Cyber threat intelligence (CTI) reports are essential for every organization. They allow you to assess emerging threats, prioritize resources, and proactively defend yourself. As a cyber security professional, you must know how to write one and be good at CTI report writing.
This guide will teach you how to write a CTI report, what you must include, and showcase a simple writing process you can follow so you don’t get stuck with writer’s block. It will also highlight best practices for CTI report writing so you can start producing high-quality reports today!
Let’s start by first understanding why CTI report writing is important and the benefits good reports can bring to an organization.
Why Is CTI Report Writing Important
A cyber threat intelligence (CTI) report provides insights into current and emerging cyber threats and is the output of following the CTI lifecycle. It is the accumulation of all your and your team’s work and the ultimate value you bring to an organization. This is why it is so important to get it right.
Your intelligence consumer doesn’t care how you collect, process, or analyze information. They care about what insights you can deliver that will support them in deciding what action to take.
The action could be operational (e.g., performing threat hunts or building detections) or strategic (e.g., making security investments or resource allocation). It will depend on the intelligence consumer and their intelligence requirements.
CTI report writing is about delivering timely, actionable, and relevant information to someone who can do something with it. This could be a key event or trend that helps a key stakeholder decide a course of action or an emerging threat that your organization must be made aware of so they can prepare accordingly.
To deliver this message, you need to structure your report so that it is easy to consume, includes key components your intelligence consumer will expect to see, and uses language that clearly answers three things:
- What is a concern?
- Why is it a concern?
- How to deal with it?
If your intelligence consumer can clearly answer these three questions after reading your report, you’ve done your job.
In summary, good CTI report writing provides the following key benefits to a business:
- Actionable Intelligence: A good CTI report will clearly communicate actionable threat intelligence that organizations can use to understand the threat landscape better, prioritize risks, and implement appropriate security measures.
- Proactive Threat Management: CTI empowers you to proactively defend your organization from current and emerging threats by assessing risks, performing threat hunting, detection engineering, and educating fellow employees.
- Enhanced Incident Response: A well-written CTI report will contain operational intelligence that an incident responder can use to quickly identify and mitigate threats to minimize the impact of a cyber attack. This includes Indicators of Compromise (IOCs) and tactics, techniques, and procedures (TTPs) an adversary uses.
- Resource Allocation: CTI reports will also include strategic intelligence that allows key stakeholders to make informed decisions about where to allocate their cyber security resources more effectively to address specific threats and critical risks.
- Increased Collaboration: Well-written CTI reports help facilitate communication and collaboration between teams within your organization and across your industry. If everyone can clearly understand the threat, why it is a concern, and how to combat it, they are more likely to work with you.
So, CTI report writing is a crucial skill, but what makes a good CTI report, and what should you include in your report? Let’s explore the key elements of a CTI report.
Key Elements of a CTI Report
A good CTI report is analogous to an onion. There are layers that you wrap your report in, and gradually, it gets more detailed the deeper you go.

You start with the structure (the outer layer) that organizes your writing into a digestible form for your reader. Then, key elements like headlines, leads, visuals, and calls to action are scattered throughout your report, acting as guideposts to help your reader navigate it. Finally, you have the language used to communicate your findings – specific and tailored to your audience.
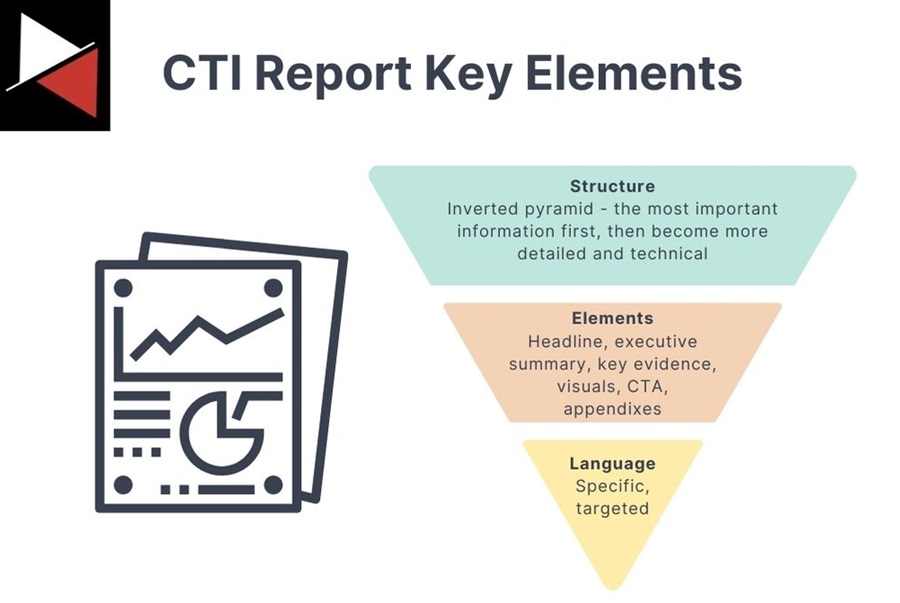
Structure
The most effective way to structure your CTI reports is by borrowing a technique from the journalist world known as the inverted pyramid. This technique presents the most important information at the start of the article (or report, in our case), followed by additional details that gradually become more technical or less important overall.
