The first task all cyber threat intelligence teams must do is define intelligence requirements. But what are intelligence requirements, how do I create them, and what is the difference between good and bad intelligence requirements?
This article answers all those questions and more. It defines intelligence requirements and explains why they are important in cyber threat intelligence. You will discover the role intelligence requirements play, the criteria for creating good requirements, and solutions to some of the challenges you may encounter when creating your own requirements.
Let’s begin by defining intelligence requirements and their key features.
What are intelligence requirements?
Intelligence is collected, processed, and analyzed information about an entity you are in competition with. In cyber threat intelligence, the competitive entity is someone who may affect your organization’s security, and the intelligence you gather about them provides you with insights into how to defend yourself.
Intelligence requirements are the insights you seek to gain about a competitive entity. They guide your intelligence process. The finished intelligence you produce should satisfy the requirements you outlined when you began your process.
According to Robert M Lee, an intelligence requirement is “a knowledge gap that needs addressing to enable action.” I like this definition. It strips down all the cyber buzzwords and focuses on the key elements. You have a gap that needs to be filled to inform a decision. Find information that helps you do that.
Intelligence requirements should be simple, focused, and support a single decision that a key stakeholder needs to make. This stakeholder could be a member of the security operations team who is triaging an incident or an executive who needs intelligence to make an informed strategic decision about future security investments. Although the decisions these two people make are very different, they both require clear and concise intelligence requirements to be defined.
This brings us to the key features of intelligence requirements.
Key features of intelligence requirements:
- Be visible to everyone: Everyone on your team and the consumer of the intelligence you generate should know the intelligence requirements you aim to fulfill. This ensures everyone understands what is expected of the intelligence generated.
- Be focused: Your intelligence requirements should focus on specific events, facts, or activities rather than ambiguous threats like “Will we be phished?” Ensure your intelligence requirements answer a single question.
- Are directed by the consumers: The people consuming the intelligence you generate should have direct input into the intelligence requirements you define. The consumers know what knowledge gaps need to be filled. You are a guiding hand to ensure the defined requirements are good, like ensuring students create SMART goals at school.
- Remain simple and support single decisions: Intelligence requirements should answer single, well-defined knowledge gaps that help a decision-maker answer a single question. For instance, what are Actor X’s current file system indicators? Is Actor Y targeting the US healthcare industry? Is Actor Z currently active?
There are two main types of intelligence requirements:
- General Intelligence Requirements (GIR): These are your organization’s ongoing and standing information needs. They are usually broad in scope and encompass a wide range of topics. For instance, they may focus on business, technology, past incidents, or geopolitics. They are the ongoing requirements that your CTI team fulfills.
- Priority Intelligence Requirements (PIR): These are intelligence requirements that are mission critical. They are key to your organization’s security success and will change based on the need to address immediate threats or situations. For example, your team may receive a PIR from the incident response team regarding additional IOCs to search for based on the latest version of Qakbot malware. PIRs should be bound to specific events or times, focusing only on critical needs.
Priority intelligence requirements are often initiated by a consumer contacting the CTI team directly when a new threat, risk, or incident emerges. It is up to the CTI team to assess if this new event is mission-critical and should be considered a priority intelligence requirement. If it is, make sure you communicate this with key decision-makers and ensure everyone buys into the requirements.
Now you know that intelligence requirements are just the knowledge gaps you want to fill. Let’s look at why it’s so important you get them right.
The Role of Intelligence Requirements
Intelligence requirements are your CTI team’s Rosetta stone. They should guide your threat intelligence processes and help navigate you through the tricky waters of the CTI Lifecycle. Let’s look at the main roles of intelligence requirements to understand why they are so important.
Inform Decision Making
Intelligence requirements guide the collection phase of the CTI lifecycle. They act as a signpost telling you what information you need to find. All intelligence requirements ask a specific question you need to generate intelligence to answer. By going through the CTI lifecycle, you can provide key decision-makers with an answer to these questions, allowing them to make an informed decision backed by data. This minimizes uncertainty and ambiguity.
Prioritize Resource Allocation and Efforts
Establishing clear intelligence requirements will help you allocate resources effectively. For instance, if you need to collect data about domains to fulfill an intelligence requirement, you can focus your collection on domain-related data sources (e.g., network flow logs, WAF logs, external data sources like Censys, etc.). This enables you to save time and money by investing in data sources relevant to intelligence needs rather than blindly collecting data.
