The cyber threat intelligence lifecycle is a fundamental model for structuring intelligence work. Implementing it is difficult and you will have to overcome many threat intelligence lifecycle challenges.
This article discusses the top five challenges you will face when using the threat intelligence lifecycle in the real world. You will discover the issues that can arise with the people, processes, and technology when trying to structure and organize your cyber threat intelligence, from having too much data to too little feedback. After each problem, I will detail solutions you can use to navigate around them and build the perfect intelligence lifecycle.
Before we jump into the challenges, here is a quick recap of the threat intelligence lifecycle to get you up to speed.
Threat Intelligence Lifecycle Recap
The Cyber Threat Intelligence (CTI) lifecycle provides a framework for organizing intelligence analysis. It is used to structure the collection, analysis, and distribution of threat data, transforming it into actionable intelligence that can be shared with key stakeholders in your organization.
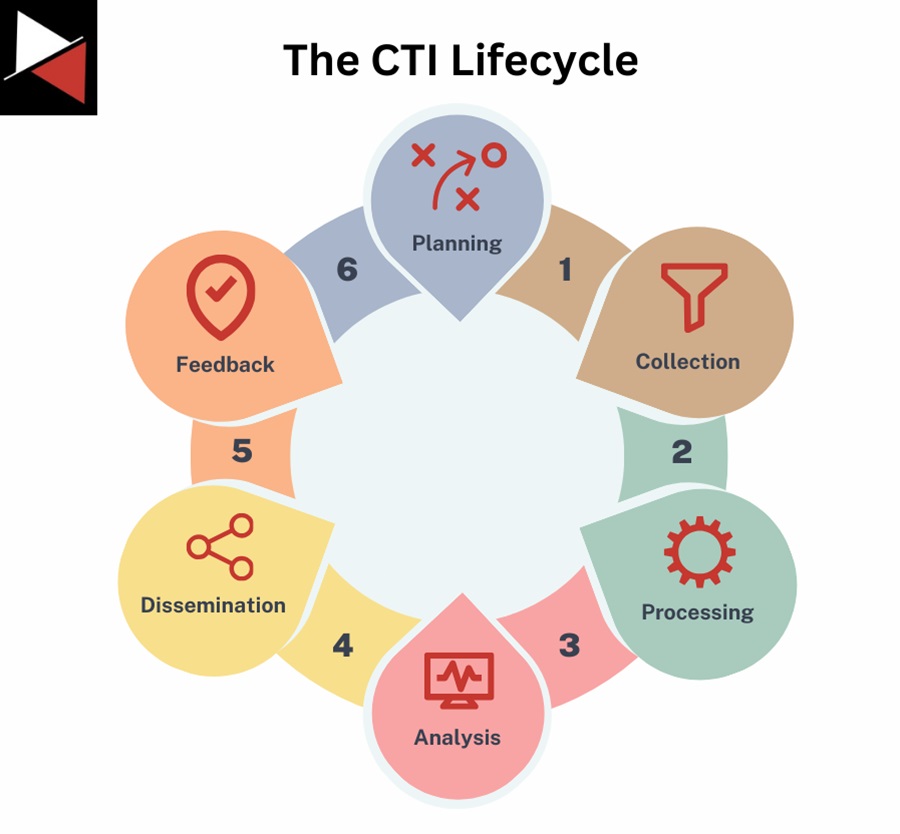
The lifecycle includes six phases that serve as a blueprint for CTI analysts to follow when performing intelligence work or by CTI leads when designing processes for their teams. These six phases are:
- Planning: Defining the goals and key objectives of your intelligence work, including how you will collect, analyze, and share information to fulfill your organization’s intelligence requirements.
- Collection: Gathering information to answer the intelligence requirements you planned to fufil. This involves identifying relevant data sources to collect information from and storing it somewhere.
- Processing: Transforming raw data into information for analysis by cleaning, normalizing, and verifying the data is legitimate.
- Analysis: Turning the information gathered into actionable intelligence that answers your intelligence requirements. The intelligence produced helps your organization defend itself from cyber attacks or informs strategic decision-making.
- Dissemination: Sharing the intelligence with relevant stakeholders. Who you share intelligence with will depend on the type of intelligence you have produced (operational, tactical, strategic) and the audience you are sharing it with.
- Feedback: Collecting feedback on the quality of the intelligence produced and the effectiveness of the process. This allows you to continuously improve your CTI work and deliver more value.
The threat intelligence lifecycle is used throughout the cyber security industry. Its structured methodology allows you to produce relevant, timely, and actionable intelligence that delivers value to your security operations team and organization executives. However, you will face challenges when turning this model into a real-world process.