In a CTI report, this usually takes the following form:
- Headline
- Executive summary
- Key details or evidence
- Supporting evidence
- Technical details (e.g., malware analysis details)
- Recommendations
- Background information and appendixes (e.g., IOCs, TTPs, detection rules).
The executive summary is the most important part of this structure. It needs to summarize your findings succinctly, explain how you came to your conclusions, and recommend what actions to take. Getting this part of your report right should be your priority. It will impact your reader most; key stakeholders often won’t even read past these first few paragraphs.
Elements
Key elements are guideposts to help your reader navigate your report without having to read every word. The reader will expect to see them, so you had better include them.
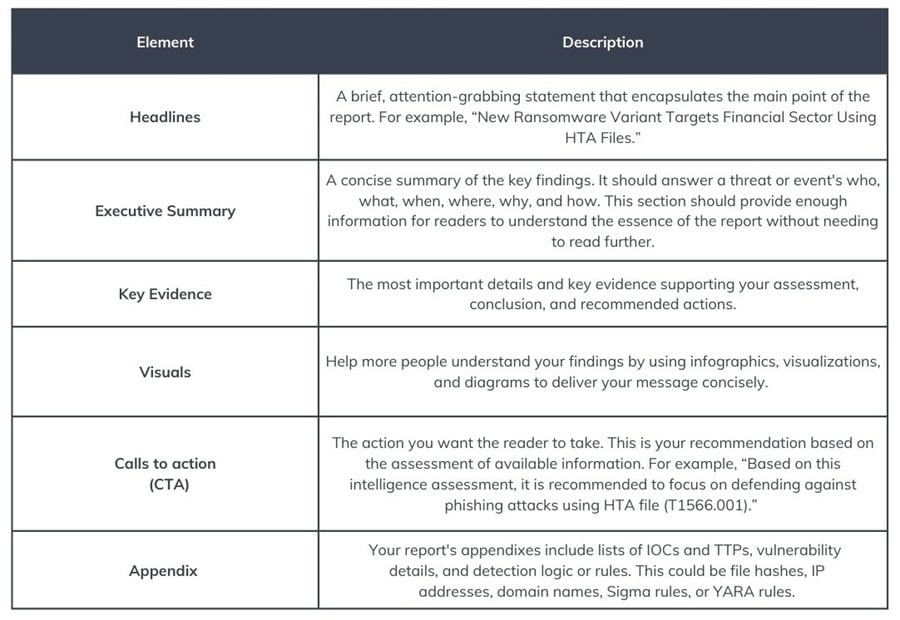
These are the foundational elements that every CTI report must include. Depending on the type of intelligence you are writing about, there may be more key elements to include. For instance, a threat actor profile should include identifiers, motivations, capabilities, and TTPs.
Check out MITRE’s CTI Blueprints project for examples of different threat intelligence reports and what to include.
Language
The innermost layer of a CTI report is the language used to communicate your findings. This should be crafted to speak to your chosen audience. If you write for an executive, it could use high-level language that skips the technical details. On the other hand, it could be highly technical if you need to communicate a specific vulnerability to a member of the operations team.
Most intelligence reports are not just for one type of audience. They include details that an executive should know and ones that the security operations team can use. As such, it is common to start with an executive summary (geared toward executives) and gradually get more technical as the report gets into the weeds or you discuss the specific evidence that led to your conclusions.
Keep it simple and easily understandable, and only get technical when necessary. You want to ensure your report speaks to the broadest audience possible.
Appendixes are a good way to separate technical details that interrupt the flow and readability of your report. These can include all the IOCs, TTPs, or vulnerability details without bogging down the natural rhythm of your report writing, making your report easier to read.
This excellent presentation by Selena Larson, a senior cyber threat analyst at Dragos, summarizes these three key components and why they are essential for writing clear and concise threat intelligence reports. She shares her experiences as a journalist and how they intertwine with CTI.
