The MITRE ATT&CK framework can be confusing, overwhelming, and difficult to navigate. It’s over-stacked with attack techniques that are hard to visualize or make sense of. If only there were a tool to help. Let me introduce you to the ATT&CK Navigator!
The ATT&CK Navigator is your go-to tool for visualizing ATT&CK techniques, using the framework for your security testing and operations, and when those pesky executives want a report that is easy to understand.
This guide will teach you everything you need to know to get started using the ATT&CK Navigator, provide examples of how to use it, and demonstrate its various features. Let’s get started visualizing cyber attacks!
What is the ATT&CK Navigator
The ATT&CK Navigator is another awesome tool that the people behind MITRE ATT&CK have created to expand the framework’s functionality. It helps cyber security professionals visualize, annotate, and work with the MITRE ATT&CK Framework through a user-friendly interface that allows you to map and analyze ATT&CK techniques.
The tool is easy to use, available locally or on the web, and, most importantly, makes the MITRE ATT&CK framework accessible!
MITRE ATT&CK is a comprehensive and structured knowledge base of cyber adversary tactics, techniques, and procedures (TTPs) used in cybersecurity. It is designed to help organizations understand and defend against the tactics used by threat actors in real-world scenarios.
Anyone can use the ATT&CK Navigator:
- Cyber threat intelligence analysts can use the tool to share visualizations of attacks.
- Security operations can use it to structure their detection engineering efforts, identify gaps in their coverage, and perform threat hunting.
- Incident responders can use ATT&CK Navigator to rapidly map overserved behaviors with specific ATT&CK techniques.
- Red teamers and penetration testers can use it to plan their attack strategies.
The tool is versatile. If you have a use case for the MITRE ATT&CK framework, it will help facilitate it by allowing you to create a layer – a custom view of the ATT&CK knowledge base.
Whenever you use the ATT&CK Navigator, you will either interactively create a custom layer or import one from a JSON file. This layer maps the ATT&CK techniques you are interested in against the Enterprise, Mobile, or ICS ATT&CK frameworks so you can visualize the matrices.
You can manipulate the cells in your layer to highlight the techniques you are interested in with color coding, add comments to annotate your work or include numerical values to indicate priority or frequency.
Once you are finished visualizing the attack techniques of interest, you can then export your ATT&CK Navigator layer as a JSON file and easily share it with others. Visualizing attacks has never been easier!
