-

YARA Rules: Empower Your Security With Custom Detections
Unlock the power of YARA rules and build your own custom detections. Learn how to write them effectively and use them in the real world with examples.
-
Analysis of Competing Hypotheses: How to Find Plausible Answers
This full guide will help you discover the power of the Analysis of Competing Hypotheses technique and learn how to analyze intelligence more efficiently.
-
The Diamond Model: Simple Intelligence-Driven Intrusion Analysis
Elevate your cyber threat intelligence analysis with the Diamond Model. This full guide will teach you everything to start using this analytical technique.
-

Top 5 Challenges With Indicators and How to Overcome Them
Discover the top five challenges with indicators (IOCs) and how to overcome them to improve the effectiveness of your cyber security operations.
-
How to Automatically Deploy a Malware Analysis Environment
Discover how to create your own automated malware analysis environment you can deploy in minutes by combining powerful technologies in this hands-on guide.
-

Threat Modeling: A Staple of Great Cyber Threat Intelligence
Learn what threat modeling is, why it is important, and how to perform using STRIDE, DREAD, PASTA, Attacks Trees, and VAST in this comprehensive guide.
-

How to Optimize Data Sources: Collection Management Framework
Discover the best way of collecting intelligence, a collection management framework. This guide will teach you what they are and how to create one.
-
The Cyber Kill Chain: How to Map and Analyze Cyber Attacks
Learn how to use the cyber kill chain. A fundamental framework for understanding cyber attacks, analyzing intrusions, and planning cyber defenses.
-

Top 5 Challenges When Creating Intelligence Requirements
Learn about the top 5 challenges when creating intelligence requirements and strategies you can use to overcome them in this guide.
-

How to Create a Local Kubernetes Cluster: Terraform and Ansible
Discover how to create your very own local Kubernetes cluster automatically using Terraform, Ansible, and the power of infrastructure as code (IaC).
-

Unraveling the Courses of Action Matrix: Full Guide to CoA
Learn about the Courses of Action matrix (CoA) and how it can help your organization accurately assess its defensive capabilities and improve resiliency.
-
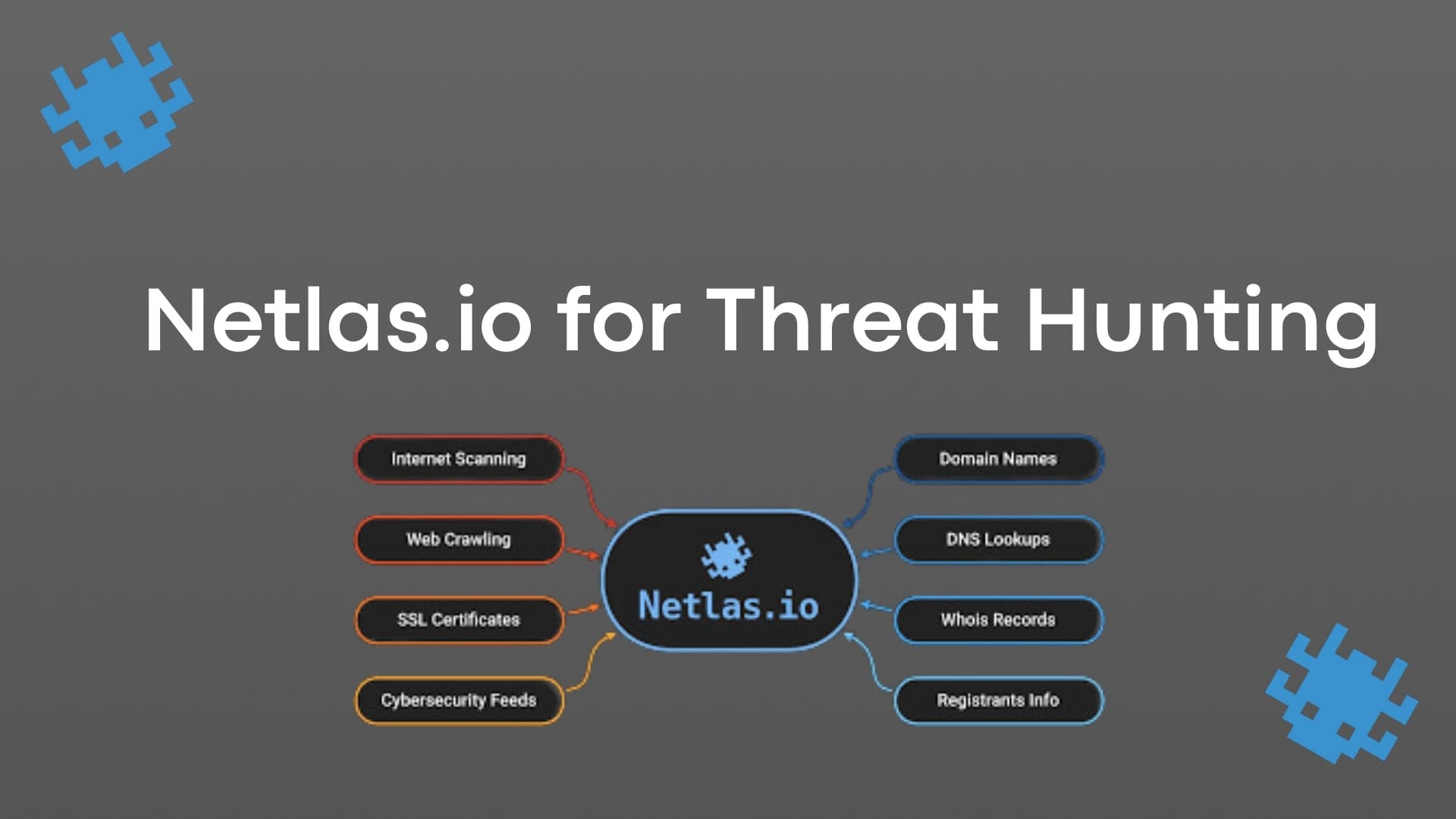
Netlas.io: A Powerful Suite of Tools for Threat Hunting
Discover netlas.io, a powerful suite of tools to enrich your threat hunts, add threat intelligence to your investigations, Discover netlas.io, a powerful suite of tools to enrich your threat hunts, add threat intelligence to your investigations, and map your attack surface.
-

Top 5 Cyber Threat Intelligence Lifecycle Challenges
Discover the top 5 threat intelligence lifecycle challenges you will face and how to overcome them to produce actionable intelligence.
-

Malware Configuration Parsers: An Essential Hunting Tool
Learn why malware configuration parsing is an essential skill for any threat hunter, plus how to use a malware configuration parsers to do this automatically.
-

Discover MITRE’s CTI Blueprints: A Revolutionary New Project
Learn about MITRE’s CTI Blueprints project. A revolutionary new CTI project that aims to help analysts deliver high-quality, standardized CTI reports.

Blog
