If you use the Cyber Kill Chain in the real world, Cyber Kill Chain challenges you will face.
Lockheed Martin’s Cyber Kill Chain is an excellent framework for analyzing cyber attacks and mapping intrusion data. However, using it in the real world can prove challenging if you misinterpret its purpose, lack experience using it, or fail to integrate it with other cyber security frameworks and models.
This article explores the top five Cyber Kill Chain challenges you will encounter using the framework. These range from its static, linear design to its assumption of complete visibility and the heavy focus on preventative measures. Along with each challenge, strategies for overcoming them are presented so you can get back to kicking ass.
Let’s begin by quickly recapping the Cyber Kill Chain and its seven stages.
Cyber Kill Chain Recap
The Cyber Kill Chain is a framework for cyber security professionals to structure their cyber intrusion analysis. Developed by Lockheed Martin in 2011, it has since become a fundamental tool for defenders across the industry.
The framework consists of seven stages that describe how an adversary performs a typical cyber attack.
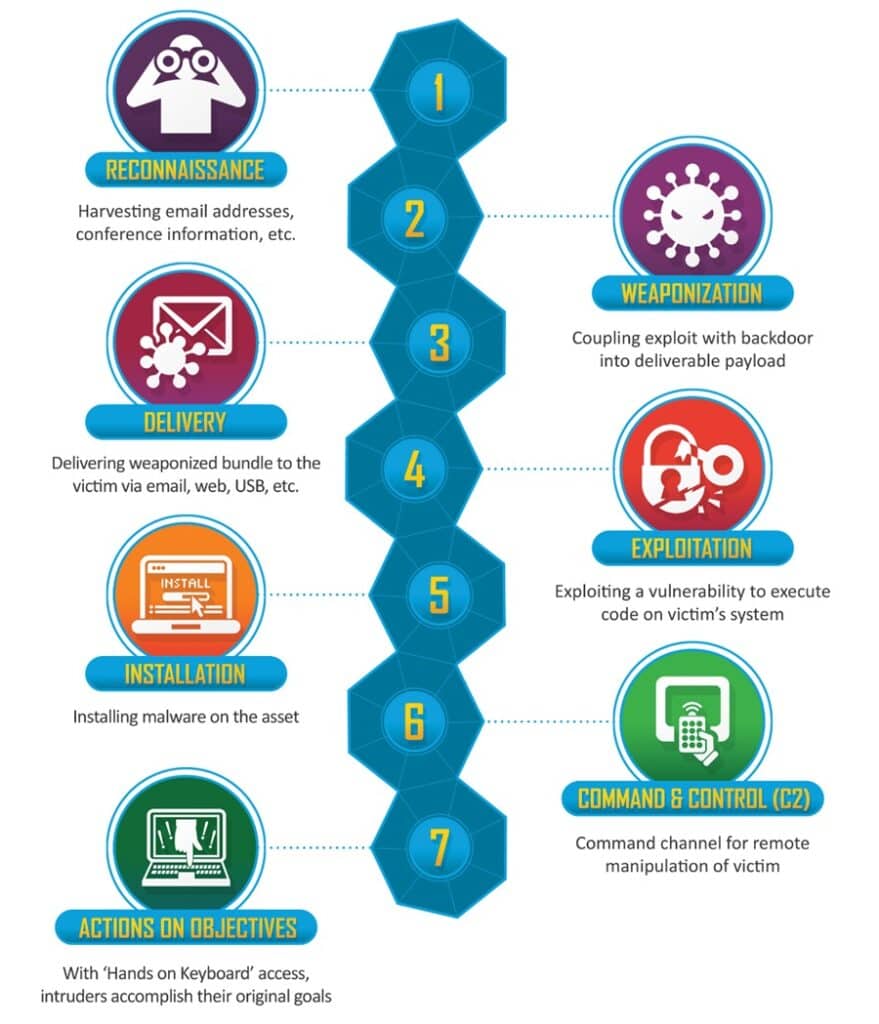
Each stage represents a key stage an adversary must complete to successfully perform a cyber attack against an organization. The stages are sequential, with each building on the last, and are as follows:
Stage 1: Reconnaissance
This is where attackers begin their attack by gathering information about their target through network scans, social engineering, and Open Source Intelligence (OSINT). To plan their attack, they will try to find data about the target’s infrastructure, employees, technology stack, and potential vulnerabilities.
Stage 2: Weaponization
Once target information has been collected, a threat actor will create or acquire the tools, exploits, or other capabilities required to exploit this information. This could be exploiting a technical vulnerability or crafting a phishing pretext to target company employees.