Now that you know what the ATT&CK Navigator is, let’s explore how to use it.
Using the ATT&CK Navigator
There are two ways you can use the ATT&CK Navigator.
- You can use the web interface by navigating to https://mitre-attack.github.io/attack-navigator/.
- You can download the ATT&CK Navigator locally and run it in your own environment.
The option you choose will depend on your use case. If you want to explore the tool, visit the GitHub Pages website. If you want to run the tool in your own production environment, keep your data local, and integrate it with other tools, clone the GitHub project and install it locally.
Let me show you both options.
ATT&CK Navigator Web Interface
If you are new to the ATT&CK Navigator, I recommend using the web interface when first starting. It’s free, available anywhere, and doesn’t require any setup.
To do this, head over to the GitHub Pages website https://mitre-attack.github.io/attack-navigator/ in your favorite web browser, so long as it’s in this list of supported browsers:
- Internet Explorer 11 (if you are insane)
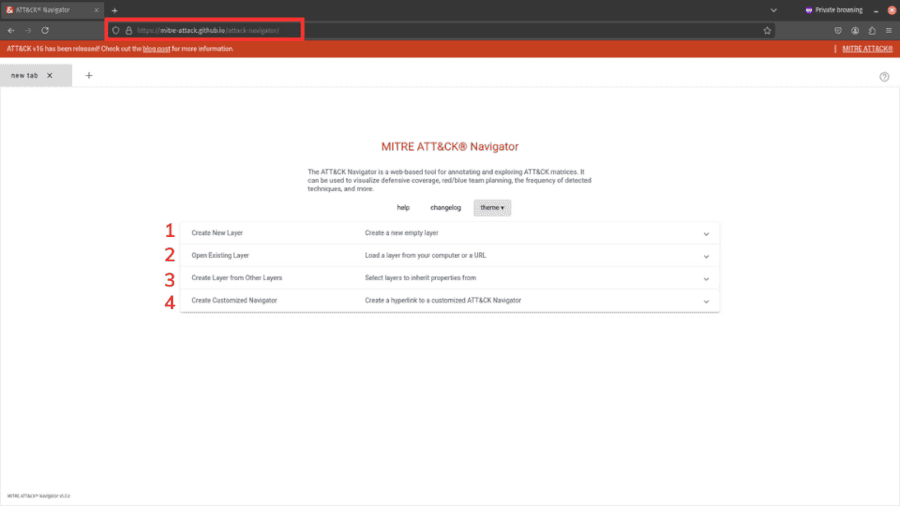
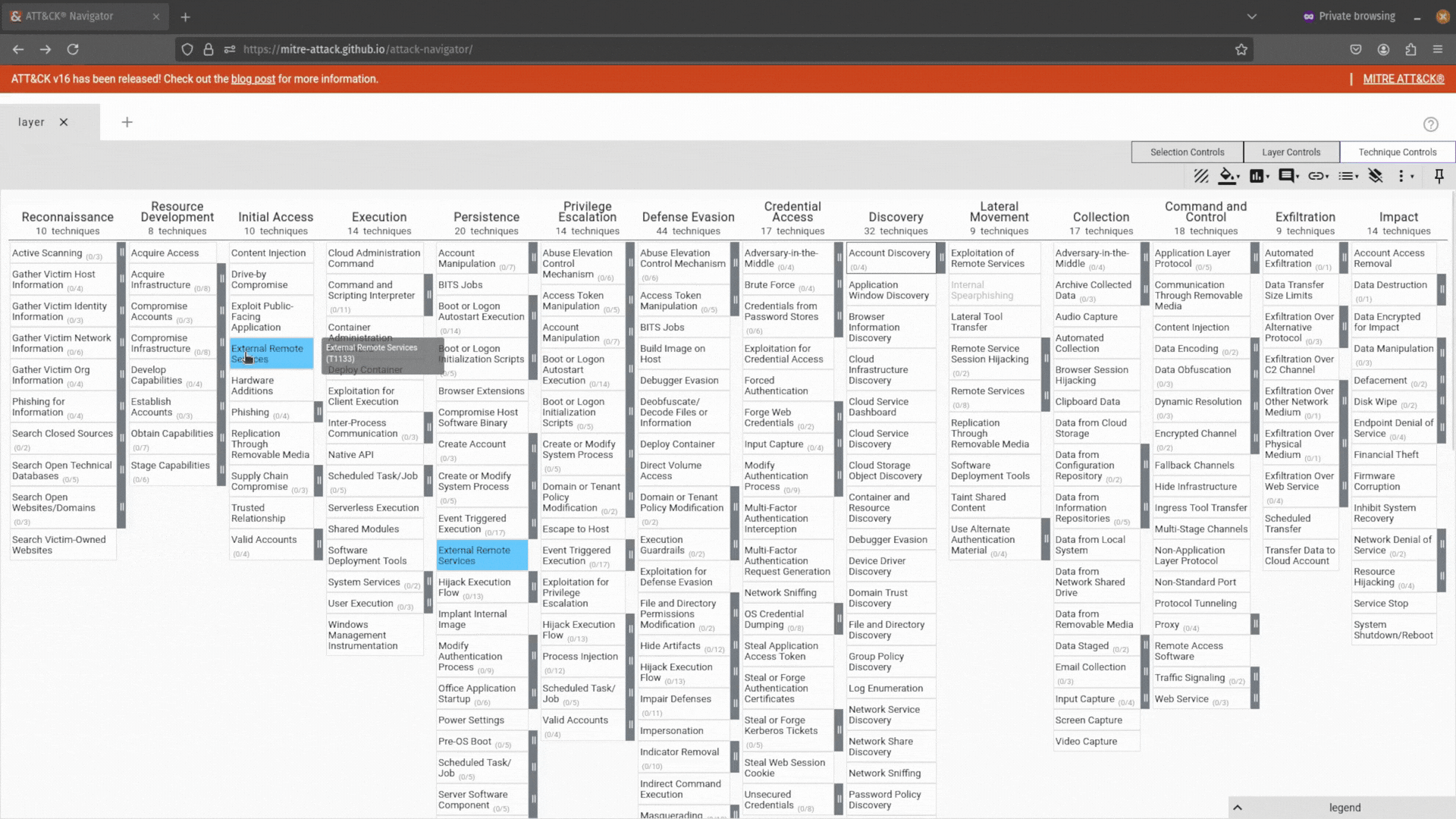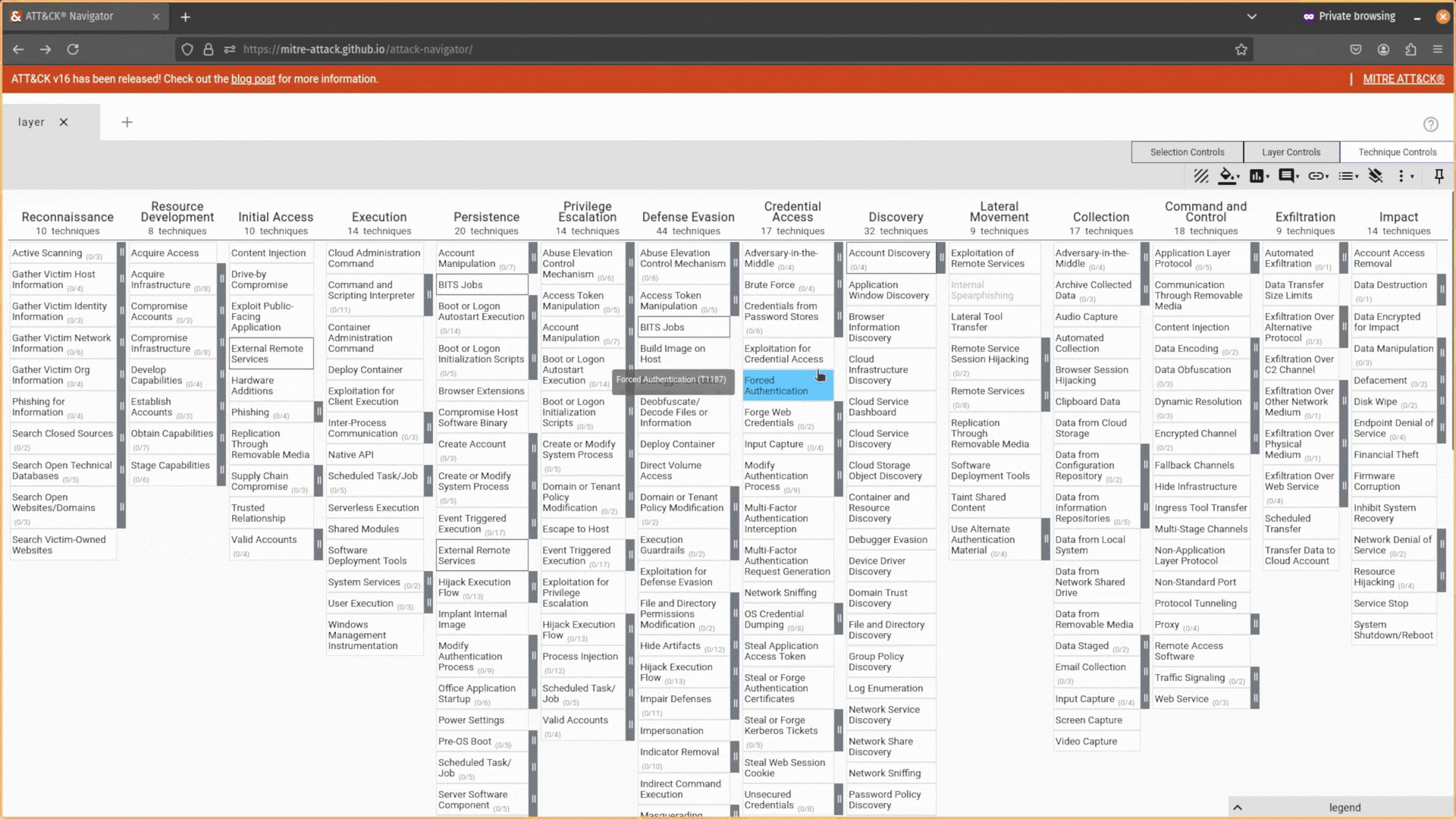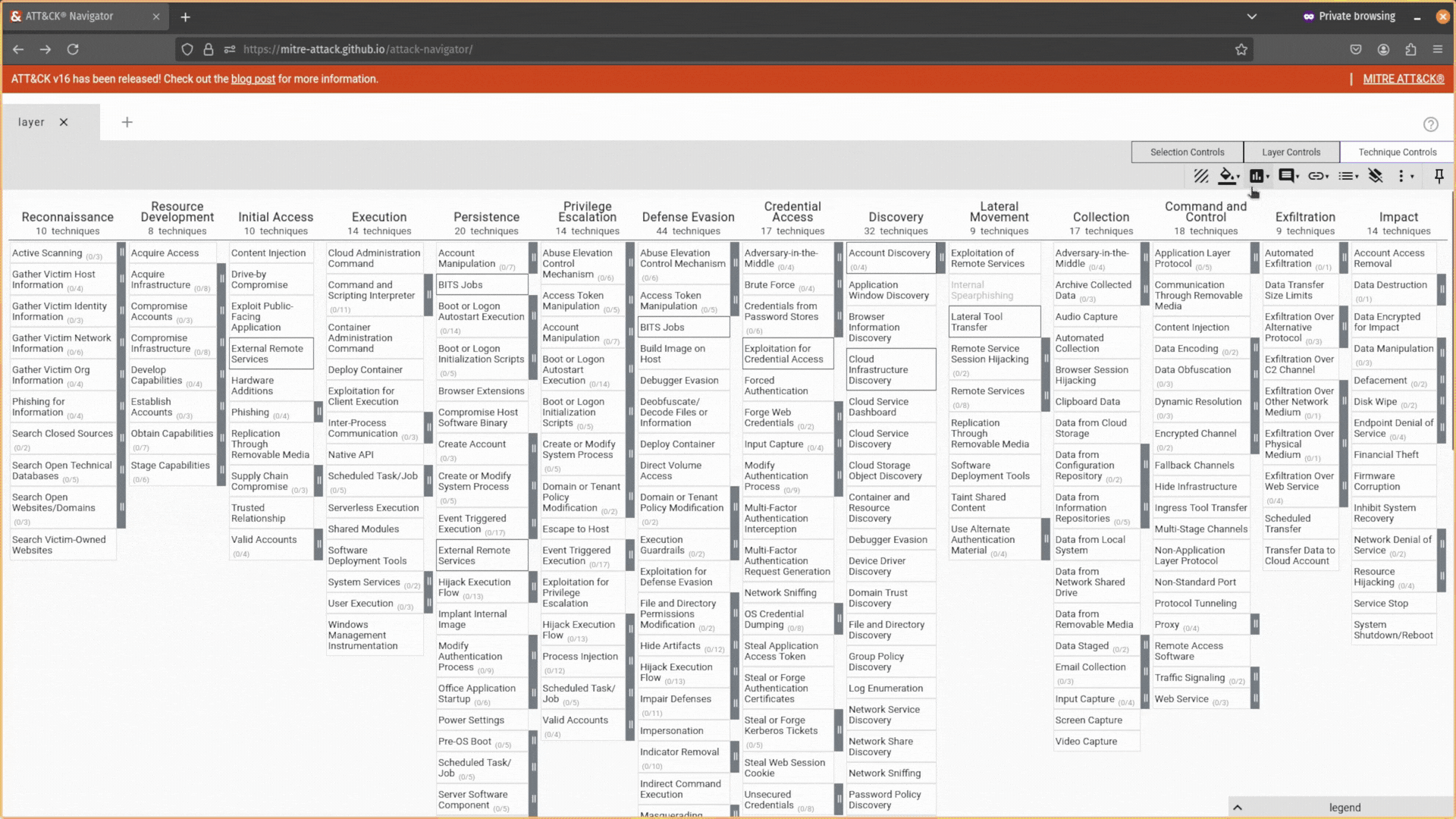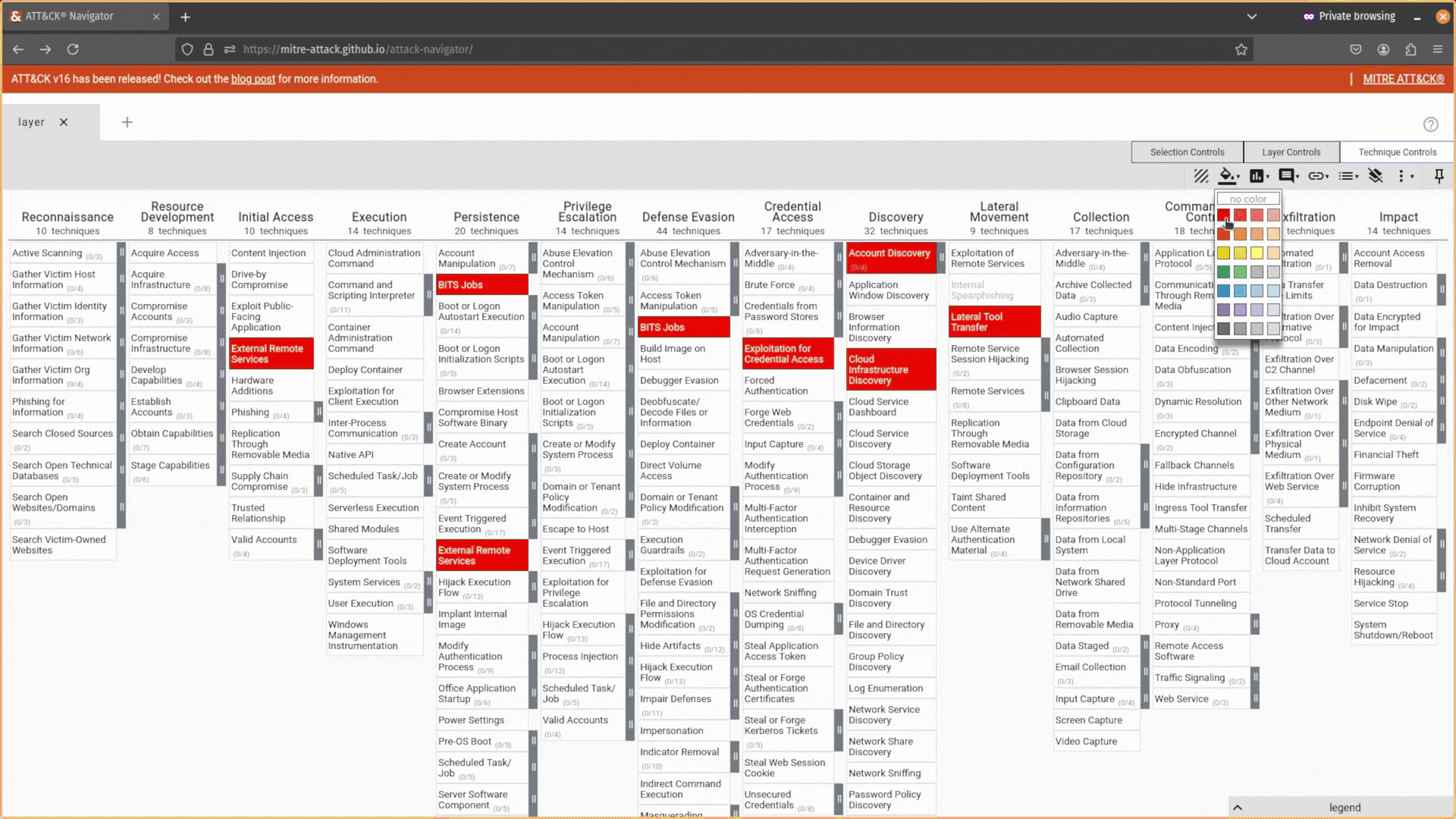
Here, you will be greeted by the default menu that lets you choose from 4 options (excluding changing the theme or viewing the help menu):
- Create a New Layer: Interactively build a new layer in ATT&CK Navigator using the web GUI.
- Open Exiting Layer: Load an existing ATT&CK Navigator layer into the tool. You can do this by uploading a JSON file from your local computer or grabbing one from a URL.
- Create Layer from Other Layers: This lets you create a layer that inherits properties from other layers, such as domain/version, technique scores, gradients, coloring, comments, links, metadata, states, filters, etc. It is useful if you need to repeat your analysis in a structured fashion.
- Create Customized Navigator: Build your own custom ATT&CK Navigator using only the features that are important to you.
You can use the tab menu at the top of the ATT&CK Navigator GUI to work on multiple layers simultaneously.
Most people get started using the tool by creating a new layer. Clicking this button will allow you to choose which MITRE ATT&CK matrix you want to use (Enterprise, Mobile, or ICS) and the version you want to use.
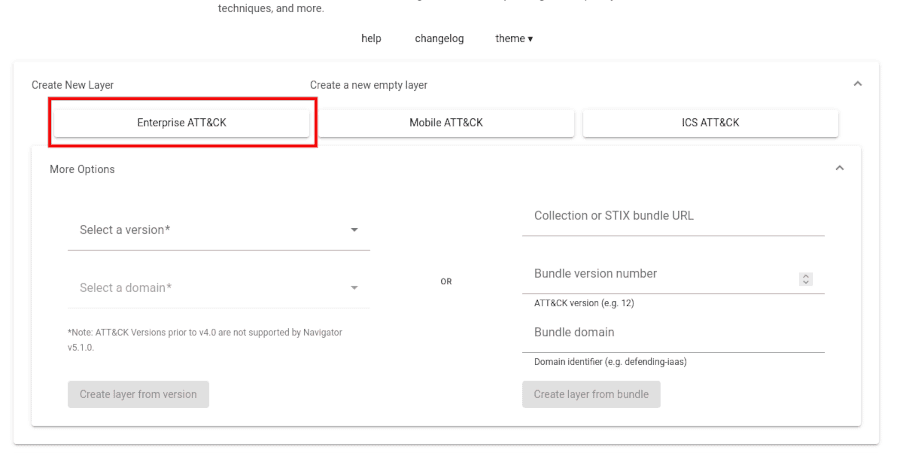
Here, I selected the default Enterprise matrix. It will then populate your ATT&CK Navigator layer with the said matrix.
