The Traffic Light Protocol (TLP) is a framework for classifying information’s sensitivity and providing guidance on how to handle it. It is a designation system widely used in cyber security, particularly cyber threat intelligence.
This quick guide will teach you everything you need to know about the framework, from the four colors it uses to classify information to how to use it in the real world and implement it at your organization using a five-step process. You will learn the benefits of TLP and best practices that will fast-track your success, and you will be ready to use the framework today!
Let’s jump straight in and explore this classification system.
What is the Traffic Light Protocol?
The Traffic Light Protocol (TLP) is a standardized classification framework for securely sharing sensitive information in cyber security. It was created to facilitate effective information sharing while protecting sensitive information from unauthorized disclosure.
The framework uses four categories to classify information based on its sensitivity, how it should be handled, and who the appropriate audience is. Each category has a designated color based on the colors of a traffic light, hence the name. These designations help organizations and individuals determine how and with whom to share information in the cyber security community.
Sharing and collaboration are essential to protecting organizations from emerging cyber threats. TLP’s focus on human readability, ease of adoption, and person-to-person sharing streamlines this communication. Dissemination is a key stage of the cyber threat intelligence lifecycle.
TLP was designed to facilitate greater information sharing and break down walls that were siloing organizations from key intelligence. Since then, it has been widely adopted within the cyber security community and is supported by various government agencies, industry organizations, and standards bodies.
Let’s take a look at the four main TLP categories to gain a better understanding of how this framework works.
Traffic Light Protocol Categories
The Traffic Light Protocol uses four categories to classify information. These categories allow organizations to balance the need for collaboration in cyberspace and protecting sensitive data. They include red, amber, green, and clear.
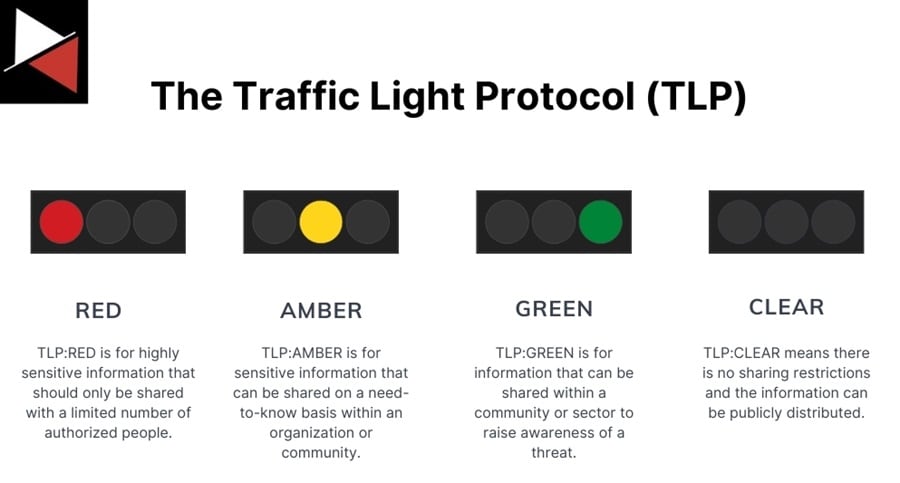
TLP:Red
This is the strictest TLP designation. It protects sensitive information that can only be shared with a limited number of authorized personnel. Sharing this information can result in significant risks to the organization’s privacy, reputation, or operations.
For example, if a meeting is classified as TLP:Red, anything discussed in that meeting should not be shared with any outside party. Additionally, any information shared between those present at that meeting should be shared verbally or in person to reduce the chances of data leaks.
TLP:Amber
Information marked with TLP:Amber should be shared only on a need-to-know basis within an organization or with trusted partners. Sharing this information may carry privacy, reputation, or operational risks, but doing so may prevent potential harm.
A subclassification of TLP:Amber is TLP:Amber+Strict. This designation means the information is restricted to the organization and not shared with its clients or trusted partners.
TLP:Green
When information can be shared within a cyber security community, it is marked as TLP:Green. This information is shared to raise awareness of emerging cyber threats unavailable via publicly accessible channels like news websites or research blogs.
Unless otherwise specified, TLP:Green information should not be shared outside the cyber security community or your sharing group. You will typically find this information on commercial threat intelligence platforms or within sharing groups (e.g., ISACS, ISAOS, CERTs, etc.)
TLP:Clear
TLP:Clear information can be shared without restriction. It carries minimal or no foreseeable risk of misuse and can be released publicly in accordance with copyright or other applicable rules.