Intelligence requirements also highlight your organization’s current security capabilities to management. Executives can see what the organization prioritizes to defend itself from cyber threats, what technologies are being used, and the value these technologies deliver. An intelligence requirement that is not being addressed or a new one that is created might need a new tool, technology, or data source. Management can judge based on existing intelligence requirements if they want to make this investment.
Intelligence requirements allow you to say, “I can defend against these threats. More investment would let me defend against these ones.”
Support Strategic Planning
Well-defined intelligence requirements allow you to align your intelligence operations with your organization’s strategic goals. This supports long-term strategic planning, including investment, defense strategies, and combating emerging threats. Intelligence requirements are vital to ensure you don’t just focus on the immediate threats but also have the capability to adapt to the evolving threat landscape.
Enable Collaboration and Cohesion
To create good intelligence requirements, you need to collaborate with the consumer of the intelligence you generate. This will be the other teams or departments in your organization, such as the SOC, the incident response team, or even the marketing and branding department. You need to walk in their shoes and understand their pain points, needs, and use cases to generate intelligence requirements that help them do their job better. This forces teams to collaborate and act cohesively, improving security.
Don’t make intelligence requirements without consulting the consumer of your intelligence. Doing intelligence for the CTI team negates the value that intelligence can bring to the entire organization. Even the marketing and branding team can get value from intelligence: “What are our customers/clients saying about our brand?” or “Is anyone trying to impersonate us?”
How to Create Effective Intelligence Requirements
Now that you know what intelligence requirements are and why they are important, let’s learn how to create good requirements.
Step 1: Determine Consumers
First, you need to determine who you will generate intelligence for, your consumers. This could be technical teams like security operations or incident response, non-technical teams like branding and marketing, or even executives (the board).
Step 2: Identify Knowledge Gaps to Fill
Once you know who you will generate intelligence for, you can sit with this consumer and determine their intelligence needs. Their intelligence needs come from what knowledge gaps they need filling, what pain points they need easing, and any use cases that can be enhanced with intelligence. Try to spend time with each consumer to understand their workflows and where intelligence might help them.
Step 3: Refine Knowledge Gaps into Intelligence Requirements
After identifying knowledge gaps, you need to create intelligence requirements that will fill these gaps. You can present a list of intelligence requirements you created to the consumer and work with them to refine these into intelligence requirements. Make sure your requirements focus on a specific fact, event, or activity, answer a single question to support a single decision, and are falsifiable.
You, not the consumer, are responsible for driving the creation of the requirements. The consumer can come to you with a list of pain points or use cases, but you are responsible for filtering and refining these into good intelligence requirements.
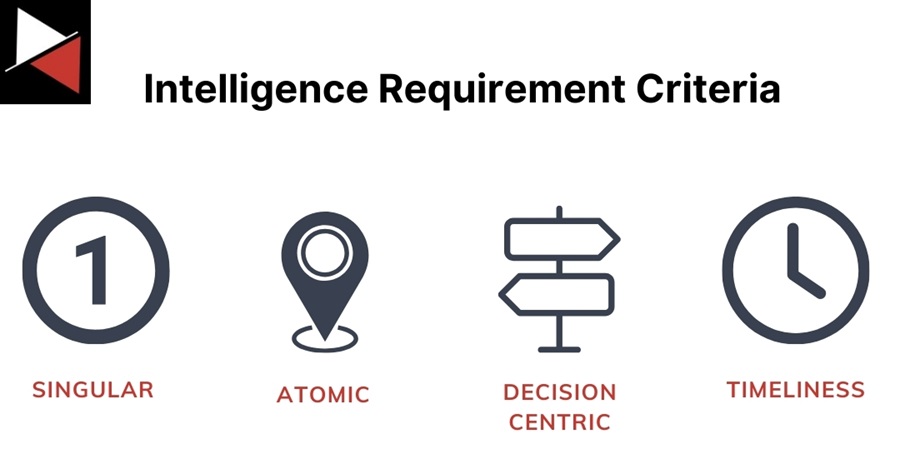
To help you create good intelligence requirements, here are four key criteria to focus on based on the work of Scott J Roberts. Intelligence requirements should be :
- Singular: A strong requirement focuses on one question and only one question.
- Atomic: The requirement should be specific to a particular fact, event, or activity.
- Decision Centric: The requirement should lead to making a single decision.
