A cyber threat intelligence (CTI) project can be a difficult undertaking. There are many hurdles, roadblocks, and pitfalls that can derail your success. To combat these, you must dedicate time and effort to comprehensively planning your CTI project.
This guide will show you how to do this by walking through all the key documentation you need before you start intelligence work.
You will learn why CTI project planning is fundamental for success, the must-have documentation to create (and how this relates to the CTI lifecycle), and how to account for the unpredictable nature of intelligence collection. By the end, you will have the knowledge and tools to plan your next great work. Let’s get started!
CTI Project Planning 101
Cyber threat intelligence (CTI) can benefit various cyber security disciplines and business functions.
- The security operations team can use CTI to efficiently triage incidents, proactively defend against the latest threats, and perform threat hunting.
- The finance and fraud teams can use it to identify scammers and fraudulent transactions.
- The marketing and branding teams can use intelligence to spot impersonators, protect the brand image, and get ahead of negative press.
Unfortunately, this means planning a CTI project can be daunting. Where do you begin? What should you cover? How do you ensure you are delivering a quality CTI project?
This is where documentation can save the day. Documentation signposts what should be completed, what should be included, and what to expect from a CTI project. It is the pillar on which your CTI project is built, allowing you to meet consumer expectations and produce quality work.
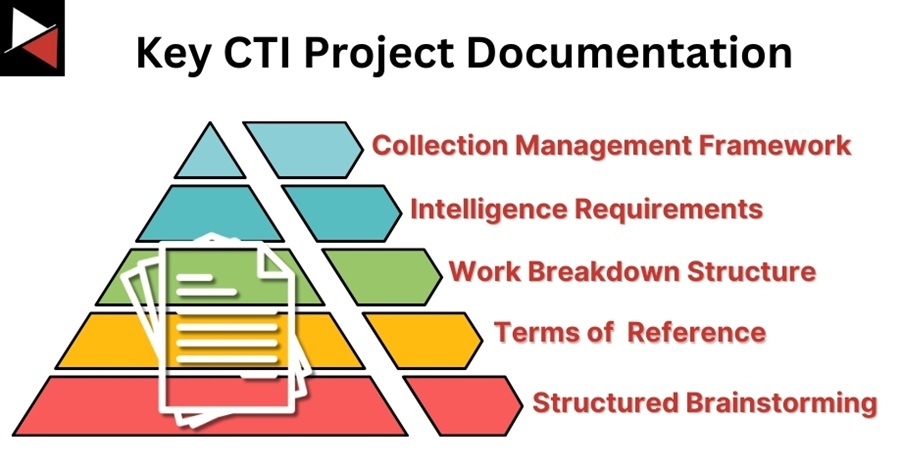
You can use these key pieces of documentation to guide you through the CTI project planning journey, from brainstorming to formal agreements with your customer. Let’s explore each key piece of documentation you need for a successful CTI project.
Structured Brainstorming
Once you’ve landed a CTI project (or been given one by your manager), you should start with a structured brainstorming session. These sessions are all about generating ideas.
- How can you solve the problem?
- What potential challenges might you face?
- What tools, data sources, and collection capabilities are available to you?
You want to involve your entire team in these sessions to help generate diverse ideas. Once you have a diverse range, you can then begin organizing these ideas into groups or categories and have your team vote on which ones to keep.
Your session should finish with a basic outline of how the project should proceed and data that can be used to create the other key pieces of documentation.
During these sessions, you can use other hypothesis generation techniques to help facilitate brainstorming. These include SWOT analysis, mind mapping, and environmental scanning (PESTLE).
Terms of Reference (ToR)
The first formal document your team needs to produce is the Terms of Reference (ToR). This puts the ideas you generated during your structured brainstorming into a written agreement you sign with your intelligence consumer. It defines the purpose and structure of your project for all involved.
A ToR will usually be organization-specific, including details relevant to the consumer you are working with and what they want to achieve. However, they will typically include the following sections.
Objectives and Deliverables
A section that defines the objective of the work and criteria for determining if this objective has been met at the end of the project. This section answers why you are doing the work, what problem you are trying to solve, and the project’s scope (what to include and exclude).
It will also list the acceptance criteria for the project’s success or completion and the client’s expectations. These expectations are usually formalized with an output structure or deliverables, including reports, meetings, reviews, milestones, and updates with a set date.
Key Stakeholders
All ToRs have a section that lists the key stakeholders involved in the project. This section answers who is doing the work, who is reviewing the work, and who the work is for to ensure people are held accountable and expectations are aligned.
During the planning stage, you can use a RACI matrix to help assign project responsibilities. This matrix clarifies the roles individuals or groups will play in the successful delivery of the project.
Resources
Another section ToRs have in common is the resources section. This is where you will list the resources that will be used to complete the project. These resources could be:
- Tools and technologies available to use.
- Data sources or collection capabilities the CTI team uses.
- A quality plan to ensure the work is satisfactory.