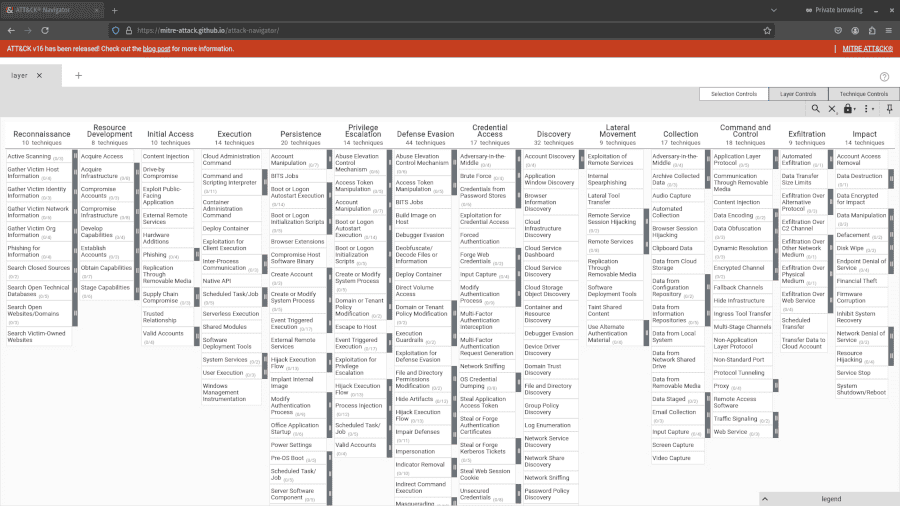
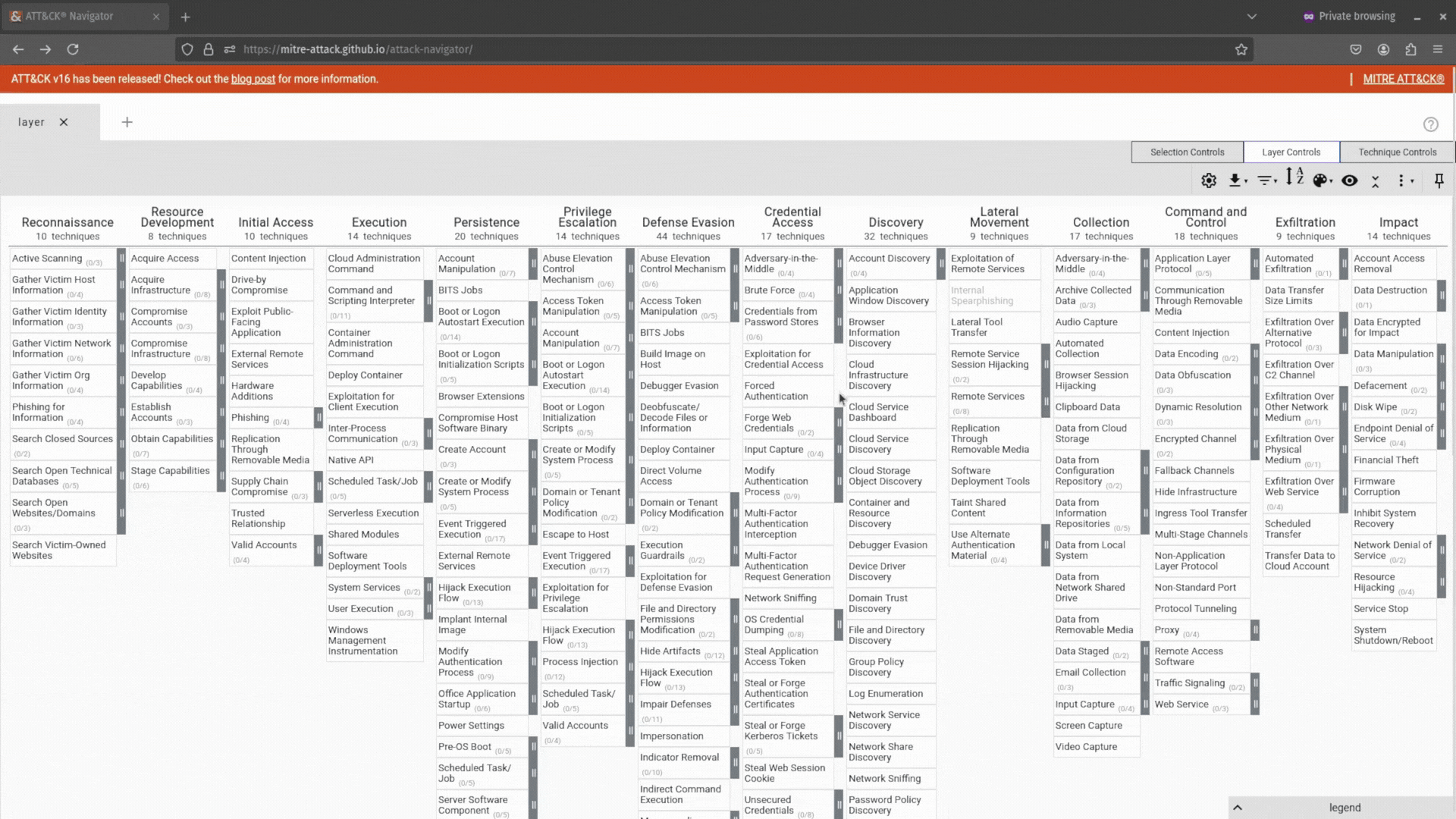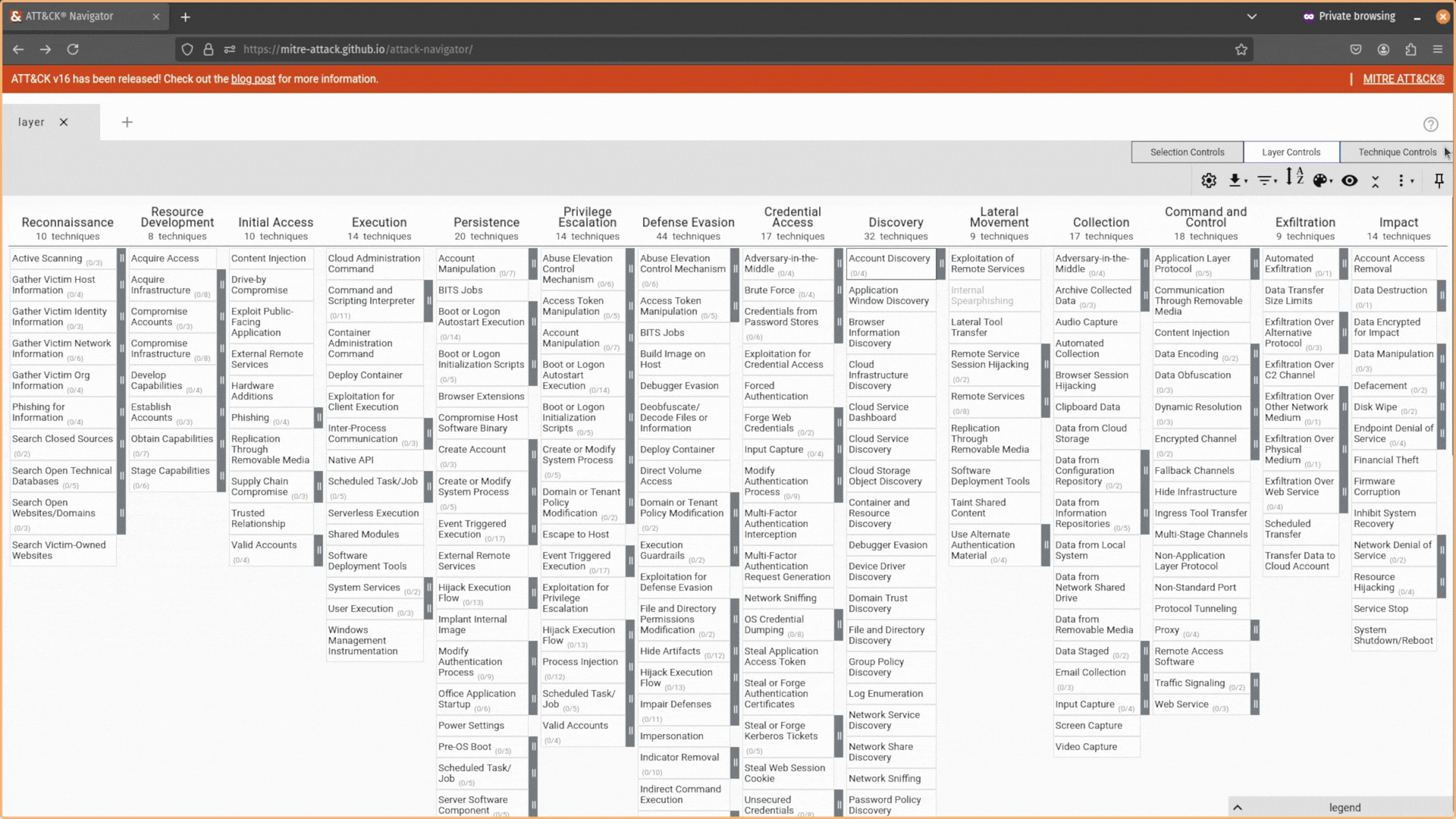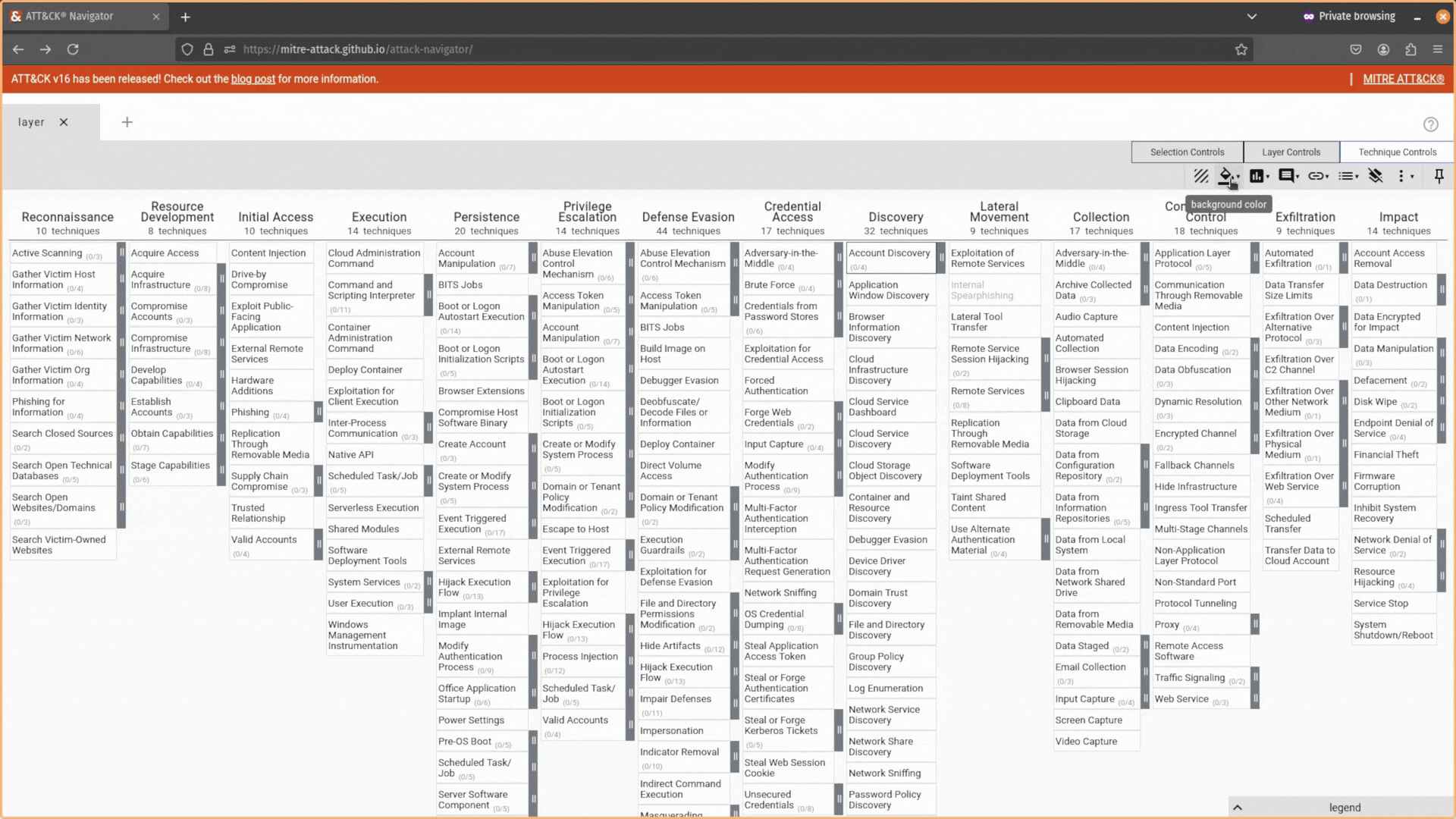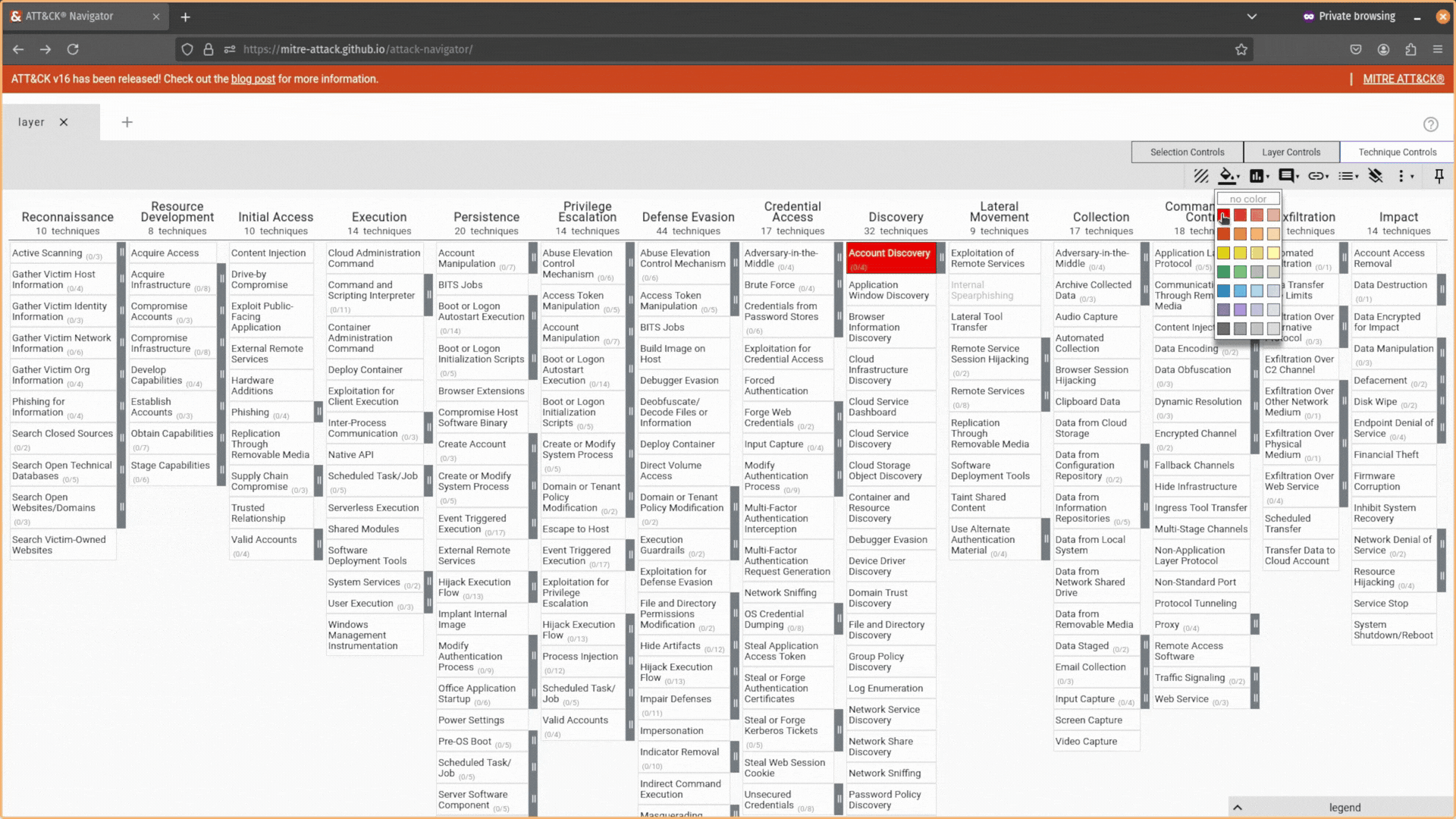
Now, the fun part! You can start interacting with your ATT&CK Navigator layer. Select a technique you want to highlight by clicking on it, navigate to the Technique Controls tab, and then use the background color tool to change its color.
