Cyber threat intelligence reporting is hard. You need to pinpoint who your intelligence is for, structure it in an easy-to-consume way for that audience, and make it actionable. However, the days of struggling with disseminating threat intelligence are over. Let me introduce you to CTI Blueprints.
This revolutionary new CTI project from the geniuses behind the MITRE ATT&CK framework aims to help CTI analysts tackle the challenges of creating consistent, actionable, and high-quality CTI reports. It provides a toolset to increase the operational relevance of reports and help analysts fulfill the intelligence requirements of their organization.
Let’s jump in and learn how a standardized set of templates and a couple of simple tools can change the CTI reporting game!
What is the CTI Blueprints Project?
CTI Blueprints is a project by MITRE Engenuity’s Center for Threat-Informed Defense that aims to improve the distribution and sharing of cyber threat intelligence (CTI). The project’s developers recognized that many threat intelligence producers lacked clear guidance on creating finished intelligence that defenders could use effectively. It was left to individual threat intelligence analysts to structure their reports as they saw best, making using threat intelligence difficult.
MITRE Engenuity is a non-profit subsidiary of the MITRE Corporation that focuses on creating innovative solutions for challenges faced by cyber security and other technology-related fields. They do this by fostering collaboration between industry, academia, and government to accelerate the development of practical solutions that serve the public interest.
Here are some of the common challenges CTI analysts face when reporting intelligence:
- No threat intelligence reporting standards: There are no standardized reporting guidelines for CTI analysts to follow, making reporting a struggle for new analysts and inconsistent for everyone else.
- No structured reporting process: Reporting and distributing intelligence is currently an unstructured process that each CTI team must define by themselves. This makes collaboration and sharing intelligence difficult.
- Reporting is manual and time-consuming: Creating intelligence reports costs analysts time and resources. It takes them away from the mission and slows down the team.
- Difficult to create actionable threat intelligence reports: Analysts struggle to create actionable reports tailored to specific stakeholder intelligence requirements.
CTI Blueprints project created a toolset to address these challenges. This toolset allows CTI analysts to produce actionable threat intelligence reports that consumers can operationalize immediately. This toolset includes templates, an authoring tool, and a publishing tool. Let’s look at each.
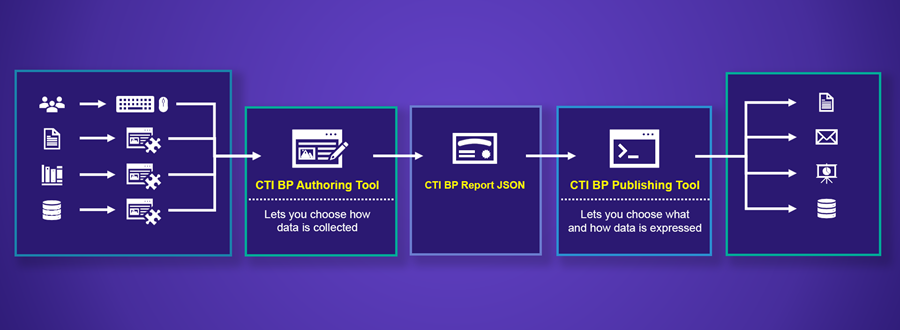
The Templates
Templates are the showpiece of the project. They provide a structured framework for communicating actionable intelligence relevant to your target audience. Each template allows you to produce high-quality, consistent, and repeatable intelligence reports every time you go through the threat intelligence lifecycle.
The project includes four templates that each focus on delivering a specific goal for a specific stakeholder. Expand the dropdowns below to find out more.
Know: Threat Actor Report
The Threat Report is designed to be a living encyclopaedia about a threat actor or category of activity. This report is maintained by the CTI team and updated whenever new intelligence about an adversary is generated. Threat reports provide an easy reference for tactical teams to understand how a threat actor relates to your organization and contain technical information to help inform follow-up actions. They help you know the adversary.
Find: Intrusion Analysis Report
The Intrusion Analysis Report supports threat hunting and incident response operations by providing actionable indicators that these teams can use to search for threats within your environment. These reports should be iterative and not focus on completion. As soon as new information is uncovered, it should be added to the report and distributed. They provide tactical, real-time support to defenders.
Change: Campaign Report
The Campaign Report highlights new information about threat actors, campaigns, and capabilities. When new intelligence comes in about a topic your team is tracking, a campaign report should be created to highlight this new information alters the risk posed to your organization. These do not include all information about a topic. Instead, they are succinct reports that convey a change to the risk calculus your intelligence consumers should be aware of.
Inform: Executive Report
The Executive Report is for informing key decision-makers about threats. It is for a non-technical audience who need clear and precise reporting that helps support a strategic decision. These reports focus on the why and how rather than the what and when. They tell a narrative to help senior leadership make better business decisions.

Authoring Tool
The CTI Blueprints authoring tool is a web application you run locally to create CTI reports based on the aforementioned CTI Blueprint templates. You select what kind of report you want to create based on your target audience or use case, and the tool will walk you through the report creation process. It includes rich dropdown menus, text boxes, tables, file saving, and the ability to edit multiple pages simultaneously.
The tool also includes an extensible plugin system that allows you to tailor it to your needs through custom plugins that enhance functionality. Currently, the tool comes pre-installed with three plugins: Attack Flow, Import CSV, and D3FEND. However, you can easily create your own plugins using the Plugin API. For more information, read the GitHub Wiki Authoring Tool page.
Publishing Tool
Reports you create with the authoring tool are saved in JSON format. To export reports to other formats and share them with intelligence consumers, you can use the project’s publishing tool. This tool can convert saved reports into common formats for distribution or storage. The tool currently supports exporting CTI reports to Microsoft Word DOCX or PDF format.
To recap, intelligence is gathered and processed by a CTI analyst, the authoring tool is used to automatically organize that data into a structured report using one of the four templates, and the publishing tool converts the report into a format that can be easily distributed. You can see Mia Sanchez demo this process in a presentation at Adversary Village.
