Cyber threat intelligence (CTI) is built on models and frameworks that allow you to turn raw data into actionable intelligence. One of the key operational models you will use as a CTI analyst is the F3EAD intelligence loop.
This guide will teach you how to use this model to structure your day-to-day intelligence work, from finding the needed data, exploiting it with specialist skill sets, and disseminating it with key stakeholders. You will learn where the F3EAD loop fits into the CTI process, how to complete each of its six stages, and see the model in action with practical examples.
The F3EAD loop is a fundamental model in CTI that you will use daily to fulfill your intelligence requirements. Let’s jump in and explore it!
What is the F3EAD Intelligence Loop?
The F3EAD loop is an alternative intelligence loop to the traditional CT lifecycle. It was initially created for military, counterterrorism, and special forces operations to target high-value individuals for “kill or capture.”
This target-centric approach empowered the fusion of intelligence analysis with military operations, providing holistic thinking, flatter command structures, and more informed decision-making. That said, its value extends beyond military operations.
F3EAD has become a popular intelligence loop within the CTI industry to more accurately define the operational tasks required to fulfill an intelligence requirement. CTI has replaced “kill or capture” with “remove or restrict.”

The CTI lifecycle is excellent for providing a high-level overview of generating an intelligence product, from planning to dissemination. However, it fails to include key stakeholders in the intelligence process, define key operational tasks, or incorporate the specialist knowledge and skills required to fulfill some intelligence requirements.
The F3EAD intelligence loop fills these gaps using a target-centric approach that provides a more granular description of what is required to collect, process, and analyze the data needed to generate actionable intelligence. It can even be used alongside the traditional CTI lifecycle between the Collection and Analysis stages.
This allows an organization’s intelligence requirements to be examined from an operational, tactical, and strategic perspective.
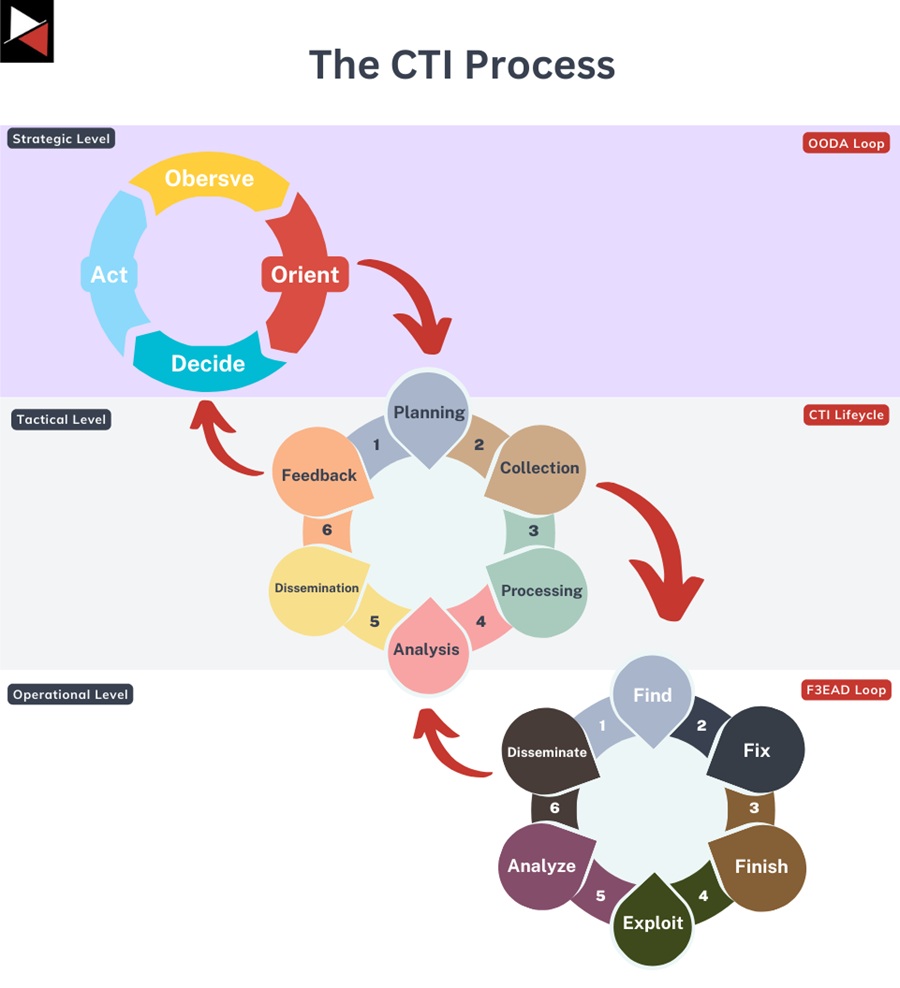
Multiple decision loops provide the appropriate abstraction for key stakeholders, CTI managers, and CTI analysts.