Hold down the <ctrl> key and click away if you want to highlight several techniques.

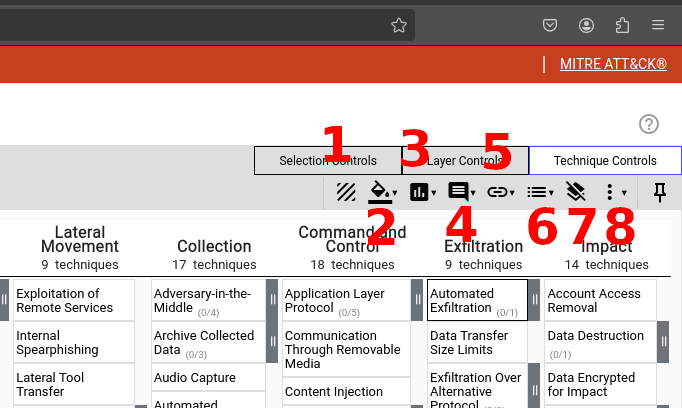
That said, there is considerably more you can do than simply highlighting using the Technique Control tab:
- You can enable or disable a technique in your layer using the toggle state button (1).
- Fill the technique’s cell with a specific color (2)
- Add a numerical score to a technique with the scoring dropdown (3).
- Annotated a technique with a comment using the comment dropdown (4).
- Attach a link to a technique with the link option (5). For instance, you could add a cyber threat intelligence report detailing the procedure seen to perform that technique.
