Indicators are a fundamental aspect of cyber threat intelligence. You encounter indicators daily in your work and must know how to utilize them to achieve your intelligence requirements. To help you with this, let me introduce you to the indicator lifecycle.
The indicator lifecycle is a foundational model that empowers cyber security analysts to work with indicators using a structured approach. It combines people, processes, and technology to be a dynamic model applicable across many security operations. For you, as a threat intelligence analyst, it will provide a systematic method for moving between data points, investigating an intrusion, and gathering evidence – pivoting.
Let’s start by learning more about indicators so you can unlock the full potential of the indicator lifecycle!
What Are Indicators?
Indicators are data points you can observe in a log file, accompanied by context. The data might be a domain name, and the context is that the domain is a known Command and Control (C2) server.
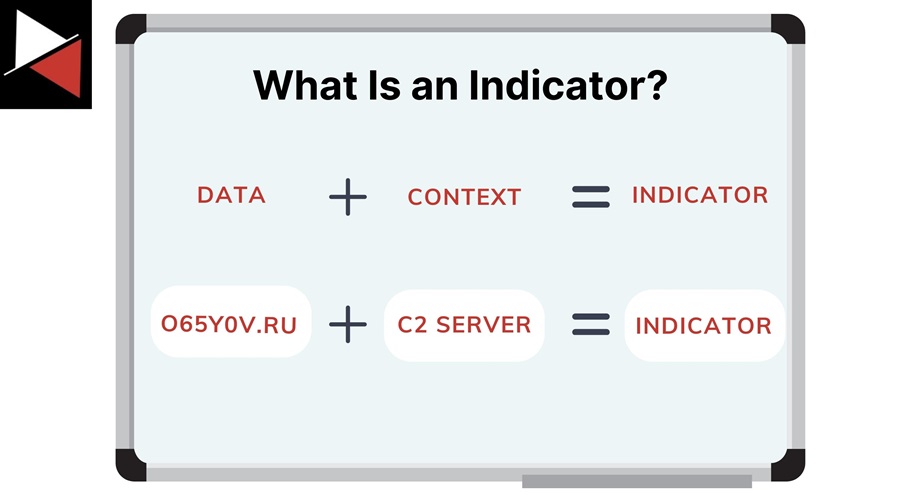
However, an indicator does not necessarily need to be malicious. An indicator simply indicates something. For instance, an indicator could be the execution of a remote access tool like TeamViewer. This is not malicious itself, but it is something to investigate.
If you find out that attackers often use remote access tools to maintain covert access to infected machines, that this execution occurred outside of normal office hours, and that a non-admin account ran the file, it may indicate it is malicious – context matters.

There are different categories that indicators can fall into. Threat intelligence vendors will use these categories when reporting on threats in their reports. Here are some categories and terms common terms you are likely to come across when reading about indicators:
- Atomic Indicators: A singular indicator that provides granular details about a specific thing. For instance, an IP address that appears in DNS logs, an email address you see in a phishing email, or a registry key’s value on an endpoint machine.
- Computed Indicators: An indicator derived or generated from the analysis or computation of raw data or atomic indicators. For example, you can calculate a file’s hash using a hashing algorithm and use this as an indicator.
- Tactics, Techniques, and Procedures (TTPs): Indicators based on an attacker’s actions. They are composed of atomic and computed indicators and are often referred to as behavioral indicators because they indicate how an adversary behaves during an attack.
- Indicators of Compromise (IOCs) and Indicators of Attack (IOAs): When an investigation is started, these are the indicators that an analyst will look for to indicate malicious or suspicious activity has taken place. IOCs consist of atomic and computed indicators, while IOAs include an attacker’s TTPs.
Knowing the different types of indicators will help you use indicators most effectively, depending on your intelligence requirements. Let’s look at some examples of indicators you will likely come across and map them to these categories.