Why You Should Use This Project
So why should you care about this project? If you have been doing cyber threat intelligence for long enough, you will know that disseminating intelligence is probably the most important stage of the threat intelligence lifecycle.
You gather intelligence, analyze, and disseminate. The only stage the consumer of your intelligence sees is the dissemination stage. If you fail to communicate the intelligence you have prepared in a clear, concise, and timely manner, all your work goes to waste. This is why it is vital to nail down the dissemination stage.
Good threat intelligence is like Kentucky Fried Chicken (KFC). It is relevant to the audience, arrives on time, and is actionable!
CTI Blueprints is a project that will empower you to do this! The project provides a standardized process for creating high-quality CTI reports tailored to a specific target audience.
- You can create a report for the front-line defenders as they are responding to a threat – an Intrusion Analysis Report.
- You can create an ongoing knowledge base report for other teams to learn more about a threat actor, campaign, or ransomware gang – a Threat Actor Report.
- You can create a report to inform decision-makers about threats so they can make key strategic decisions – an Executive Report.
CTI Blueprints covers the full range of threat intelligence and makes reporting simple, consistent, and efficient.
Advantages of CTI Blueprints
- Advances the quality of CTI reporting: The project provides standardized templates that include prescriptive guidance on essential elements you must include based on your target audience. These elements ensure maximum impact is delivered and actionable intelligence is produced.
- Provides a standardized reporting process: The project allows CTI teams to build a standardized reporting process into their workflow. They can use the tools provided and add custom plugins to tailor the tools to their specific needs. This reduces the time spent manually building reports and allows analysts to streamline their work.
- Increases analytical rigor: Many organizations throw money at CTI products without spending time creating processes that follow a rigorous analytical framework and deliver relevant, actionable reports. CTI Blueprints delivers templates that require intelligence requirements, feedback, probability, data sources, and intelligence gaps to be considered. This requires analysts to deliver a higher quality of intelligence.
- Makes it easier to consume and share CTI: The project provides a standard for what makes a good CTI report and packages it in a common machine-readable JSON format. This can then be ingested by machines or transformed into a readable report for your intelligence consumer. These factors make sharing and consuming CTI reports consistent and easy.
- Streamlines the integration between CTI and key stakeholders: CTI Blueprint’s templates allow CTI teams to streamline communication with other security or technology teams. Disseminating relevant intelligence to an incident responder or senior executives is as simple as changing a few options in a web GUI.
Still not convinced? Discover how others are using the project and why it matters to them.
How to Use CTI Blueprints
Let’s move on to the fun part, using CTI Blueprints! The proceeding sections will talk you through installing the toolkit, using the authoring and publishing tools, and extending the tools through plugins.
If you just want to get a quick demo of what the CTI Blueprints project offers, check out the web-based authoring tool. The Center for Threat-Informed Defense hosts this tool so you can see what the project is about, discover the different reporting types, and create a demo report without installing anything on your local machine.
Installation
To run the CTI Blueprints project locally, go to the project’s GitHub Releases page and download the ZIP archives for the Authoring and Publishing tools. You will also see a ZIP archive for the templates, you can use this if you want to modify the Microsoft Word DOCX directly.
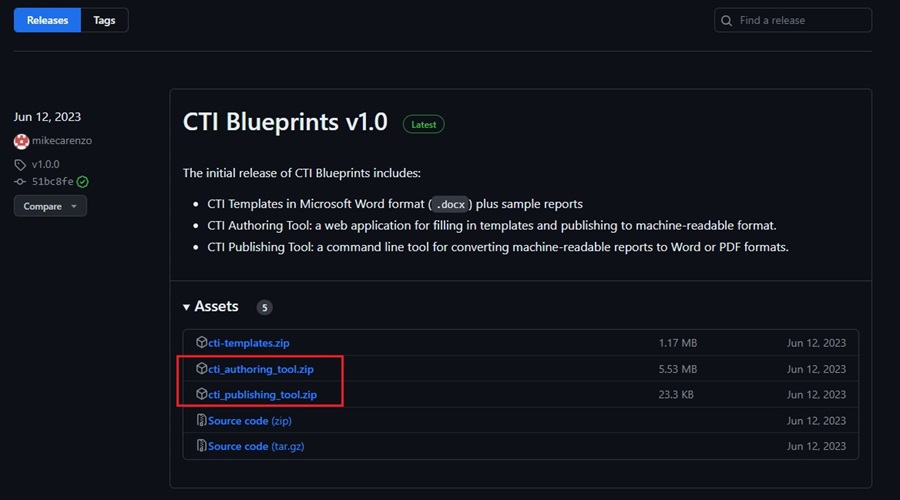
Next, extract the two tools to your chosen destination. The Authoring tool is built using HTML, CSS, and JavaScript, so you only need a web browser to run it. There are no dependencies to install.
