Cyber threat intelligence can be a game-changer for most organizations. It enables them to proactively manage the risks they face when conducting business in the cyber domain. But what does this look like? What key roles and responsibilities does a CTI team have?
This guide answers these questions by explaining how a CTI team fits into the larger business and the key roles within a CTI team that are required to fulfill its mission. This includes general roles, like CTI manager and analyst, and specialized roles, such as CTI engineer, threat hunter, and dark web researcher.
Each role is pivotal in ensuring the CTI team can collect, analyze, and share threat intelligence that informs key business decisions. That’s why this guide also showcases how these roles work together by breaking the CTI process into the OODA loop, CTI lifecycle, and F3EAD loop.
Let’s get started exploring what you need to build a great CTI team!
Understanding the Role of a CTI Team
Before we discuss the roles and responsibilities of a cyber threat intelligence (CTI) team, we need to take a step back and examine how they fit into the broader organization. It is important to remember that cyber security plays a small role in the overall business.
You have the big movers that propel a business forward, like marketing, sales, services and customer fulfillment, leadership and management, and product development. Then, you have the business enablers who keep operations going, like finance and accounting, human resources, legal and compliance, customer service, and information technology.
For most businesses (excluding vendors), cyber security is just one component of information technology, and CTI is just a piece of cyber security.
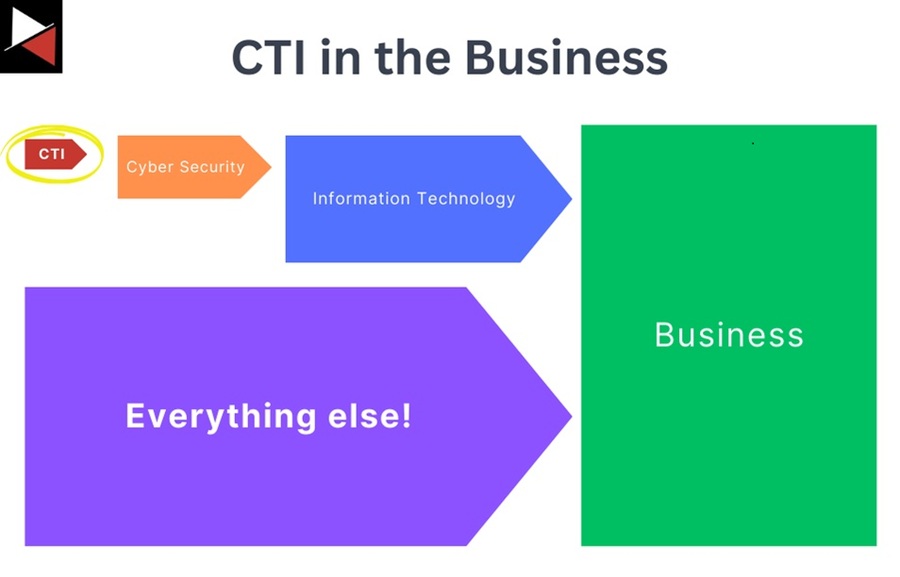
This is how CTI is viewed from the top down: It is just a tiny part of a supporting function that ultimately exists to reduce a business’s risk in its day-to-day operations. Your role as a member of CTI is to provide actionable insights that can be used to reduce business risk.
You don’t get paid to track threat actors, research the latest tactics, techniques, and procedures (TTPs), or hunt down bad guys – despite what your job description might say. Instead, you are there to provide stakeholders with insights that help them make informed decisions that manage the cyber risks that impact the business.
This doesn’t mean CTI is about ticking boxes and wearing hard hats. Far from it!

CTI is a proactive approach to defending an organization against cyber threats. It involves collecting, analyzing, and disseminating intelligence about cyber threats and risks that impact the entire business.
Just because CTI is a small piece of the puzzle when it comes to running a business, its potential impact on all business units makes it fundamentally different from most other cyber security functions.