- Timeliness: A requirement should capture the timeframe for usable intelligence.
Satisfying these criteria will help you refine knowledge gaps into actionable intelligence requirements that your CTI team can fulfill. Let’s apply these criteria to several intelligence requirements to determine whether they are good or bad.
What actors might attack our company?
- Singular: Does not answer a single question.
- Atomic: Focuses on multiple actors.
- Decision Centric: Does not lead to a single decision.
- Timely: No time period.
Verdict = Weak Requirement
What indicators should we be using in our IDS?
- Singular: Does not answer a single question.
- Atomic: Not specific to a threat actor, tradecraft, activity group, or vulnerability.
- Decision centric: Does not lead to a single decision.
- Timely: No time period.
Verdict = Weak Requirement
Is X Actor currently active?
- Singular: Answers a single question.
- Atomic: Focuses on a single threat actor.
- Decision centric: Leads to a decision.
- Timely: Focuses on the current time.
Verdict = Strong Requirement
What are the current file system indicators of Actor X?
- Singular: Answers a single question (file system indicators).
- Atomic: Focuses on a single actor’s file system indicators.
- Decision centric: Leads to a decision.
- Timely: Focuses on the current time.
Verdict = Strong Requirement
What malware should we look for on our network?
- Singular: Does not answer a single question.
- Atomic: Focuses on multiple pieces of malware across the entire network.
- Decision centric: Does not lead to a single decision.
- Timely: No time period.
Verdict = Weak Requirement
Has Actor X targeted Region Y in the last six months?
- Singular: Answers a single question.
- Atomic: Focuses on a single threat actor and region.
- Decision centric: Leads to a decision.
- Timely: Defines a time period.
Verdict = Strong Requirement
It takes time and practice to develop good requirements. Use the criteria outlined above to test your intelligence requirements and ask others what they think before you invest the time in actioning it. That said, writing good intelligence requirements often comes with experience trying to satisfy them, finding problems, and refining them.
Consider using a Collection Management Framework (CMF) to help you develop requirements you can answer. A CMF details where to find data to answer different types of questions. It outlines your internal and external data sources, what data you can find there, and what CTI model the data maps to. We will look at CMFs later in this series, just remember they are a handy resource to reference when determining if you can satisfy your intelligence requirements.
Conclusion
The first piece of the puzzle in creating a CTI team is defining your intelligence requirements. These pillars guide you through the CTI lifecycle and dictate what information you collect. Intelligence requirements are the knowledge gaps the consumer of your intelligence needs you to fill.
In this article, you discovered the role of intelligence requirements in supporting key stakeholders to make informed decisions, prioritize resource allocation, and foster collaboration. You also learned the three steps to creating effective intelligence requirements, how they must be singular, atomic, decision-centric, and timely, and the difference between general intelligence requirements (GIR) and priority intelligence requirements (PIR).
Armed with the information provided in this article, you now have the power to start creating your own intelligence requirements. Good luck. Most importantly, remember to ensure your intelligence requirements fit the needs of your intelligence consumers.
Frequently Asked Questions
What is the difference between general intelligence requirements (GIR) and priority intelligence requirements (PIR)?
General intelligence requirements (GIR) focus on standing and ongoing intelligence needs. They are the requirements your CTI team aims to fulfill on a regular basis to support the continuous knowledge gaps that need to be filled. Priority intelligence requirements (PIR) are intelligence requirements that are critical for mission success. They are tied to events or time and need to be fulfilled immediately. These requirements should be set at the highest level.
How many intelligence requirements should I create?
Each CTI analyst in your team should have 2-5 GIRs that they are fulfilling, anymore they will become overwhelmed. Additionally, when a PIR arises, you want your CTI analysts to focus all their efforts on fulfilling these mission-critical requirements. Ensure there is internal visibility of an analyst’s intelligence requirements so your intelligence consumers understand what they are getting and where to get it.
How do operations, tactical, and strategic intelligence relate to intelligence requirements?
The intelligence requirements you define will dictate the type of threat intelligence you need to gather and produce. You want your intelligence to answer a single question. As such, they will usually fall either focus on operational, tactical, or strategic intelligence exclusively.
Your intelligence consumer will also dictate what threat intelligence you gather and produce. If a requirement is intended for a member of the SOC, the intelligence you share with this intended audience will be different than if you are fulfilling a requirement for an executive. Remember to always tailor your intelligence to the intended audience (consumer).