However, the Publishing tool is built using Python. To install the dependencies required to run the tool, open the folder where the tool is located by right-clicking and selecting Open in Terminal (on Windows). Then run the following command:
pip install -r requirements.txt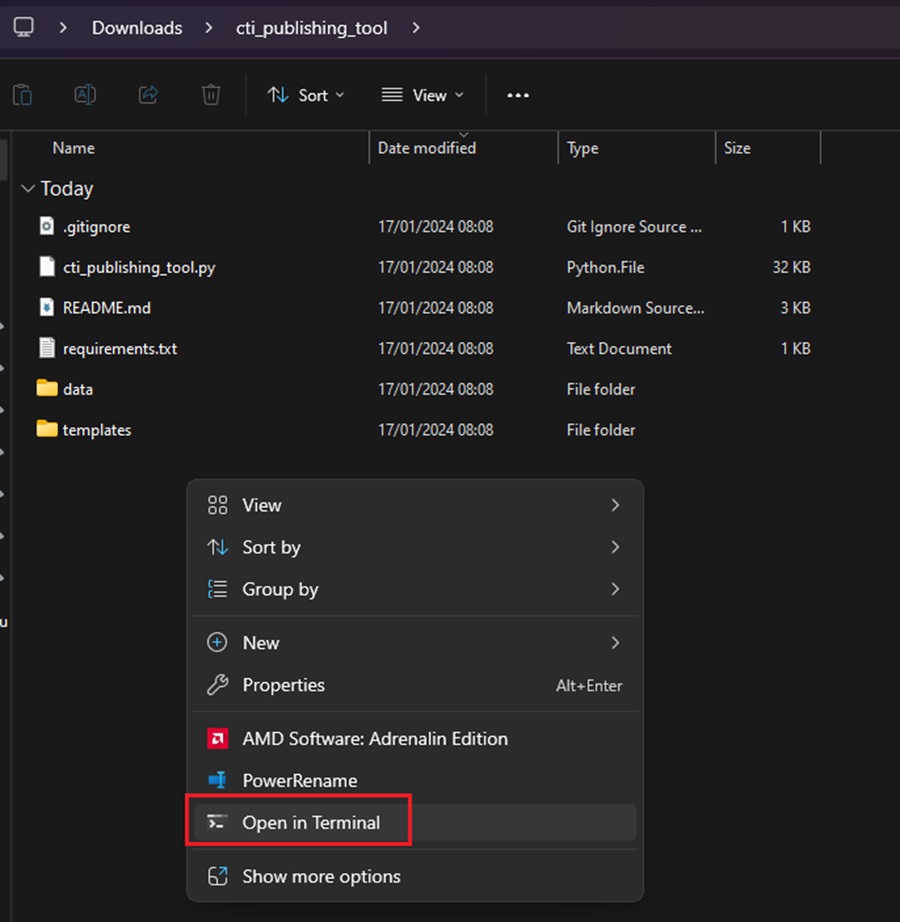
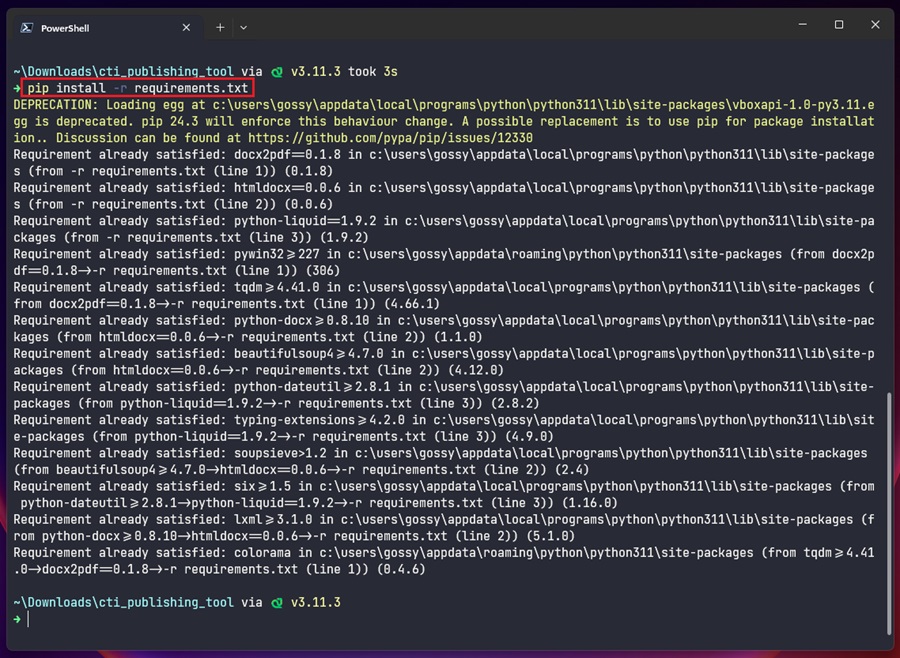
Now you can get your hands dirty and begin using these tools.
Authoring
To open the Authoring tool, navigate to the folder where the tool is located and double-click on the index.html file. This will open the tool in your local web browser, ready for you to use.
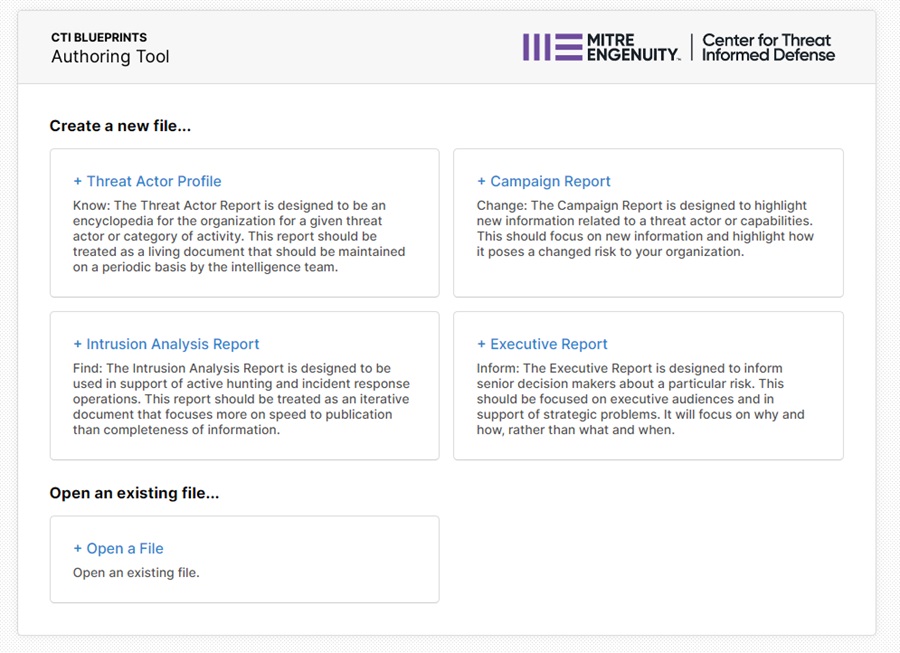
The Splash page will welcome you. Here you can select the type of threat intelligence report you want to create or open an existing one you have saved on your machine.
