How do you know if your cyber threat intelligence is any good? Do you spell check, corroborate evidence, and tailor it to your audience? How do you remember to do all these things and produce consistent quality? Let me introduce you to the principles of intelligence.
The eight principles of intelligence will improve your intelligence work. They help guide you, keep your processes on track, and ensure your end product can withstand scrutiny. This guide explores each and gives you actionable advice on achieving them, from using a threat intelligence platform to structured analytical techniques to having an intelligence fusion function.
Let’s get stuck in and find out how to ensure you deliver a quality intelligence product every time!
The 8 Principles of Intelligence
All cyber threat intelligence (CTI) projects require careful planning, review, and guiding principles to uphold high quality. Common principles include sticking to a budget, delivering milestones on time, and SPAG (spelling, punctuation, and grammar). CTI projects must abide by these principles and eight principles specific to intelligence.
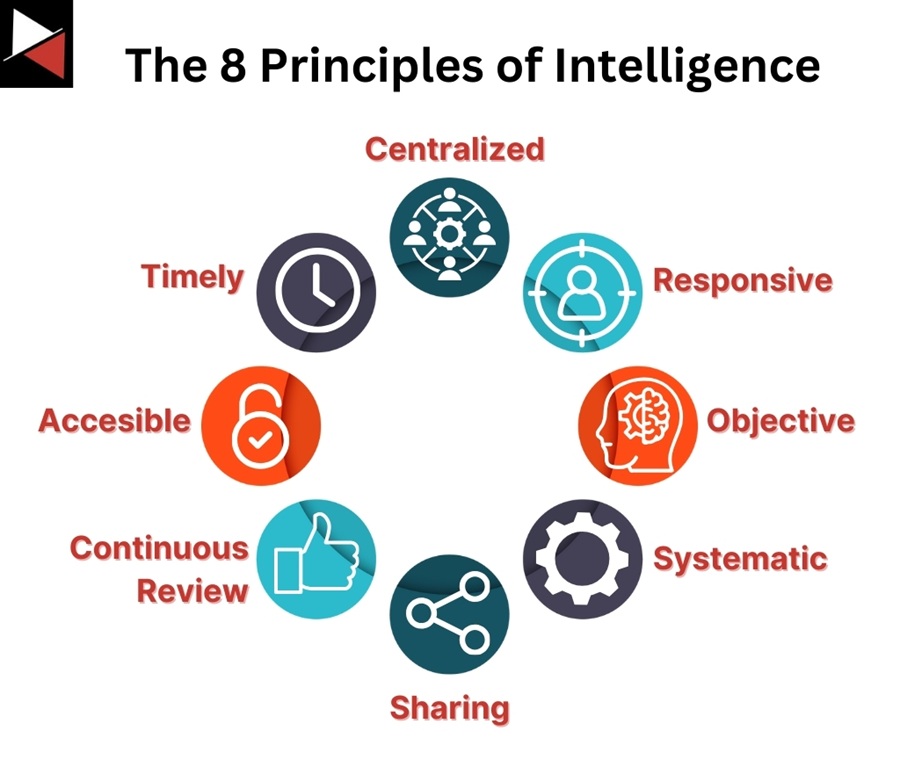
These eight principles of intelligence come from CREST and outline the key foundations that all CTI processes and products must adhere to. You can use them as a checklist when planning and reviewing your CTI project to ensure its quality.
CREST is an internationally recognized governing body that sets standards and provides accreditation for companies and professionals in the cyber security industry. It plays a vital role in the cyber security ecosystem by ensuring that security testing and related services are performed to the highest standards.
To remember these principles, you can use the mnemonic CROSSCAT. Let’s look at each.
#1 Centralized
You should have centralized control of your intelligence. This allows for efficient allocation to the right people and departments, a standardized approach, and a point of contact for any questions or issues.
Having your intelligence controlled by a centralized system allows you to control the flow of intelligence from collection to dissemination. Individuals can be tasked appropriately without duplication of effort, and resources can be maximized. For instance, having centralized intelligence tasking prevents the tasking of intelligence requirements (IRs) or Request for Information (RFIs) multiple times.
The larger your organization becomes, the more important this principle becomes!
The easiest way to achieve centralized intelligence is using a Threat Intelligence Platform (TIP), where all intelligence goes into and is shared from. You can use open-source solutions, like MISP or OpenCTI, or commercial options, like Recorded Future or Anomali ThreatStream.
#2 Responsive
Intelligence needs to be responsive to its consumers. It needs to be the right type of intelligence, adaptable to the needs of specific intelligence consumers, and shared using a clearly defined reporting method.
This could mean producing operational intelligence that is shared using a STIX/TAXII feed, tactical intelligence delivered in a report, or strategic intelligence presented to executive leadership using PowerPoint.