It can support technical functions like security operations, incident response, and vulnerability management. But it can also help business executives reduce their digital footprint, the marketing department protect the brand’s identity, and finance minimize fraud.
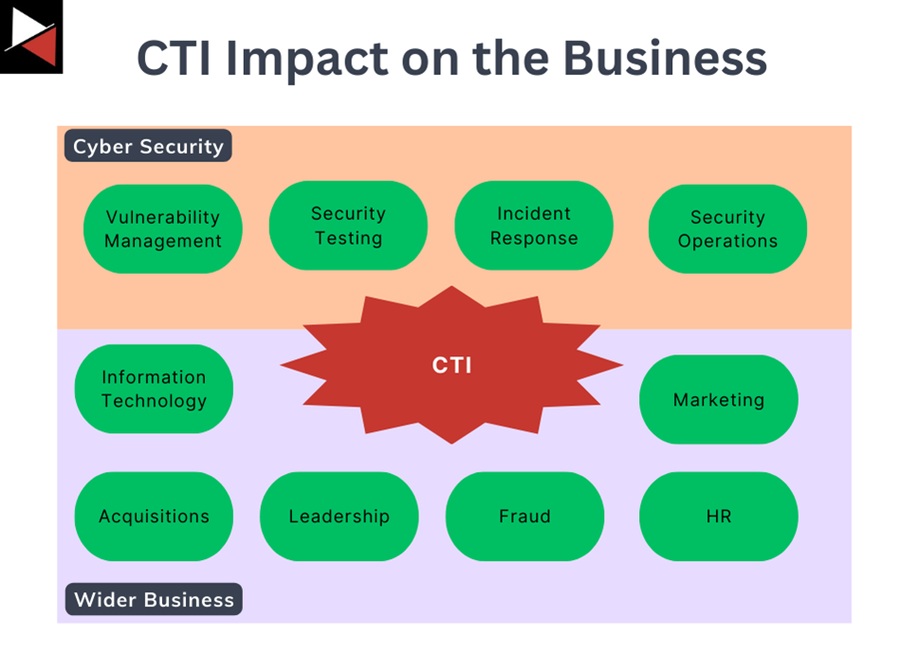
This is because not all threat intelligence is the same. Intelligence about real-time attacks and vulnerabilities differs from intelligence about geopolitical events and emerging threats exploiting technological trends.
Good CTI teams do not just focus on one type of intelligence; they use all three to bring value to the entire business!
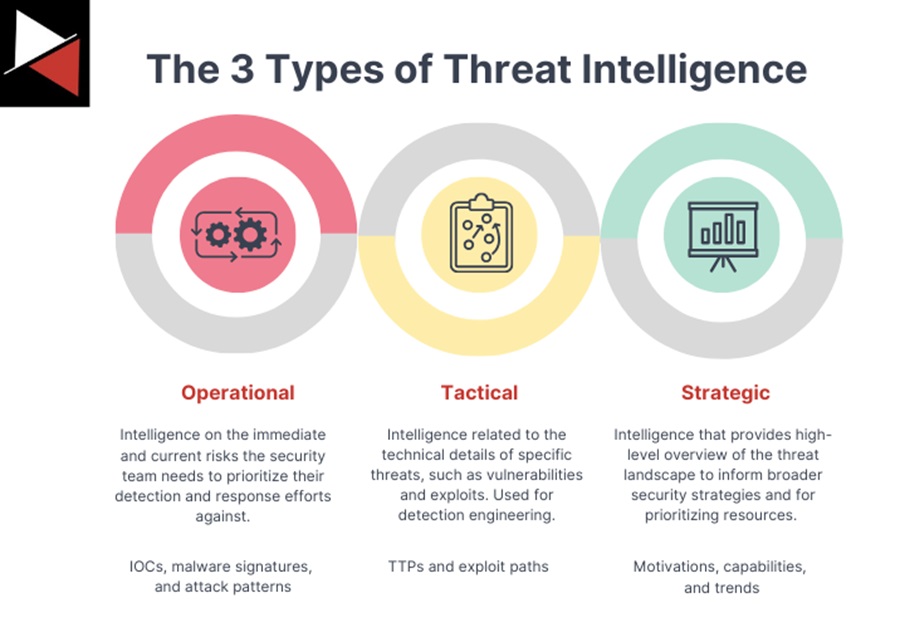
Operational Intelligence
Focus: Day-to-day security operations.