Once you select the type of report you want to create, you will be taken to a web GUI. Here you fill in the report details using a mixture of typed fields, rich dropdown menus, and tables.
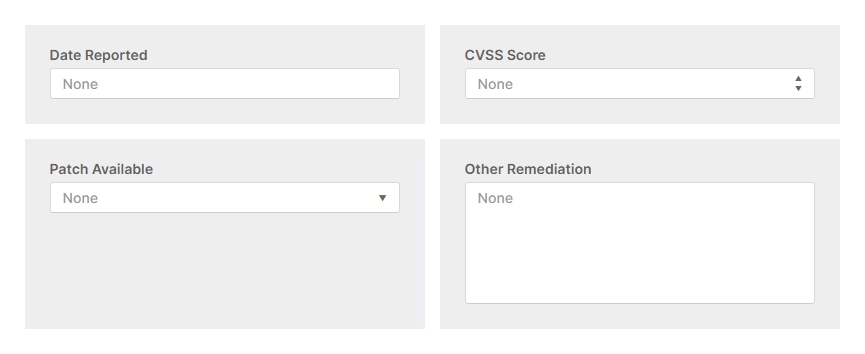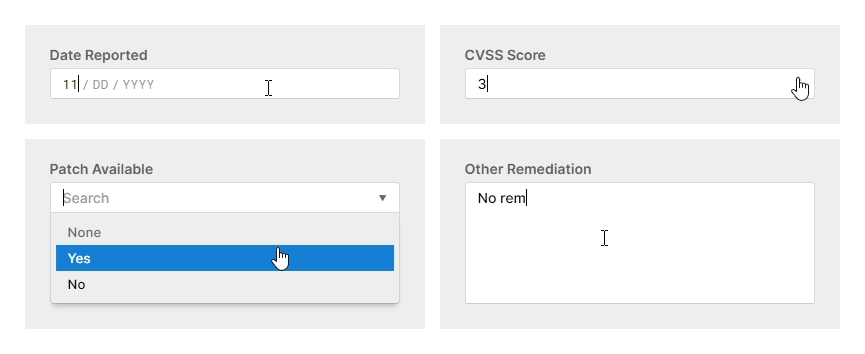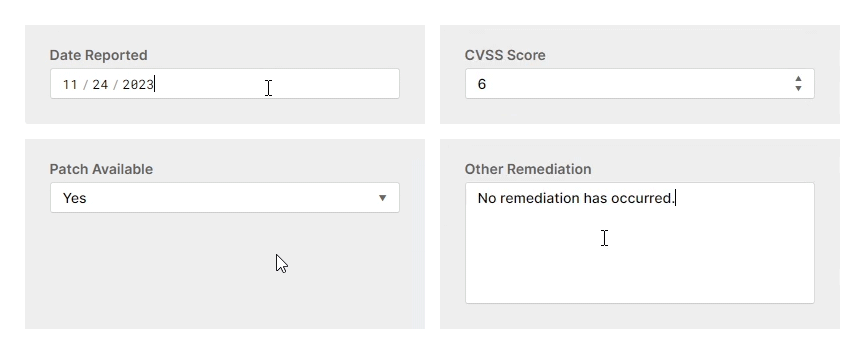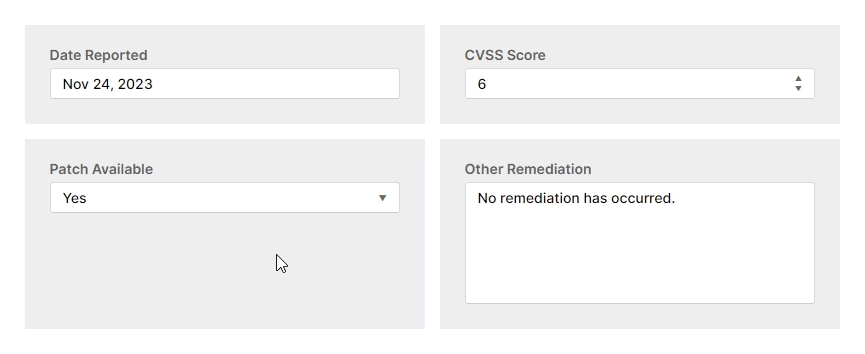
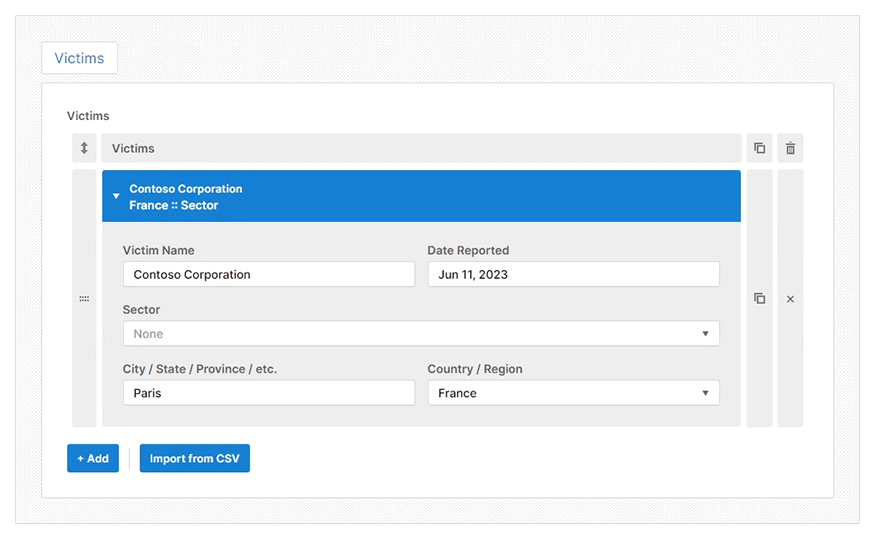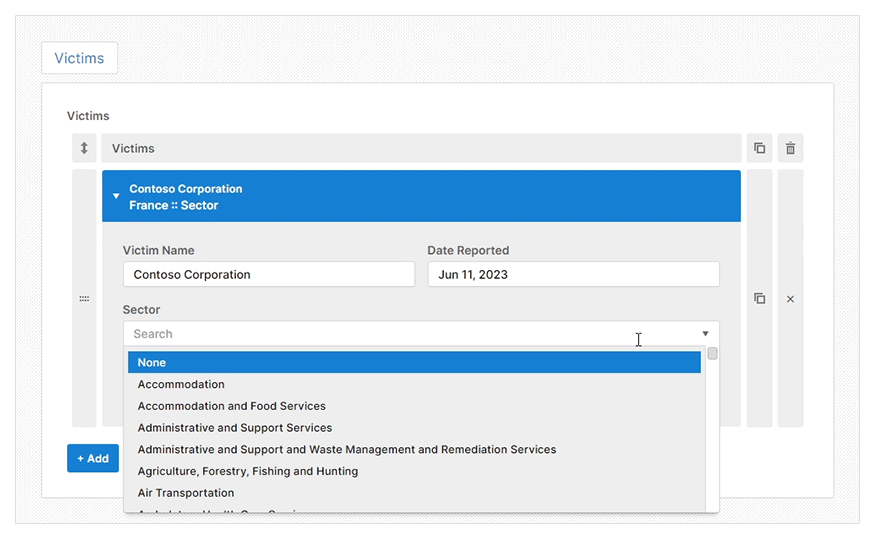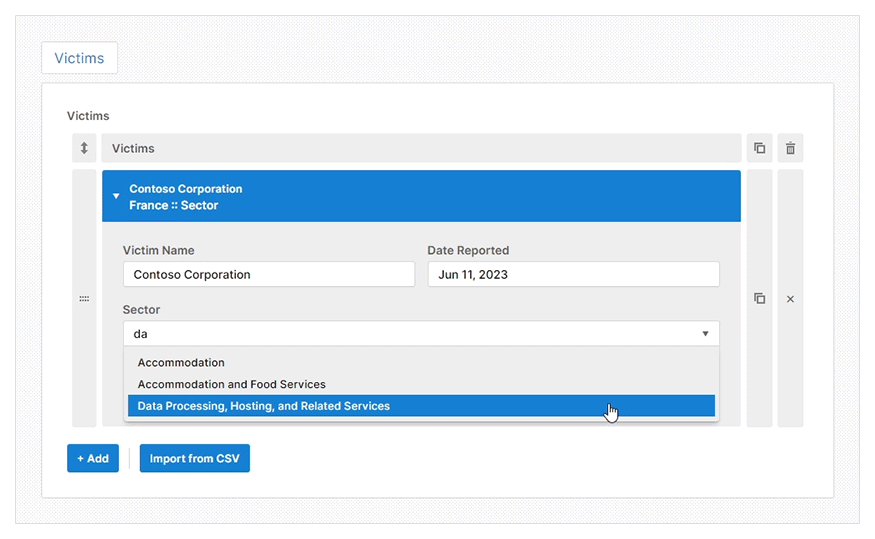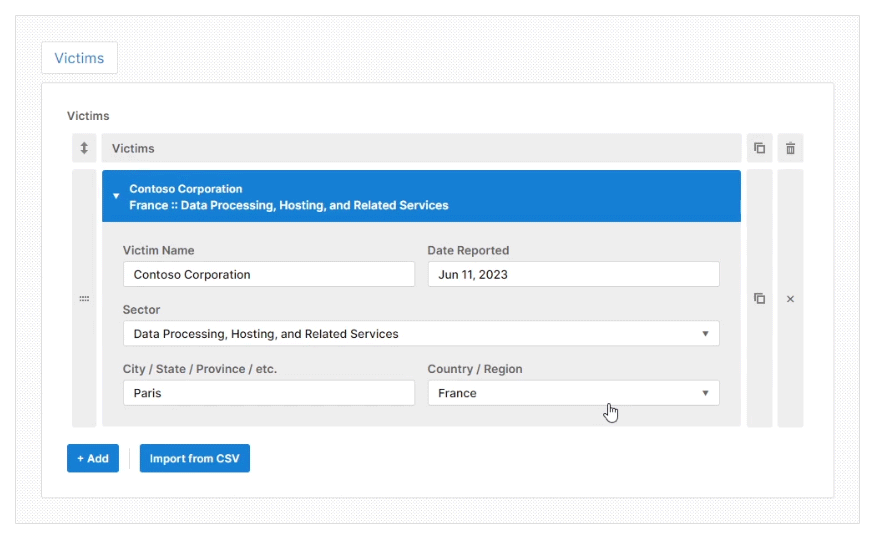
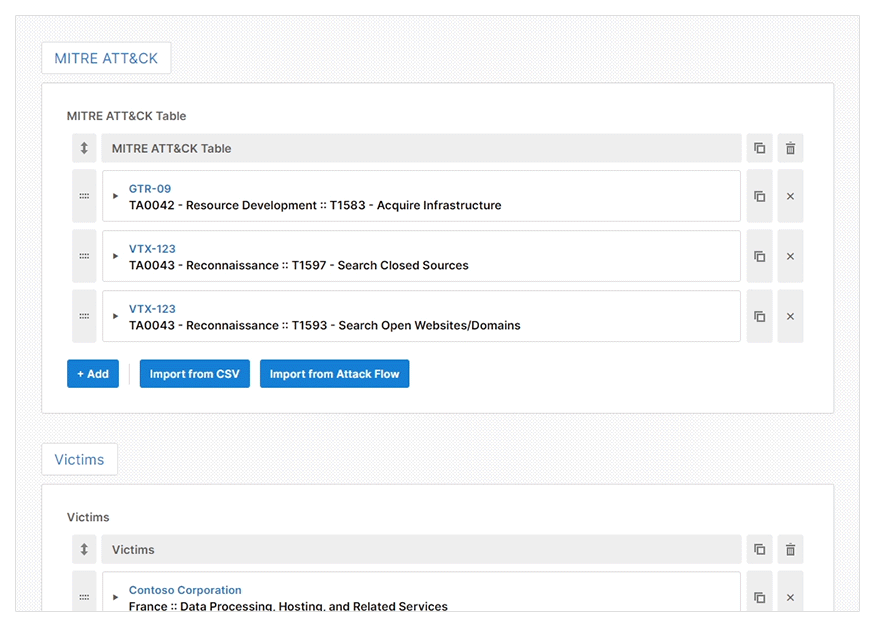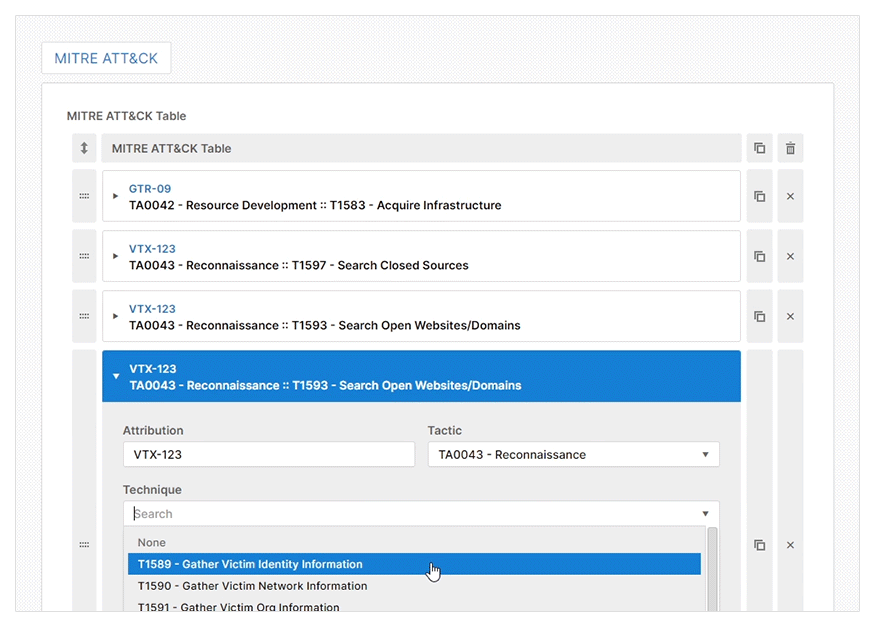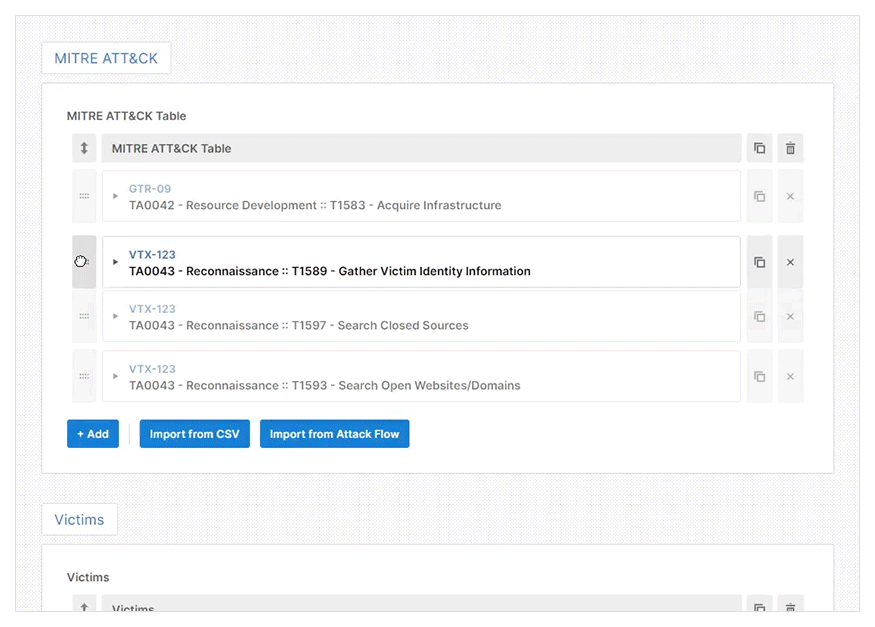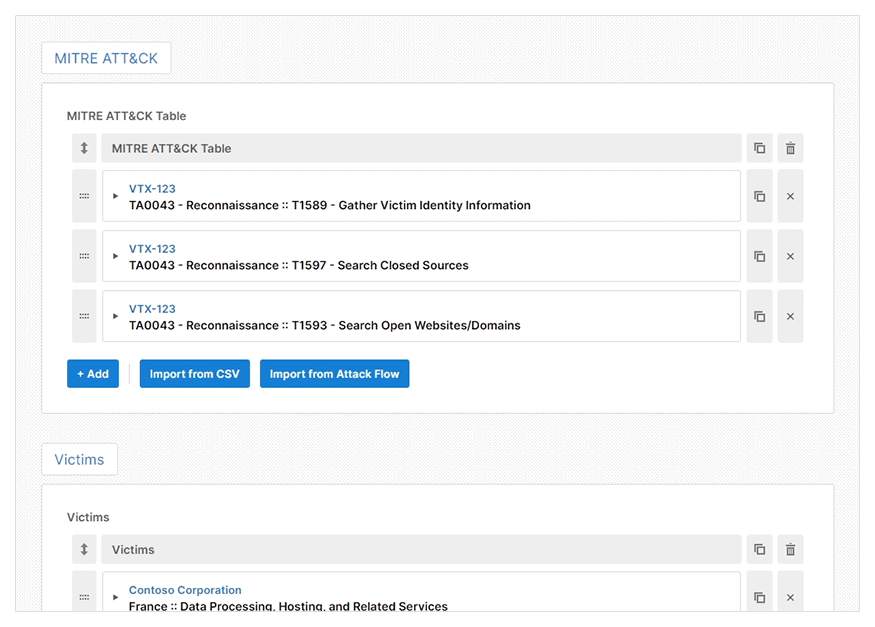
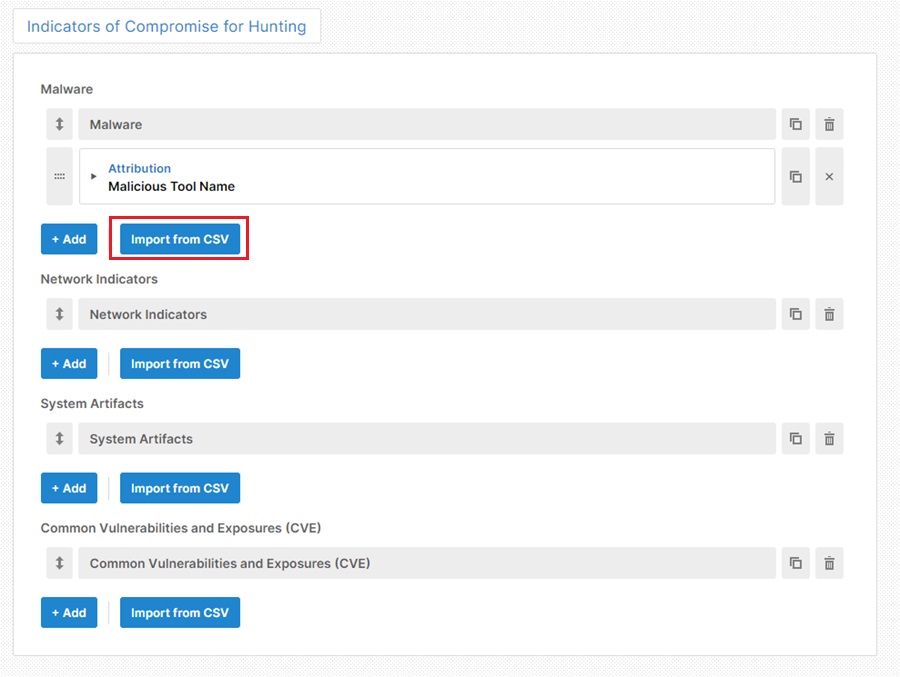
The web GUI will show different reporting details for you to complete based on your chosen report type. It also offers prescriptive guidance to help you to create a high-quality