You can adapt the lifecycle to suit your intelligence requirements, team structure, and organizational needs. If you want to learn more about the cyber threat intelligence lifecycle, read this complete guide.
Threat Intelligence Lifecycle Challenges
Despite the CTI lifecycle’s many benefits, you will encounter implementation challenges. Let’s look at some of those challenges and how to overcome them.
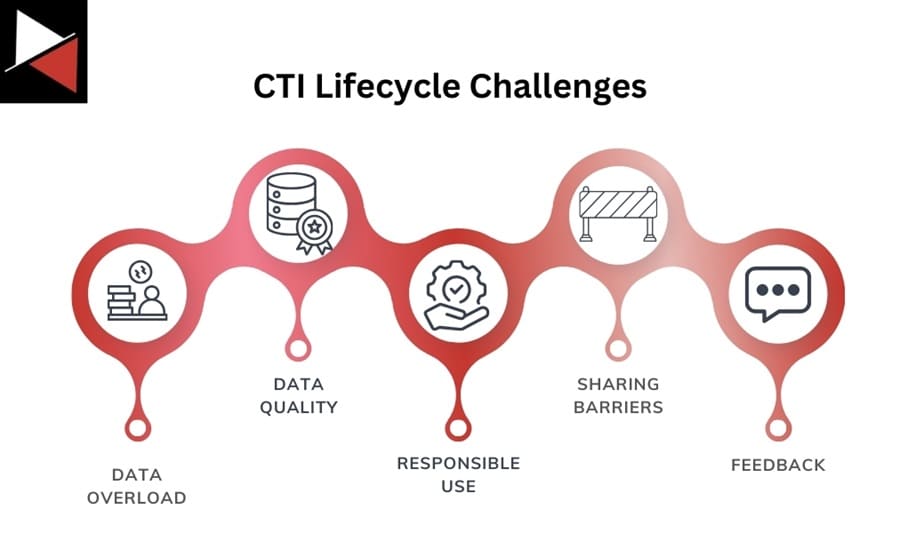
Data Overload
As you work through the threat intelligence lifecycle, you will Collect large quantities of data, filter it through Processing, refine it with Analysis, and share key pieces of intelligence during Dissemination. The sheer volume of data available when you start the Collection phase, and then the data you need to sort through during the Processing and Analysis phases, can be overwhelming.
It is a resource-intensive process to filter out the noise, identify what is relevant, and then enrich the relevant intelligence with your collected data. This is especially true if you don’t have the right people, technology, and processes in place.
Solution
Overcoming data overload is simple. You can either invest more resources in your threat intelligence process, be it a new data processing tool or more analysts, or consume less data. A good place to start is by streamlining your existing procedures. Ask questions like:
- Are your existing procedures efficient?
- Are there things you can automate to save analyst time?
- Are you analysts sufficiently trained in their tools to derive the most value from them?
- Are there free or open-source tools you could use to make processes more efficient?
- Have you planned your processes to make them optimum for your purpose and scheduled time to think of innovative solutions regularly?
Procedures are usually the easiest place to begin. You can optimize procedures without incurring much (if any) cost, and with the power of automation, there are usually time-consuming tasks you can cut out of your analyst’s workload. Once you are confident your procedures have peaked, look at training new people and investing in technology.
Data Quality
The quality of the data you ingest into the threat intelligence lifecycle will dictate the quality of data you get out. If you put garbage data in, you will get garbage data out.
This is because the key phases of Processing, Analysis, and Dissemination rely upon the data ingested at the Collection phase. Collecting inaccurate, untrustworthy, or outdated information will create bad intelligence reports because your assessments will be based on poor data. However, ensuring the accuracy and trustworthiness of the data you collect is challenging.
Solution
You need quality control to prevent bad data from clogging up your intelligence processes. Start creating criteria to assess the quality of data you are consuming, you can do this by asking questions like:
- Does this data source produce a high number of false positives?
- Are the indicators shared in a timely manner?
- What is the credibility of this data source?
- Can this data source produce unique information, or can I get it elsewhere?
- What is the likely validity of the claim made by this data source?
Next, list all your current data sources and assess the quality of data they produce against your assessment criteria. Remove them as a source if they fail to satisfy your data needs. Whenever you find new data sources, use these criteria to assess them before adding them to your collection.
Assessing data quality can be hard when you are in the moment. Use historical data to understand how regularly a data source produces bad information using an acceptable tolerance.