Purpose: Provide intelligence on the immediate and current risks the security team needs to prioritize their detection and response efforts against. It includes Indicators of Compromise (IOCs), malware signatures, and attack patterns.
Tactical Intelligence
Focus: Short to medium-term actions and operations.
Purpose: Provide intelligence related to the technical details of specific threats, such as vulnerabilities and exploits. Defenders use this to identify and mitigate particular threats using detection rules and mitigation policies using security tools. The focus is on targeting threat actors’ tactics, techniques, and procedures (TTPs) rather than individual indicators.
Strategic Intelligence
Focus: Long-term planning and decision-making.
Purpose: Provide a high-level overview of the threat landscape to inform broader security strategies (e.g., developing policies and procedures, resource allocation, and prioritizing investments). It includes the motivations, capabilities, and trends.
It is important to note that tactical and operational intelligence can be defined differently, depending on who you are talking to in CTI. This is often the case in North America, where tactical and operational intelligence are flipped (CrowdStrike). The descriptions above align with how operational, tactical, and strategic intelligence are defined in the United Kingdom and Europe (CREST).
This unique position requires the CTI team to have a diverse range of skills and roles. Let’s explore them!
Key Roles in a CTI Team
When looking at what roles make up a CTI team, you can split them into two main categories:
- General: These are roles typical across nearly every CTI team. They are the first ones you will hire and are the bedrock required to fulfill the essential function of the CTI team – collecting, analyzing, and sharing intelligence.
- Specialist: These roles are required to fulfill specific intelligence requirements. Not every CTI team needs them, and they are often fulfilled by members across the broader cyber security function.
Let’s first explore the general roles you must fulfill to have a functioning CTI team.
General Roles
General roles are the core positions that all CTI teams must fill. They allow the team to complete the CTI lifecycle by generating intelligence requirements, collecting data, analyzing it to produce intelligence, and then disseminating it to key stakeholders.
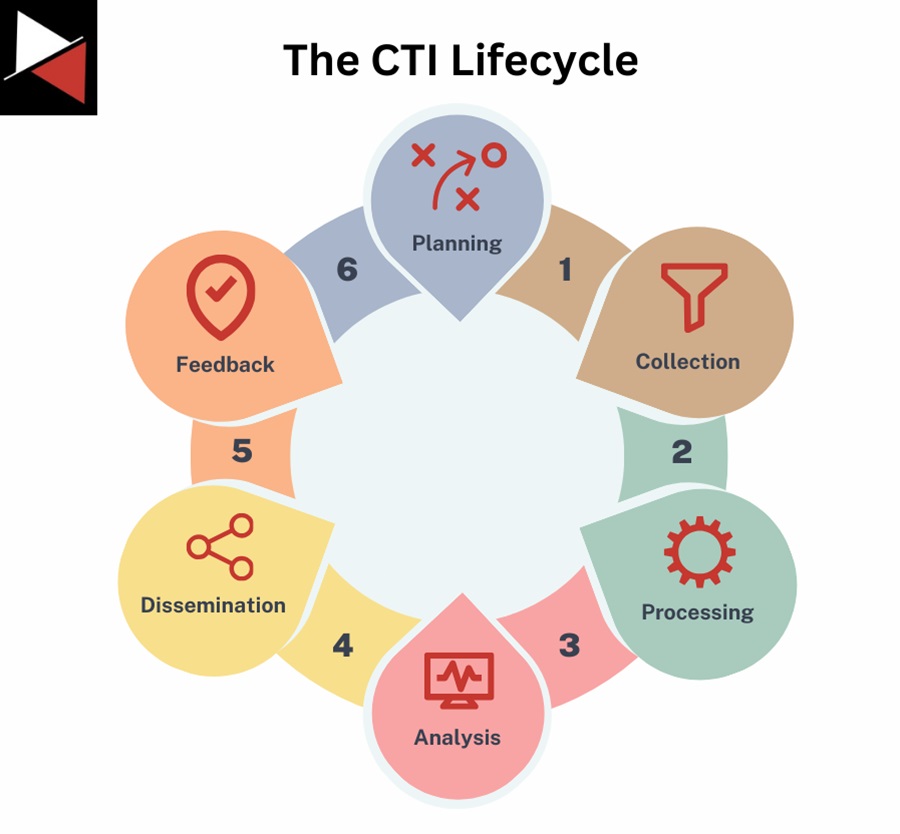
Two main roles are required to successfully complete the CTI lifecycle and produce an intelligence product to share with key stakeholders: a CTI analyst and a CTI manager (or lead).