It is important to note that tactical and operational intelligence can be defined differently, depending on who you are talking to in CTI. This is often the case in North America, where tactical and operational intelligence are flipped (CrowdStrike). The descriptions above align with how operational, tactical, and strategic intelligence are defined in the United Kingdom and Europe (CREST).
#3 Objective
The CTI team that fulfills the CTI project must remain as objective as possible. Procedures should be in place to remove prejudice and bias from reports and ensure the intelligence product produced supports informed decisions.
This is often difficult to achieve and requires careful planning, Structured Analytical Techniques (SATs), and a thorough editorial review to succeed. You must ensure these procedures are set up before starting your CTI project.
You can have a specific team member responsible for writing, editing, and reviewing all the technical documentation and reports your CTI team produces (e.g., a Technical Writer). They can help assess the objectivity of the intelligence work.
#4 Systematic
To produce intelligence, your CTI project must methodically exploit data and information in a coherent and coordinated fashion. This includes using qualitative (e.g., SATs) and quantitative methods (e.g., data analysis) to produce an intelligence product that, when questioned, stands up to scrutiny and remains reliable.
In simple terms, you must show your work. Use well-known analysis techniques to explore problems and solutions logically.
#5 Sharing
You might have the greatest intelligence that can save your organization from disaster. However, if you do not share this intelligence, if it is shared in the wrong format or with the wrong people, or if it is not securely shared, you have a problem.
Intelligence should be shared according to its protective markings (e.g., Traffic Light Protocol), intelligence sources should be protected, and the intelligence product should be protected in transit and at rest (e.g., encryption).
#6 Continuous Review
All intelligence has a shelf life. A CTI product or assessment is just a snapshot in time. Its usefulness will expire after a certain period. This means intelligence must be continually updated and challenged when new information is revealed.
During the feedback stage of the CTI lifecycle, you must gather insights from key stakeholders on the value of the intelligence you have produced, how it will be used, and what improvements could be made. These metrics allow you to refine your intelligence product and ensure it is effective for your consumers.
Iterating on an intelligence product may fall outside the scope of your CTI project if you are just consulting a customer. Nevertheless, gathering feedback to improve your project next time is still important.
#7 Accessible
An often overlooked principle is Accessibility. Your intelligence product is worthless if it cannot be accessed physically and conceptually. Consideration must be given to the audience consuming your intelligence, and different formats should be available to accommodate their diverse needs.
For instance, ensure the color scheme you use on reports accommodates those who are color blind and add accessibility features that make your presentation digestible for those who are neurodiverse (e.g., images, simple bullet points, stories, etc.).
Accessibility also goes beyond accommodation for those with disabilities. For example, have you ensured that your intelligence customer can easily (and securely) access your intelligence product?
#8 Timely
In the world of CTI, an 80% completed CTI project on time is better than a 100% late project!
Threat intelligence is time-sensitive. Your intelligence project must be delivered within an effective timeframe to be useful to your consumer. It’s better to be ugly and timely rather than pretty and late.
This is where the idea of an Intelligence Cut-Off Date (ICOD) comes in useful. An ICOD is the last date the intelligence product is useful to the client. Agree on ICODs with your intelligence consumer and stick to them.
Knowing the eight principles of intelligence is great. But how can you fulfill them?
Fulfilling the 8 Principles of Intelligence
You need an intelligence fusion function to ensure your CTI project fulfills the eight principles of intelligence. But wait. What is an intelligence fusion function?
An intelligence fusion function is a set of processes responsible for the mechanics of intelligence work. It is typically used in the public sector to ensure that timely, relevant, and accurate intelligence is shared between government agencies.
In Europe, there are projects like the NATO Intelligence Fusion Centre; in the United States, there is an entire National Network of Fusion Centers. These exist between State, Local, Tribal/Territorial (SLTT), federal, and private sector partners.

You don’t need an entire center to support your CTI project, but you do need processes to support the following:
- Defending your intelligence requirements and project objectives to ensure scope creep does not occur.
- Managing the input of specialists into the intelligence product (e.g., the F3EAD loop).
- Ensuring the administrative elements of intelligence work are defined and adhered to.
You should have a person on your CTI team who is responsible for intelligence fusion. This person must ensure that intelligence work is centralized, responsive, accessible, systematic, shared in a timely manner, and continuously reviewed.
These responsibilities typically lie with the CTI manager, who oversees the project and ensures that the intelligence produced aligns with business and security objectives. However, they may rely on other team members, like a technical writer, to fulfill other intelligence principles (e.g., objective) and their CTI analysts to ensure principles are followed when performing operational work (e.g., systematic and sharing).
A technical writer or editor is a supplementary role in your CTI team. They assess the validity of your intelligence product or assessment and its content from a non-technical perspective. Although they do not perform technical CTI work, they are imperative to ensuring the quality of your CTI product.