Stage 3: Delivery
Next, an attacker needs to deliver their weaponized payload to the target. This could include exploiting a public-facing vulnerability, sending a phishing email, or exploiting a common weakness on the company’s website. The information gathered during the Reconnaissance stage will heavily influence this stage.
Stage 4: Exploitation
Once the malware, phishing link, or exploit has been delivered to the target, it must be executed to take advantage of software bugs, misconfigurations, weak authentication mechanisms, or missing security controls. This execution will allow the attacker to gain initial access to a target machine.
Stage 5: Installation
After gaining initial access, a threat actor will try to install a persistence mechanism to solidify their initial foothold and withstand password resets, system reboots, or security updates. You can learn more about persistence mechanisms in the Hunting for Persistence With Cympire series.
Stage 6: Command and Control (C2)
With a persistent foothold established, an attacker can aim to establish a communication channel between the compromised systems and their command infrastructure. This C2 communication allows the attacker to perform post-exploitation tasks like data exfiltration, escalating privileges, and lateral movement.
Stage 7: Actions on Objectives
In the final stage of a cyber attack, the adversary will look to fulfill the objectives they planned to achieve in Stage 1. This could be exfiltrating sensitive data, gaining access to a certain machine, sabotaging key infrastructure, performing espionage, deploying ransomware, or anything else they are motivated to do.
These seven stages allow defenders to better understand how a cyber attack happens, what an attacker must do to be successful, and where they can build defenses to prevent an intrusion.
Using the Cyber Kill Chain to generate reactive detections that you monitor or proactive threat hunts your team performs to search for the presence of threat actors are fundamental building blocks of all cyber security programs.
The Cyber Kill Chain is often used alongside other structured analytical techniques, including the MITRE ATT&CK framework and the Diamond Model, to fulfill these use cases. Combining these frameworks allows cyber security professionals to perform consistent, comprehensive, and thoughtful data analysis when analyzing threat intelligence.
To summarize, here are the key benefits the Cyber Kill Chain provides cyber security analysts:
- A structure for investigating intrusions and building cyber defenses.
- It helps non-technical stakeholders understand the main stages of a cyber attack and form a narrative.
- Is great for creating a visual representation of how an attack happened.
- It can be easily integrated with frameworks and methodologies like the MITRE ATT&CK matrix and Diamond Model.
- It provides a common language for analysts to communicate their findings with the wider community and foster collaboration.
Despite its benefits, using the cyber kill chain in the real world will present several challenges. Let’s examine these challenges and how you can overcome them.
Cyber Kill Chain Challenges
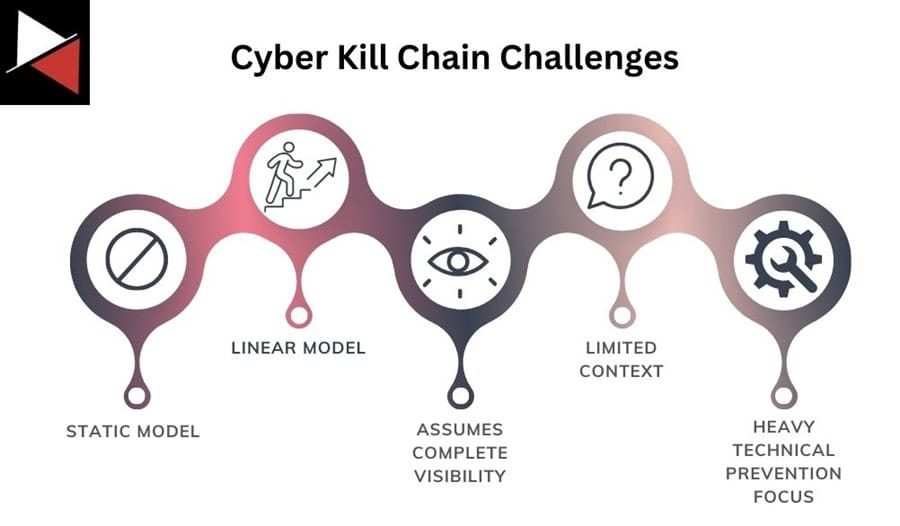
The Cyber Kill Chain has existed since 2011. Since then, cyber security and technology have changed significantly. The emergence of ransomware, service-based cybercrime, and supply chain attacks have all tested the framework’s effectiveness in analyzing modern cyber attacks. This has led to five main criticisms and subsequent challenges when using the model.
The Cyber Kill Chain challenges are:
- It is a static model that only focuses on external threats
- The model is linear, unlike modern attacks
- It assumes defenders have complete visibility
- Provides limited context
- Too heavily focused on technical prevention
Static Model Focused on External Threats
The Cyber Kill Chain is a static model that focuses on how an adversary performs a typical cyber attack from outside an organization; the stages don’t change, the attacker is always external, and no framework component accounts for evolving threats.
