There is a powerful new suite of tools for threat hunting and it’s called Netlas.io. This innovative platform allows you to hunt across a vast network dataset collected from across the globe. You can use this data to enrich your threat hunts, add additional threat intelligence to your investigations, and map the attack surface of adversaries.
In this article, you will discover what makes this platform so powerful and how to use it to perform link analysis that takes your threat hunts to the next level. Let’s jump in and get started by learning what Netlas.io actually is.
What is Netlas.io?
Netlas is a platform for discovering, researching, and monitoring your online assets. The platform scans every IPv4 address and crawls every website and application to generate a rich collection of network data about assets worldwide. It then makes this data available through the Netlas Search tools. Included in this toolset are:
- Host Search: A summary of public information about an IP address or domain.
- Attack Surface Discovery Tool: A graph-based tool that maps your target’s attack surface. Great for threat hunting and gaining insight into what an attacker can discover about your organization from the outside.
- Response Search: Scans a specific group of services or devices, such as IP cameras, IoT devices, databases, or web servers.
- DNS Search: Searches DNS data Netlas.io has collected from certificates, Whois records, and periodic scans.
- Whois IP and Domain Search: IP address and domain searches through a curated and carefully structured Whois database.
- Certificate Search: For searching SSL certificates collected from the Certificate Transparency Log and host responses during scans.
To effectively use these tools, the team at Netlas.io built a powerful search engine that allows you to build complex search queries using different conditions and operators to search through over 10,000 fields. The engine uses Elasticsearch on the backend to support wildcards, regexp, fuzzy, and proximity searches using the web interface or API, allowing you to pivot through data sets effortlessly.
That’s enough talk. Let’s see Netlas.io in action and discover why it is a powerful tool in your threat hunting arsenal!
Threat Hunting With the Netlas Tools
Threat hunting involves proactively searching for threats within your environment that have evaded traditional security tools, like anti-virus, EDR, and IDS. It tasks you with actively uncovering signs of suspicious or malicious activity using human-driven analysis, investigation, and intuition. To be effective, you need a tool that can rapidly enrich indicators you find with intelligence and help you discover new data points to search for.
This is where Netlas.io can be a game-changer. The tool allows you to write powerful search queries to investigate suspicious network indicators you find during your threat hunts, be it an IP address, domain name, or SSL certificate. Using the intelligence returned, you can pivot to new data points, dive deeper into your threat hunt, and complete the indicator lifecycle.
Let’s use a practical example to demonstrate this.
The Scenario
In your network logs, you see one of your endpoint machines connecting to a suspicious IP address you haven’t seen before. This prompts you to gather data about this network indicator and start a threat hunt.
You load up Netlas.io and navigate to the Attack Surface Discover Tool to start your visual link analysis.
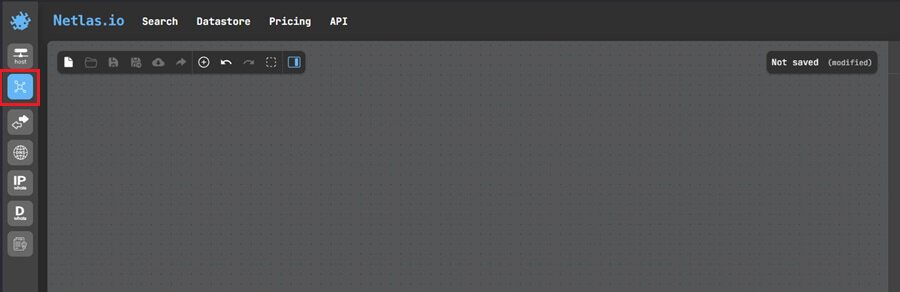
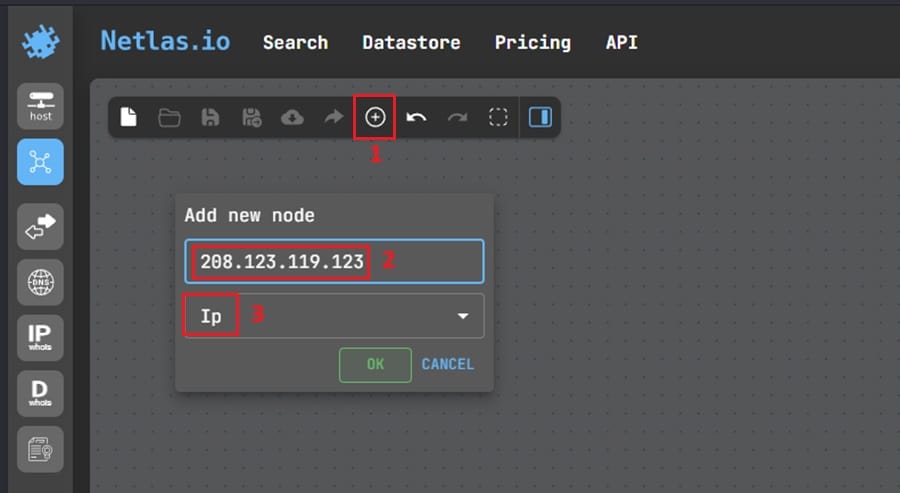
Next, you add the suspicious IP by selecting the Add Node icon from the toolbar at the top (1), entering the IP address (2), and selecting Ip from the dropdown menu (3).