194.38.22.53
This is an IP address. They are often found in network logs and are one of the main indicators for investigating adversary infrastructure and network activity. They may be an IOC (depending on context) and are always atomic indicators that are not specific to a threat actor or attack campaign.
o65y0v.ru
This is a domain name. It is another atomic indicator found in network logs (or DNS logs) that you will see a lot of during your cyber security career. You can have more specific network indicators that derive from domain names, such as URLs and hostnames.
d8f55bbbcc20e81e46b9bf78f93b73f002c76a8fcdb4dc2ae21b8609445c14f9
This is a file hash. It is a computed indicator calculated based on a specific hashing algorithm. You will regularly encounter MD5, SHA1, and SHA256 hashes during investigations. Hashes are helpful for finding specific malicious files that attackers use. However, any change to a file will alter its hash. A better way to identify malicious files is with YARA rules, which are more flexible.
“The attacker used a phishing email to gain initial access (T1566).”
This is a description of a behavioral indicator or TTP. It describes how an attacker gains initial access to a system and is an action you can be on the lookout for, either with detections or threat hunts. An industry standard for describing adversary behaviors is the MITRE ATT&CK framework, which you can learn more about in MITRE ATT&CK Framework: The Holy Bible of Threat Intelligence.
Key Indicators
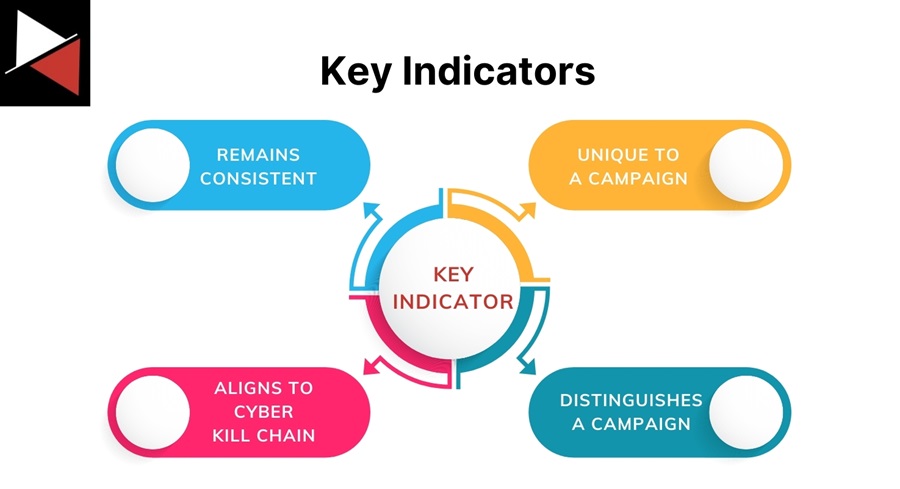
Some indicators are more valuable than others. The indicators you want to prioritize are key indicators. These indicators have the following characteristics:
- Remain consistent across intrusions.
- Uniquely distinguish an attack campaign.
- Distinguish a campaign from benign activity.
- Align to a phase of the Cyber Kill Chain.
A key indicator might be an email address, a malware mutex, and a domain seen together across multiple intrusions. When looking for one of these indicators, the chances of encountering the other two are high.
You want to identify as many key indicators as possible during your threat intelligence work or intrusion analysis because they allow you to track attack campaigns accurately. Having at least two for each stage of the Attack Kill Chain allows you to group an intrusion into a campaign. From here, you can enrich your analysis with data you found when investigating similar intrusions and direct your investigation efforts to look at other possible IOCs.
It is important to remember that just because an indicator is a key indicator for you, it might not be for others. Depending on their dataset and intrusion analysis, others may only come across your key indicator once or twice. Its relevance is trivial. Your intrusion data is the most valuable dataset because it is unique to you and holds information about who is actually attacking you.
Now that you know what indicators are, let’s look at their role in cyber threat intelligence.