This can lead to two main problems:
- The kill chain cannot adapt to emerging threats like ransomware-as-a-service (RaaS) and Advanced Persistent Threats (APTs) that require different defense approaches.
- Only focusing on external threats that originate from outside the target organization inadvertently ignores common attacks that stem from insider threats and supply chain attacks—again, requiring different defense approaches.
These two problems lead many to criticize the Cyber Kill Chain for being outdated and failing to keep up with new attack tactics and techniques.
Solution
These two problems arise due to misuse of the Cyber Kill Chain. The framework does not offer prescriptive advice on how to deal with specific threats, like ransomware, insider threats, or supply chain attacks. If you need this guidance, you can use other frameworks alongside the kill chain, such as NIST’s Cybersecurity Framework or MITRE Defend.
The Cyber Kill Chain is also not designed to be an evolving framework like MITRE ATT&CK that changes in response to emerging threats. Instead, it is designed to allow analysts to structure their investigation and group data into common attack stages.
Other techniques like threat modeling and threat profiling help organizations defend against emerging threats and highlight the specific TTPs that need to be defended against. Defenders can then group these TTPs into the attack stages defined by the Cyber Kill Chain for reporting, narrative creation, and strategic planning.
Linear Model
The Cyber Kill Chain is a linear model. An attack starts at Reconnaissance and finishes at Actions on Objective. As such, it assumes attackers progress through each stage sequentially, never returning to an old stage or skipping one. However, many cyber attacks do not follow a linear progression. They will revisit or skip stages depending on the attacker’s goals, access to information, and strategic attack plan.
Microsoft’s attack kill chain is a more accurate model for modern cyber attacks. It highlights how attackers gain initial access, escalate their privileges, and move across the Active Directory domain. This newer model shows the cyclical nature of some of the kill chain phases.
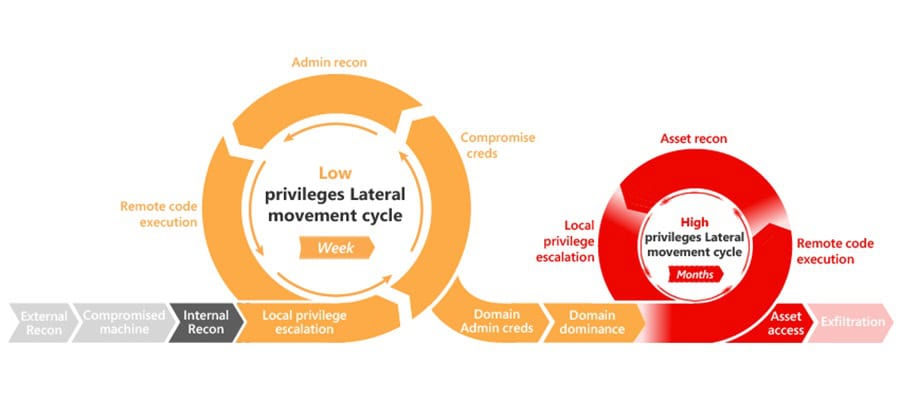
The mismatch between how modern cyber attacks are performed and how the Cyber Kill Chain describes them can lead to confusion, poor analysis, and missing intrusion data.
Solution
We know more about cyber attacks than we did when the Cyber Kill Chain was created in 2011. Models like Microsoft’s attack kill chain better represent how real-world attacks happen and are useful frameworks to use during an investigation. Unfortunately, these more detailed models can become convoluted, difficult to follow, and slow down an investigation.
This is particularly true for less technical stakeholders who are looking for a simple attack narrative to follow and understand.
This is where the Cyber Kill Chain shines. Its simple, linear description of a cyber attack makes it easy to follow and use. Practitioners can use the model to group data into distinct stages to ensure a comprehensive analysis. Meanwhile, managers can use it to create an attack narrative that provides non-technical stakeholders a simple overview of what happened and how their operational team responded.
Use the Cyber Kill Chain to simplify a cyber attack and create a high-level overview for grouping data. Then, use cyber threat intelligence and other frameworks (e.g. MITRE ATT&CK and Diamond Model) to dig deeper.
Assumption of Complete Visibility
Defenders need complete visibility into their networks, systems, and external-facing assets to accurately complete the Cyber Kill Chain. They cannot provide intrusion data or build defenses for every stage without this visibility.