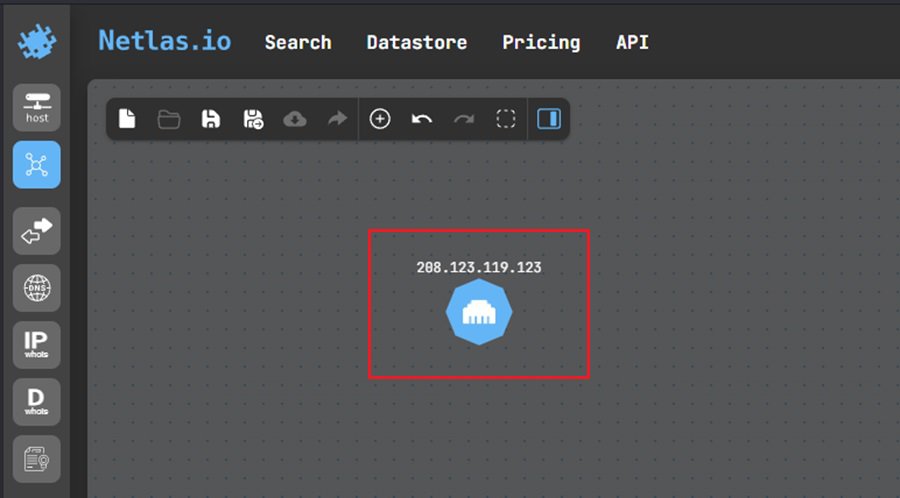
Once added, click on the node to bring up a popup menu that includes additional network information about the node, such as DNS records, Whois data, and more. You can pivot off of any of these data points by selecting the SEARCH button.
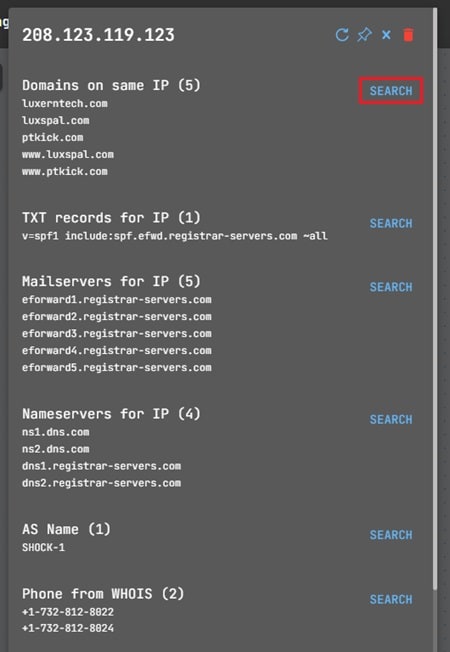
Let’s search for domains related to that IP address. This will populate the graph with related IP addresses (1) and the right-hand panel with your node and search data (2) – useful when you need to search for, remove, or exclude a node.
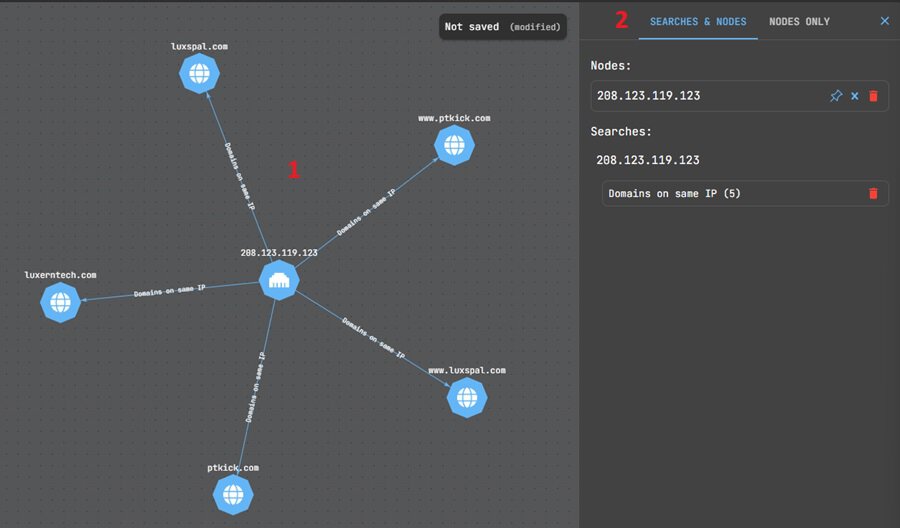
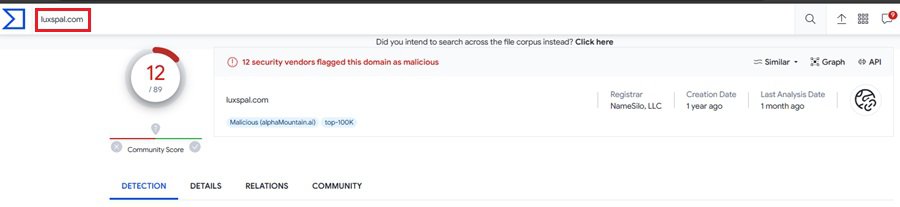
You could add these domains and subdomains to your threat hunt to see if any appear in your DNS logs as you look to identify any other potentially compromised machines. A good one to start with might be luxspal.com based on VirusTotal.