Role of Indicators in Cyber Threat Intelligence
Indicators are the bread and butter of the cyber security industry. They pop up everywhere, from security operations and malware analysis to security engineering and vulnerability management. Defenders must know how to use indicators to fight against attackers effectively. However, before you can do that, you need to understand what indicators can be used for.
Indicators will intertwine many security roles and get passed around like wings at a football night. It is helpful to know how other security teams will use indicators so you can tailor intelligence to their needs.
Indicators are used in two main ways in cyber. To detect threats using detection rules or to hunt for adversaries using threat hunting queries.
Threat Detection
Perhaps the most obvious use case for indicators is threat detection. You learn about a malicious IP address, create an alert that triggers whenever one of your endpoint machines tries to connect to it, and then block any connection attempts. Simple. This is how anti-virus (AV) solutions were used to block malware based on hash values in the 1990s.
Of course, this is not the greatest way to detect threats. Nowadays, you can use large language models (LLMs), artificial intelligence (AI), machine learning, User Entity and Behaviour Analytics (UEBA), memory scanning, and various other technologies and techniques to create detections. However, when performing detection engineering and writing detection rules, you will return to the concept of writing rules that trigger based on an indicator, be it atomic, computational, or behavioral.
Indicators can also be used to enrich existing detections with threat intelligence. You can correlate indicators together (group key indicators) to provide an analyst with additional context about an alert. An alert triggers on a malicious domain name, and your detection automatically pulls in related malware samples, IP addresses, and URLs. This allows analysts to search for IOCs using this additional context during their investigation. Leading us into threat hunting.
Threat Hunting
Working in cyber security, you will come across hundreds of indicators daily. Should you write a detection rule for all of them? Of course not! You should write detection rules for the key indicators but use the rest like fishing bait. Attach an indicator to a threat hunting query, search all your systems for it, and throw it away when you are done.
Indicators are a great starting point for finding suspicious activity to investigate quickly. Unfortunately, an adversary dictates the lifespan of an indicator and its usefulness. They can choose to change network infrastructure or recompile malware. Hence, fishing with atomic or computational indicators and targeting adversary behavior with detection rules is often the best approach.
In the series Threat Hunting With Velociraptor, you can learn to do threat hunting. This series walks you through creating a threat hunting environment, outlines the three pillars all successful threat hunts must follow, and showcases how to perform threat hunting using the popular Digital Forensics and Incident Response (DFIR) tool Velociraptor.
That brings us to the indicator lifecycle, a model for understanding how to use indicators in your day-to-day work best.
The Indicator Lifecycle
Like cyber threat intelligence, indicators also have a lifecycle that you can follow to ensure you make the best use of them. The lifecycle consists of three main stages:
- Revealed: You find an indicator.
- Mature: You ready the indicator for threat detection or threat hunting, also known as a Course of Action (CoA).
- Utilized: You use the indicator, revealing other indicators and restarting the lifecycle.