- Add metadata to a technique (6), clear all annotations (7), or change what is displayed in your ATT&CK Navigator layer (8).
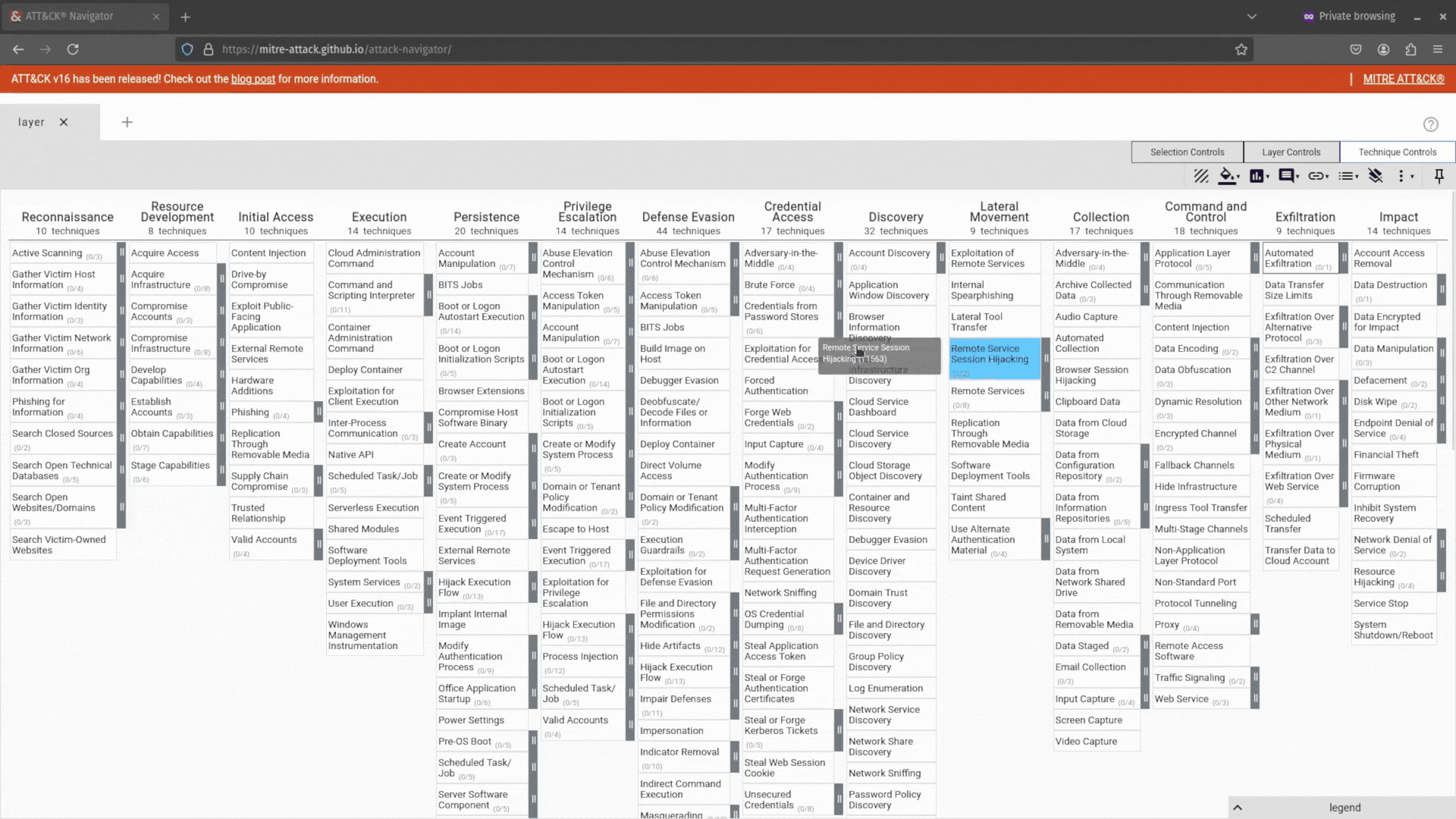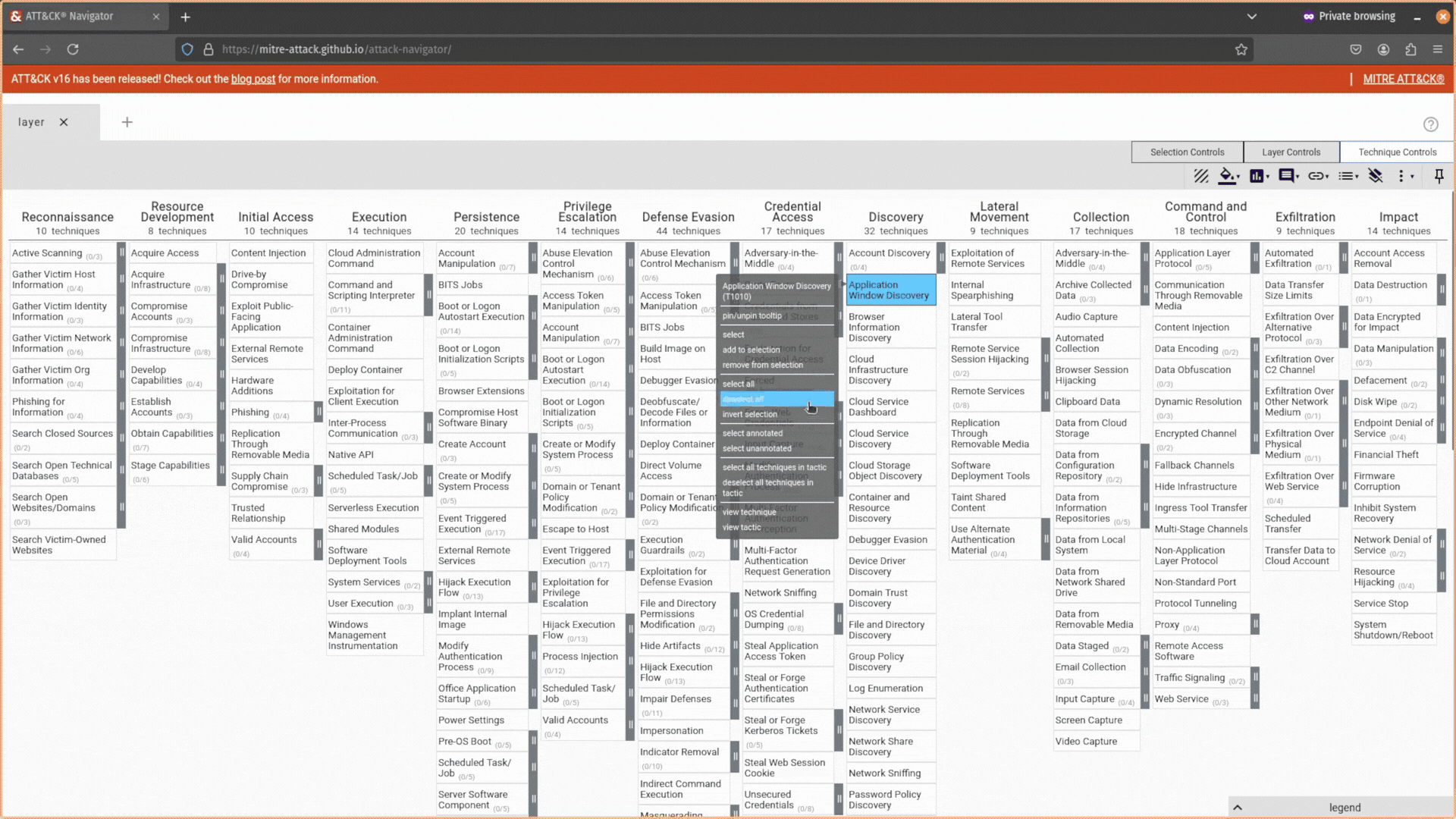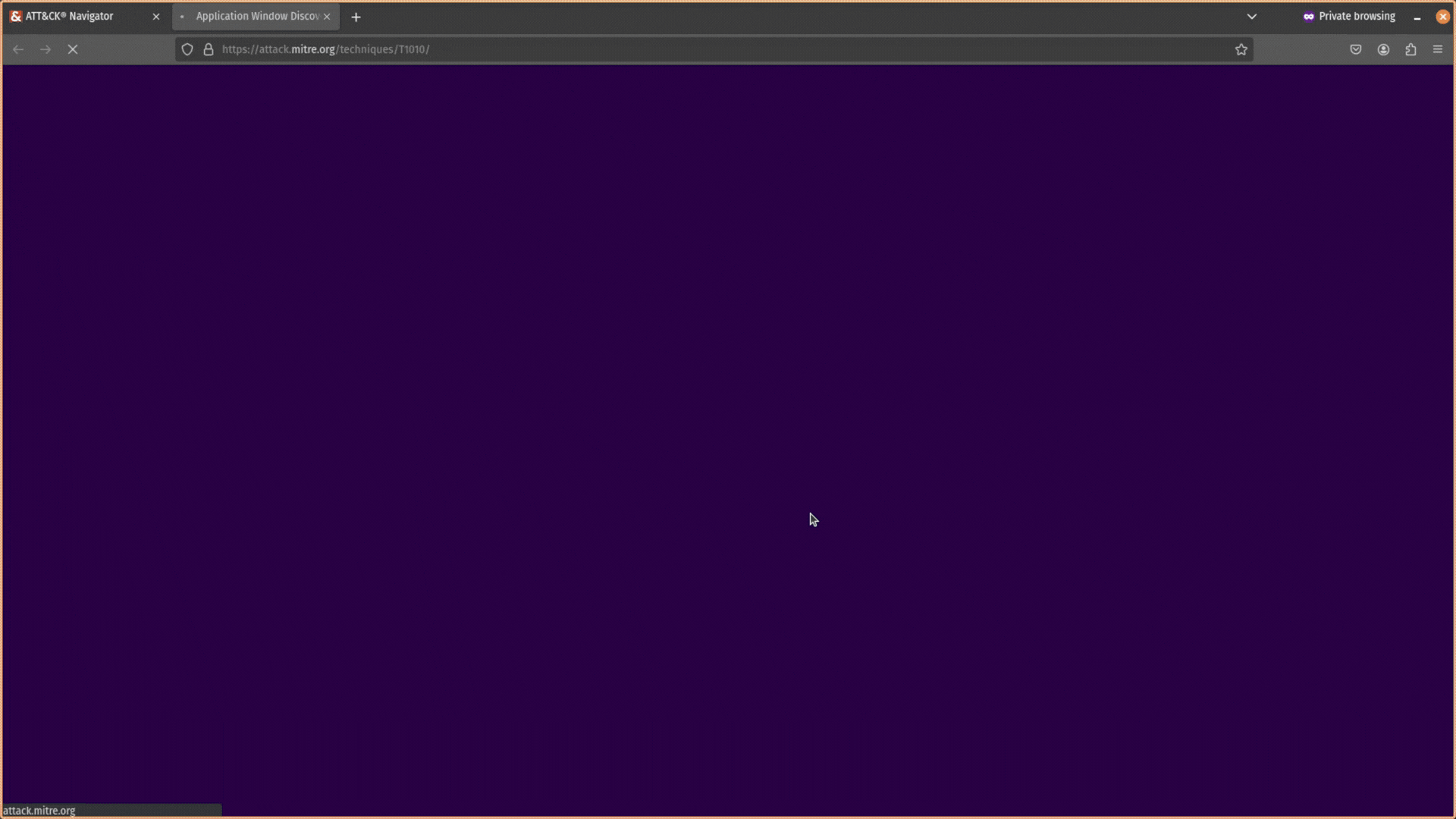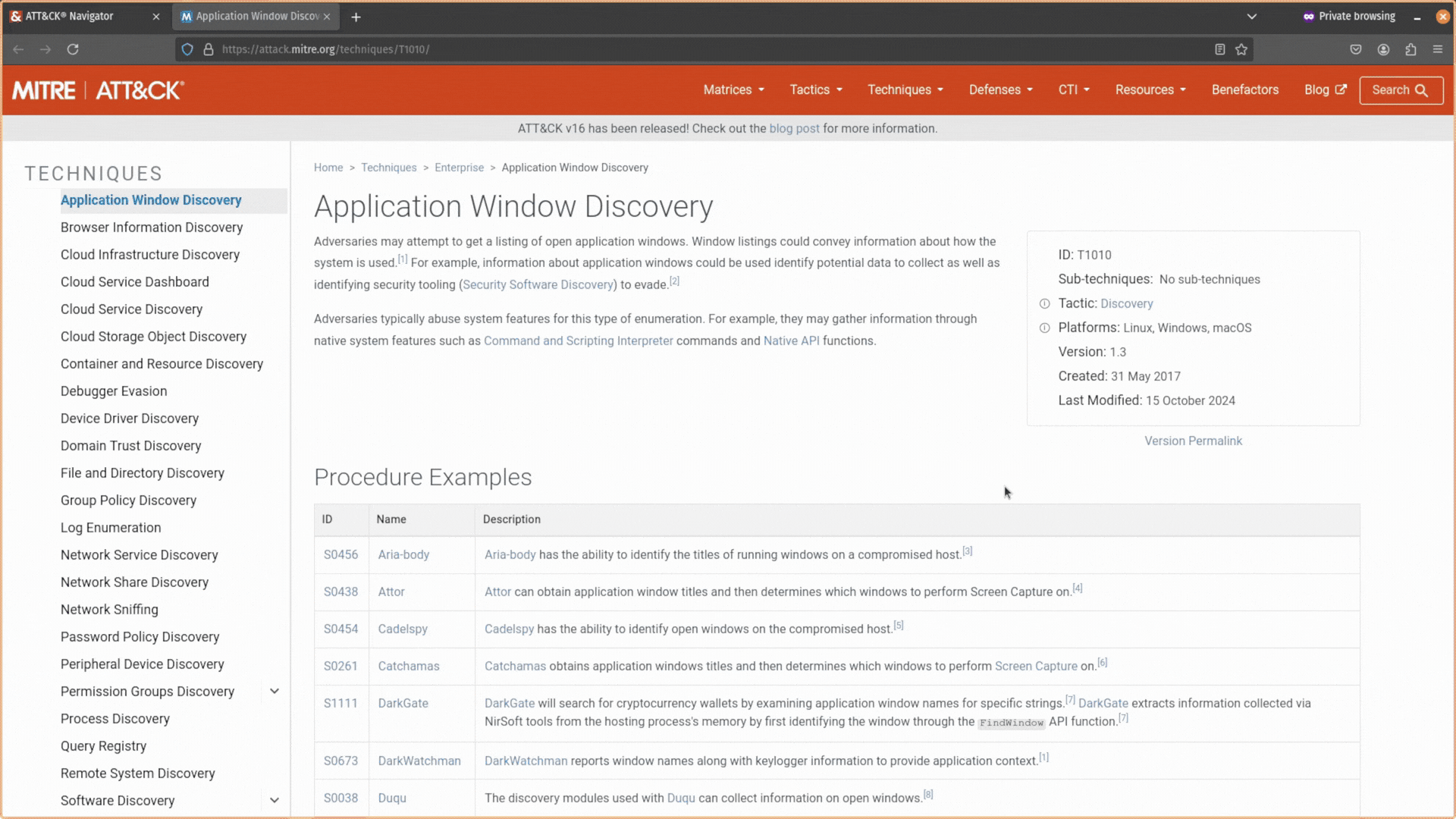
But what if you don’t know a certain tactic or technique and want to do some research before selecting it? Easy. Just right-click on it and select view technique or view tactic, and you will be taken to it in a new tab.