- Risk register to manage potential risks associated with the work.
The resources outlined will typically be project and team-specific. You will use the resources and deliverables you define in the ToR to create a project plan that breaks down the work required.
Work Breakdown Structure (WBS)
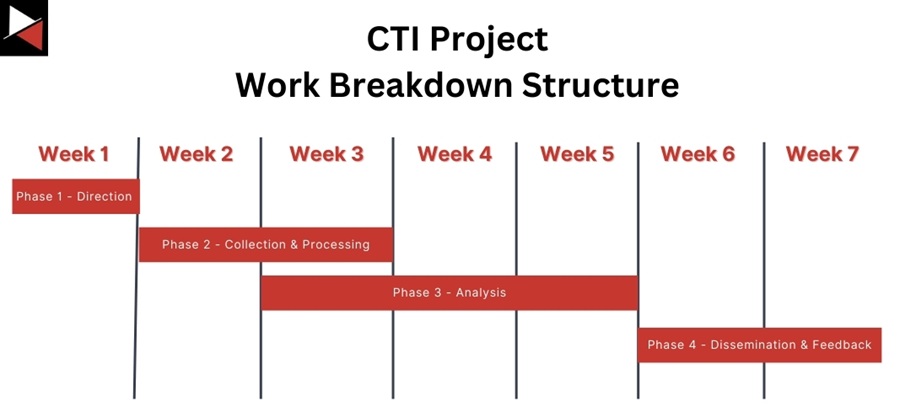
The ToR document will lead to the creation of a Work Breakdown Structure (WBS). This document plans how you will deliver the project and meet the success criteria defined in the ToR.
A WBS is broken down into phases mapped to a timeline. Each phase usually has one or more deliverables with a delivery date for the intelligence consumer. The successful completion of a deliverable (package of work) allows the project to progress (they are usually dependencies for other work) and the client to track this progress. Deliverables are included in the success criteria for a project.
In most projects, a WBS is straightforward to follow. However, in a CTI project, aligning the CTI lifecycle with a WBS can be challenging. Often, during CTI work, the collection and analysis stages overlap. You may complete the analysis of one data set and find that you must collect more. Therefore, you must consider this overlap in your WBS timeline.
For example, a WBS for a CTI project could be broken into four phases:
- Direction: You can cover this phase during the project scoping call with the client and your structured brainstorming session. You should be able to create a list of objectives to turn into intelligence requirements. The phase should end with delivering the ToR, WBS, and intelligence requirements to the consumer.
- Collection and Processing: This is where the real intelligence work begins. You must seek out data that will allow you to fulfill the intelligence requirements defined using various collection sources.
- Analysis: This phase should overlap with the collection and processing phase in your WBS. Often, you must revisit the collection phase after your initial analysis.
- Dissemination and Feedback: Once you share the intelligence product with your consumer, it is a good place to call the project closed. You should “pad” this phase with time to allow for a product draft, revisions, and quality assurance.
So, what should your intelligence requirements look like?
Intelligence Requirements
The intelligence requirements (IRs) you define for your CTI project come from the objectives, deliverables, and success criteria outlined in the ToR you signed with the client. They are a list of questions (or topics) that your CTI team must focus on answering.
IRs can come from the CTI teams themselves, the intelligence consumer, the industry verticals the consumer operates within (e.g., telecoms, shipping, transportation), or the nature of the organization itself (e.g., geolocation, politics, etc.). You must work with the intelligence consumer to create IRs that are relevant to them and that your team can realistically fulfill.
To learn more about IRs, read What Are Intelligence Requirements? A Comprehensive Guide.
Once you have a list of IRs, you must map them to a Collection Management Framework (CMF) or collection plan so you can track them and ensure they are fulfilled.
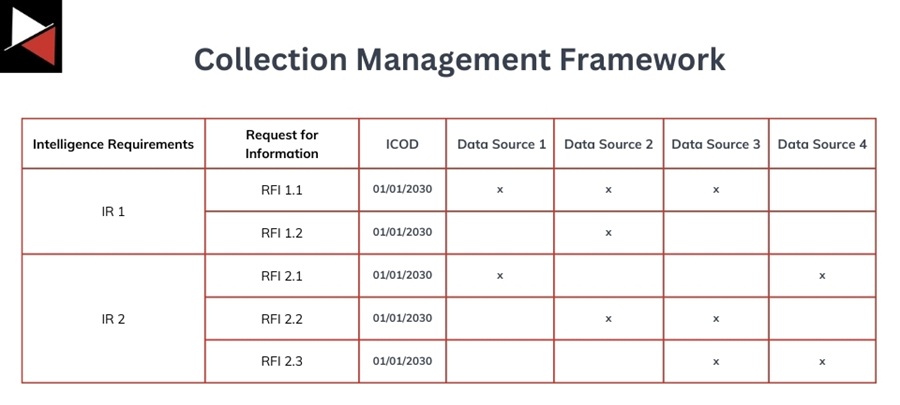
Collection Management Framework (CMF)
A CMF systematically tracks intelligence requirements by mapping each IR to a data source or collection capability that can be used to answer it.