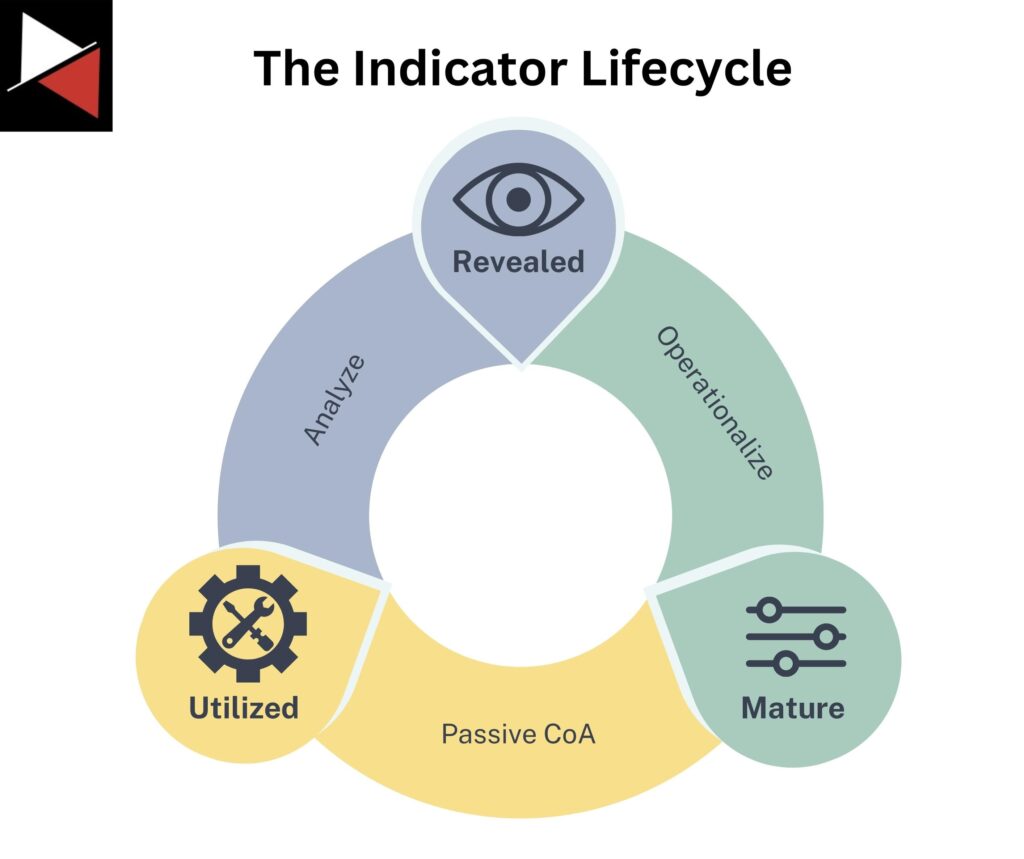
The model combines people, processes, and technology making it dynamic and applicable across many security operations. As a threat intelligence analyst, this model forms the basis of pivoting. It provides a structured approach to moving between data points, investigating an intrusion, and gathering evidence.
When using the model, keep in mind that indicators beget indicators. If you start with a good indicator, you will find more good indicators to pivot to. However, starting with a bad indicator can lead down a slippery slope of other bad indicators and curb your investigation. Ensure that indicators are relevant, from good sources, and meet your intelligence requirements.
This is a pretty easy model to follow, but let’s look at how you can move an indicator between each stage to get the most out of it (inspired by an article from Joseliyo).
Revealed to Mature
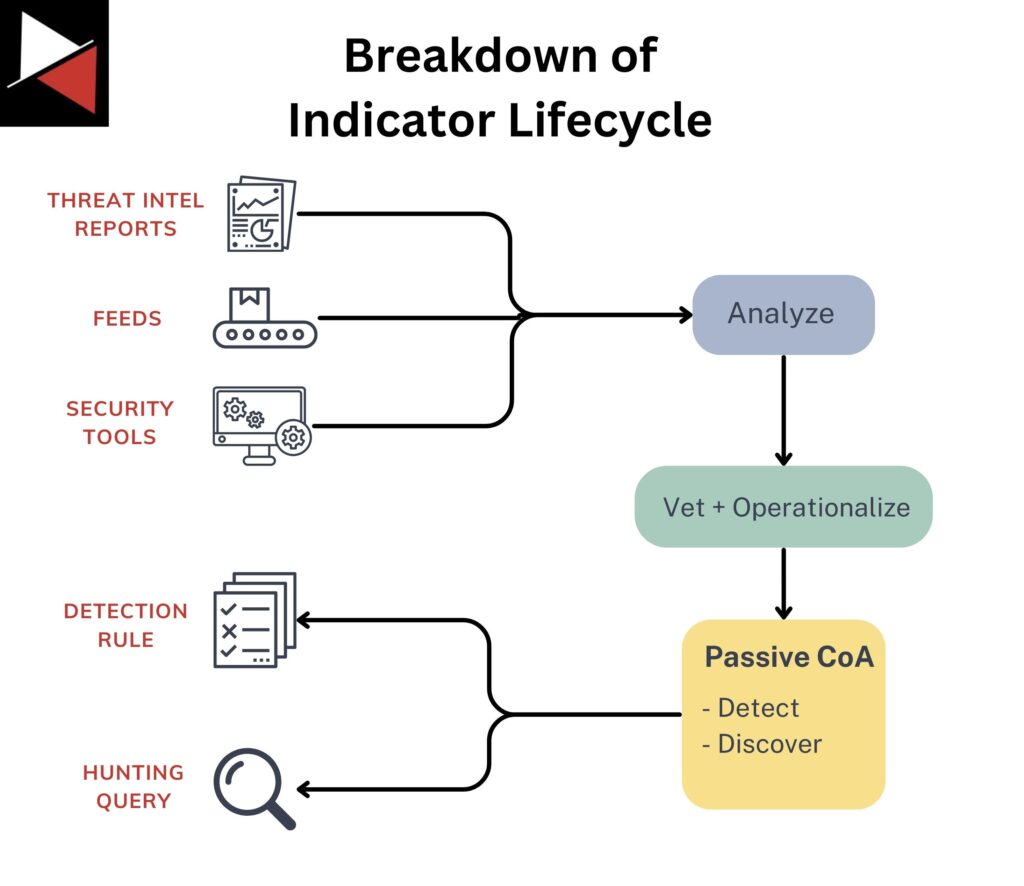
The first stage is to gather, examine, and operationalize the indicators.
You can gather indicators from threat intelligence reports, feeds, and your own security tools or datasets. Once gathered, you examine an indicator to ensure it is legitimate, relevant to your threat model or intelligence requirements, and can be operationalized. Finally, operationalizing means translating that indicator into a form your security tools can use, such as a detection rule or threat hunting query.
Mature to Utilized
A mature indicator is an indicator that is ready to be utilized by your security tools. You typically have two ways of using an indicator based on the Courses of Action (CoA) matrix:
- Detect: Identifying an adversary’s current activities by creating detection rules.
- Discover: Identifying an adversary’s past activities that have gone undetected by running threat hunting queries.
Which passive CoA you choose will depend on your intelligence requirements, tools, logging capabilities, and the type of indicator you are processing. You may be limited in how you utilize indicators based on these factors.