That’s great, but I want to do things a bit quicker and a bit more efficiently. Can I type attack techniques into the tool and select them that way? Well, my keyboard-bashing friend, of course!
Head to the Selection Controls tab and use the select & multiselect option.
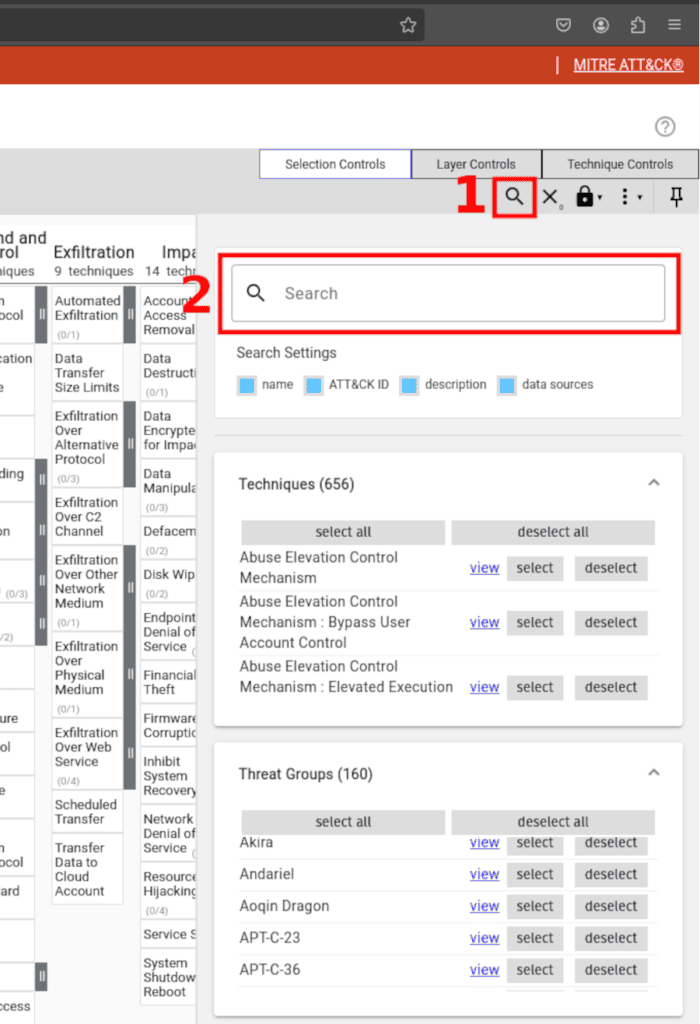
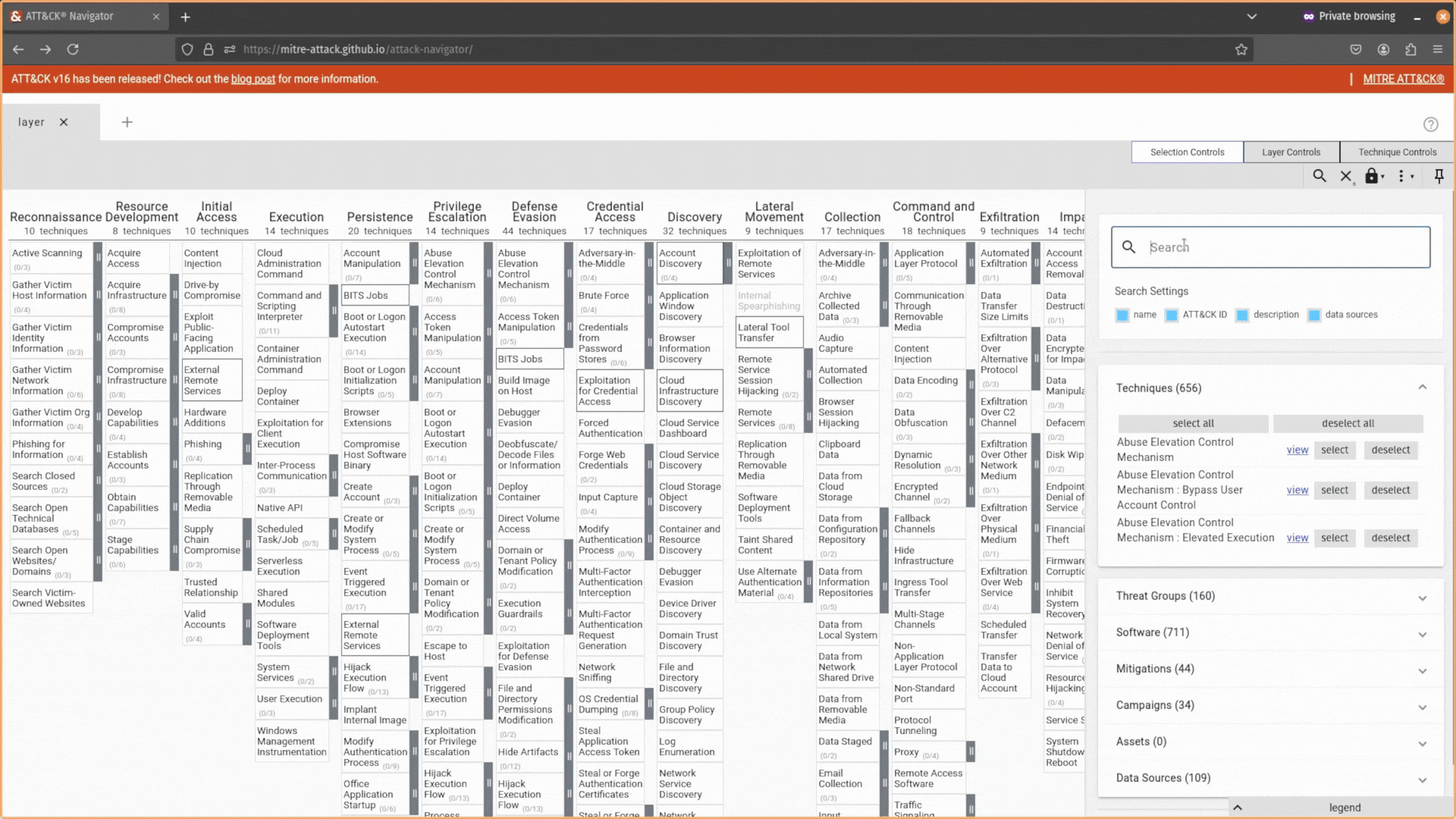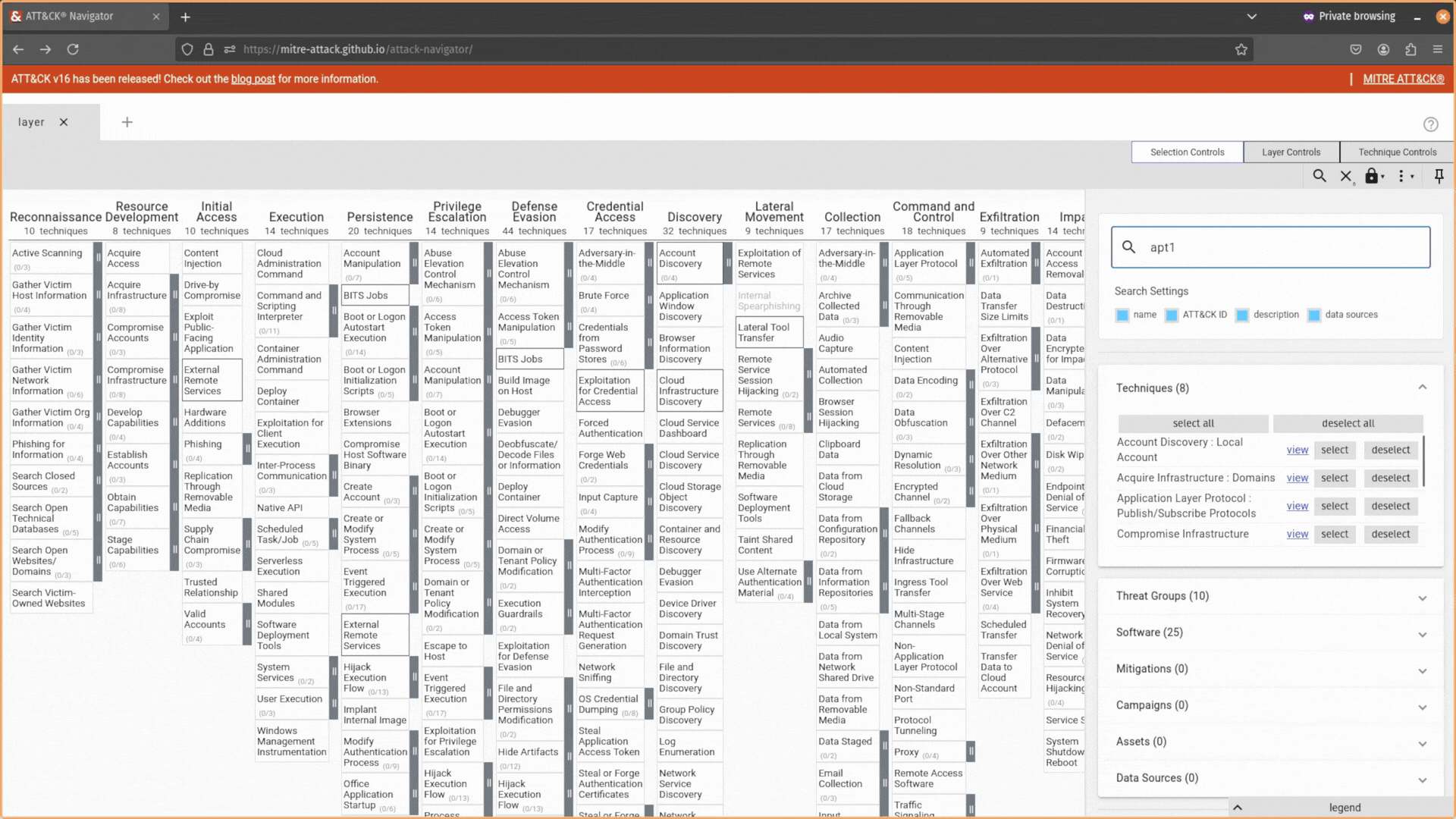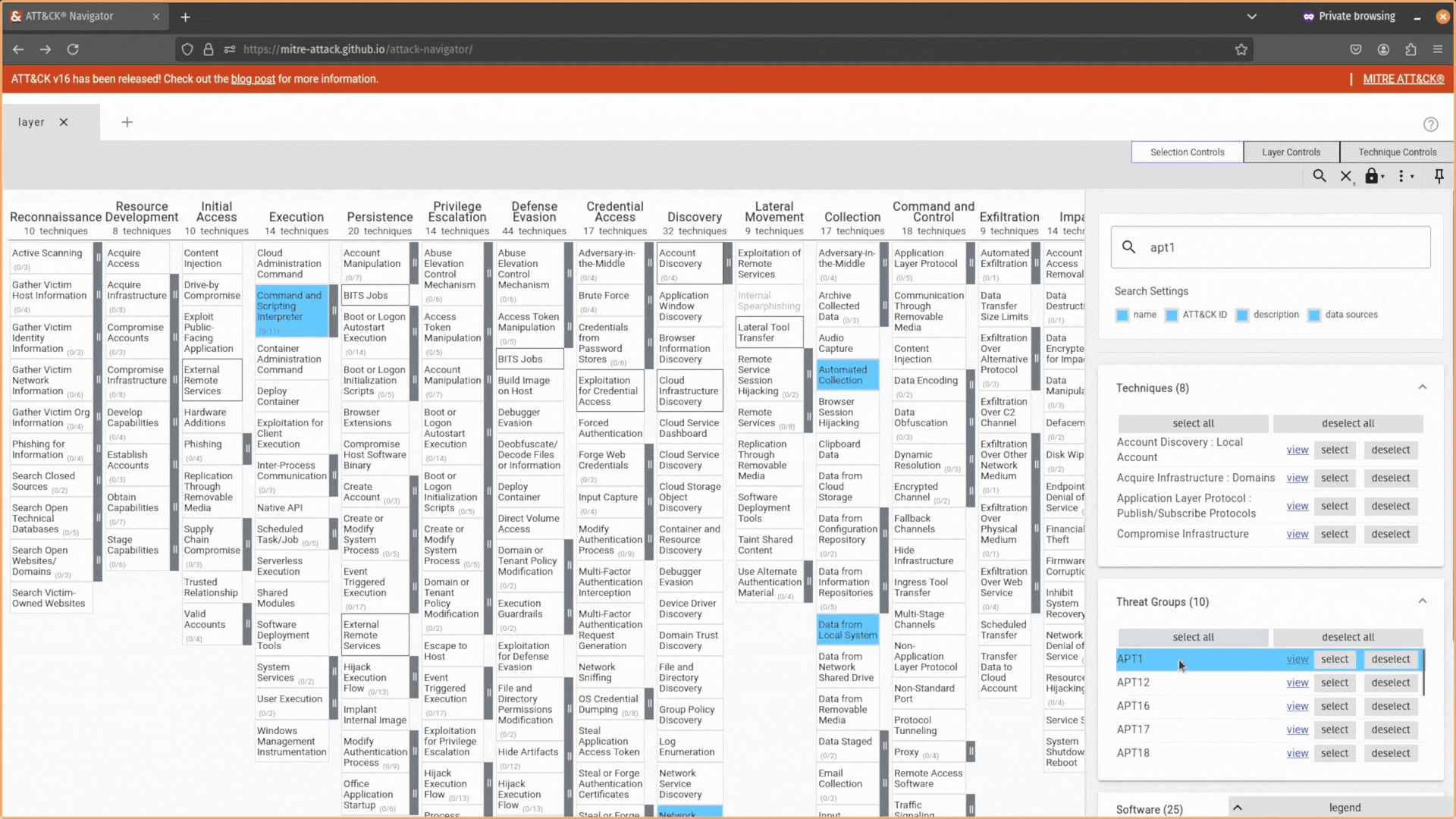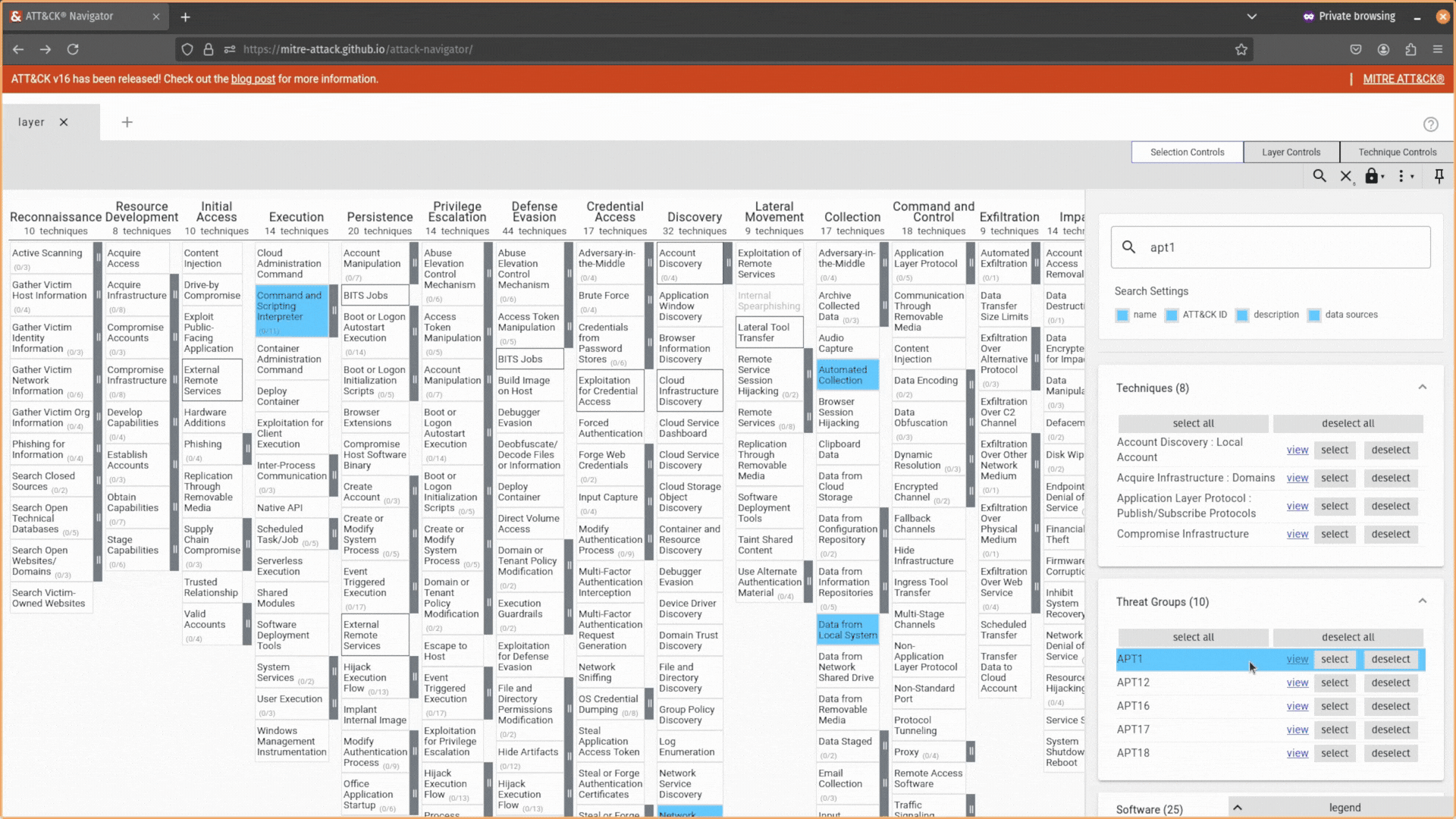
Here, you can search for attack techniques, IDs, threat actors, software, mitigations, campaigns, and data sources, and the ATT&CK Navigator will allow you to select (or deselect) them in your layer automatically.