You will typically break down an IR into smaller Request for Information (RFI) tasks that a CTI analyst can complete. Each IR may have multiple supporting RFIs that must be completed to fulfill it. Additionally, each RFI will have an Intelligence Cut-Off Date (ICOD) that determines when it is no longer useful for the intelligence consumer. You must deliver your intelligence product before this date.
Once your CMF is built, you can move on from the project planning stage. You have all the pieces in place to start your CTI project! But hold on. There are some important challenges of a CTI project you must account for before moving on.
CTI Project Planning Considerations
A CTI project has many components in common with a regular consulting project (e.g., ToR, WBS, etc.). However, there are some unique challenges you must account for, namely the unpredictability of data collection.
The collection phase of the CTI lifecycle can be unpredictable.
For instance, what do you do if you don’t get anything back from a data source? What happens if the data source cannot meet your project’s deadline? How can you account for these delays in your WBS? These challenges are exacerbated if you rely on human data sources (HUMINT) for collection!
These issues arise because data sources (or collection capabilities) are like fruit. You plant the seed, nurture it, and then pick the fruit during your CTI project. To do this, you must have these capabilities in place and mature them before you can use them for a project. The more mature these capabilities are, the more likely they will come through for you.
When planning your CTI project, you must account for these potential delays or lack of data and aim to set each collection capability up for success. You can do this by aligning the intelligence consumer’s expectations with the probability of successful collection.
- What are the chances that the collection will be successful?
- What can you do if you cannot collect from source X?
- Do you have a backup source?
- What are the success criteria for each of your collection capabilities, and is this written in the ToR?
- Can you account for your work even if you find nothing?
To make these questions easier to answer, you can create a matrix for your existing collection capabilities and assess them on how easy they are to manage and how responsive they are.
| Do you have access? | Trade or Skill? | Does it rely on a research program? |
|---|---|---|
| Yes or No. | A specialization outside of the CTI team (trade) or something you can do within the team. | Long-term strategic programs that develop insight into a research area (i.e., Russia, PRC, dark web). |
| Easy to manage. You buy access. | Managed through personal relationships and employee training. | The most unpredictable and challenging to manage. |
Using this matrix to assess each of your collection capabilities allows you to align customer expectations better and more accurately plan your CTI project.
Conclusion
A CTI project can be challenging. You must align objectives with your intelligence consumer’s expectations, produce a high-quality intelligence product in a timely manner, and navigate potential roadblocks like the unpredictability of data collection. Solving these challenges requires comprehensive project planning.
In this guide, you have seen how to perform CTI project planning by creating the five key pieces of documentation every CTI project needs.
- Structured brainstorming to generate ideas.
- Terms of Reference (ToR) to solidify those ideas and align with customer expectations.
- A Work Breakdown Structure (WBS) to map your CTI project to a timeline.
- Intelligence Requirements to turn objectives into requirements your CTI team can fulfill.
- A Collection Management Framework (CMF) will turn requirements into questions your CTI team can answer and map these to collection capabilities that will provide those answers.
Make sure you dedicate the time to plan your next CTI project and include these five key pieces of documentation. Good luck!
Frequently Asked Questions
What is a CTI Manager?
A CTI manager is a key role in any CTI team. They oversee the CTI function and ensure that the intelligence produced aligns with business and security objectives. They help facilitate the planning of CTI projects, ensure the intelligence produced is actionable, and act as a bridge between the CTI team and other security teams or other business units that could benefit from intelligence.
How to Plan a CTI Project?
You can plan a CTI project using five key documents:
- Structured Brainstorming: These sessions allow you to generate ideas for your CTI project, identify solutions, and navigate potential challenges. They help create an outline of how the project should proceed.
- Terms of Reference (ToR): This document formalizes the ideas you came up with during structured brainstorming. It includes the objectives and deliverables of the CTI project, the key stakeholders involved, and the resources to be used.
- Work Breakdown Structure (WBS): This document plans how you will deliver the project and meet the success criteria defined in the ToR using a timeline.
- Intelligence Requirements (IRs): The IRs you define for your CTI project come from the objectives, deliverables, and success criteria outlined in the ToR. These are what questions your CTI team will work to answer.
- Collection Management Framework (CMF): A CMF systematically tracks IRs by breaking down IRs into Request for Information (RFI) tasks and mapping each RFI to collection capabilities that can used to answer it.
What is Cyber Threat Intelligence?
Cyber threat intelligence (CTI) is a proactive approach to defending an organization against cyber threats. It involves collecting, analyzing, and disseminating intelligence about cyber threats and potential risks an organization will face.
CTI plays a crucial role across various cyber security jobs, from deeply technical ones like incident responders to key decision-makers like managers or directors. It can also be used by other business functions like fraud, marketing, branding, and executives to fill knowledge gaps.