Triaging the Week 012

Big bounty offered for ransomware leaders, malware gets more sophisticated, and a critical vulnerability in Zoom in triaging the week 012.
We use cookies to help you navigate efficiently and perform certain functions. You will find detailed information about all cookies under each consent category below.
The cookies that are categorized as "Necessary" are stored on your browser as they are essential for enabling the basic functionalities of the site. ...
Necessary cookies are required to enable the basic features of this site, such as providing secure log-in or adjusting your consent preferences. These cookies do not store any personally identifiable data.
Functional cookies help perform certain functionalities like sharing the content of the website on social media platforms, collecting feedback, and other third-party features.
Analytical cookies are used to understand how visitors interact with the website. These cookies help provide information on metrics such as the number of visitors, bounce rate, traffic source, etc.
Performance cookies are used to understand and analyze the key performance indexes of the website which helps in delivering a better user experience for the visitors.
Advertisement cookies are used to provide visitors with customized advertisements based on the pages you visited previously and to analyze the effectiveness of the ad campaigns.

Big bounty offered for ransomware leaders, malware gets more sophisticated, and a critical vulnerability in Zoom in triaging the week 012.
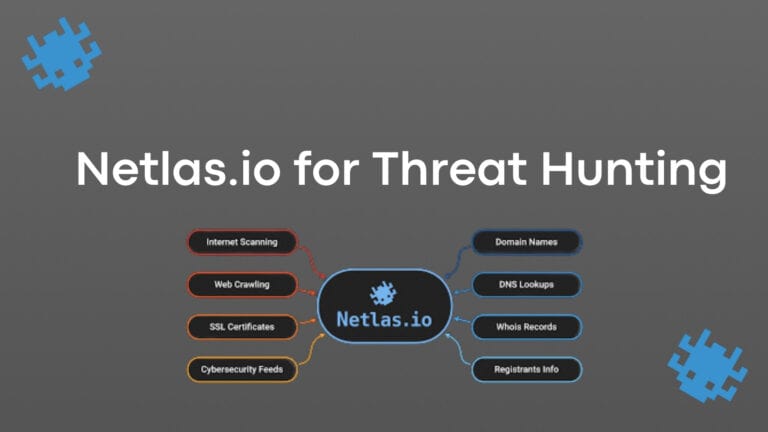
Discover netlas.io, a powerful suite of tools to enrich your threat hunts, add threat intelligence to your investigations, Discover netlas.io, a powerful suite of tools to enrich your threat hunts, add threat intelligence to your investigations, and map your attack surface.

New container escape, malware spreads with Facebook ads, and toothbrushes fight back in triaging the week 011.

Discover the top 5 threat intelligence lifecycle challenges you will face and how to overcome them to produce actionable intelligence.

NSA steals data, Mercedes fumbles GitHub tokens, and the police hit the Bitcoin jackpot in triaging the week 010.
Learn why malware configuration parsing is an essential skill for any threat hunter, plus how to use a malware configuration parsers to do this automatically.

Malware abuses Discord, Australia imposes sanctions, and the Uber of cybercrime is revealed in triaging the week 009.
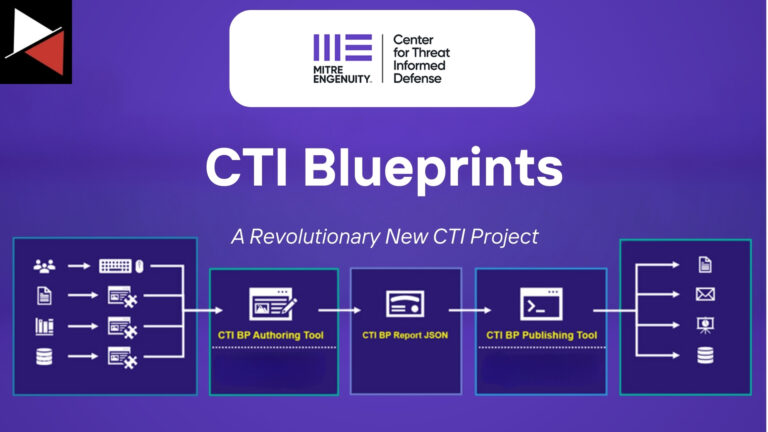
Learn about MITRE’s CTI Blueprints project. A revolutionary new CTI project that aims to help analysts deliver high-quality, standardized CTI reports.

New mitigations and with GrapheneOS and iShutdown scripts, top ransomware gangs to watch out for in 2024, and MacOS malware evades XProtect in triaging the week 008.

Discover the indicator lifecycle in this full guide on cyber security indicators. You will learn what indicators are and how to use them best.

DPKR steals all the crypto, X accounts are under siege, and China Cracks Apple’s AirDrop in triaging the week 007.

Learn about cyber threat intelligence requirements, why they are important, and how to create effective intelligence requirements in three simple steps.

Australian court hacked, a formal ban on ransomware incoming, and Mandiant X account hijacked in triaging the week 006.

Learn about the cyber threat intelligence lifecycle, the six stages of this fundamental model, and how you can use it in real-world security operations.

Hackers abuse GitHub, FBI takes major shot at ALPHV ransomware, and the Lapsus$ hacker gets sentenced in triaging the week 005.