- Stakeholders focus on making decisions using the OODA loop.
- CTI managers focus on generating intelligence from a tactical perspective with the CTI lifecycle.
- CTI analysts focus on the day-to-day operations required to generate the intelligence product using the F3EAD loop.
It is important to note that the in-depth intelligence analysis described by the F3EAD loop is not always necessary to fulfill an intelligence requirement. Most intelligence requirements can be completed using the CTI lifecycle and do not require specialist skillsets or the deployment of advanced collection capabilities that the F3EAD loop introduces.
Nevertheless, the F3EAD is a valuable tool for breaking strategic intelligence requirements into operational Request for Information (RFI) tasks that a CTI must complete to fulfill the stated requirement.
Let’s examine the six stages of the F3EAD loop to understand how it is used in intelligence engagements.
The Six Stages of the F3EAD Intelligence Loop
The F3EAD intelligence loop contains six stages that take you from finding data to disseminating structured intelligence that a key stakeholder can use. These stages are Find, Fix, Finish, Exploit, Analyze, and Disseminate.
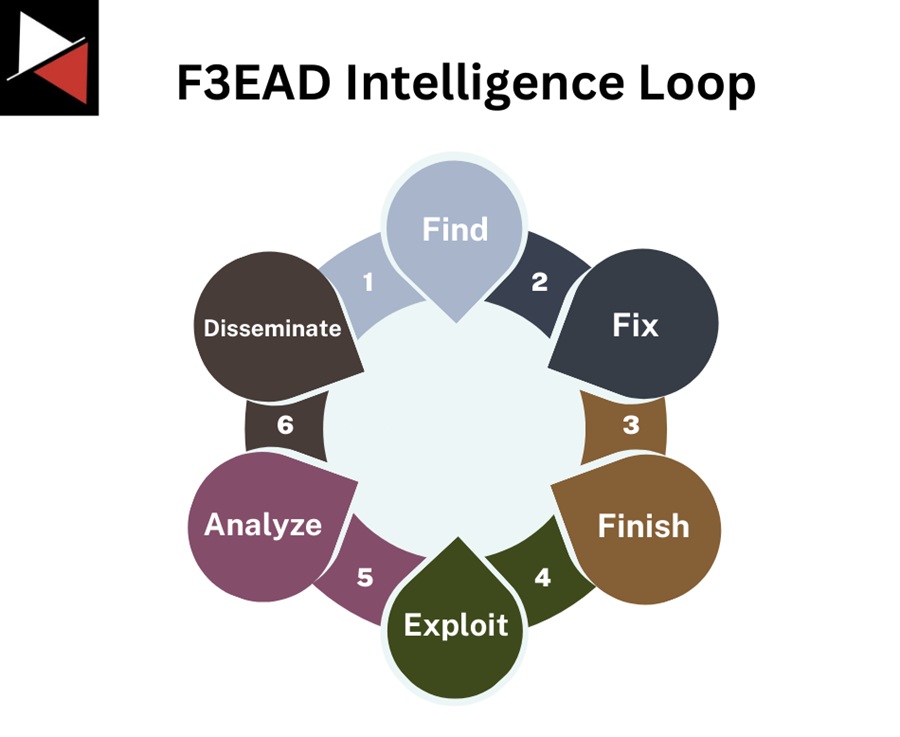
Let’s look at each stage in detail.