CTI Analyst
A CTI analyst is involved in the day-to-day operations of the CTI team and, through their work, drives intelligence production forward.
- They help the CTI manager to define intelligence requirements and requests for information (RFIs) during the Planning stage.
- They gather data that addresses the intelligence requirements during the Collection stage. This includes open sources, the dark web, security feeds, and security incidents.
- They analyze this data to turn it into intelligence. This includes working with Indicators of Compromise (IOCs) and tactics, techniques, and procedures (TTPs) and using Structured Analytical Techniques like Analysis of Competing Hypotheses (ACH).
- Finally, they package this intelligence into a digestible product and share it with key stakeholders during the Dissemination stage.
This work is the bedrock for any CTI function. It requires general IT and cyber security knowledge (e.g., how a cyber attack happens, security controls, etc.).
It also requires analytical skills and intelligence tradecraft, such as knowing where and how to collect data, effectively analyzing data to avoid bias, and packaging this intelligence for consumption.
If you are new to CTI, you will start here, develop your skillset, and then choose to branch out into a more specialist role or one with more responsibilities, like a CTI manager or lead.
CTI Manager / Lead
Another key role all CTI teams must have is a CTI manager or lead. They oversee the CTI function and ensure that the intelligence produced aligns with business and security objectives.
They are most instrumental in the Planning and Dissemination phase of the CTI lifecycle.
- At the Planning stage, they will collaborate with key stakeholders to define “good” intelligence requirements and assign the completion of these requirements to CTI analysts on their team.
- During the Dissemination stage, they will coordinate with stakeholders, including SOC, incident response, and risk management teams, to ensure the shared intelligence is actionable and supports decision-making.
Outside of the CTI lifecycle, a CTI manager will be responsible for interfacing with other teams within the organization and intelligence initiatives outside the organization (e.g., ISACs, government agencies, etc.).
They act as a bridge between CTI and other security teams (SOC, Red Team, IR, CISO) or other business units that could benefit from intelligence (e.g., marketing, fraud, etc.).
This role requires experience running CTI operations and delivering intelligence products, strong interpersonal skills to facilitate the management of people and processes, and the ability to understand business objectives and how intelligence can be used to support them.
A CTI manager is the highest role one can reach in the CTI team (in terms of the corporate ladder). However, CTI analysts can also choose to transition to a range of specialist roles outside of management.
Specialist Roles
You are good to go once you have a CTI analyst and CTI manager! You have the minimum operational capacity to begin producing intelligence that supports your business. As your team matures and develops its capabilities, more specialist roles may be required to fulfill more complex intelligence requirements.
For instance, you may have an intelligence requirement that requires you to dissect malware and hunt for variants of it in your environment. In that case, you need a malware analyst (or reverse engineer) and a threat hunter. You may have a requirement to search the dark web for employee data and get ahead of potential data breaches. To fulfill this, you need a dark web researcher.