You may occasionally see TLP:White on old documents. This category was used in an older version of the framework (TLP v1.0). Since 2022, TLP v2.0 has replaced it completely with TLP:Clear.
Now that you know the basics of TLP, let’s look at why you would want to use it.
Benefits of Traffic Light Protocol
TLP has helped improve the cyber security industry by providing a standardized system for classifying and handling sensitive information. It guides users through classifying, handling, and sharing data with others, all with an intuitive color-coding scheme.
This reduces the risk of accidentally disclosing sensitive information and promotes sharing crucial threat intelligence with the community to address security vulnerabilities and tackle threat actors collaboratively. It helps streamline communication, enhance situational awareness, and improve incident response by facilitating threat intelligence sharing and enhancing information exchange initiatives.
Here are the key benefits of adopting the Traffic Light Protocol for you and your organization.
- Compliance with data regulation: All organizations are subject to compliance regulations if they handle sensitive data (e.g., GDPR). TLP makes it easier to comply with these regulations by marking the sensitivity of data and ensuring employees know how to handle it appropriately.
- Fosters collaboration: TLP helps foster community collaboration and information sharing by providing clear guidelines for handling and sharing sensitive information. This allows multiple organizations to work together on a security project or respond to an incident.
- Enhances organizational reputation: The adoption of TLP shows that an organization takes protecting data seriously and is committed to ensuring it is handled appropriately. This enhances the organization’s reputation and builds trust with key stakeholders.
- Improve security: TLP allows organizations to safely share information about the latest cyber threats, detection techniques, and industry trends with the community. This controlled flow of intelligence empowers organizations to bolster their defenses while reducing the risk of disclosing sensitive information.
- Easy to adopt: TLP can be used on documents, emails, presentations, and within automated sharing exchanges like MISP. It is also optimized to be easy to use and human-readable, making it straightforward to implement in most organizations.
- Streamlines communication: TLP’s focus on person-to-person intelligence sharing, whether threat intelligence reports or emails, facilitates frequent and effective collaboration. Licensing terms, handling and encryption rules, or other overbearing restrictions do not hamstring it.
With these benefits in mind, let’s explore using TLP in real-world situations.
How to Use the Traffic Light Protocol
TLP is adaptable to various real-world scenarios, such as email and messaging, distributing documents, and sharing via automated information exchange like MISP or OpenCTI. Here are some popular sharing methods and how to use TLP with them.
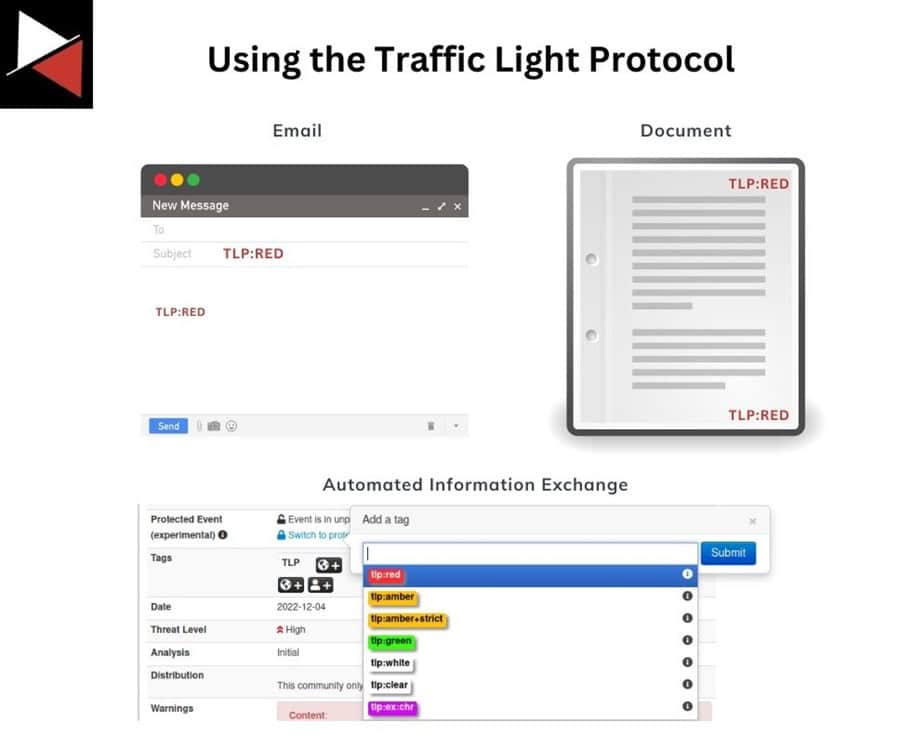
How to use TLP in Email
When exchanging emails that contain TLP-tagged information, you should indicate the TLP color in the Subject line and the email body before the designated information. This allows the recipient to see the TLP classification clearly and decide if they are the intended audience. If they are not, they should immediately report the incident.