The Courses of Action (CoA) matrix is an intelligence-driven method for planning and keeping track of all the different defensive actions you can take to counter a cyber attack. Actions exist on a scale from passive countermeasures like detect and discover to active countermeasures like deceive and destroy. A CoA matrix is something every security team should have visibility of so they can see who is doing what to defend against attacks.
Utilized to Revealed
Utilizing an indicator will often generate new indicators that kickstart the lifecycle again. This is known as pivoting. You start with one data point, search for it to provide more context, and then discover another one to investigate. Pivoting is a fundamental skill for any security analyst but a downright way of life for threat intelligence analysts.
For example, using an indicator during intrusion analysis will allow you to find other indicators and build a complete picture of the attack. Meanwhile, using an indicator as a basis for a threat hunting hypothesis will allow you to expand the scope of your threat hunt and uncover malicious activity.
Case Study
Let’s see the indicator lifecycle in action using a case study. This will showcase how to use the lifecycle when encountering indicators in your daily work and get the most out of them.
Stage 1: Revealed
During your daily sweep of threat intelligence reports, you come across one related to your organization and matching your intelligence requirements. Reading through the report, you come across a domain the adversary uses to stage their Command and Control (C2) infrastructure. The domain name is badguy[.]com.
You decide it will be useful to hunt for this domain to see if you can find any suspicious activity. You have the tools and logs to perform the hunting and vet the intelligence to ensure it is legitmate. Now you can get started operationalizing.