Having the intelligence fusion function (and its associated processes) outlined in your CTI project planning will ensure you keep each CROSSCAT principle at the forefront of your work.
Conclusion
To ensure you deliver high-quality intelligence and meet the expectations of your intelligence consumer, you must abide by the eight principles of intelligence. Following these principles allows you to deliver timely, actionable, and tailored intelligence to help a key stakeholder make an informed decision.
When planning any CTI project, make sure you include how you will fulfill each of these principles. You could use a TIP to ensure your intelligence is centralized, follow SATs so your analysis is objectives and systematics, and have an intelligence fusion function to fulfill the responsive and timely principles.
Try adding these principles of intelligence to the next iteration of your CTI lifecycle!
Frequently Asked Questions
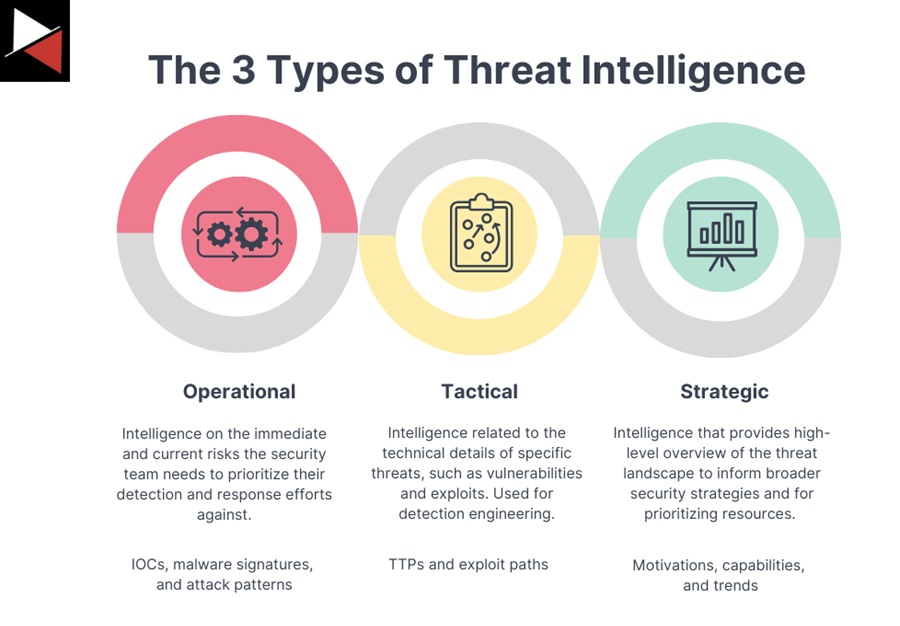
What Are the Three Types of Cyber Threat Intelligence?
There are three main types of cyber threat intelligence that you use to categorize a piece of intelligence:
- Operational: intelligence on the immediate and current risks the security teams need to prioritize their detection and response efforts against.
- Tactical: Intelligence related to the technical details of specific threats, such as vulnerabilities and exploits. This is used for detection engineering and threat hunting.
- Strategic: Intelligence that provides a high-level overview of the threat landscape to inform broader security strategies and prioritize resources.
What Are the Principles of Intelligence?
There are eight principles of intelligence that ensure the intelligence product produced is high quality and actionable for the intelligence consumer. These can be remembered with the mnemonic CROSSCAT and include:
- Centralized: Central control of your intelligence allows for efficient resource allocation, a standardized approach to intelligence work, and a point of contact for any questions or issues that arise.
- Responsive: Intelligence needs to be responsive to the consumers of that intelligence and tailored to their use cases.
- Objective: CTI practitioners must remain as objective as possible in their assessments, and procedures must be in place to remove biases from intelligence products.
- Systematic: The data turned into intelligence needs to be methodically exploited in a coherent and coordinated fashion so that when questioned, it stands up to scrutiny and remains reliable.
- Sharing: Intelligence must be shared in a timely manner, in a format suitable for the intelligence consumer, and protected in transit and at rest (encryption).
- Continuous Review: Intelligence has a shelf life and will expire after a certain time. Assessments must be continually challenged when new information is revealed, and feedback must be taken into account at all stages.
- Accessible: Intelligence that cannot be accessed physically or conceptually is worthless. Consideration must be made for the audience consuming your intelligence, and different formats must be made available.
- Timely: An 80% solution on time is better than a 100% solution that is late. Intelligence is time-sensitive and is only useful when delivered within an effective timeframe.
What is Intelligence Fusion?
An intelligence fusion function is a set of processes responsible for the mechanics of intelligence work. It ensures that timely, relevant, and accurate intelligence is shared between intelligence producers and consumers.
This responsibility typically falls to the CTI manager overseeing the project and ensuring that the intelligence produced aligns with business and security objectives. They are ultimately accountable for ensuring that the eight principles of good intelligence are met.