threat intelligence report efficiently. A feature that helps with this efficiency is the pre-installed Import CSV plugin which allows you to import data directly from a CSV file.
The Authoring tool also includes handy features for working with files. You can save or open reports you previously created and need to edit. Saved files are stored as JSON documents, allowing them to be easily shared and machine-readable.
You also have the ability to work on multiple reports at once using the multi-page editing feature at the bottom of the web GUI. For instance, you may be writing a Campaign Report about an ongoing attack campaign you are seeing while also updating a Threat Actor Profile Report to add to the encyclopaedia of knowledge you have about a specific adversary.
Plugins
The Authoring tool has three plugins pre-installed:
- Attack Flow: A plugin that allows you to upload a published Attack Flow document to populate MITRE ATT&CK tactics, techniques, and sub-techniques automatically.
- Import CSV: To let you automatically populate any table with a CSV file. This is useful when entering many indicators or TTPs during an investigation.
- D3FEND: A plugin that automatically creates a link to the appropriate security controls to mitigate an attack in MITRE D3FEND for each TTP you enter. This eliminates the need to look up each D3FEND control and manually paste the link in yourself.
That said, you are not limited to just these plugins. The team behind the project is working on adding more plugins that support integrations with existing CTI projects like OpenCTI, the ability to send malware hashes for analysis, and one for creating a timeline of events. You can find out more by visiting the project’s GitHub Development page.
Publishing