Stage 1: Find
The Find stage is your starting point. Here, you perform “target nomination” by deciding what you must find out about a target to answer the intelligence requirement you have been tasked with.
You may need to find data about a piece of malware, collect open-source intelligence (OSINT) about a threat actor, or gather forensic data from an incident your organization has experienced. In these cases, the target is malware, a threat actor, and a security incident.
Identifying the target of your data collection lays the foundation for the subsequent stages of the F3EAD loop and what type of intelligence you need to collect (e.g., OSINT, HUMINT, etc.).
Stage 2: Fix
Once you identify a target for collection, you must deploy your collection capabilities against it to fix the collection to a “space and time.” Within a cyber context, this typically means gaining access to the resources that will provide data about your target.
For instance, knowing where you can find data about malware or what dark web forum you can use to gather data about a threat actor. You locate the exact data resource from which you can collect your data.
Stage 3: Finish
With the data resource obtained, you can start the Finish stage. In cyber, this would be collecting the actual data, such as collecting additional malware samples, gathering data about a threat actor, or downloading the logs of an infected machine.
In a military context, this is where you achieve the desired effect on the target. You find where the target is, fix them to a single geographic point in time, and then engage them during the finish stage. Thankfully, no one is getting “neutralized” during a CTI engagement.
Stage 4: Exploit
Once you have collected data about the target, you must Exploit it to turn the data into information you can analyze. This stage may require you to bring in specialist collection capabilities to process the collected data and generate information a CTI analyst can use.
Specialist collection capabilities can include:
- Malware Analysis: To investigate malware and understand the adversary, collect indicators of compromise (IOCs), gather tactics, techniques, and procedures (TTPs), and create detections (e.g., YARA rules).
- Digital Forensics and Incident Response (DFIR): Analyzing compromised systems and networks to understand how an attack was performed and gather IOCs and TTPs.
- Reverse Engineering: To dissect malicious code to understand the capabilities of a piece of malware and collect IOCs higher up the Pyramid of Pain.
Using specialist skill sets, these roles can capitalize on the data collected during an operation. This is why you need a diverse CTI team with unique skills.
Learn more about specialist CTI roles and responsibilities in The CTI Team: Roles and Responsibilities You Need. You may have these roles within your CTI team or outsource them to other teams.
Stage 5: Analyze
Once the raw data has been turned into information, a CTI analysis can examine it and extract actionable intelligence that allows a stakeholder to develop a comprehensive understanding of the threat.
This stage will involve performing quantitative (e.g., data analytics, pattern recognition, etc.) or qualitative analysis using Structured Analytical Techniques (SATs), such as the Analysis of Competing Hypotheses (ACH).
It could also involve collaborating with experts outside of your CTI team to solicit their expert judgment about the information collected to provide you with insight.
Stage 6: Disseminate
Finally, once you have produced your intelligence product, you must share it with relevant stakeholders and decision-makers to help them decide on an appropriate course of action (CoA).
This could include sharing your intelligence product in a report, briefing, or through a machine-readable format (e.g., STIX/TAXII). It is essential that you structure your intelligence product to suit the consumer’s needs. This will facilitate informed strategic and tactical decisions and close the intelligence loop.
Using the F3EAD Intelligence Loop
Now that you know what the F3EAD loop is, how do you use it?
Let’s review several examples of intelligence requirements and apply the F3EAD loop to them so you can see how the model can be applied in the real world.
Scenario #1: Impact of a Recent Vulnerability
A key stakeholder sees something on the news about a Microsoft exploit. They know that the business uses Microsoft products and wants to see if it’s been impacted. They task their CTI team with investigating this exploit and producing a report.