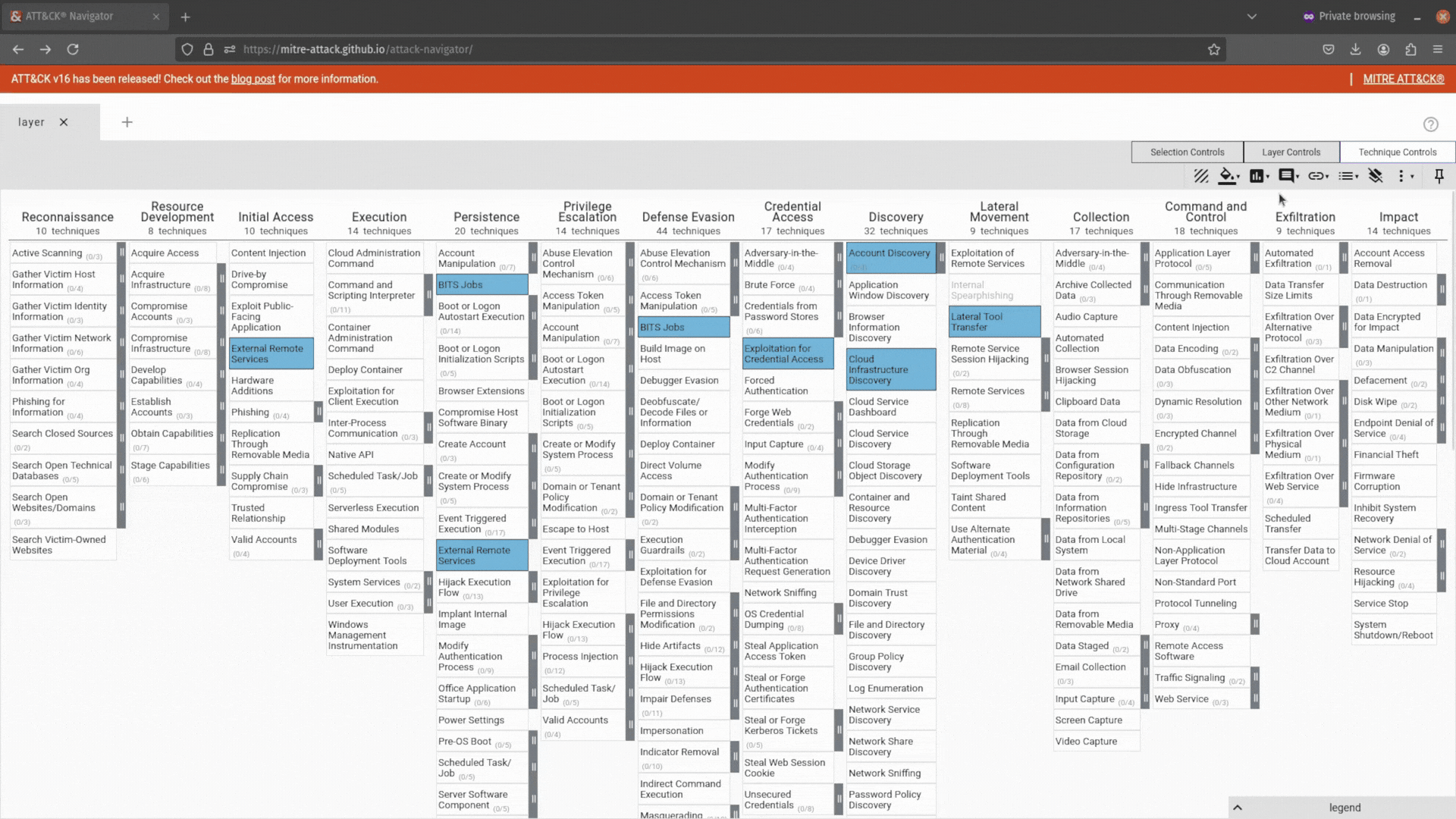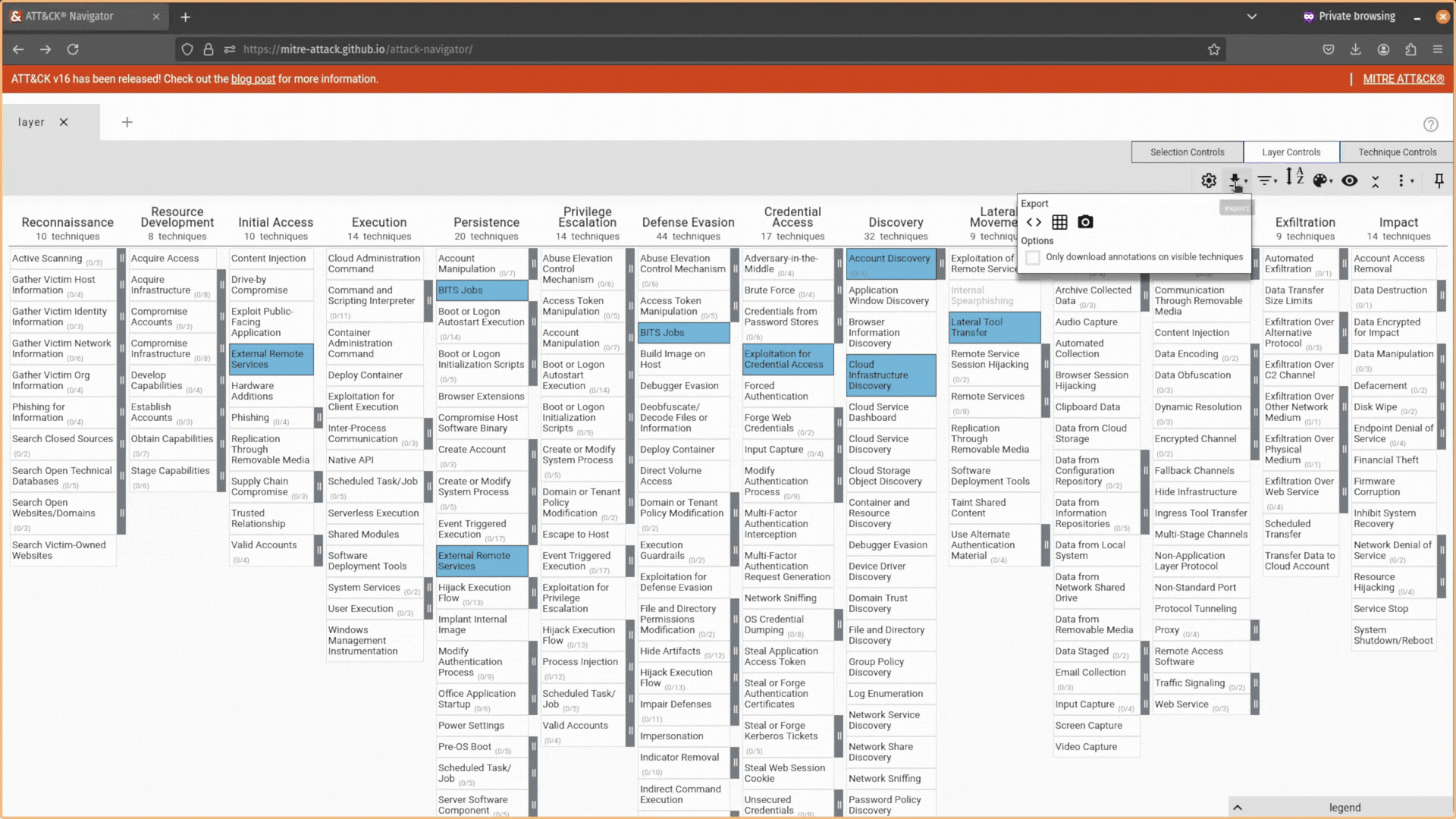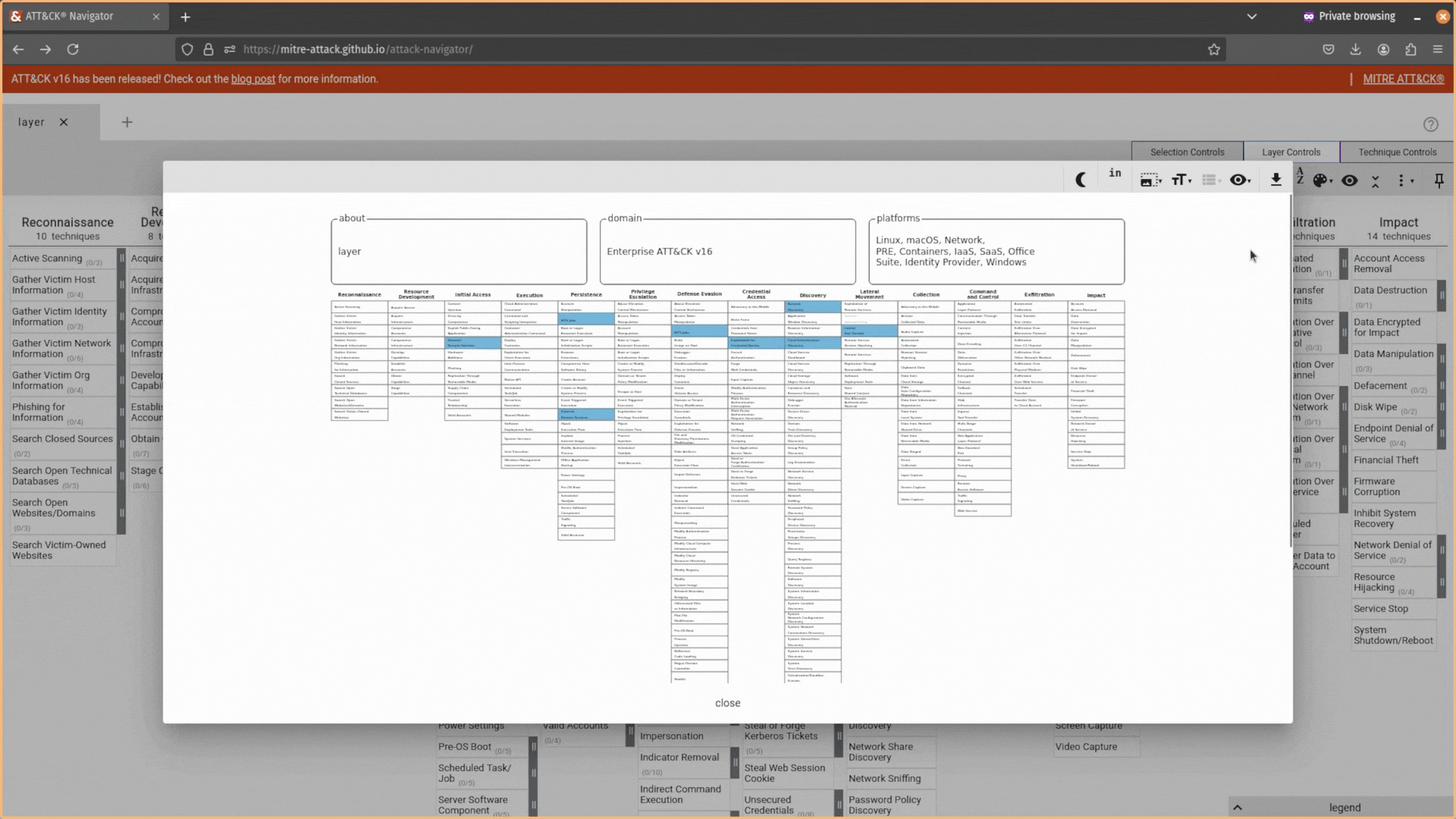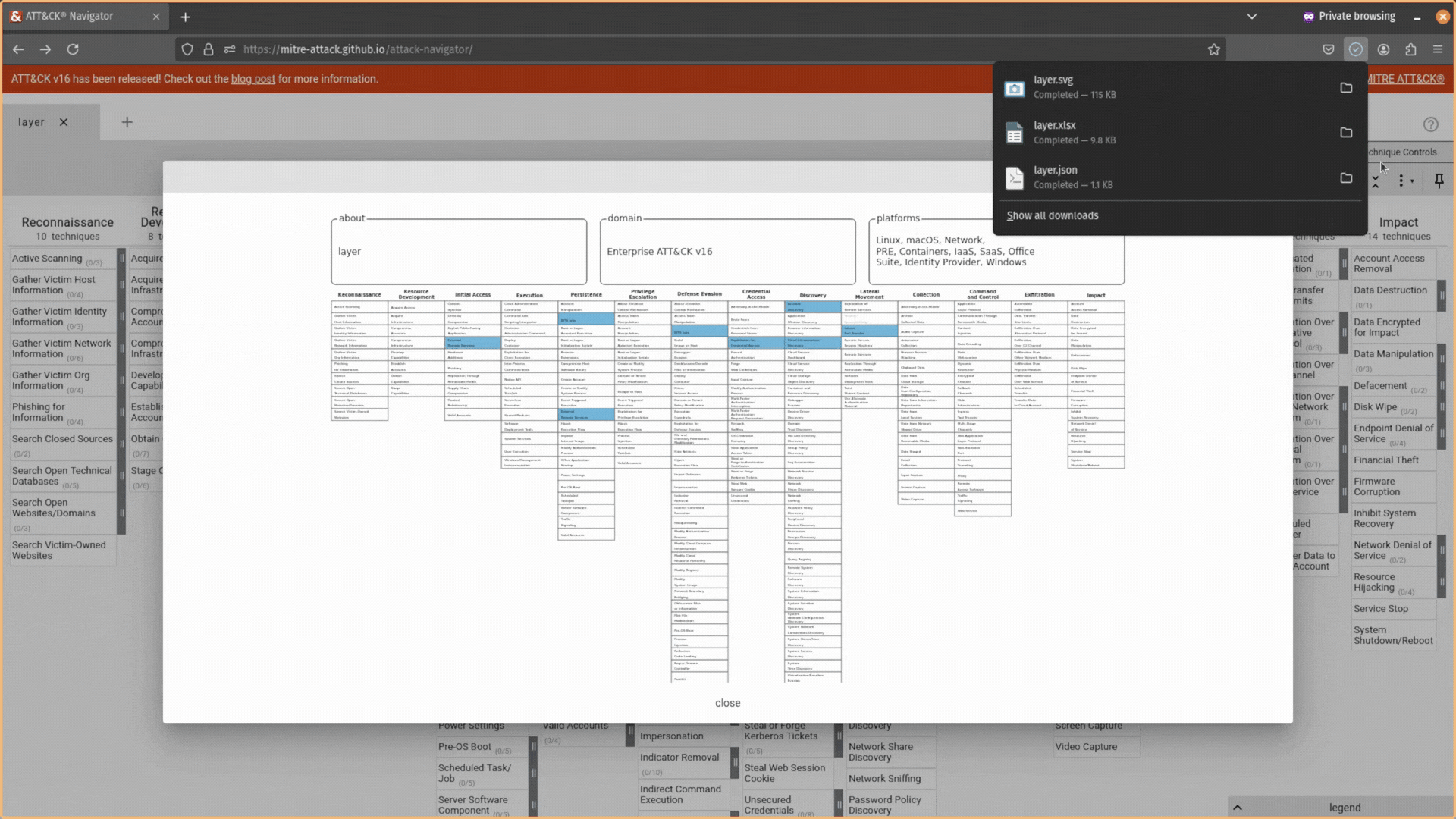
Cool stuff, but how about when I’m done making my selections and annotations? Well, then you can head over to the Layer Controls tab and export your selections as a JSON file you can load back into the tool (1), an Excel spreadsheet you can share with executives (2), or as a pretty SVG image to add to your report (3).