These specialist roles became apparent as you are tasked with intelligence requirements that require specialist knowledge or skills. They may be fulfilled by someone within the intelligence team, a member of another security team, or a third-party service provider.
Either way, awareness of these roles is essential, as you will encounter them during your CTI career.
Threat Hunter
A threat hunter is responsible for proactively searching for hidden threats inside the organization’s environment. They work from the premise that security tools will not detect all threats. Hence, they must proactively seek ones that have bypassed traditional security controls.
To do this, they must deeply understand how cyber attacks happen from a technical perspective, what traces threat actors leave behind, and how to use security tools to search for them. This work requires working closely with SOC (Security Operations Center) and Digital Forensic and Incident Response (DFIR) teams to identify attacker behaviors using frameworks like MITRE ATT&CK.
Threat hunters are typically consumers of the intelligence produced by the CTI team. However, organizations often group these two roles, and threat hunting falls under the responsibility of the CTI team. As such, a common position CTI analysts transition into is threat hunting (if they enjoy technical work).
You can also have external threat hunting. A threat hunter will hunt for adversary infrastructure using data external to a company, such as passive DNS records, WHOIS data, and TLS certificates. Read C2 Hunting: How to Find C2 Server with Shodan to learn more.
CTI Engineer
CTI teams need tools, technology, and people to operate effectively. This requires someone to build and maintain the technology the CTI team uses, including Threat Intelligence Platforms (TIPs), custom tooling, and automation that streamlines operations. If your CTI team has the budget, you will hire a CTI engineer to fulfill this role.
They may work with any of the following technologies:
- Open-source TIPs to support the collection and storage of data. Two widely used platforms are MISP and OpenCTI.
- Commercial TIPs and threat intelligence service providers to integrate them into the CTI team’s day-to-day operations. Popular CTI vendors are Recorded Future, Anomali, and Group-IB.
- Custom tools that improve the efficiency of the CTI team’s work could be used during the Collection, Analysis, or Dissemination stages of the CTI lifecycle. This often includes working with STIX/TAXII protocols.
- Security tools the company uses (e.g., SIEM, EDR, SOAR) to integrate them with the intelligence the CTI team produces.
Technical Writer
A technical writer is an often-overlooked role in a CTI team. They play a crucial role in documenting and communicating intelligence findings in a clear, structured, and actionable manner.
This includes:
- Writing documentation and Standard Operating Procedures (SOPs) for the CTI team to follow.
- Editing and reviewing the intelligence products produced by the CTI team to ensure clarity, accuracy, and consistency.
- Translating technical intelligence into non-technical language for executives and decision-makers.
- Assisting in preparing intelligence for sharing with Information Sharing and Analysis Centers (ISACS), government agencies, or security vendors so that sensitive information is handled appropriately.
Dark Web / OSINT Researcher
Dark web research and advanced OSINT require specialist tradecraft and skills for two reasons:
- To know how to find the information you are looking for.
- Maintain operational security when performing research and do not bring undue risk to yourself or the organization.
This role requires you to conduct deep-dive research on threat actors and emerging threats by monitoring dark web forums, hacker chat groups, social media, breach websites, and criminal marketplaces. This research often feeds into an organization’s attack surface management to reduce risks based on current exposure to the threat landscape (e.g., leaked credentials, known targeting by threat actors, etc.).
Malware Analyst / Reverse Engineer
Malware is often the bread and butter of a cyber attack. It is rare to see an attack that does not use some form of malware, be it for initial access, command and control, or data exfiltration.
This popularity often means the malware used during an attack can be a valuable intelligence source. By analyzing a piece of malware, you can learn a lot about a threat actor, their infrastructure, and their capabilities. Then, use the Diamond Model to find questions that will generate leads, insights, and actionable intelligence.