The CTI Report Writing Process
Although what makes a good CTI report is clear-cut, how you go about actually writing the report is down to you. Some analysts like to complete their assessment and have all the information upfront. Others like to create an outline before starting their assessment and fill it in as they go.
How you write your reports is down to personal preference. I will share the CTI report writing process that has served me over the years and allowed me to be the most efficient.
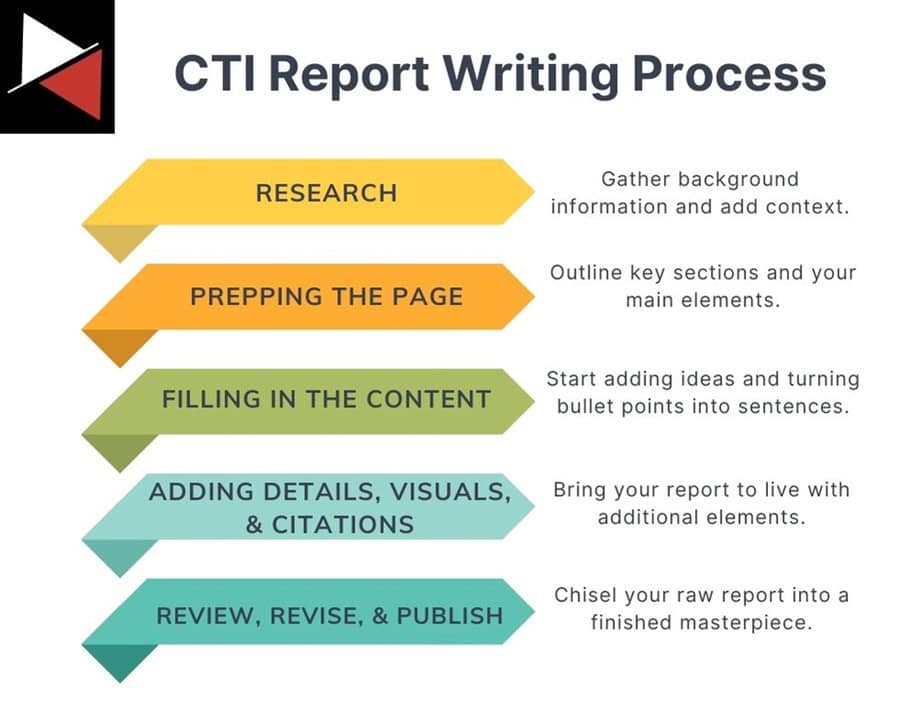
Research
Start by researching the topic, event, or outcome you are writing about in an intelligence assessment. This may sound obvious, but many analysts fail to gather background information or organize their evidence. Giving the reader context is key to good report writing.
You may be an expert in your domain, but your intelligence consumer may not be. You must provide context that allows them to get up to speed on the threat landscape quickly.
Prepping the Page
Many writers find starting the hardest part of the writing process. When faced with a blank page, knowing where to start or what to write can be daunting. This is where prepping the page comes in.
This simple writing technique will help you overcome writer’s block and get the ball rolling. You begin by outlining the main parts of your report, such as the headline, introduction, main points, and conclusion. Your big headings (H2s). From there, you write out the ideas you want to cover under these main components as H3s.
Watch this video to learn more:
You want someone to be able to skim your H2s and H3s and get the main gist of the report. They should know where you will take them without having to read every word. Once you have an outline, you can start filing in the content.
Filling in the Content
To fill in the outline I created with content, I start by adding a few bullet points under each H3 that contain key ideas or evidence I want to discuss in each section. Next, I add a connecting sentence between the H2s so the report flows and the reader can seamlessly move between ideas.
This gets the general flow of the report sorted and reminds me of the key ideas or evidence I want to discuss in each section. After this skeleton is in place, you simply transform the bullet points into sentences. Easy.
I find it easiest to write the introduction, conclusion, and executive summary last. I like to get the bulk of the report out of the way with all the details, evidence, and ideas and then return to these three sections. Filling them in once your main content is done is very easy.
Adding Details, Visuals, and Citations
As you begin filling in the content of your report, you will come across points where you need to add more details, visuals, or citations. Don’t let this bog you down. Just note what you want to add and come back later to add it.
Effective CTI report writing is all about getting into a flow where you enter a state of transferring ideas, evidence, and knowledge to paper (or keyboard taps). The longer you can sustain this flow, the quicker and better your report will be. You can always add in the nitty gritty details and pretty visuals later.