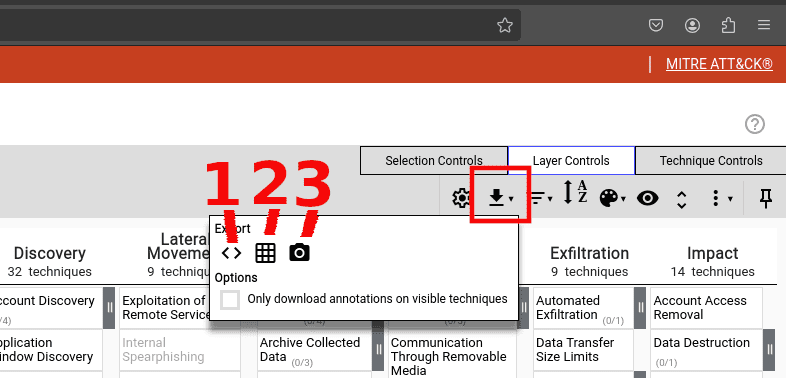
You can also use the Layer Control tab to change your layer’s settings, add filters (e.g., only attack techniques that apply to Windows machines), expand sub-techniques, and more.
That’s some cool functionality, but there are tons more to explore, and I highly recommend giving it a go. Let’s see how you can run the ATT&CK Navigator on your own machine.
ATT&CK Navigator Local Install
Using the public ATT&CK Navigator web application is easy and convenient. But this is a powerful tool you may want to run in your own organization where you can keep your data to yourself and build additional tools or processes around it. To accommodate for this, the fine folks at MITRE ATT&CK have open-sourced the project so you can run it locally.
To do this, install Docker on the machine you want to run the ATT&CK Navigator on (follow this guide) and clone the GitHub project to your installation location with the command git clone https://github.com/mitre-attack/attack-navigator.git.
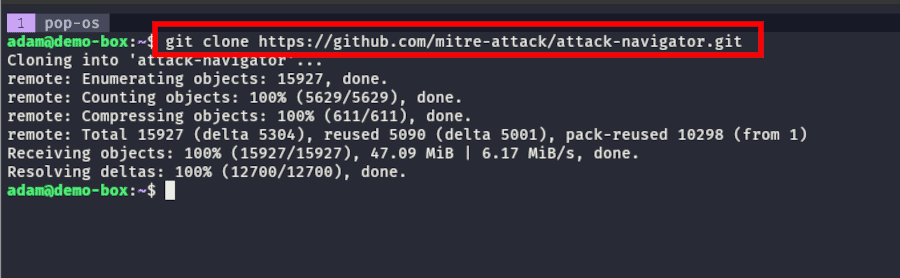
Next, cd into this directory and run the following commands to build a Docker image:
- Run
docker build -t <yourcustomname> .to build the image.
- Run
docker run -p 4200:4200 <yourcustomname>to start the image.
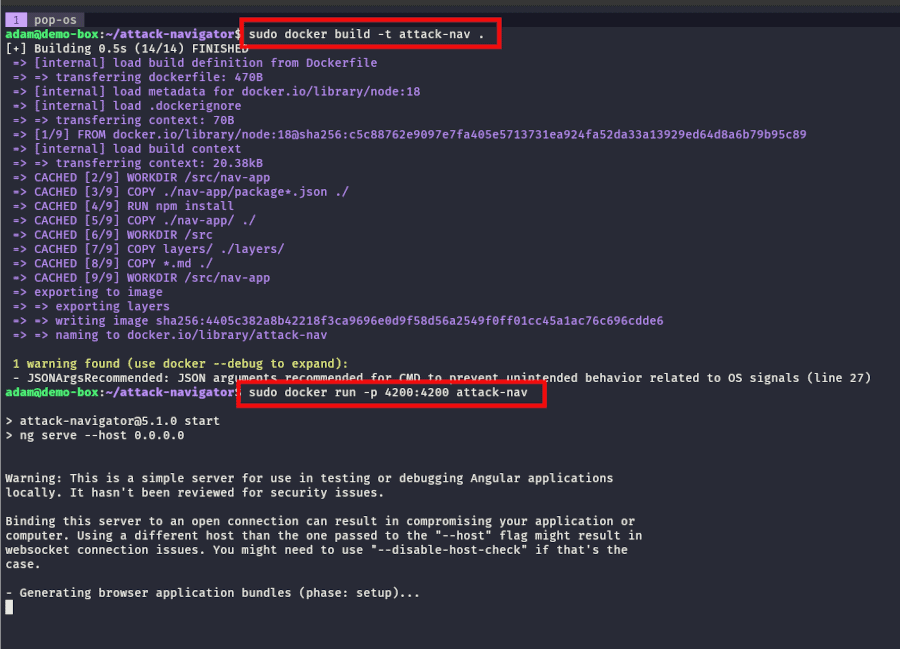
Now, navigate to http://localhost:4200 using your web browser to access the ATT&CK Navigator web GUI.
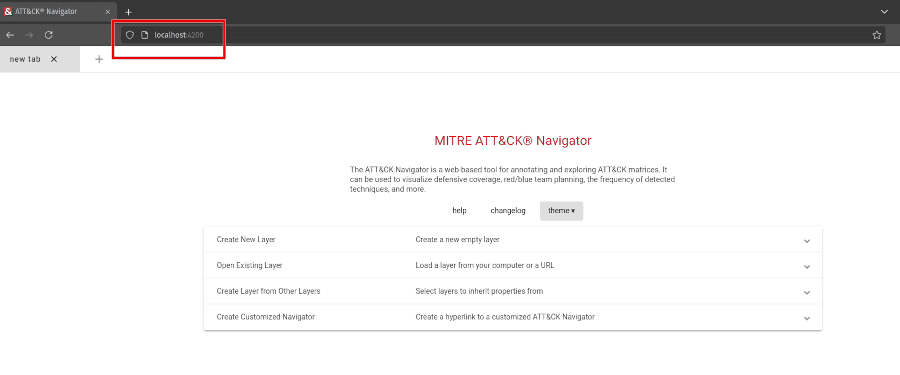
Nice, the docker image is up and running. The tool is the same as the one hosted on the public GitHub Pages website with the same features and functionality ready for you to use.
You can also use the Node Package Manager (NPM) and the Angular CLI to run the project, but Docker is a lot easier, trust me.
Now you know the basics of the ATT&CK Navigator, let’s look at some of the main ways you can use the ATT&CK Navigator.
Use Cases for the ATT&CK Navigator
The ATT&CK Navigator is a versatile tool that can be used across your security teams. Anyone who uses the MITRE ATT&CK framework can benefit from individual contributors in your security operations team planning technical controls to your security managers creating visual reports for executives.
Here are some ways you can use the tool.
Cyber Threat Intelligence
Cyber threat intelligence (CTI) teams can map specific threat actor behaviors to techniques in the ATT&CK matrix based on threat intelligence reports or internal data. This allows them to better understand an adversary’s tactics, techniques, and procedures (TTPs), allowing them to:
- Better fulfill intelligence requirements.
- Generate more engaging reports and assessments.
- Tailor their detection and defense mechanisms against specific threats
Everyone enjoys visualizations in reports!
Threat Hunting
Threat hunters can use the ATT&CK Navigator to plan and track their hunts by marking which techniques are the focus of their current investigation. They can use annotation features like color coding, comments, or numerical values to document and structure their processes, ensuring critical techniques are considered and tracked during hunts.
For instance, they assign a color or numerical value to techniques they have automated threat hunts running for, another for ones they are currently working on, and a third for attack techniques that are not a priority (or exclude these techniques using a filter). They could then timestamp their coverage over the month and show a nice visualization of how they have expanded coverage regarding reporting.
Security Operations
The ATT&CK Navigator is a very useful tool for your security operations team. They can use it for a range of technical and non-technical use cases.
- They can use it to perform gap analysis, where you overlay your current security controls onto the ATT&CK matrix to identify gaps in coverage. This helps to prioritize security improvements and investments by showing which techniques are not well-detected or mitigated.
- It can be used to assess your organization’s attack surface by analyzing which techniques are most used in attacks against a specific industry or organization type. This provides insights into the most likely attack paths your organization will need to combat and helps in hardening defenses against industry-specific threats.
- The team can use it to visualize the effectiveness of your security controls (e.g., SIEM, EDR, NDR) against different ATT&CK techniques by creating a heatmap of detected vs. undetected techniques based on SIEM log analysis. This offers a clear picture of where security controls are strong or weak, enabling more effective resource allocation.
- Those responsible for compliance can use the ATT&CK Navigator to align their defenses with specific compliance frameworks (e.g., NIST, PCI DSS) by mapping relevant ATT&CK techniques. This helps demonstrate compliance efforts and supports audit and reporting requirements.
- Those responsible for security architecture (or detection engineering) can use the ATT&CK Navigator to develop a comprehensive threat detection strategy that aligns with known adversary behaviors, ensuring detection capabilities are focused on the most relevant techniques and improving the organization’s overall security posture.
These are just a few ways the ATT&CK Navigator can be used. Try thinking of how you can apply it to your field of expertise.
Red Team / Purple Team / Adversary Emulation
It’s not just the blue team that can use the ATT&CK Navigator. Red teams can build attack plans, emulate specific threat actor behaviors, collaborate with the blue team, and develop purple team exercises using the Navigator as a guide or development.
This ensures that the attack techniques being tested align with realistic and known threat behaviors, making the assessment more relevant and identifying areas where the blue team needs to improve detection or response capabilities.
For example, you could use the ATT&CK Navigator to plan out a simulation of ransomware tactics, select specific techniques used by known ransomware groups, or emulate a particular threat actor known to target your organization’s industry. Then, during a purple team exercise, you can mark successful and missed detections during the simulated attack scenario.
Training and Awareness
The ATT&CK Navigator doesn’t just have to be for day-to-day cyber security work. It can also be used as an educational tool to train security teams on different attack techniques and their mitigations or raise awareness among non-technical stakeholders.
The ATT&CK Navigator allows you to develop learning exercises, create infographics, and help others become familiar with the tactics and techniques used by adversaries.
If everyone knows how a cyber attack happens, everyone can get involved in helping stop it.
Conclusion
The ATT&CK Navigator is a powerful tool. It allows you to visualize, annotate, and work with the MITRE ATT&CK Framework through a user-friendly. You can map and analyze attack techniques, plan red team exercises, and generate visualizations of attacks for your reports.
This guide has shown you how to get up and running with the tool using the beginner-friendly web interface if you use the tool on an ad-hoc basis and how to run the ATT&CK Navigator locally using Docker. You’ve also seen its powerful features like color coding, annotation, and export options. Now it’s time for you to get your hands dirty.
Play around with the ATT&CK Navigator in your own web browser, see what additional functionality it offers or what use cases you can find for it, and (if you’re brave enough) try running it locally.
Good luck!
Frequently Asked Questions
What is the ATT&CK Navigator?
The ATT&CK Navigator is an interactive tool developed by MITRE to help cyber security analysts visualize, annotate, and work with the MITRE ATT&CK Framework in a user-friendly. You can map and analyze attack techniques, plan penetration tests or red team exercises, and generate visualizations of attacks for your reports.
You can run the tool locally by downloading it from GitHub or accessing it via the GitHub Pages website.
What is MITRE ATT&CK Used For?
MITRE ATT&CK (Adversarial Tactics, Techniques, and Common Knowledge) is a comprehensive knowledge base of adversary tactics, techniques, and procedures (TTPs). It describes how hackers perform cyber attacks based on real-world observations.
You can use it to identify and categorize adversary behavior, map threat actor behavior seen during a cyber attack, perform a gap analysis to determine where you lack defensive coverage, help emulate an attack, or use a common language when discussing cyber threats.
Is MITRE ATT&CK Navigator Free?
Yes. The MITRE ATT&CK Navigator is an open-source project you can use for free. You can choose to access it through the GitHub Pages website (https://mitre-attack.github.io/attack-navigator/) or by downloading from the project on GitHub (https://github.com/mitre-attack/attack-navigator). If you decide to download the project, you can run it as a JavaScript NPM package or use Docker.
Who Created the ATT&CK Navigator?
The ATT&CK Navigator was created by MITRE Corporation, a not-for-profit organization that operates federally funded research and development centers (FFRDCs) in the United States. The tool was developed to extend the popular MITRE ATT&CK framework and other tools like the ATT&CK Powered Suit.