Unfortunately, dissecting a piece of malware requires much technical skill. This is why malware analysis, or reverse engineering (if necessary), often requires a specialist role that the CTI relies upon to determine the functionality and behavior of malware samples. From this information, the CTI team can then perform analysis to generate intelligence.
This role could be outside the CTI team (e.g., you have a malware analysis team at your organization), but bringing these skills locally to the CTI team to streamline operations is often better.
If you want to start practicing your skills as a malware analyst, read this article on automatically deploying a malware analysis environment.
Digital Forensics and Incident Response Specialist
A role similar to a malware analyst / reverse engineer is that of a DFIR specialist. A DFIR team is another component of a cyber security function. They are responsible for investigating and responding to significant security incidents.
With smaller CTI teams, analysts or managers will liaise with the DFIR team to collect and provide intelligence. As your CTI team grows, having a DFIR specialist with a background in incident response can be helpful.
It allows you to have someone internal to your team liaise with the DFIR team, translate their findings into intelligence, and run CTI-focused DFIR activities using their incident response knowledge. This role strengthens the CTI team’s ability to collect data from internal sources and interface with other security functions.
Strategic Intelligence Analyst
Operational and tactical threat intelligence is not the only type of intelligence that CTI teams can produce. Strategic intelligence focuses on geopolitical, economic, and sector-specific cyber risks from a high-level perspective, providing a bird’s-eye view of the threat landscape. Insights from this intelligence can inform broader security strategies (e.g., policies and procedures, resource allocation, and prioritizing investments).
If your intelligence requirements require a great deal of strategic intelligence to fulfill, investing in a strategic intelligence analyst for your CTI team might be worthwhile. They can produce high-level intelligence reports for executives and board members focusing on shaping long-term security strategies based on threat trends.
This role often requires structured analysis to build likely scenarios of future events, generate hypotheses related to these predictions, and derive recommended courses of action to reduce future risk.
Gatekeeper
Have you considered the ethical and legal responsibilities of your CTI team? When you interact with cybercriminals on dark web forums, marketplaces, or message groups, these can become points of contention.
A gatekeeper helps you resolve this. They are responsible for the activities the CTI team conducts from a legal and ethical perspective and give the go-ahead for those operations.
- If the CTI team wants to buy stolen credentials to see if the organization has been impacted, you must run it by the gatekeeper.
- If your team wants access to a Telegram channel run by cybercriminals to gain insight into their activity, you must run it by the gatekeeper.
- If you want to create a fictitious persona to illicit information from cybercriminals in a dark web forum, you must run it by the gatekeeper.
The gatekeeper sits outside the day-to-day work of the CTI team. Still, it should be the CTI manager’s first call to ensure all operations align with the organization’s legal responsibilities and ethical policies. This role requires a strong knowledge of cyber security laws and communicating with the business’s legal counsel to manage the risk around CTI operations.
Not all CTI teams will need a gatekeeper; consulting the business’s data protection officer or legal team will often suffice. However, if you plan on interacting with cyber criminals, you may require a gatekeeper to ensure your CTI team is 100% certain of the legality and ethicality of their actions.
How a CTI Team Works Together
So, how do all these roles and responsibilities fit together? How does the core CTI team fit into the wider business? How do specialist roles fit within the CTI team?