To add the TLP designation, enter TLP: followed by the appropriate color and ensure you use capital letters (e.g., TLP:RED, TLP:AMBER, TLP:GREEN, or TLP:CLEAR). Keep this consistent for automated data protection tools and cohesive reporting.
How to use TLP in Documents
Documents that include a TLP designation should indicate the TLP color of the information in the header and footer of each page. It is advisable to right-justify TLP designations to avoid confusion with existing control marking schemes.
To ensure the TLP designation is legible, the TLP color should appear in capital letters and use a 12-point font type or greater. Again, capital letters are a requirement of the designation.
How to use TLP in automated information exchange
TLP usage in automated information exchanges is not defined in the standard framework and is left to the designers of such exchanges.
It is common for automated information exchanges to provide tags that users can add to their threat intelligence to provide additional context. This allows users to tag information using TLP designations and use sharing rules to ensure sensitive information is only shared with the appropriate audience.
TLP Best Practices
Knowing which TLP designation to use for a given piece of information can be challenging when using the framework in the real world. Here are some best practices to help you get started.
- If a recipient needs to share the information more widely than indicated by the original TLP designation, they must obtain explicit permission from the original source.
- The source of the TLP-labeled information is responsible for ensuring recipients understand and can follow TLP sharing guidance.
- The source of the TLP-labeled information can specify additional sharing restrictions that the recipients must adhere to, such as encryption requirements, licensing agreements, etc.
- TLP labels and their definitions are not intended to affect freedom of information or have legal ramifications.
- TLP is optimized for person-to-person sharing and is most effective in these situations, such as sharing documents, reports, presentations, messages, videos, and in-person meetings.
- Ensure clear documentation on the framework is easily accessible to all employees and training is provided before implementing TLP at your organization.
So, how can you get started implementing TLP today?
Implementing the Traffic Light Protocol
To implement TLP in your organization, you can follow these five simple steps:
- Identify sensitive information that needs protection: First, you must determine what information is sensitive to your organization and requires protection. This could include information about customers, operations, security vulnerabilities, or proprietary technologies. Techniques like crown jewel analysis (CJA) can help at this step.
- Use TLP to classify this information: Next, classify this information using the TLP categories so employees know how to handle this and what can be shared. It can help to add automation to speed up this process and ensure all new documents include a TLP classification.
- Create guidelines, training, and documentation on TLP: Once all sensitive information has been classified, you can develop policies and procedures for handling TLP-labeled information. This is an important step because it establishes how your organization will use TLP, ultimately dictating the success of implementing the framework.
- Train employees and key stakeholders: With your guidelines created, you can move on to training your employees and stakeholders on using TLP to handle sensitive information. This includes training employees on how to classify information with TLP, identify and report potential breaches of TLP guidelines, and procedures for sharing TLP-labelled information with others.
- Schedule periodic reviews to ensure TLP is being used appropriately: Finally, you want to periodically review how employees are using TLP, how documents are being labeled, and what information is being shared with the wider community. This will ensure that your TLP guidelines are understood and followed appropriately. You may find guidelines need to be revised, or employees need more training.