This visibility is very hard to achieve in the real world for two main reasons:
- The reliance on third-party services like authentication providers, web hosting services, and software-as-a-service (SaaS) products compartmentalizes and hides data. This reliance on third parties is often required to make businesses function. It streamlines operations, reduces costs, and can even be a compliance requirement. Getting away from third parties is impossible in today’s complex and dynamic business world.
- Visibility into the Reconnaissance and Weaponization phase is difficult for most organizations, if not impossible. It would require companies to track all the information that can be used against them (e.g., OSINT data, exploits, TTPs) and have visibility into an adversary’s systems to see what they are doing with it. For organizations outside of nation-states, this is impossible.
These two challenges can hinder the Cyber Kill Chain’s effectiveness because practitioners can never complete it.
Solution
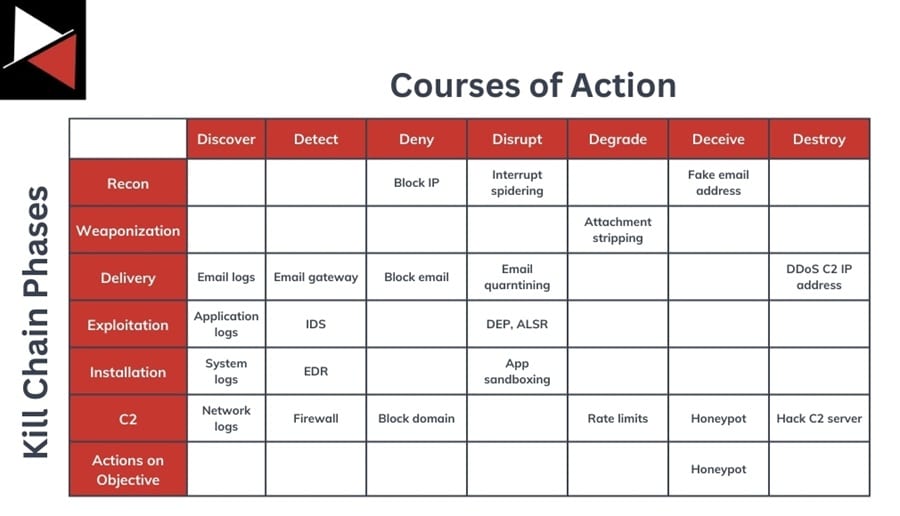
There are ways to gain visibility into the Reconnaissance and Weaponization stages of the kill chain through actions described in the Courses of Action matrix, particularly Discover and Deceive.
- Discover: You can use active threat intelligence techniques like dark web monitoring and credential leak hunting to collect intelligence about how attackers are weaponizing exploits and what information they already have about a target. This can be used to prioritize resources and proactively defend against an attack.
- Deceive: Deception tactics like honeypots, honey tokens, and fake personas that interact with threat actors can help you gather intelligence about exploits attackers have access to, TTPs that are being used, and malware being sold. Again, this gives you visibility into the Reconnaissance and Weaponization stages.
Although active countermeasures like these can be used, they don’t have to be if you lack the resources. It is important to remember that the Cyber Kill Chain does not offer prescriptive advice on combating cyber threats. It simply groups data. As such, filling out every stage is unnecessary if you lack visibility.
You can just use the framework where it provides value, such as grouping data into attack stages, tracking intrusions, and generating an attack narrative. Then, use other frameworks or models to fill in the gaps.
Limited Context
The Cyber Kill Chain is designed to provide a high-level overview of a cyber attack by mapping out the key stages an adversary must complete to be successful. The model does not provide context about the specific tactics, techniques, and procedures (TTPs) an attacker will use to complete these stages or capture the nuances of different attack scenarios or strategies.
This makes it challenging to build cyber defenses that protect against specific attacker behavior, such as detections, incident response plans, or threat hunts.
Additionally, the model does not fully account for the complexity of modern hybrid environments, which include a mix of on-premises infrastructure, cloud services, and third-party applications. It does not offer prescriptive advice on where these fit into a cyber attack or security controls that can help defend these assets—again, making the creation of defenses challenging.
Solution
This is another challenge that arises if you try to use the Cyber Kill Chain for the wrong things. The kill chain is not designed to offer prescriptive advice. It does not hold all the answers to how a cyber attack happens and how to defend against it. Instead, the model is about grouping data into common stages that allow you to create an attack narrative that is easy to understand and follow.
Use the Cyber Kill Chain as a high-level overview of each stage an attacker will typically complete. Then, other frameworks like MITRE ATT&CK and NIST can be used to provide more context about the TTPs an attacker will use and the cyber defenses you can use to defend against them. With this added detail, you can build detections, incident response plans, and threat hunts.
The Cyber Kill Chain is meant to help you group data. It is most useful when integrated with other frameworks and models.