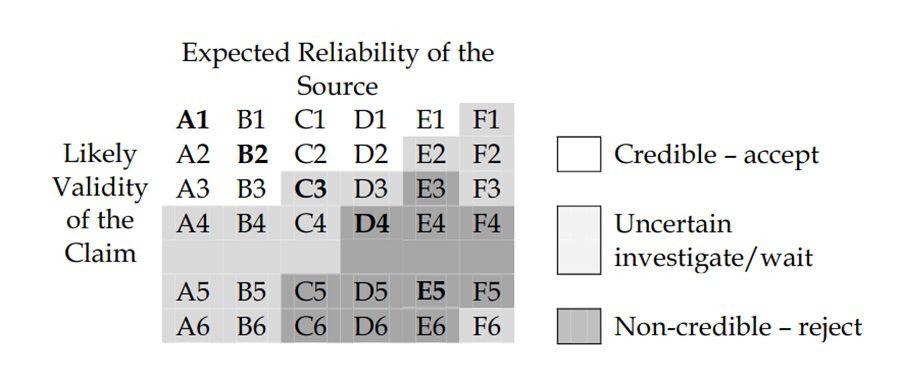
A good practice used in the intelligence community to assess the quality of data sources is estimative probability. Tagging a source, or piece of information, with a language that conveys the likelihood of it being good allows you to add confidence to your assessments. For example, you may have a high level of certainty about an assessment you make because your data source is reliable and you have multiple pieces of evidence.
A popular scale to rank the reliability of a data source and the credibility of information is the Admiralty Scale (a.k.a. the NATO System). If you use the MISP threat intelligence platform, you can add it as a taxonomy and tag information using it.
Responsible Use
Threat data can include sensitive information. It is your responsibility as a CTI analyst to not abuse this information and use it responsibly by following ethical guidelines, adhering to privacy concerns, and complying with data protection regulations. Ensuring ethical and responsible use of intelligence is difficult given the amount of data that passes through the threat intelligence lifecycle. It is a problem you must consider during the Planning phase.
Solution
To ensure data is used responsibly, you must implement processes and procedures designed to protect it. The Traffic Light Protocol (TLP) is a good one to get started with. TLP is a set of delegations used to control the distribution and sharing of sensitive information using a color-coded classification system.
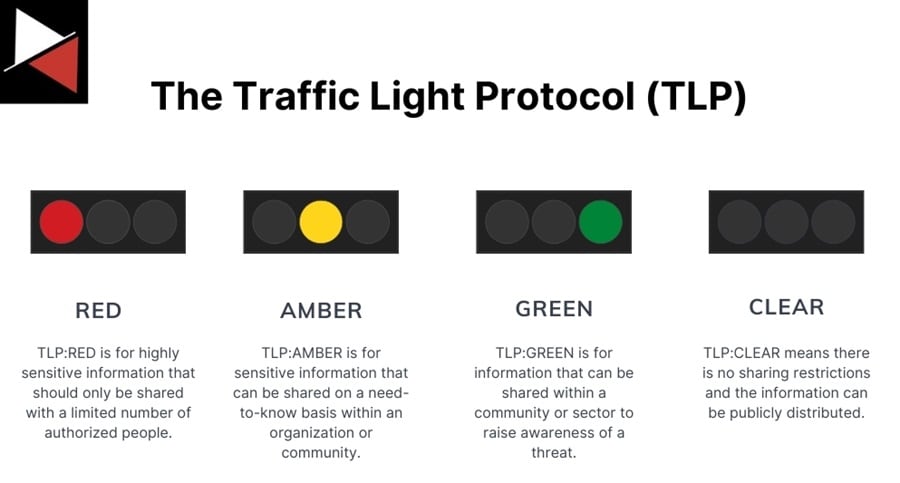
There are four primary colors used in this system. Expand the dropdowns for a detailed description of what they mean.
Red
Information marked as TLP:RED is considered highly sensitive and should only be shared with individuals who have a need to know. It is intended for a specific audience and should not be disclosed beyond that group.
Amber
Information marked as TLP:AMBER is sensitive but can be shared within a community or sector. It is intended for organizations and individuals actively participating in efforts related to a specific threat or incident. There is also TLP:AMBER+STRICT used to restrict sharing to an organization, not its clients.
Green
Information marked as TLP:GREEN is intended for a broader audience and can be widely shared. It is suitable for sharing within an industry or community.
Clear
Information marked as TLP:CLEAR is considered unrestricted and can be shared freely without limitations. It is suitable for public dissemination. This was TLP:WHITE in TLP version 1.0.
You should tag all your data with a TLP delegation to ensure it is clear who should be able to access it, promoting a culture of responsible data usage and sharing.
The MISP threat intelligence platform includes a TLP taxonomy you can use to tag your data with a sensitivity delegation.
Intelligence Sharing Barriers
Often, the hardest part of the threat intelligence lifecycle is the Dissemination phase. Many barriers exist to sharing threat intelligence across your organization or with the wider community. Some include legal or regulatory constraints, trust issues, lack of standardized data-sharing practices, disparate report styles/formats, and missing interoperability between tools and platforms.
