-

Web Scraping Cyber Threat Intelligence Using Octoparse: Full Guide
In this complete guide, learn how to create your own custom web scraping tool to gather cyber threat intelligence using the no-code platform Octoparse.
-

C2 Hunting: How to Find C2 Servers with Shodan
C2 hunting empowers you to track down adversary C2 servers and stay a step ahead of the bad guys. This guide teaches you how to do it using Shodan.
-
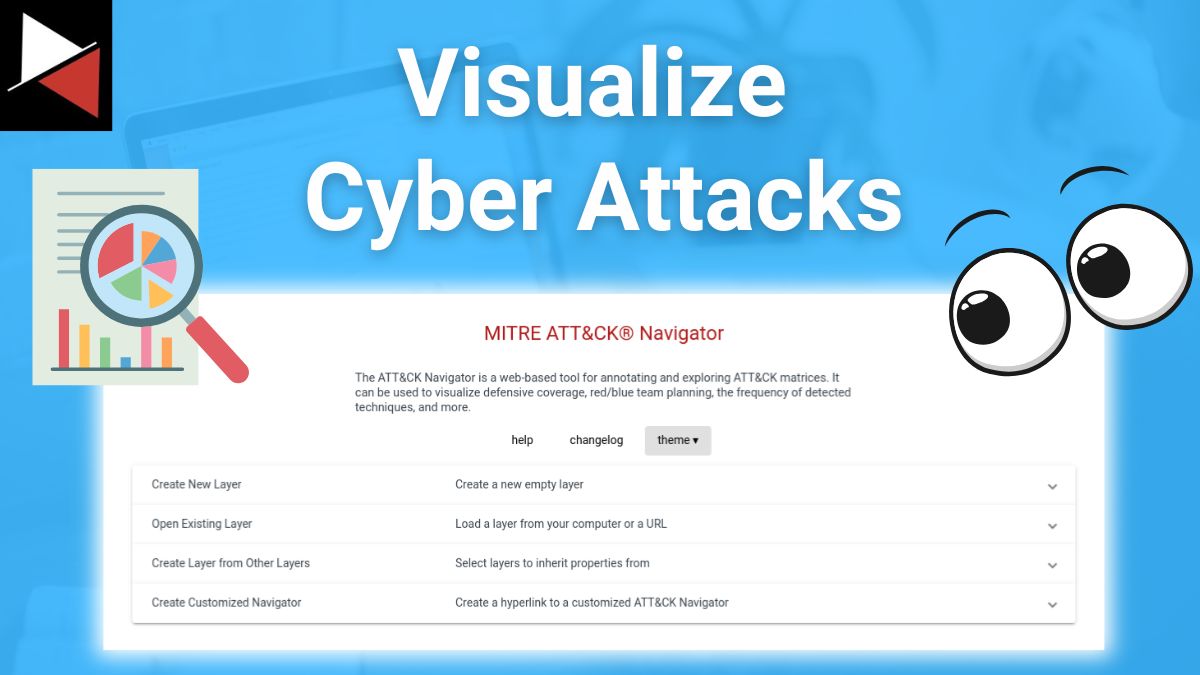
The ATT&CK Navigator: A Powerful Tool for Visualizing Cyber Attacks
Unlock the power of the ATT&CK Navigator, discover its many use cases, and learn to visualize and map attack techniques through a user-friendly interface.
-

ATT&CK Powered Suit: Streamline Your Research and Save Time
The ATT&CK Powered Suit puts the entire ATT&CK knowledge base at your fingertips. Streamline your research and save valuable time with this new tool from MITRE.
-

Collection Management Framework Template (+FREE Download)
This collection management framework template provides you with the structure to effectively document your data sources and understand how to use them.
-
Intelligence Requirements Template (PDF + Word Doc Download)
This intelligence requirements template allows you to document your company’s intel requirements and kickstart your cyber threat intelligence program.
-

Cyber Threat Intelligence Report Template (+FREE Download)
A cyber threat intelligence report template saves you and your CTI team valuable time and effort. Here is a FREE report template you can use today!
-

Essential Threat Intelligence Collection Sources You Need to Know
Intelligence collection sources are the most important component of a CTI program. This guide will teach you what they are and how to use them.
-
CTI Analysis Bias: How to Overcome Your Prejudices During Analysis
CTI analysis bias is inherent in all analysts. You must learn how to overcome it to produce accurate intelligence assessments. This guide will teach you how.
-

CTI Report Writing: How to Communicate Threat Intelligence
CTI report writing is an essential cyber security skill. This guide will teach you why it’s important, the key elements, and how to write a great report.
-

Estimative Language: How to Assign Confidence to Your Assessments
Estimative language is fundamental for good cyber threat intelligence reporting. This guide will teach you everything you need to know, from probability terms to confidence levels.
-

Intrusion Analysis: How to Fully Investigate Cyber Security Attacks
Learn how to perform intrusion analysis in this comprehensive guide that includes a four-step process for success, tips and tricks, and practical examples.
-

Crown Jewel Analysis: How to Figure Out What to Protect
Crown Jewel Analysis is a fundamental risk management methodology you should know. This guide will teach you what it is, how to use it, and tools to help.
-
The Traffic Light Protocol: How to Classify Cyber Threat Intelligence
Learn the Traffic Light Protocol (TLP). A fundamental cyber threat intelligence framework used to classify information for secure intelligence sharing.
-

5 Cyber Kill Chain Challenges and How to Prevail
Explore the top five Cyber Kill Chain challenges you will face when using this cyber security model in the real world and how to overcome them.

Blog