Review, Revise, and Publish
Once you have finished your first draft of the report, it’s time to review, revise, and publish. This is probably the most important step in the CTI report writing process as you need to chisel your collection of evidence and judgements into a finely crafted finished product. The reader will scrutinize your report for any mistakes, poor grammar, or key details you miss.
I strongly recommend using a grammar and punctuation checker like Grammarly when reviewing and revising your report. Tools like this will eliminate basic mistakes and force you to be clearer and more concise in your writing.
Best Practices for CTI Report Writing
Congrats, you know how to write a CTI report.
Mastering creating clear, engaging, and concise reports will take time and dedication. To help you get started, here are some best practices to focus on that will raise the level of your CTI report writing:
- Classifying the sensitivity of your report: Use an information classification framework like the Traffic Light Protocol (TLP) to ensure sensitive data is handled appropriately. This will help others share your report while remaining compliant with regulation standards.
- Communicating the likelihood of your assessment: Make sure to include estimative language to add additional context, such as how certain you are an event or outcome will happen based on the information available.
- Tailoring your report to the right audience: Ensure your report is fit for your target audience. The report’s length, the language you used, and the details you include should be targeted to deliver information to a specific intelligence consumer. Projects like MITRE’s CTI Blueprints can help you with this.
- Using well-known cyber security methodologies: Include relevant and well-known methodologies in your report where appropriate. This demonstrates you collected and analyzed all available evidence appropriately. Popular ones include the Diamond Model, MITRE ATT&CK matrix, Cyber Kill Chain, and Analysis of Competing Hypotheses. Just don’t go overboard and include them all.
- Adding a course of action to your CTA: Don’t just report on a concern and why it’s a concern; also include a call to action that specifies how the intelligence consumer can address the problem. This could be IOCs or TTPs to hunt for or strategic security investments.
- Include detection opportunities: Adding IOCs and TTPs to your report is great, but don’t just stop there. Add possible detection opportunities, pseudo logic that can be used to detect threats, or even complete detection rules like YARA and Sigma rules. These are incredibly valuable for security operations teams.
Conclusion
CTI report writing is an essential skill in your cyber security arsenal. It allows you to explain a threat, why it is a concern, and how to defend against it so that your intelligence consumer can decide what action to take.
This guide has taught you the importance of CTI report writing, the key elements to include, and how to write a report. It also highlighted best practices for elevating your reports and making them stand out. Use this practical advice to start writing better CTI reports and bringing more value to your organization.
Just remember to tailor your reports to your target audience!
Frequently Asked Questions
What is CTI Reporting?
CTI reporting is a key component of the cyber threat intelligence process. Once you have gathered and analyzed information, you need to disseminate it as intelligence so your intelligence consumer can use it to make informed decisions. Your CTI reports must accurately convey threats, risks, and actions that can be taken to defend against them. Focus on being clear, concise, and actionable.
What Are the Different Types of CTI Reports?
Depending on your target audience, you can produce different types of CTI reports. The MITRE CTI Blueprints project defines four main types:
- Threat Actor Report: This report type is a living encyclopedia about a threat actor or category of activity that is updated whenever new intelligence about an adversary is generated. It is a reference for tactical teams to understand how an adversary operates.
- Intrusion Analysis Report: These reports support threat hunting and incident response operations by providing actionable indicators that these teams can use to search for threats within your environment. They are iterative and based on intrusion analysis findings.
- Campaign Report: This report highlights new information about threat actors, campaigns, and capabilities. It is concise and conveys changes your intelligence consumers should be aware of.
- Executive Report: This report informs key decision-makers (non-technical stakeholders) about threats. It is clear and precise to support a strategic decision, focusing on the why and how rather than the what and when.
How Do You Write a Cyber Threat Report?
To write an effective CTI report, you should follow these five steps:
- Research the topic, event, or outcome for which you are writing an intelligence assessment. You must provide context allowing the reader to quickly get up to speed on the threat landscape.
- Prep the page by outlining the main parts of your report, such as the headline, introduction, main points, and conclusion. Then, write the ideas you want to cover under these main components.
- Fill in the content using your outline. Add connecting sentences to join each component and transform your bullet points into sentences.
- Add details, visuals, and citations to your report to beef it up and make it more appealing to read.
- Review, revise, and publish your CTI report. Ensure it is free of mistakes and poor grammar, with all the key details included.
What Is a Threat Report in Cyber Security?
A threat report is a comprehensive document that informs an intelligence consumer or key decision-maker about a threat. It explains a concern, why it is a concern, and what can be done to address it. A report can be highly technical and aimed at operations teams or high-level and support a strategic decision. The type of report you write will depend on your target audience and intelligence requirements.