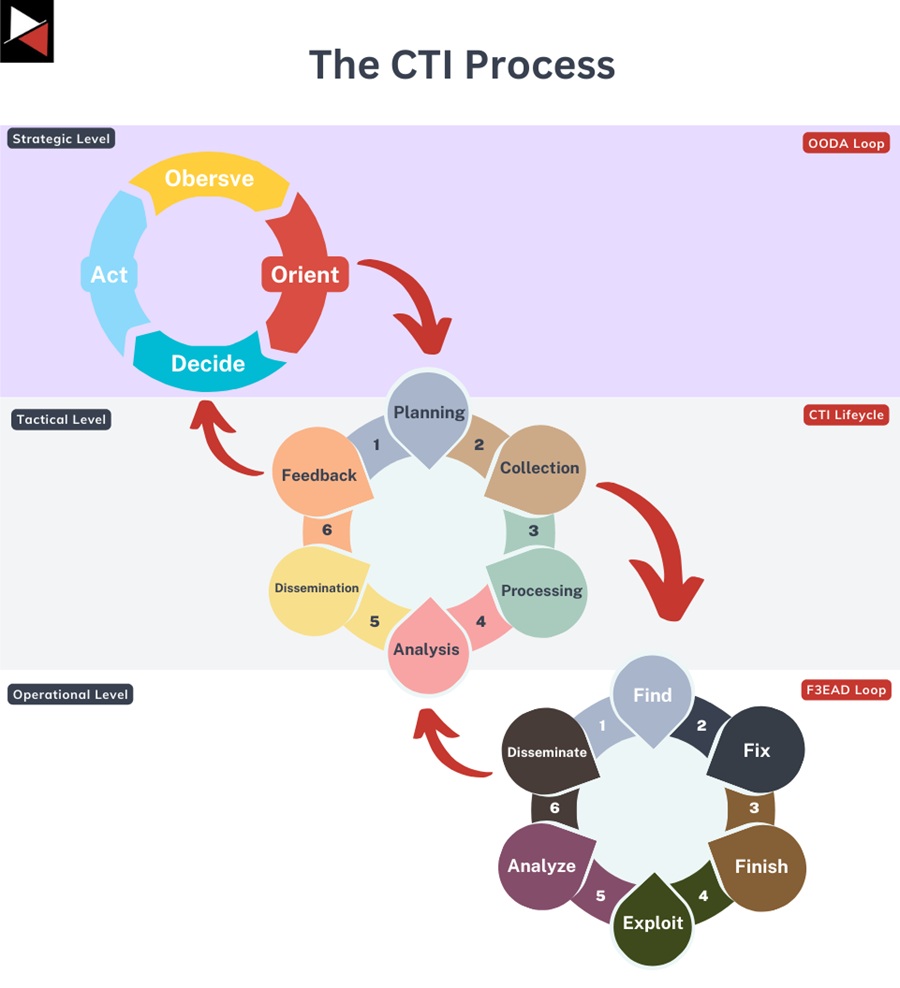
To understand how these roles fit together, it helps to consider the intelligence process at an organization. This process is composed of three distinct cycles:
- OODA loop: A general decision-making process made up of four steps: (1) Observe – a user makes an observation; (2) Orient – they contextualize what they observe based on everything they know; (3) Decide – they formulate the best course of action; (4) Act – they execute that action.
- The CTI lifecycle: The 6-stage process of generating intelligence from Planning what needs to be produced to Collecting and Analyzing data to Disseminating the intelligence generated.
- F3EAD cycle: This 6-stage cycle sits inside the CTI lifecycle, starting at the Collection stage and feeding into the Analysis stage. It includes the specific operational tasks that must be performed to turn data into intelligence. These steps are Find, Fix, Finish, Exploit, Analyze, and Disseminate.
Each loop is an abstraction that maps to the three levels at which a business operates (strategic, tactical, and operational):
- At the strategic level, there is the OODA loop. Here, key stakeholders like executives and department heads make strategic, long-term decisions about the direction they want to take the business.
- Next, you have the tactical level, where the CTI manager takes strategic decisions and turns them into actionable objectives that their CTI team can fulfill using the CTI lifecycle.
- Finally, you have the operational level, where the nitty-gritty intelligence work happens using the F3EAD cycle. This is the day-to-day work that generates the intelligence product.
You can think of each loop as a gear. The big gear (OODA loop) will result in multiple turns of the middle gear (CTI lifecycle). One request from a stakeholder could result in multiple intelligence requirements. Depending on the complexity of the intelligence requirement and its associated RFIs, each intelligence requirement could then require multiple cycles of the F3EAD loop to fulfill.