The Publishing tool is a simple Python script that takes your threat intelligence report (in JSON format) and generates a Microsoft Word DOCX or PDF document for sharing.
If you are unfamiliar with using and installing Python scripts, read the CTI Blueprints Authoring tool documentation. This walks you through the installation process, how to resolve dependency issues, and provides solutions to common problems.
The command below generates a Threat Actor report based on the apt29.json file. The generated report will be saved to the output folder by default, as shown below.
python.exe cti_publishing_tool.py -r 1 -f "apt29.json"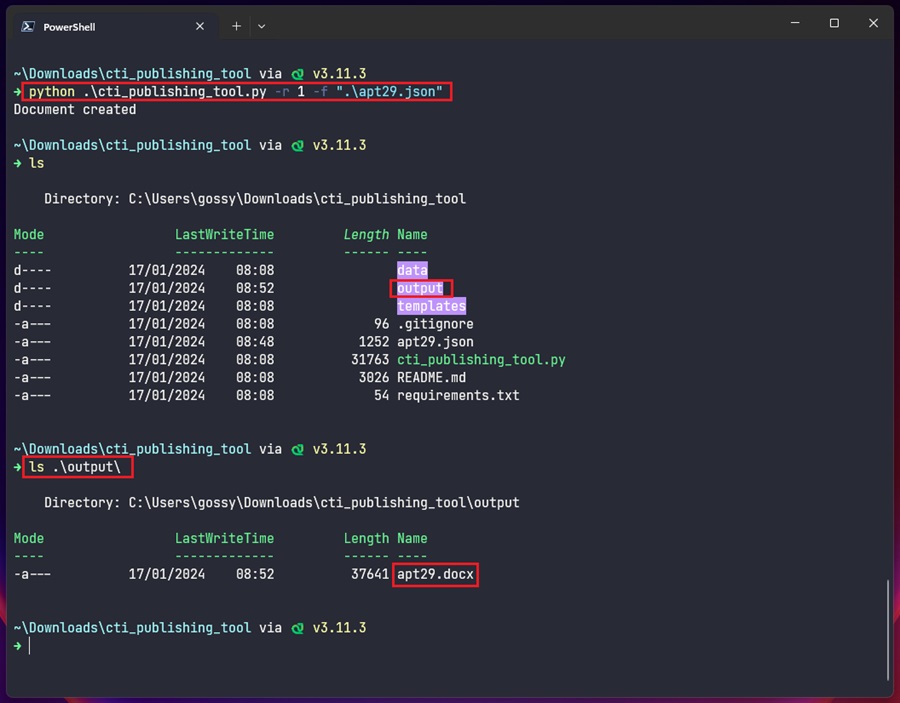
The -r argument specifies the report type to generate; 1 for Campaign, 2 for Executive, 3 for Intrusion Analysis, and 4 for Threat Actor. Meanwhile, the -f argument specifies the absolute path to the JSON data input.