Solution
Overcoming these barriers can be difficult, if not impossible, but there are certain solutions you can adopt at your own organization and push the community to move towards. Some of these solutions include:
- A standardized threat intelligence reporting format: Adopting a standard way of reporting cyber threat intelligence will allow analysts to more easily share reports, raise the reporting quality, and provide consistency. MITRE Engenuity’s CTI Blueprints project is a great project that makes this idea a reality.
- Use of a common language: In CTI, we have primarily adopted the MITRE ATT&CK matrix to describe attacker TTPs and capabilities. You should use this matrix in your CTI reports and continue the push to make it an industry standard.
- Data sharing centers: Organizations that exist to help facilitate the sharing of information are awesome, be it sector-specific Information Sharing and Analysis Centers (ISACs), Information Sharing and Analysis Organizations (ISAOs), or national-level Computer Emergency Response Teams (CERTs). However, the quality of these groups depends on the people running them. Often they can have high dues, lack value, and be painfully slow. Make sure to do your due diligence before investing in one.
- Interoperability between threat intelligence platforms/tools: Open-source threat intelligence platforms like MISP and OpenCTI are great for storing, organizing, and visualizing knowledge about cyber threats. They integrate with many other security tools, allowing you to easily ingest and share data. I highly recommend adopting one of these platforms and looking for tools to work with them. It will make it substantially easier to share intelligence.
Feedback and Improvement
The most overlooked and neglected stage of the threat intelligence lifecycle is the Feedback stage. CTI teams often fail to incorporate metrics to assess the effectiveness of their intelligence activities, don’t implement processes to generate feedback from their intelligence consumers, and lack continuous improvement. Without spending time receiving feedback and improving existing processes, CTI teams are just blindly sharing intelligence with people in their organization and not considering if it adds value.
Solution
To get feedback, you must build a process that requires your intelligence consumer to provide it. This could be a Google doc they have to spend five minutes filling out for each intelligence report, a quarterly assessment they complete about the value they are getting from the CTI teams and what improvements could be made, or even a monthly video call to provide teams with a platform for open discussion.
The key is to have a process that makes it easy for the consumer to share feedback, easy for you to collect and process it, and time built into your workflow to implement any improvements.
Another factor that may limit your ability to implement the CTI lifecycle effectively is resource constraints, such as limited time, manpower, and money. Read The Cyber Threat Intelligence Lifecycle: A Fundamental Model to learn more.
Conclusion
CTI is challenging. Implementing the threat intelligence lifecycle in the real world is no easy task. This article detailed five main challenges you will face when turning this simple model into a fully functioning process. They were data overload, data quality, responsible use, intelligence sharing barriers, and feedback and improvement.
You saw ways to overcome these challenges, be it tagging data or scheduling time for improvement. The common factor underlying all of these solutions is planning. You must think critically about the data you are ingesting, how you use it, and how to get the most value from it for your organization. Answering these questions will keep you on track when implementing the threat intelligence lifecycle.
Frequently Asked Question
What Is the Cyber Threat Intelligence Lifecycle?
The Cyber Threat Intelligence (CTI) lifecycle is a fundamental model used in cyber security for organizing intelligence analysis. It helps CTI analysts and teams structure threat intelligence collection, analysis, and distribution so organizations can better defend themselves from cyber threats. It includes six phases; Planning, Collection, Processing, Analysis, Dissemination, and Feedback.
What Is the Benefit of Using the Threat Intelligence Lifecycle?
The threat intelligence lifecycle provides a framework that empowers cyber security professionals to structure their intelligence work. It describes a systematic and thorough process that will help you to produce high-quality intelligence that will be of value to your organization. It is not overly prescriptive and can be adapted to your organization’s structure, needs, and intelligence requirements.
What Are the Main Challenges of Using the Threat Intelligence Lifecycle?
The threat intelligence lifecycle is a model all intelligence teams should use to structure their processes. Implementing this model comes with several challenges. The five main ones are:
- Data overload: Too much threat data for you or your team to collect, process, and analyze.
- Data quality: Too much bad data that is inaccurate, untrustworthy, or contains false positives. Leading to bad intelligence assessments.
- Responsible use: Using data responsibly by following ethical guidelines, adhering to privacy concerns, and complying with data protection regulations.
- Intelligence sharing barriers: Legal or regulatory restrictions, trust issues, lack of standardized data-sharing practices, disparate report styles/formats, and missing interoperability between tools/platforms make sharing intelligence difficult.
- Feedback and improvement: A lack of metrics or feedback to assess the effectiveness of their intelligence activities and make continuous improvements.