To see how this happens, consider this example of a typical intelligence engagement:
- A key stakeholder sees something on the news about a Microsoft exploit. This kickstarts their OODA loop. They Observe that something may affect their business and must Orientate themselves to the threat landscape to make a Decision and then take Action.
- To do this, they task their CTI team with generating a report (e.g., “What risk does this exploit pose to our organization? Have we been impacted?”). The CTI Manager will take this request and generate a priority intelligence requirement that a CTI Analyst can fulfill. This is the start of the CTI lifecycle at the Planning stage
- Once tasked with an intelligence requirement, the CTI Analyst will then need to collect data about this exploit and their environment during the Collection stage of the CTI lifecycle. As part of this stage, they will need to start the F3EAD cycle to Find – locate any potentially impacted systems, Fix – gain access to those systems, Finish – confirm if they are vulnerable, Exploit – investigate if they have been compromised, and Analyze – pull this information together to produce intelligence.
- The CTI Analyst feeds their analysis into the Analysis stage of the CTI lifecycle, which is then Disseminated by themselves or the CTI Manager to the key stakeholder.
- The stakeholder then uses the intelligence to make a Decision and take Action, finishing their OODA loop.
This example shows where the CTI Manager and CTI Analyst fit into the overall picture. However, where do the specialist roles fit in?
Roles like threat hunter, dark web researcher, malware analyst, DFIR specialist, and strategic intelligence analyst are needed during the F3EAD cycle. Producing actionable intelligence can require specialist skills and knowledge to Find, Fix, Finish, and Exploit data. The specific expertise required will depend on the type of intelligence requirement the team has been tasked with fulfilling.
The other specialist roles discussed (e.g., CTI engineer, technical writer, and gatekeeper) are supporting functions that enable the CTI team to be more efficient, ensure accurate reporting, and adhere to legal and ethical standards.
Conclusion
Cyber threat intelligence is a game changer for businesses. It allows you to proactively manage risk using the latest threat landscape insights. However, to do this, you need a fully stacked CTI team.
This guide explored the key roles and responsibilities you must fulfill to have a successful CTI team, from general roles like CTI analyst to specialized roles like dark web researcher. It also highlighted how these roles work together and how CTI fits into the wider business using the OODA loop, CTI lifecycle, and F3EAD loop.
Now that you know each of the key roles and responsibilities within a CTI team, which one(s) are you currently doing or aspire to do in the future? Let me know in the comments!
Frequently Asked Questions
What is a CTI Team?
A Cyber Threat Intelligence (CTI) team is a specialized unit with a cyber security function. They are responsible for collecting, analyzing, and disseminating intelligence about cyber threats to help organizations manage the risks they face. The team aims to identify threats proactively, understand adversary tactics and techniques, and provide actionable insights to help key stakeholders make informed decisions.
What is the Role of CTI?
Cyber Threat Intelligence (CTI) is a proactive approach to defending an organization against cyber threats. It involves collecting, analyzing, and disseminating intelligence about cyber threats and risks that impact the entire business. CTI aims to help an organization manage its risks when conducting business based on its threat landscape.
How to Build a CTI Team?
Building a Cyber Threat Intelligence (CTI) team requires careful planning, skilled professionals, and the tools to effectively collect, analyze, and share threat intelligence.
You first need to select who will manage your CTI team and work with them to determine the objectives that the CTI function should aim to fulfill. From there, they can select CTI analysts and tools/platforms to help them achieve these objectives. Finally, the CTI manager and their analysts must work together to develop processes and workflows to ensure efficient intelligence collection, analysis, and dissemination.
What is a CTI Analyst?
A CTI analyst is involved in the day-to-day operations of the CTI team and drives intelligence production forward with their work. They are mainly responsible for the Collection, Analysis, and Dissemination stage of the CTI lifecycle. This role requires general IT and cyber security knowledge and analytical and intelligence tradecraft skills (e.g., identifying IOCs, analyzing TTPs, tracking threats).