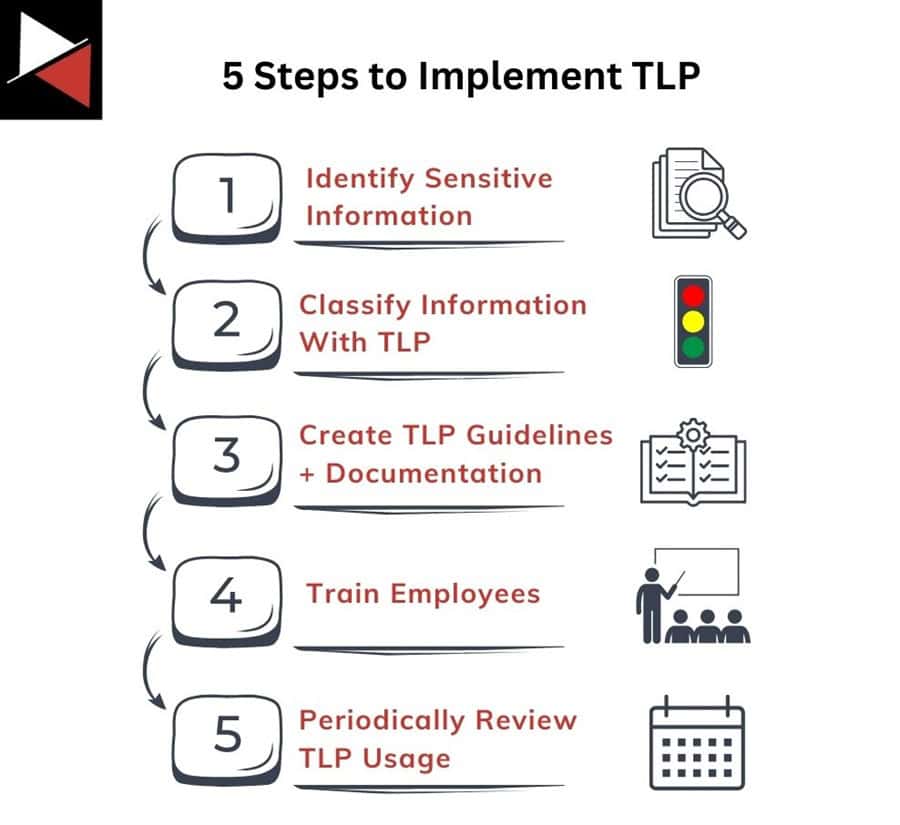
These five simple steps will help your organization start using TLP. Your success will largely depend on how you implement TLP and balance the need for information sharing, data protection, and limiting overhead.
Conclusion
The Traffic Light Protocol (TLP) is a fundamental designation system used throughout cyber security, particularly cyber threat intelligence, to classify information’s sensitivity and guide you on handling it.
It uses four colors to assign a sensitivity label to information. These labels dictate how it should be handled, shared, and protected. Using this system, organizations can more efficiently share information without worrying about inadvertently leaking sensitive data that could be used against them.
This guide has taught you everything you need to get started using TLP, from best practices to practical examples. It is now time for you to get your hands dirty and implement it at your organization using the five-step process demonstrated. Good luck!
Frequently Asked Questions
What Are the Four Traffic Light Protocol (TLP) Colors?
The Traffic Light Protocol (TLP) consists of four color-coded designations that categorize information based on its sensitivity and how it should be handled. The four designations include:
- TLP:Red: The strictest designation for the most sensitive information. This information should only be shared with a limited number of authorized people due to potential risks.
- TLP:Amber: This is assigned to the information that must be shared on a need-to-know basis within an organization and with its trusted partners/clients to prevent potential harm. It has a subclassification called TLP:Amber+Strict, which is information only to be shared within an organization and not its clients.
- TLP:Green: This information can be shared within a cyber security community to raise awareness about emerging threats, which are unavailable through public channels like news sites or threat research blogs. It should not be shared outside of the community.
- TLP:Clear: This is for information that can be shared freely without restrictions. It carries minimal risk of misuse and can be shared freely in accordance with copyright laws.
Who Uses the Traffic Light Protocol?
The cyber security industry has widely adopted the Traffic Light Protocol (TLP) to facilitate information sharing between organizations. It is used by numerous information-sharing communities (e.g., ISACS, ISAOS, CERTs, etc.), businesses, standard bodies, and government agencies.
Why Should I Use the Traffic Light Protocol?
The Traffic Light Protocol (TLP) offers many benefits regarding classifying and handling sensitive information. The main ones include:
- Compliance with data regulation: TLP makes it easier to comply with these data regulations and ensures employees know how to handle sensitive data appropriately.
- Fosters collaboration: TLP helps foster community collaboration and information sharing by providing clear information-sharing guidelines for sensitive information.
- Enhances organizational reputation: The adoption of TLP shows that an organization takes data protection seriously and is committed to handling sensitive data appropriately.
- Improve security: TLP allows organizations to safely share sensitive information about the latest cyber threats, detection techniques, and industry trends with the community to bolster everyone’s defenses.
- Easy to adopt: TLP can be used across various information-sharing mediums (documents, emails, etc.) and is optimized to be easy to use and human-readable.
- Streamlines communication: TLP’s focus on person-to-person intelligence sharing facilitates frequent and effective collaboration.
Why Does TLP Red Mean?
Red is the strictest TLP designation used to protect the most sensitive information. Information marked TLP:Red can only be shared with a limited number of authorized personnel, as sharing it can result in significant risk to an organization’s privacy, reputation, or operations.
Why Does TLP White Mean?
White was an old TLP designation used in TLP v1.0, replaced by Clear in TLP v2.0. Information labeled TLP:Clear can be freely shared as it carries minimal or no foreseeable risk of misuse. However, if you release it publicly, make sure you comply with copyright or other applicable rules.