The CTI manager will take this request and work with the requester to create a Priority Intelligence Requirement (PIR) that the CTI team can fulfill. This is the start of the CTI lifecycle (the Planning stage).
Once an intelligence requirement has been created, “Are any of the systems we own at ACME impacted by CVE-2025-21415?” The CTI manager and analyst will break this down into the operational RFI tasks required to fulfill this requirement.
- Are Microsoft product(s) described in this CVE relevant to our organization?
- Is there a patch/mitigation available for this CVE?
- What is the feasibility of applying this patch/migration?
- What indicators are there that a system has been exploited?
- Are there any indicators on the systems we own?
Using these RFIs, the CTI analyst can move onto the Collection stage of the CTI lifecycle and kickstart the F3EAD loop. One of these F3EAD loops could look like the following:
| Stage | Action | Outcome |
|---|---|---|
| Find | Locate machines that use the Microsoft product described in the CVE. | The IP address of machines potentially impacted by the CVE. |
| Fix | Gain access to those machines using remote machine management (RMM) software. | Access to the potentially impacted machine. |
| Finish | Check the machine for signs of exploitation (IOCs). | A yes/no answer if signs of compromise are seen. |
| Exploit | If IOCs are found, determine if the exploit was successful using DFIR skills. | Determine if an exploit was successful and what information was compromised. |
| Analyze | Analyze the impact of the machine being compromised and the effect it could have on the broader business. | Requiring DFIR or the SOC to investigate further and contain the incident. |
| Disseminate | Create an operational report for the security team, including IOCs. Create a high-level report for management describing key findings and recommendations. | Relevant stakeholders are informed with actionable intelligence and next steps. |
Scenario #2: Employee Credentials on the Dark Web
An executive sees that a massive data breach of a commercial retailer is in the news. They have used their work account to create an account with that retailer and are worried other employees may have done the same, leading to the leak of employee credentials. They ask their CTI team to investigate if employee credentials are on the dark web for sale.
The CTI manager works with the executive to create an intelligence requirement their team can fulfill. This results in the following, “Are ACME employee credentials on popular dark web forums or breach websites?” The CTI team then creates the following RFIs that must be completed to fulfill this requirement:
- What popular dark web forums and breach websites exist?
- Are we able to gain access to these collection sources?
- Can we find ACME employee credentials on these sites?
- Are the accounts for sale or leaked to the public?
- Can we verify the reliability of this data?
- What actions can we take if we find legitimate ACME credentials?
One of the F3EAD intelligence loops a CTI analyst could complete is as follows:
| Stage | Action | Outcome |
|---|---|---|
| Find | Locate the dark web forums and breach sites where employee data may appear. | A list of sites to check. |
| Fix | Gain access to these sites. | Access to the sites and the ability to collect data. |
| Finish | Collect data from these sites by searching for ACME employee credentials. | A list of compromised employee credentials. |
| Exploit | Verify that these credentials are legitimate using the expertise of the SOC or IT team. | A list of verified credentials. |
| Analyze | Analyze the credentials for insights into how they may have been compromised (e.g., patterns, trends, etc.). | Additional intelligence or context on how the credentials were leaked. |
| Disseminate | Create a tactical/strategic report on the breach, including a narrative of how the credentials leaked. Give the list to the SOC or IT team to perform password resets. | Relevant stakeholders are informed with actionable intelligence and the next steps. |
Scenario #3: Enriching Malware Samples
The security operations team comes to you asking for intelligence on a malware sample they found on an employee workstation. You take this request and generate several RFIs to create an actionable intelligence product.
- What malware family does this sample belong to?
- Where is this malware typically seen (e.g., what type of attack or recent campaign)?
- What are the capabilities of this malware?
- What IOCs are associated with this malware sample?
- Are there any detection rules that can be used to identify this malware?