On the other hand, you could choose to pivot to one of these subdomains and find additional indicators to look for by following the indicator lifecycle. For example, luxerntech.com has another IP address associated with that domain. You can use the SEARCH button to add this IP to your graph.
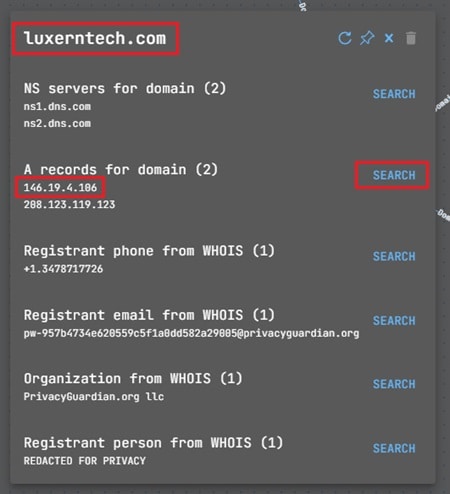
This IP address 146.19.4.106 has new domains associated with it. You can add these to your graph using the SEARCH button again.
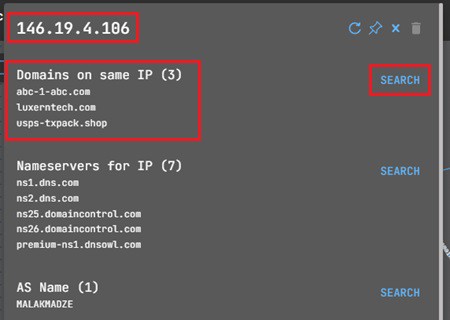
As you can see, our list of indicators is growing with every pivot we make, allowing you to expand your threat hunt and uncover suspicious activity related to that original IP address.
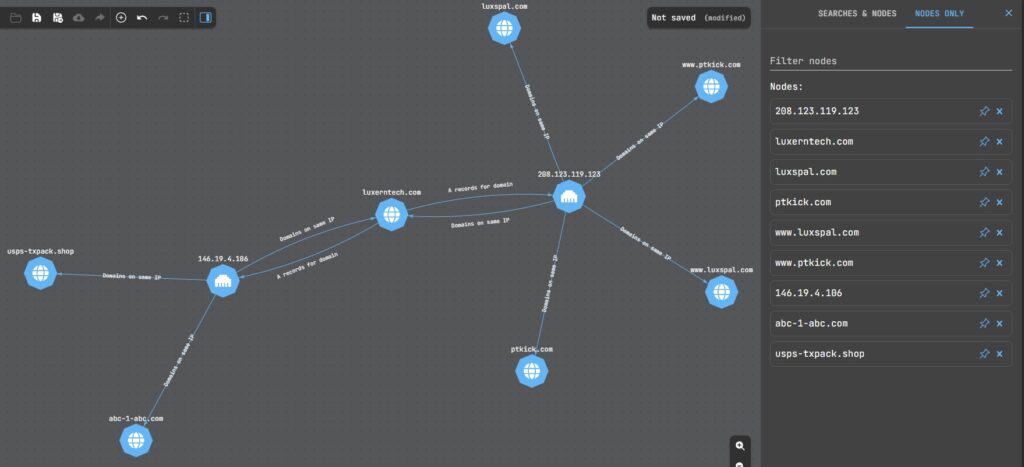
You don’t just need to pivot from IP addresses and domains. You can pivot from nameservers, Whois data like email addresses, certificates, JARM fingerprints, and more!
Conclusion
Visual link analysis is a great way to expand your threat hunts and uncover additional IOCs to investigate based on a single data point. The Netlas.io Attack Surface Discover Tool is the perfect tool to use. You can quickly pivot around Netlas.io’s vast network data sets, manage your nodes and searches in the right-hand panel, and even save and export your graph!
The Netlas tool suite is free to try out right now. There are also many features I didn’t get to showcase today, like the API and powerful query language, that I highly recommend playing around with using your own indicators. Give it a go, and let me know your thoughts!