Stage 2: Mature
Your security team uses Elastic as their Security Information and Event Management (SIEM) solution. To prepare your indicator for use with Elastic, you create a threat hunting query using the solution’s propriety log querying language ES|QL (Elasticsearch Query Language). Your query looks like this:
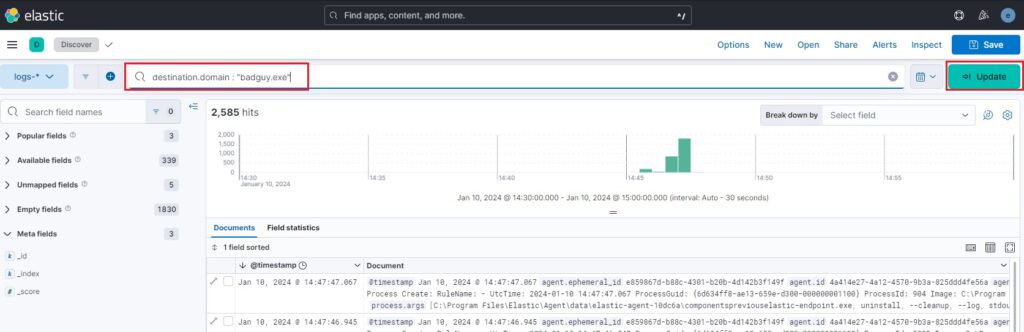
With your query prepared, you are now ready to perform the Discover CoA and try to find suspicious activity based on this indicator. Your bait is hooked, and you are ready to start fishing.
Stage 3: Utilized
You execute the threat hunting query, and after some time, you see results. John Smith’s machine visited that domain yesterday, not using a web browser but an executable you haven’t seen before called backdoor.exe.
You have used an indicator (badguy[.]com), and new indicators have been revealed (backdoor.exe – the filename, file hash, file path, etc.). Now you can pivot to this new data point and hunt for backdoor.exe to see if any other machines have this executable, indicating they too may have been compromised.
There are many paths you could take at this point:
- Look into
badguy[.]commore to find related network indicators to hunt for. - Examine network connection data from the compromised machine.
- Look for other malware or IOCs on the compromised machine.
- Follow
backdoor.exeand its related indicators. - And more!
At this point, it is important to remember that indicators lead to more indicators, good or bad. The best way to stay on track is to follow the lifecycle, vet the indicators you come across, and use structured analytical techniques like the Cyber Kill Chain, Diamond Model, and MITRE ATT&CK framework to map out the intrusion.
To learn about the challenges you will face using indicators in the real world, read Top 5 Challenges With Indicators and How to Overcome Them.
Conclusion
Indicators are great. They let you detect and discover things in your environment, move your investigation along by pivoting between them, and learn how an adversary achieves their strategic objectives.
You have discovered what makes a key indicator, the role indicators play in cyber threat intelligence, and a structured approach to using indicators with the indicator lifecycle. Use the case study discussed to practice working with indicators using your data sets and integrate this model into your daily work. Good luck!
Frequently Asked Questions
What makes a good indicator?
A good indicator for you may not be the same as a good indicator for someone else. You may want an indicator that produces zero false positives so you can use it for detections, whereas someone else may want an indicator that has a higher false positive rate but allows them to hunt for threats. Determining if an indicator is good should be based on how you plan to use that indicator. This happens as you move between the Mature and Utilized stages of the indicator lifecycle.
What indicators should I focus on?
Not all indicators are created equal. Threat actors can easily change atomic and computed indicators to evade detection. However, changing their TTPs (behavioral indicators) takes much more effort, so these often stay consistent between attack campaigns. Aim to focus on these indicators to create more robust detection rules and hunting queries. Read Elevate Your Threat Detections Using the Almighty Pyramid of Pain to learn more.
Should I keep using an indicator?
Indicators are useful until they are not. They have a limited lifespan that the adversary determines. When an adversary changes their indicators, you must retire the indicators you used to detect, track, or hunt for them. Typically, indicators have a shelf life of 30-60 days, where they might be useful. A good way to track this is with decaying models that you can create to devalue indicators slowly over time.