One of the F3EAD intelligence loops that could play out is as follows:
| Stage | Action | Outcome |
|---|---|---|
| Find | Locate malware like the one found by the SOC team. | A list of malware to find and download. |
| Fix | Gain access to the list of malware similar to the one found. | Additional malware samples to analyze. |
| Finish | Download the malware sample into a testing environment, ready for analysis. | Malware prepped for malware analysis. |
| Exploit | Perform malware analysis to determine common IOCs and TTPs and generate detection rules. | A list of IOCs, TTPs, and detection rules. |
| Analyze | Examine the IOCs, TTPs, and detection rules to find the most impactful. | A list of prioritized IOCs, TTPs, and detection rules. |
| Disseminate | Share the prioritized list of IOCs, TTPs, and detection rules with the SOC team. | An operational report that can be used to take immediate action to address the malware found. |
These basic examples highlight how a CTI team uses the F3EAD intelligence loop to structure their CTI work from an operational perspective. In the real world, each intelligence requirement may have multiple RFIs, and each RFI may require multiple iterations of the F3EAD loop.
Conclusion
The F3EAD loop is a fundamental model in CTI. It maps out the operational tasks required for a CTI analyst to complete RFIs and fulfill intelligence requirements. The six F3EAD stages allow analysts to structure their intelligence work from collection to exploitation to analysis and dissemination.
The model works hand-in-hand with other intelligence models like the CTI lifecycle and the more strategic OODA loop. While those two models are aimed at the tactical and strategic levels, F3EAD focuses on CTI from an operational perspective and the expert skillsets that are sometimes needed to produce actionable intelligence.
Study the practical examples in this guide and apply the F3EAD intelligence loop to your CTI work!
Frequently Asked Questions
What is the F3EAD Loop?
The F3EAD loop is a structured process used to collect, analyze, and disseminate intelligence. It is primarily used in military, counterterrorism, and cyber operations to transform raw data into actionable intelligence that helps a key stakeholder make an informed decision.
The cycle includes six stages:
- Find: Identifying potential targets or threats to collect data about.
- Fix: Pinpointing the data source needed to gather the data from.
- Finish: Collecting the data required.
- Exploit: Turning the raw data into information that can be analyzed. This could require specialist skillsets (e.g., malware analysis, forensics, reverse engineering).
- Analyze: Examining the collected information to extract valuable insights and generate intelligence.
- Disseminate: Sharing the analyzed intelligence with relevant stakeholders to inform decisions.
What is the CTI Lifecycle?
The Cyber Threat Intelligence (CTI) lifecycle is a model for structuring your intelligence analysis from beginning to end. Using this model, you can create processes for gathering, analyzing, and distributing threat intelligence to your organization’s key stakeholders.
The lifecycle follows the idealized model of how Western intelligence organizations structure their intelligence work from collection to dissemination. It is a guide for the CTI team to follow when doing their work or as a template for CTI leads to use when designing processes for their teams.
What are the 5 Stages of Threat Intelligence?
The Cyber Threat Intelligence (CTI) lifecycle has five main stages:
- Direction and Planning: You define the goals and objectives of your threat intelligence activity.
- Collection: Gather information that addresses the intelligence requirements you previously defined. This involves identifying relevant data sources from which to collect information and storing it somewhere.
- Processing: Once raw data is collected, it needs to be processed to transform it into information for analysis by cleaning, normalizing, and verifying it.
- Analysis: Turning your collected information into actionable intelligence by identifying patterns, trends, and insights.
- Dissemination: Sharing the intelligence generated with key stakeholders.
What is the Difference Between D3A and F3EAD?
D3A and F3EAD are both targeting methodologies used by military and intelligence personnel. D3A is a strategic planning tool useful at higher levels of military command, while F3EAD is helpful at the operational and tactical levels.
F3EAD has emerged as a prominent methodology used in cyber threat intelligence (CTI) to fulfill intelligence requirements that require specialist skill sets, such as malware analysis, forensics, and reverse engineering. Meanwhile, D3A has remained prominent in the military as a planning tool.