete the threat model. Threat modeling should be an iterative process that evolves as threats and risks change.
- If your company is very large, build different threat models for separate business units (e.g., one for your HR department and another for software developers – they will face different threats).
- Use intelligence to drive the threat modeling process. You need to gather intelligence on who will target your key assets, how they will do this, and how to defend against them. This will evolve over time as the threat landscape changes.
- Threats are not always equally distributed. A threat for one organization may not be a high priority for another. You must tailor your threat model to match your organization’s requirements and prioritize.
Conclusion
Threat modeling is the systematic process of identifying, evaluating, and prioritizing threats against your organization. It uncovers vulnerabilities you must patch, attack methods you must mitigate, and the potential impact of compromised assets.
This guide taught you what threat modeling is, why it is important, and how to get started. It’s now time for you to apply this knowledge in the real world. Take what you have learned, be it a threat modeling methodology or a practical recommendation, and get started with threat modeling today.
Remember. Start general and then gradually break it down into TTPs and vulnerabilities, specific systems and data repositories, and mitigation strategies specific to your organization. Keep it simple, keep it continuous, and good luck!
Frequently Asked Questions
What Is Threat Modeling in SDLC?
Software architects and developers must systematically identify, assess, and mitigate potential security threats and vulnerabilities in their applications or systems at various stages of the Software Development Life Cycle (SDLC). This is essential to building secure software and reducing the likelihood of security breaches. Popular threat modeling methodologies to do this are STRIDE, DREAD, and VAST.
What Is the Threat Modeling Process?
Threat modeling is a systematic approach to identifying, evaluating, and prioritizing the risks that threaten your systems, applications, or organization’s security. You methodologically analyze your assets and determine what vulnerabilities may exist, what attacks they are likely to face, and the potential impact on your organization if an asset is compromised. This allows you to mitigate and manage security threats effectively.
Why Do We Do Threat Modeling?
Threat modeling is performed to reduce the likelihood or impact of a security incident. It allows security operations teams to plan their defenses and minimize the impact of an attack, allocate resources to defend critical assets and ensure business continuity, and effectively manage risk. It is used in software design, system architecture, and by security teams to mitigate potential cyber threats.
What Should Be Included in a Threat Model?
A threat model should include various components to provide a thorough understanding of the potential cyber security threats and vulnerabilities facing a system, application, or network. These can include:
- Assets: The key assets (e.g., systems, applications, or information) an organization must protect.
- Threat actors: Groups who may target an organization’s assets, such as cybercriminals, nation-states, hacktivists, insiders, or competitors.
- Attack vectors, threats, and TTPs: The various methods, attack paths, and technologies a threat actor may use to attack assets.
- Vulnerabilities: Potential vulnerabilities in the system that could be exploited, including lacking security controls, outdated applications/machines, or software vulnerabilities.
- Mitigation strategies: How the organization will defend against the identified threats, such as implementing security controls, applying patches and updates, or redesigning system architecture.