Focus on Technical Prevention
The Cyber Kill Chain strongly emphasizes the role of technical security controls in defending against cyber attacks. Technical security controls like detection rules and technologies like Endpoint Detection and Response (EDR) are important, but they are not an organization’s only strategies.
Organizations must consider other defensive strategies beyond preventing attacks, such as employee awareness training, proactive threat hunting, and incident response capabilities. The Cyber Kill Chain can give defenders a false sense of security by overemphasizing technical prevention.
Solution
Factor in other defensive strategies to the model. It’s that simple.
The Cyber Kill Chain highlights the stages of a typical cyber attack. Defenders usually interpret this as points where they can build defenses to prevent an adversary’s success. This is logical, but it assumes technical prevention is enough to defend against modern attacks. It is not.
You should use the Cyber Kill Chain to focus on where you can act against cyber threats. The actions you can take are defined in the Course of Action matrix and include:
- Discover: Uncover an adversary’s past activity in the logs.
- Detect: Identify an attacker’s current activity using detection and visibility tools, such as anti-virus, EDR, and IDS.
- Deny: Block an attacker’s activities using firewall rules, email filtering, privilege restrictions, etc. This is the prevention component.
- Disrupt: Interrupt an attacker’s activities using strategies like quarantining files, exploit protections, and application sandboxing.
- Degrade: Reduce the effectiveness of an adversary’s activities by slowing them down and giving defenders more time to respond.
- Deceive: Use false information to mislead the adversary and gather data about them (e.g., fake accounts, honeypots, honey tokens).
- Destroy: Damage an attacker’s infrastructure to make it no longer operational (e.g., “hacking back”).
Consider how you can use all these actions to defend against an attack and map them to each stage of the Cyber Kill Chain.
Conclusion
The Cyber Kill Chain is an incredibly useful tool that all cyber security professionals should understand and use to analyze intrusions effectively. However, using it in the real world can create several challenges.
This article covered five common issues analysts face when using the framework and strategies to overcome them. The predominant challenges identified arose due to misuse of the framework.
The Cyber Kill Chain does not offer prescriptive advice on combating cyber threats. Instead, it allows you to group intrusion data into common attack stages to create an attack narrative that is easy to follow and understand. Read The Cyber Kill Chain: How to Map and Analyze Cyber Attacks to learn more about the Cyber Kill Chain and get the most value from it.
Frequently Asked Questions
What Are the Weaknesses of the Cyber Kill Chain?
The Cyber Kill Chain is a fundamental model used in cyber security for analyzing intrusions, building cyber defenses, and threat hunting. However, the model is not perfect. Some of its weaknesses include:
- Being a static model that only focuses on external attacks.
- Cyber attacks are assumed to have a linear progression. This is not always true with insider threats, Ransomware-as-a-Service (RaaS), or supply chain attacks.
- Assuming defenders have complete visibility into cyber attacks. This is also not always true with cloud deployments, hybrid environments, remote work, and software-as-a-service (SaaS).
- The model lacks context about the tactics, techniques, and procedures (TTPs) attackers employ at each stage.
- The Cyber Kill Chain heavily focuses on technical controls that prevent an intrusion while ignoring non-technical controls (e.g., training and awareness) and other cyber security capabilities like detection, response, recovery, and proactive monitoring.
Solutions to overcome these challenges are discussed in the article.
Is the Cyber Kill Chain Outdated?
The Cyber Kill Chain was created by Lockheed Martin in 2011. Cyber attacks have changed significantly since then with the proliferation of insider threats, Ransomware-as-a-Service (RaaS), and supply chain attacks. Some critics claim that the model is outdated and too simplistic to have value in defending against evolving cyber threats.
However, many cyber security professionals see great value in the model’s ability to help craft an attack narrative that they can use to describe a cyber attack to non-technical stakeholders and to structure their analysis. As such, it is still widely used in the cyber security industry and is an important tool in your arsenal. Read The Cyber Kill Chain: How to Map and Analyze Cyber Attacks to learn more.
What Is the Benefit of the Cyber Kill Chain?
The Cyber Kill Chain has many benefits. Some of the key benefits include:
- Providing a structured approach to defending against cyber attacks and investigating intrusions.
- Helping non-technical employees understand how a cyber attack happened.
- Being used for visual reporting and providing a high-level overview of an intrusion using an attack narrative.
- Integrating with frameworks and methodologies that provide more granular technical details on what an adversary did, like the MITRE ATT&CK matrix and Diamond Model.
- Helping foster collaboration across organizations by providing a common language for cyber analysts to communicate their findings.