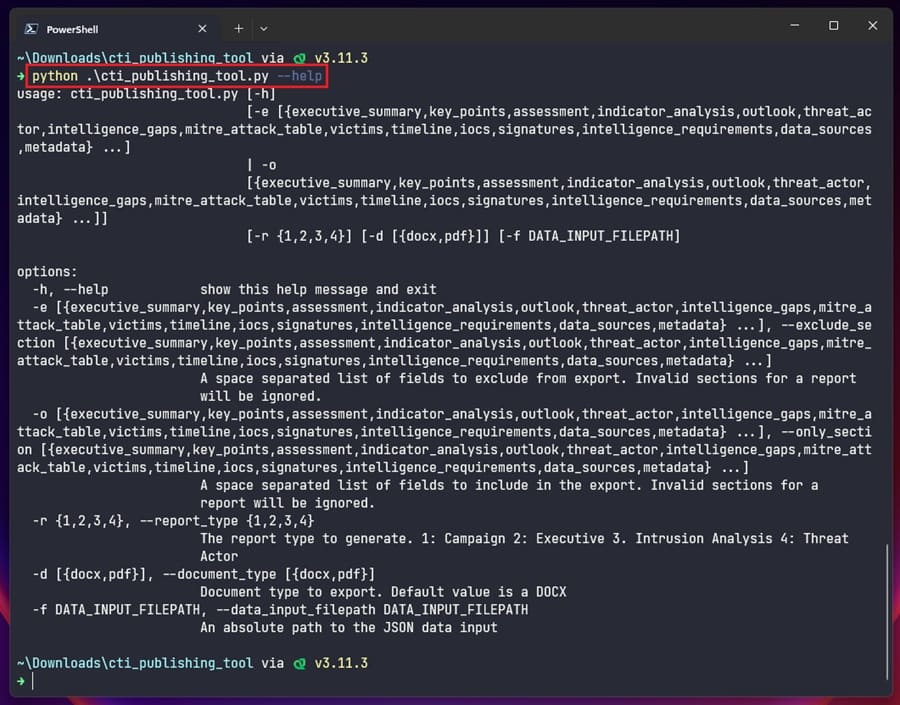
If you want to learn more about the command line options provided by the tool, run the tool with the --help argument.
The report is now ready to distribute. By default, the Publishing tool will export reports in DOCX format. Add the argument -d pdf to the command if you want a PDF.
Conclusion
Cyber threat intelligence reporting is hard. The CTI Blueprints project aims to make it much easier, more consistent, and more efficient. You saw some of the advantages the project can bring to your CTI workflow and how it can empower your team to deliver high-quality, actionable reports every intelligence cycle. I highly recommend trying this project to see if it works for you!
If you want to explore some of the other projects MITRE Engenuity’s Center for Threat Informed Defense has to offer, I recommend checking these ones out:
- Sensor Mappings to ATT&CK: A project to help security operations teams and security leaders understand which tools, capabilities, and events can help detect real-world adversary TTPs in their environments.
- Summiting the Pyramid: A research project focusing on evaluating cyber analytics based on how difficult it is for an adversary to evade them. It aims to shift the advantage towards defenders with improved analytics that catch adversaries even as they evolve and is based on the Pyramid of Pain.
- Threat Report ATT&CK Mapper (TRAM): An open-source platform that automates the mapping of CTI reports to MITRE ATT&CK using a Large Language Model (LLM). This reduces the cost and increases the effectiveness of integrating ATT&CK across the CTI community.
- ATT&CK Workbench: An application allowing users to explore, create, annotate, and share extensions of the MITRE ATT&CK knowledge base so they can track the latest threats.
- Attack Flow: A language for describing how cyber adversaries combine and sequence various offensive techniques to achieve their goals. It uses a visual building tool to combine ATT&CK techniques, chart an attack path, and allow defenders to understand their defensive coverage.
Let me know if you want a deep dive into any of these projects to learn more!
Frequently Asked Questions
Who Can Benefit From the CTI Blueprints Project?
The project is for CTI teams that produce threat intelligence reports for key stakeholders. This includes common CTI customers, such as SOC analysts, threat hunters, red/purple teams, and executives, as well as other CTI teams. It empowers teams to perform scalable, repeatable, and targeted dissemination of threat intelligence.
Is the CTI Blueprints Project Free?
Yes. CTI Blueprints is a free, open-source project that aligns with the Center for Threat-Informed Defense’s mission of advancing threat-informed defense globally through freely available research and development projects. You can start using the project today by visiting the GitHub page and following the guidance in this article.
Who Can I Contribute to the CTI Blueprints Project?
The project owners welcome feedback or contributions that help advance the CTI Blueprints project. You can provide feedback by reaching out on GitHub or LinkedIn or contacting the team directly at ctid@mitre-engenuity.org. If you want to contribute to the project, try developing additional plugins for the community. See the GitHub Wiki Developer page for a list of suggested plugins the developers would find useful.
That said, spreading the word is the best way to give back to this project and help it grow. The team wants to see widespread adoption of CTI Blueprints in the community, so use it, make content about it, and share it in your professional network!
Can I Customize the Report Templates?
Yes. Customizing the report templates can be done by editing the Microsoft Office DOCX template documents included in the project. You can change fonts, format, and structure by editing the document templates to personalize your reports. For more details, read the GitHub Wiki CTI Templates page.